In keeping with
ArsTechnica, researchers at the moment offered proof exhibiting that over 4 years as many as hundreds of iPhone items have been attacked by spy ware. These iPhones have been owned by workers of safety agency Kaspersky in Moscow. The attackers have been in a position to get hold of a degree of entry by no means seen earlier than and it was all carried out by exploiting a vulnerability in a {hardware} characteristic that not too many outdoors of Apple and semiconductor design agency Arm Holdings have been acquainted with.
It is not identified how the attackers realized about this {hardware} characteristic and even the researchers do not know what goal it had. Additionally unknown is whether or not the {hardware} was a local iPhone half or enabled by a third-party element similar to Arm’s CoreSight. Along with infecting iPhone items belonging to Kaspersky workers, the spy ware additionally affected the iPhones that have been utilized by hundreds of individuals working in embassies and diplomatic missions in Russia.
How was the spy ware disseminated to focus on iPhones? It apparently was despatched via iMessage texts utilizing a course of that didn’t require the sufferer to take any motion. As soon as contaminated, the iPhones transmitted microphone recordings, pictures, geolocation information, and different delicate info to servers managed by the attackers. Whereas rebooting an iPhone would rid the gadget of the an infection, the attackers would ship a brand new textual content loaded with spy ware to the identical gadget and re-infect it each time it was rebooted.
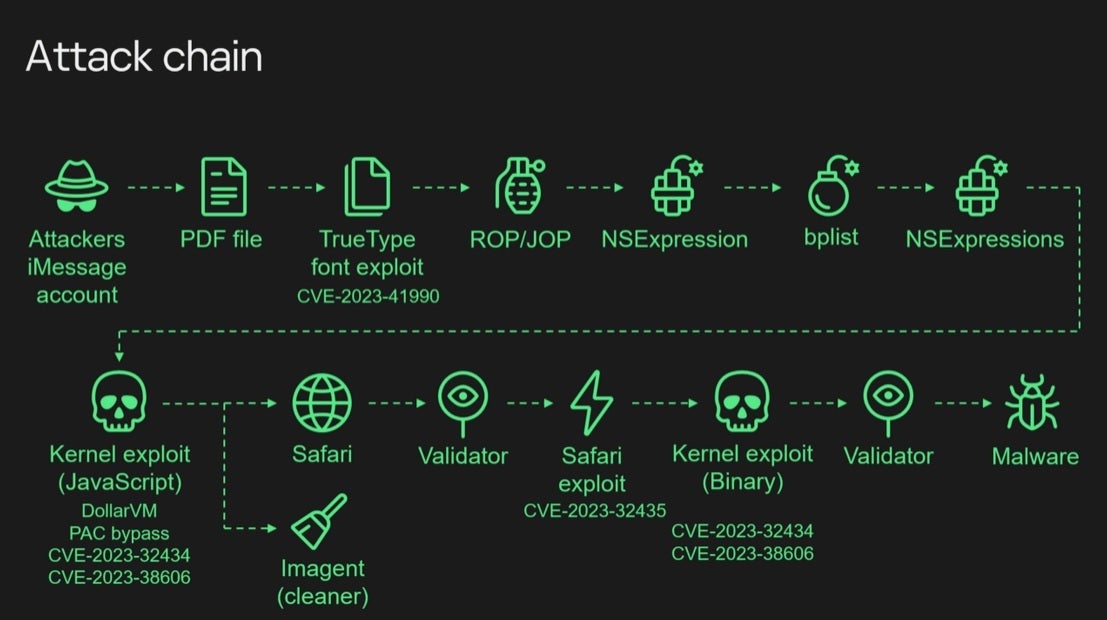
The Triangulation exploit chain
In an e-mail, Kaspersky researcher Boris Larin wrote, “The exploit’s sophistication and the characteristic’s obscurity counsel the attackers had superior technical capabilities. Our evaluation hasn’t revealed how they grew to become conscious of this characteristic, however we’re exploring all prospects, together with unintended disclosure in previous firmware or supply code releases. They might even have stumbled upon it via {hardware} reverse engineering.”
The malware and the marketing campaign that led to the set up of it have been each known as “Triangulation” and it contained 4 zero-day vulnerabilities which signifies that the attackers knew about these vulnerabilities earlier than Apple did. Apple has since patched the issues which have been cataloged as:
- CVE-2023-32434
- CVE-2023-32435
- CVE-2023-38606
- CVE-2023-41990
The aforementioned secret {hardware} on the root of this problem and the 4 zero-day flaws not solely affected iPhone fashions, it additionally impacted iPads, iPods, Macs, Apple TVs, and Apple Watches. Apple patched the vulnerabilities on the entire above-mentioned units.
In a press launch, Kaspersky’s Larin added, “That is no odd vulnerability. As a result of closed nature of the iOS ecosystem, the invention course of was each difficult and time-consuming, requiring a complete understanding of each {hardware} and software program architectures. What this discovery teaches us as soon as once more is that even superior hardware-based protections will be rendered ineffective within the face of a complicated attacker, significantly when there are {hardware} options permitting to bypass these protections.”
As for who was behind the assault, some blame the U.S. Nationwide Safety Company (NSA). Russia’s Federal Safety Service says the assault got here from the NSA working with Apple though Kaspersky stated that it has no proof that both have been concerned.