Cybercrime continues to develop quickly; certainly, it’s a extremely profitable world business. With out precisely accounting for income from cybercrime (1, 2), we’re left wanting on the staggering estimated value of US$7.08 trillion in 2022 for reference. Measured by way of GDP, the unlawful proceeds would rank as the third-largest “economic system” worldwide. Regardless, this panorama retains evolving, pushed by new tech, additional monetization of the web, new illicit alternatives enabled by the colourful cybercrime as-a-service enterprise mannequin, and ever extra assets invested in prison revenue extraction.
Cybercrime has world attain, is aware of no borders and the barrier to entry is low. Certainly, in comparison with conventional crime, this can be a high-reward, low-risk ‘enterprise’, with legislation enforcement dealing with persistent challenges in bringing cybercriminals to justice. Its progress is additional fueled by the truth that many individuals aren’t ready to face digital threats. Lastly, the alternatives to pursue cybercrime loom massive over each customers and enterprise 24/7 and might impression almost each individual or group that has or handles private or in any other case precious information.
As a result of scale of the issue and the surge in its impacts, customers have gotten more and more involved about their on-line security and privateness, prompting a requirement for larger safety beneath the legislation and transparency in information transmission, not solely with delicate providers like finance, but in addition extending to transportation and even leisure. Concern has additionally impacted customers’ “attitudes” relating to how their chosen digital safety services operate, and the way these capabilities are carried out to additional the continued progress within the cybersecurity business. Nevertheless, what these modifications don’t present is that many threats, particularly internet threats, nonetheless handle to slide by way of the cracks.
In cooperation with Join-Residing, unbiased testing group AV-Comparatives not too long ago put 20 shopper safety distributors to the check -including ESET- analyzing data-sharing practices, insurance policies, accessibility, and transparency. ESET emerged as one of many top-performing distributors, receiving 4.5/5 stars.
To handle these threats, shifts in know-how are wanted that align with the on a regular basis threat customers take after they need to share their private information with web sites and apps. This want goes past AV merchandise that primarily defend investments made in PCs [which, coincidentally, require certain data collection to be able to analyze threats and recognize them in future instances (e.g., identification of types of malicious code attempting to infect a device)].
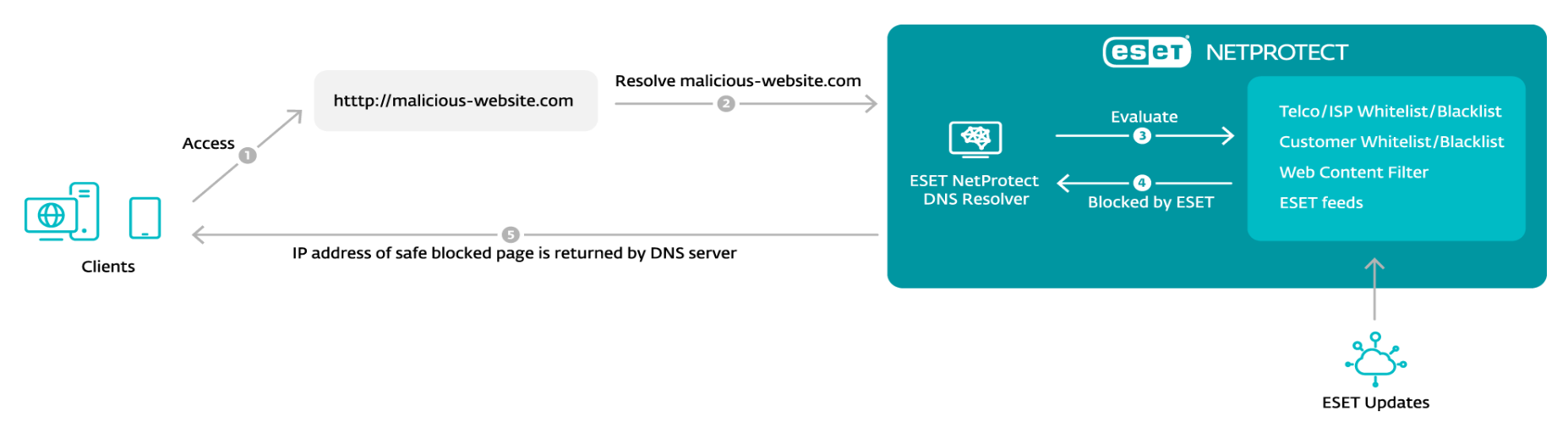
As a substitute, rising approaches to safety have to ship impactful safety that mitigates web-based threats. This requires safety distributors and Web Service Suppliers (ISPs) – in tandem – to concentrate on defending belief itself. These efforts have led to the event of services that safe the exact moments a consumer takes motion based mostly on an (on-line) belief relationship. One highly effective strategy will be achieved by blocking many strategies prized by cybercriminals at their very foundations, specifically on the Area Title System (DNS) degree.
Internet threats
The dimensions and scope of the world extensive internet imply that the true miracle of its inception is the power to go looking, filter, and efficiently entry content material. Whereas DNS is definitely a pairing of numeric Web Protocol (IP) addresses utilized by computer systems with text-based domains utilized by people, for customers it’s an deal with ebook for the online and performs unnoticed.
Nevertheless, occasions change. We will muse that threats and malicious domains ought to by no means have entered into existence, however the rising quantity and complexity of threats exhibits that to be an impossibility. Thus, DNS is more and more checked out to offer complete safety, a task it could possibly play by filtering out malicious or suspicious domains. To create a workable DNS-level safety answer, safety distributors, ISPs, and telecommunications or communications service suppliers (TELCOs) need to accomplice up and deploy these automated techniques at scale.
As nearly all world extensive internet exercise takes place by way of DNS, utilizing it to sort out internet threats isn’t any small matter. Telemetry from ESET and different distributors exhibits that even supposing the variety of potential internet threats has gone down barely previously years, some, like phishing, proceed to be prevalent. Statistics from the T3 2022 Risk Report confirmed that, for instance, the whole variety of blocked phishing web sites climbed to 13 million globally.
Newer developments seen with internet threats contain legit web sites internet hosting malware, referred to as malware objects, which have been documented by ESET since its Q2 2022 Risk Report. Right here, an in any other case legit web site from a legit creator has been compromised by a 3rd get together who has implanted malicious capabilities: weblinks, pdfs, or lead seize, or the web site has develop into host to a service that permits others to retailer or obtain recordsdata. These recordsdata might then embody malicious code, unlawful or dangerous content material, or malware objects.
IoT Threats
Web of Issues (IoT), one other identify for good gadgets that work by being related to the web, embody gadgets like child displays, door cameras, TVs, medical gadgets, house home equipment, community routers, and far more. Oftentimes, these devices have been rushed to market with out sturdy safety measures in place and have restricted to non-existent on-device security measures, together with weak authentication mechanisms, vulnerabilities and non-existent replace paths, and unencrypted information transmissions. Consequently, cybercriminals can misuse IoT gadgets broadly, together with to create large networks of compromised gadgets often known as botnets. These can be utilized to overwhelm varied forms of on-line techniques, from web sites to telecommunications providers and important infrastructure.
Addressing IoT safety is important as a result of botnets pose a big risk, whether or not used to execute large DDoS assaults, brute power (password/credential guessing), additional infections, or vulnerability exploitation. They do that by compromising the community or the gadgets which have a cloud-based management panel (for instance, outdated IP cameras) the IoT machine is related to. Since IoT gadgets are operated by way of connection to a router, many doorways are open for these eager to trigger hurt. Botnets are one in all attackers’ most prized instruments, and one which DNS-level safety is very efficient towards.
With important incidents as early 2001, assaults have solely elevated in scale, frequently disrupting and even stopping entry to a number of the world’s hottest web sites and providers. Certainly one of these, the Mirai botnet, has since 2016 periodically hijacked consumer-grade Web of Issues (IoT) gadgets, utilizing lots of of 1000’s of them to orchestrate assaults. These assaults can nonetheless be detected in 2023.
Different botnets, like Mozi, which have joined the threatscape extra not too long ago, have additionally benefited from variants of Mirai, that’s till October 2023 when it just about disappeared in an obvious takedown. Throughout its reign between 2019 and 2023, the Mozi botnet turned the most important of its type, at one level incorporating over 1.5 million distinctive gadgets into its community and working primarily by way of recognized vulnerabilities in NETGEAR DGN gadgets and JAWS internet servers.
Routers
Becoming a member of IoT threats, internet threats vectoring by way of compromised routers will be managed with DNS Safety by blocking entry to malicious or suspicious domains. This works to interrupt prison infrastructure like phishing and malicious web sites used to steal customers’ private information and credentials. DNS safety, paired with a multilayered safety answer that options community inspection instruments, which allow customers to check their routers for weaknesses equivalent to poor passwords and out-of-date firmware. This mix mitigates the safety implications of know-how’s relentless march towards bringing every kind of on a regular basis bodily objects on-line and making them “good.”
And, whereas good is the brand new commonplace, we should acknowledge that many dangers observe when “on a regular basis objects” are embedded with software program, processors, sensors, actuators, and web connectivity that allow them to gather information and work together each with their setting and each other.
When discussing the myriad good gadgets that now inhabit our properties, it’s important to place a highlight on routers. Not solely are these the unsung heroes of recent connectivity remaining turned on 24/7, however they’re really the inspiration of the related house. Actually, they’re specialised computer systems whose working techniques, embedded as firmware, require important updates to handle safety loopholes, and are topic to manufacturer-maintained lists of end-of-life gadgets.
And, whereas routers don’t retailer folks’s private information, all site visitors from each internet-enabled machine in a family goes by way of the router. Poorly secured, they’ll put all gadgets on a community on the mercy of dangerous actors. And, in an period of distant/hybrid working, their safety has taken on larger significance and will even have implications for company networks. Right here a couple of measures go a good distance: utilizing sturdy passwords as an alternative of defaults, making use of the best degree of encryption, disabling distant administration entry and each pointless providers and options to scale back assault surfaces, or creating separate networks for IoT gadgets to guard information on PCs and smartphones.
Preserving the world related and safe
The TELCO and ISP business, which income from world connectivity, additionally bears the duty of safeguarding huge quantities of private information entrusted to it by their clients. Correctly managing this information is pivotal to TELCO and ISP fame and guaranteeing the belief wanted to gasoline their enterprise mannequin.
In response to rising pressures from cybercriminals and the evolving wants of their clients, conserving tempo with rising threats and securing the belief relationships demanded in right this moment’s digital world is a should. Belief will not be merely a product/service, but in addition the important aspect to have interaction in on-line trade in any respect, a lot in order that partnering with the correct safety supplier, one which safeguards not solely the ISP/TELCO but in addition its clients and their information, is essential for future-proofed enterprise.
With extra discerning clients fretting about safe connections and information than ever earlier than, ISPs and TELCOs might want to differentiate themselves by way of the safety options they provide, together with whether or not there’s an choice so as to add an additional layer like DNS safety to the shopper’s plan. Offering this extra degree of service, in partnership with safety distributors, not solely advantages finish customers however enhances the supplier’s fame.
For his or her half, cybersecurity distributors have additionally needed to evolve over the past 30 years, from defending and securing {hardware}, to precious information, and more and more, to securing personally identifiable information. In league with ISPs and TELCOs, it may be precisely mentioned that safety distributors now goal to guard customers’ digital lives. Central to this mission is DNS safety, which affords widespread advantages. DNS safety coupled with router safety are simple methods to safeguard quite a few households, particularly the place each web service subscriptions and cell information are in use.
The use case extends additionally to high-traffic areas like cafes, eating places, lodges, airports, and hospitals, the place offering public Wi-Fi entry is frequent; in these areas DNS options provide a really protected and user-friendly selection. Contemplate a hospital with a single community catering to over a thousand each day sufferers, not counting guests and employees. This community concurrently shops important medical information and certain additionally helps many different skilled and even private on-line actions. Right here, safety challenges can mushroom from the fairly open community entry required – the place anybody, together with potential malicious actors, may join and exploit the community.
Cybercrime will not be going anyplace
Cybercrime stays an everlasting and ever-evolving problem in our related world. To foster a safer on-line setting, people should prioritize their digital security. Nevertheless, TELCOs and ISPs are rising because the entities with essentially the most company, and probably the first duty for addressing these dangers. By exploring DNS safety in league with safety distributors can allow speedy deployment of extra sturdy safety measures the place wanted.
Shoppers’ rising concern about safety and privateness has signaled that TELCOs and ISPs should deal with these worries proactively. And, given the pervasive nature and substantial financial impression of cybercrime, it’s essential for all stakeholders to take it severely. Many of those assaults goal customers instantly, creating a robust demand for accessible but highly effective safety options. In right this moment’s data-driven panorama, the place huge quantities of knowledge are collected and utilized, the necessity for enhanced safety is gaining momentum. This presents a big alternative for TELCOs and ISPs to satisfy the rising demand for safe digital experiences based mostly on belief.

