Digital Safety
AI-driven voice cloning could make issues far too simple for scammers – I do know as a result of I’ve examined it so that you just don’t must be taught concerning the dangers the onerous manner.
22 Nov 2023
•
,
6 min. learn
The latest theft of my voice introduced me to a brand new fork within the street when it comes to how AI already has the potential of inflicting social disruption. I used to be so stunned by the standard of the cloned voice (and in that extraordinarily intelligent, but comedic, type by certainly one of my colleagues) that I made a decision to make use of the identical software program for “nefarious” functions and see how far I might go with a purpose to steal from a small enterprise – with permission, in fact! Spoiler alert: it was surprisingly simple to hold out and took hardly any time in any respect.
“AI is more likely to be both the most effective or worst factor to occur to humanity.” – Stephen Hawking
Certainly, because the idea of AI turned extra mainstream in fictional movies corresponding to Blade Runner and The Terminator, folks have questioned the relentless prospects of what the know-how might go on to provide. Nevertheless, solely now with highly effective databases, rising laptop energy, and media consideration have we seen AI hit a worldwide viewers in methods which might be each terrifying and thrilling in equal measure. With know-how corresponding to AI prowling amongst us, we’re extraordinarily more likely to see inventive and slightly refined assaults happen with damaging outcomes.
Voice cloning escapade
My earlier roles within the police power instilled in me the mindset to aim to suppose like a felony. This method has some very tangible and but underappreciated advantages: the extra one thinks and even acts like a felony (with out really turning into one), the higher protected one may be. That is completely important in preserving updated with the newest threats in addition to foreseeing the developments to return.
So, to check a few of AI’s present skills, I’ve as soon as once more needed to tackle the mindset of a digital felony and ethically assault a enterprise!
I just lately requested a contact of mine – let’s name him Harry – if I might clone his voice and use it to assault his firm. Harry agreed and allowed me to start out the experiment by making a clone of his voice utilizing available software program. Fortunately for me, getting maintain of Harry’s voice was comparatively easy – he usually data quick movies selling his enterprise on his YouTube channel, so I used to be in a position to sew collectively a number of of those movies with a purpose to make a superb audio check mattress. Inside a couple of minutes, I had generated a clone of Harry’s voice, which sounded similar to him to me, and I used to be then in a position to write something and have it performed again in his voice.
To up the ante, I additionally determined so as to add authenticity to the assault by stealing Harry’s WhatsApp account with the assistance of a SIM swap assault – once more, with permission. I then despatched a voice message from his WhatsApp account to the monetary director of his firm – let’s name her Sally – requesting a £250 cost to a “new contractor”. On the time of the assault, I knew he was on a close-by island having a enterprise lunch, which gave me the right story and alternative to strike.
The voice message included the place he was and that he wanted the “flooring plan man” paid, and mentioned that he would ship the financial institution particulars individually straight after. This added the verification from the sound of his voice on prime of the voice message being added to Sally’s WhatsApp thread, which was sufficient to persuade her that the request was real. Inside 16 minutes of the preliminary message I had £250 despatched to my private account.
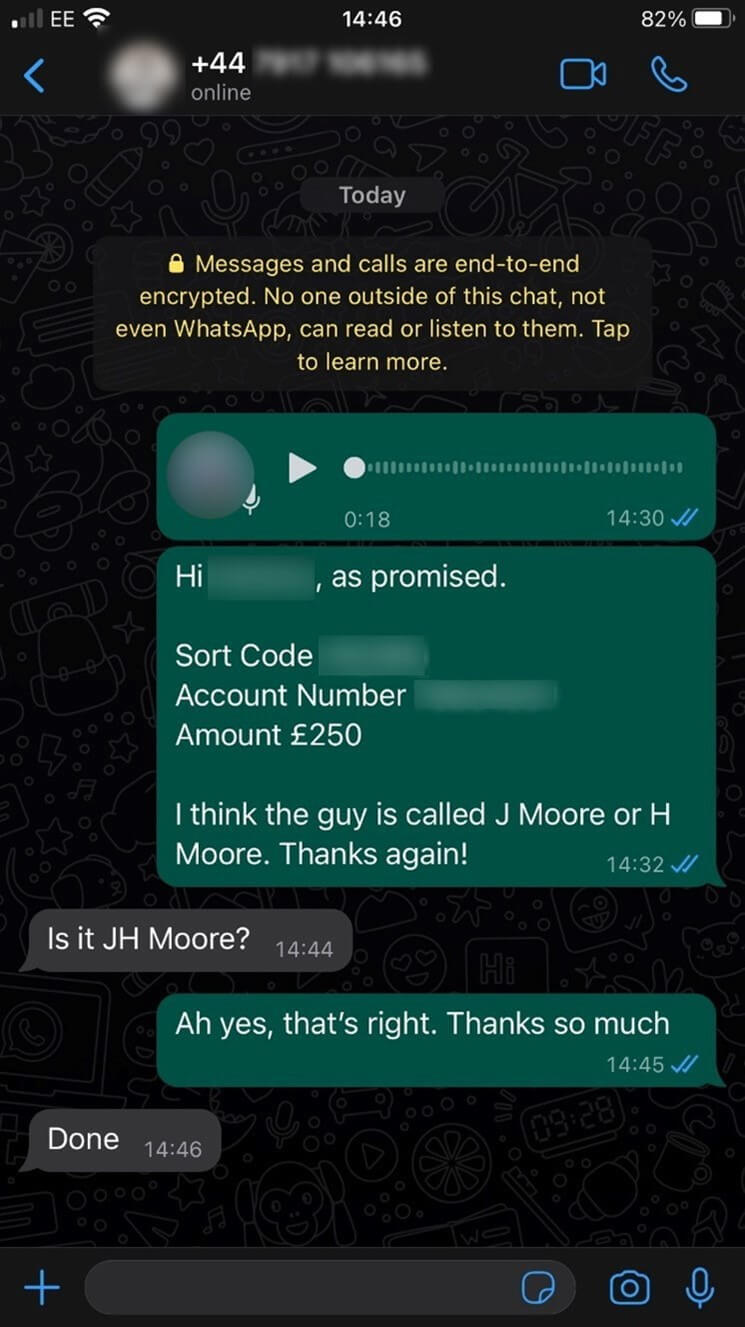
I have to admit I used to be shocked at how easy it was and the way shortly I used to be in a position to dupe Sally into being assured that Harry’s cloned voice was actual.
This stage of manipulation labored due to a compelling variety of related components:
- the CEO’s cellphone quantity verified him,
- the story I fabricated matched the day’s occasions, and
- the voice message, in fact, sounded just like the boss.
In my debrief with the corporate, and on reflection, Sally said she felt this was “greater than sufficient” verification wanted to hold out the request. For sure, the corporate has since added extra safeguards to maintain their funds protected. And, in fact, I refunded the £250!
WhatsApp Enterprise impersonation
Stealing somebody’s WhatsApp account by way of a SIM swap assault might be a slightly long-winded option to make an assault extra plausible, however it occurs way more generally than you may suppose. Nonetheless, cybercriminals don’t must go to such lengths to provide the identical end result.
For instance, I’ve just lately been focused with an assault that, on the face of it, regarded plausible. Somebody had despatched me a WhatsApp message purporting to be from a buddy of mine who’s an government at an IT firm.
The attention-grabbing dynamic right here was that though I’m used to verifying info, this message arrived with the linked contact identify as a substitute of it displaying up as a quantity. This was of particular curiosity, as a result of I didn’t have the quantity it got here from saved in my contacts listing and I assumed it will nonetheless present as a cellular quantity, slightly than the identify.
Apparently the way in which they finagled this was just by making a WhatsApp Enterprise account, which permits including any identify, picture and electronic mail deal with you need to an account and make it instantly look real. Add this to AI voice cloning and voila, now we have entered the subsequent technology of social engineering.
Thankfully, I knew this was a rip-off from the outset, however many individuals might fall for this straightforward trick that might finally result in the discharge of cash within the type of monetary transactions, pay as you go playing cards, or different playing cards corresponding to Apple Card, all of that are favorites amongst cyberthieves.
With machine studying and synthetic intelligence progressing by leaps and bounds and turning into more and more obtainable to the plenty just lately, we’re shifting into an age the place know-how is beginning to assist criminals extra effectively than ever earlier than, together with by bettering all the prevailing instruments that assist obfuscate the criminals’ identities and whereabouts.
Staying secure
Going again to our experiments, listed below are a number of primary precautions enterprise house owners ought to take to keep away from falling sufferer to assaults leveraging voice cloning and different shenanigans:
- Don’t take shortcuts in enterprise insurance policies
- Confirm folks and processes; e.g., doublecheck any cost requests with the particular person (allegedly) making the request and have as many transfers as doable signed off by two staff
- Maintain up to date on the newest developments in know-how and replace the coaching and defensive measures accordingly
- Conduct advert hoc consciousness coaching for all workers
- Use multi-layered safety software program
Listed here are a number of ideas for staying secure from SIM swap and different assaults that intention to separate you out of your private knowledge or cash:
- Restrict the non-public info you share on-line; if doable, keep away from posting particulars corresponding to your deal with or cellphone quantity
- Restrict the quantity of people that can see your posts or different materials on social media
- Be careful for phishing assaults and different makes an attempt luring you into offering your delicate private knowledge
- In case your cellphone supplier provides extra safety in your cellphone account, corresponding to a PIN code or passcode, make certain to make use of it
- Use two-factor authentication (2FA), particularly an authentication app or a {hardware} authentication gadget
Certainly, the significance of utilizing 2FA can’t be understated – make certain to allow it additionally in your WhatsApp account (the place it’s known as two-step verification) and every other on-line accounts that supply it.