Indian authorities entities and the protection sector have been focused by a phishing marketing campaign that is engineered to drop Rust-based malware for intelligence gathering.
The exercise, first detected in October 2023, has been codenamed Operation RusticWeb by enterprise safety agency SEQRITE.
“New Rust-based payloads and encrypted PowerShell instructions have been utilized to exfiltrate confidential paperwork to a web-based service engine, as a substitute of a devoted command-and-control (C2) server,” safety researcher Sathwik Ram Prakki stated.
Tactical overlaps have been uncovered between the cluster and people broadly tracked below the monikers Clear Tribe and SideCopy, each of that are assessed to be linked to Pakistan.
SideCopy can be a suspected subordinate aspect inside Clear Tribe. Final month, SEQRITE detailed a number of campaigns undertaken by the risk actor focusing on Indian authorities our bodies to ship quite a few trojans similar to AllaKore RAT, Ares RAT, and DRat.
Different current assault chains documented by ThreatMon have employed decoy Microsoft PowerPoint information in addition to specifically crafted RAR archives prone to CVE-2023-38831 for malware supply, enabling unbridled distant entry and management.
“The SideCopy APT Group’s an infection chain includes a number of steps, every rigorously orchestrated to make sure profitable compromise,” ThreatMon famous earlier this 12 months.
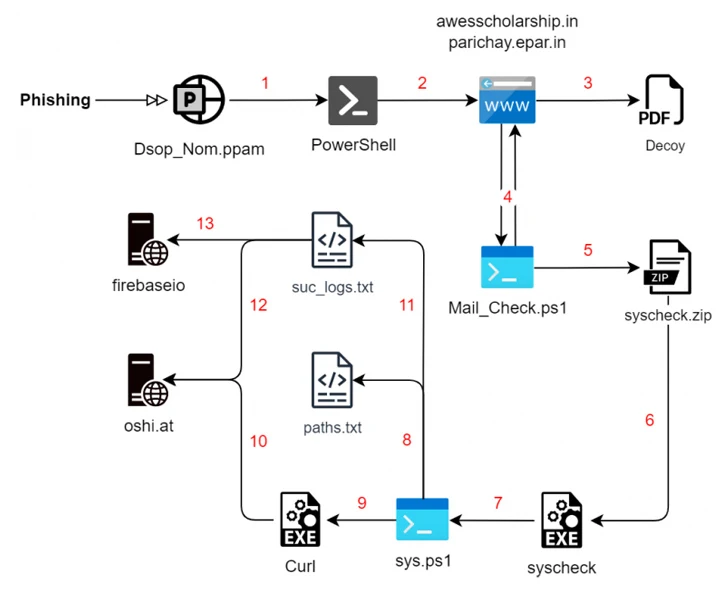
The newest set of assaults commences with a phishing e-mail, leveraging social engineering strategies to trick victims into interacting with malicious PDF information that drop Rust-based payloads for enumerating the file system within the background whereas displaying the decoy file to the sufferer.
Moreover amassing information of curiosity, the malware is supplied to gather system info and transmit them to the C2 server however lacks the options of different superior stealer malware out there within the cybercrime underground.
A second an infection chain recognized by SEQRITE in December employs an analogous multi-stage course of however substitutes the Rust malware with a PowerShell script that takes care of the enumeration and exfiltration steps.
However in an attention-grabbing twist, the final-stage payload is launched through a Rust executable that goes by the identify “Cisco AnyConnect Internet Helper.” The gathered info is finally uploaded to oshi[.]at area, an nameless public file-sharing engine known as OshiUpload.
“Operation RusticWeb might be linked to an APT risk because it shares similarities with numerous Pakistan-linked teams,” Ram Prakki stated.
The disclosure comes practically two months after Cyble uncovered a malicious Android app utilized by the DoNot Staff focusing on people within the Kashmir area of India.
The nation-state actor, additionally recognized by the names APT-C-35, Origami Elephant, and SECTOR02, is believed to be of Indian origin and has a historical past of using Android malware to infiltrate units belonging to individuals in Kashmir and Pakistan.
The variant examined by Cyble is a trojanized model of an open-source GitHub undertaking known as “QuranApp: Learn and Discover” that comes fitted with a variety of spyware and adware options to document audio and VoIP calls, seize screenshots, collect information from numerous apps, obtain extra APK information, and observe the sufferer’s location.
“The DoNot group’s relentless efforts to refine their instruments and strategies underscore the continued risk they pose, notably of their focusing on of people within the delicate Kashmir area of India,” Cyble stated.