UPDATE (November 13th, 2023): The web site has eliminated the “DOWNLOAD APP” button, though the malicious app continues to be hosted on its servers.
ESET researchers have recognized what seems to be a watering-hole assault on a regional information web site that delivers information about Gilgit-Baltistan, a disputed area administered by Pakistan. When opened on a cell system, the Urdu model of the Hunza Information web site provides readers the chance to obtain the Hunza Information Android app straight from the web site, however the app has malicious espionage capabilities. We named this beforehand unknown spyware and adware Kamran due to its bundle title com.kamran.hunzanews. Kamran is a standard given title in Pakistan and different Urdu-speaking areas; in Farsi, which is spoken by some minorities in Gilgit-Baltistan, it means lucky or fortunate.
The Hunza Information web site has English and Urdu variations; the English cell model doesn’t present any app for obtain. Nevertheless, the Urdu model on cell provides to obtain the Android spyware and adware. It’s value mentioning that each English and Urdu desktop variations additionally supply the Android spyware and adware; though, it isn’t suitable with desktop working techniques. We reached out to the web site regarding the Android malware. Nevertheless, previous to the publication of our blogpost, we didn’t obtain any response.
Key factors of the report:
- Android spyware and adware, which we named Kamran, has been distributed by way of a potential watering-hole assault on the Hunza Information web site.
- The malware targets solely Urdu-speaking customers in Gilgit-Baltistan, a area administered by Pakistan.
- The Kamran spyware and adware shows the content material of the Hunza Information web site and comprises customized malicious code.
- Our analysis reveals that a minimum of 20 cell units have been compromised.
Upon launching, the malicious app prompts the person to grant it permissions to entry varied knowledge. If accepted, it gathers knowledge about contacts, calendar occasions, name logs, location data, system recordsdata, SMS messages, pictures, and many others. As this malicious app has by no means been provided by the Google Play retailer and is downloaded from an unidentified supply known as Unknown by Google, to put in this app, the person is requested to allow the choice to put in apps from unknown sources.
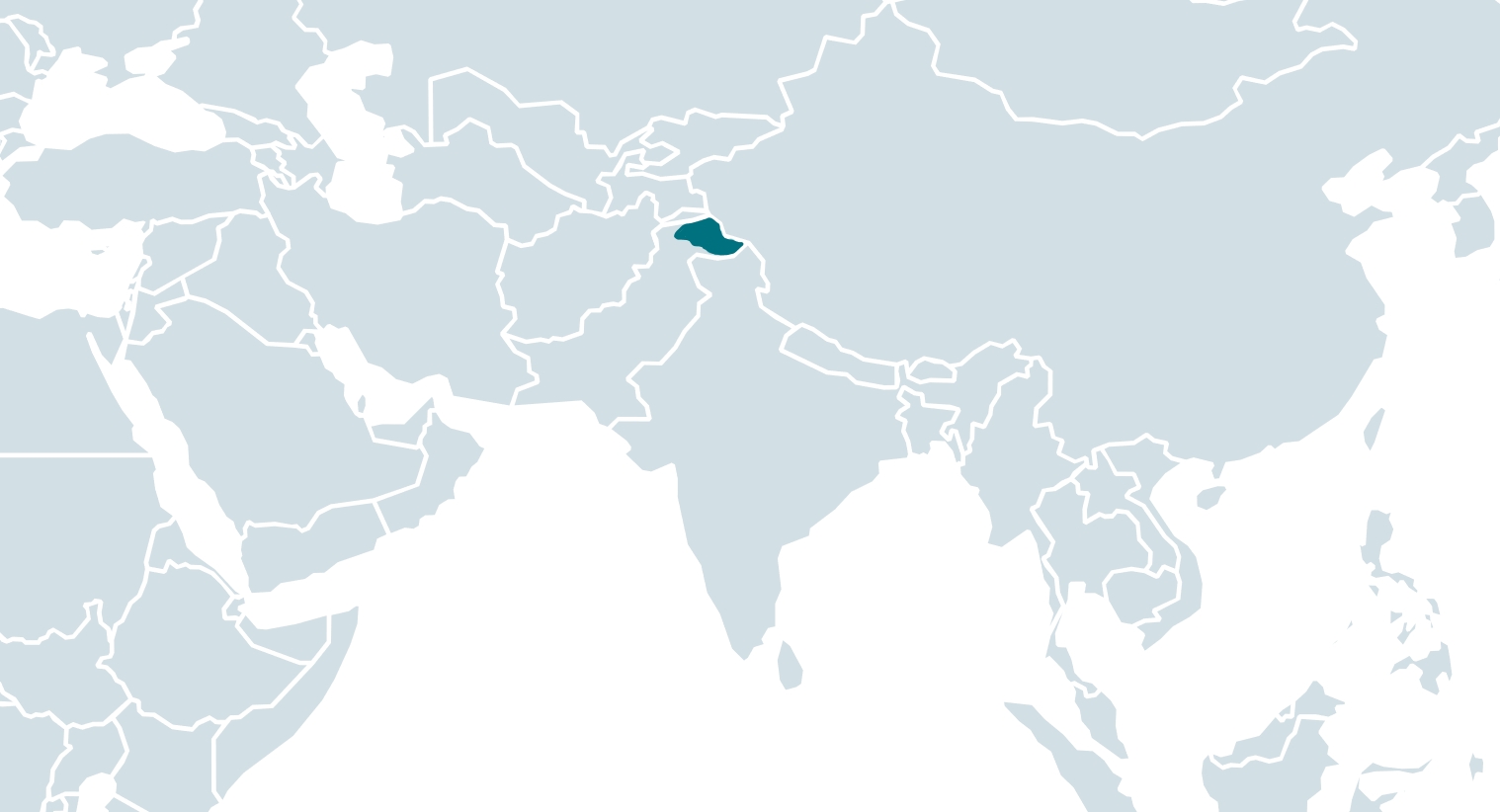
The malicious app appeared on the web site someday between January 7th, 2023, and March 21st, 2023; the developer certificates of the malicious app was issued on January 10, 2023. Throughout that point, protests have been being held in Gilgit-Baltistan for varied causes encompassing land rights, taxation considerations, extended energy outages, and a decline in backed wheat provisions. The area, proven within the map in Determine 1, is underneath Pakistan’s administrative governance, consisting of the northern portion of the bigger Kashmir area, which has been the topic of a dispute between India and Pakistan since 1947 and between India and China since 1959.
Overview
Hunza Information, doubtless named after the Hunza District or the Hunza Valley, is an internet newspaper delivering information associated to the Gilgit-Baltistan area.
The area, with a inhabitants of round 1.5 million, is known for the presence of among the highest mountains globally, internet hosting 5 of the esteemed “eight-thousanders” (mountains that peak at greater than 8,000 meters above sea stage), most notably K2, and is due to this fact regularly visited by worldwide vacationers, trekkers, and mountaineers. Due to the protests in spring 2023, and extra ones occurring in September 2023, the US and Canada have issued journey advisories for this area, and Germany steered vacationers ought to keep knowledgeable in regards to the present state of affairs.
Gilgit-Baltistan can be an essential crossroad due to the Karakoram Freeway, the one motorable highway connecting Pakistan and China, because it permits China to facilitate commerce and vitality transit by accessing the Arabian Sea. The Pakistani portion of the freeway is at present being reconstructed and upgraded; the efforts are financed by each Pakistan and China. The freeway is regularly blocked by harm brought on by climate or protests.
The Hunza Information web site offers content material in two languages: English and Urdu. Alongside English, Urdu holds nationwide language standing in Pakistan, and in Gilgit-Baltistan, it serves because the widespread or bridge language for interethnic communications. The official area of Hunza Information is hunzanews.internet, registered on Might 22nd, 2017, and has been constantly publishing on-line articles since then, as evidenced by Web Archive knowledge for hunzanews.internet.
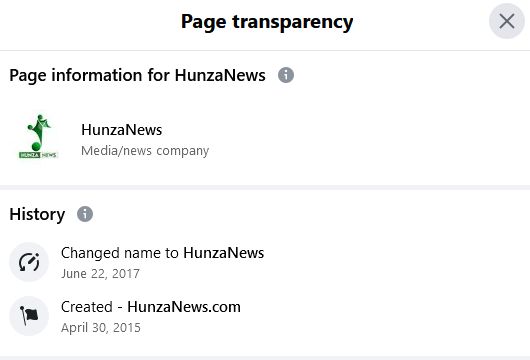
Previous to 2022, this on-line newspaper additionally used one other area, hunzanews.com, as indicated within the web page transparency data on the positioning’s Fb web page (see Determine 2) and the Web Archive information of hunzanews.com, Web Archive knowledge additionally reveals that hunzanews.com had been delivering information since 2013; due to this fact, for round 5 years, this on-line newspaper was publishing articles by way of two web sites: hunzanews.internet and hunzanews.com. This additionally implies that this on-line newspaper has been energetic and gaining on-line readership for over 10 years.
In 2015, hunzanews.com began to supply a legit Android utility, as proven in Determine 3, which was obtainable on the Google Play retailer. Based mostly on obtainable knowledge we consider two variations of this app have been launched, with neither containing any malicious performance. The aim of those apps was to current the web site content material to readers in a user-friendly method.
Within the second half of 2022, the brand new web site hunzanews.internet underwent visible updates, together with the removing of the choice to obtain the Android app from Google Play. Moreover, the official app was taken down from the Google Play retailer, doubtless as a result of its incompatibility with the newest Android working techniques.
For a number of weeks, from a minimum of December 2022 till January 7th, 2023, the web site offered no choice to obtain the official cell app, as proven in Determine 4.

Based mostly on Web Archive information, it’s evident that a minimum of since March 21st, 2023, the web site reintroduced the choice for customers to obtain an Android app, accessible by way of the DOWNLOAD APP button, as depicted in Determine 5. There is no such thing as a knowledge for the interval between January 7th and March 21st, 2023, which may assist us pinpoint the precise date of the app’s reappearance on the web site.

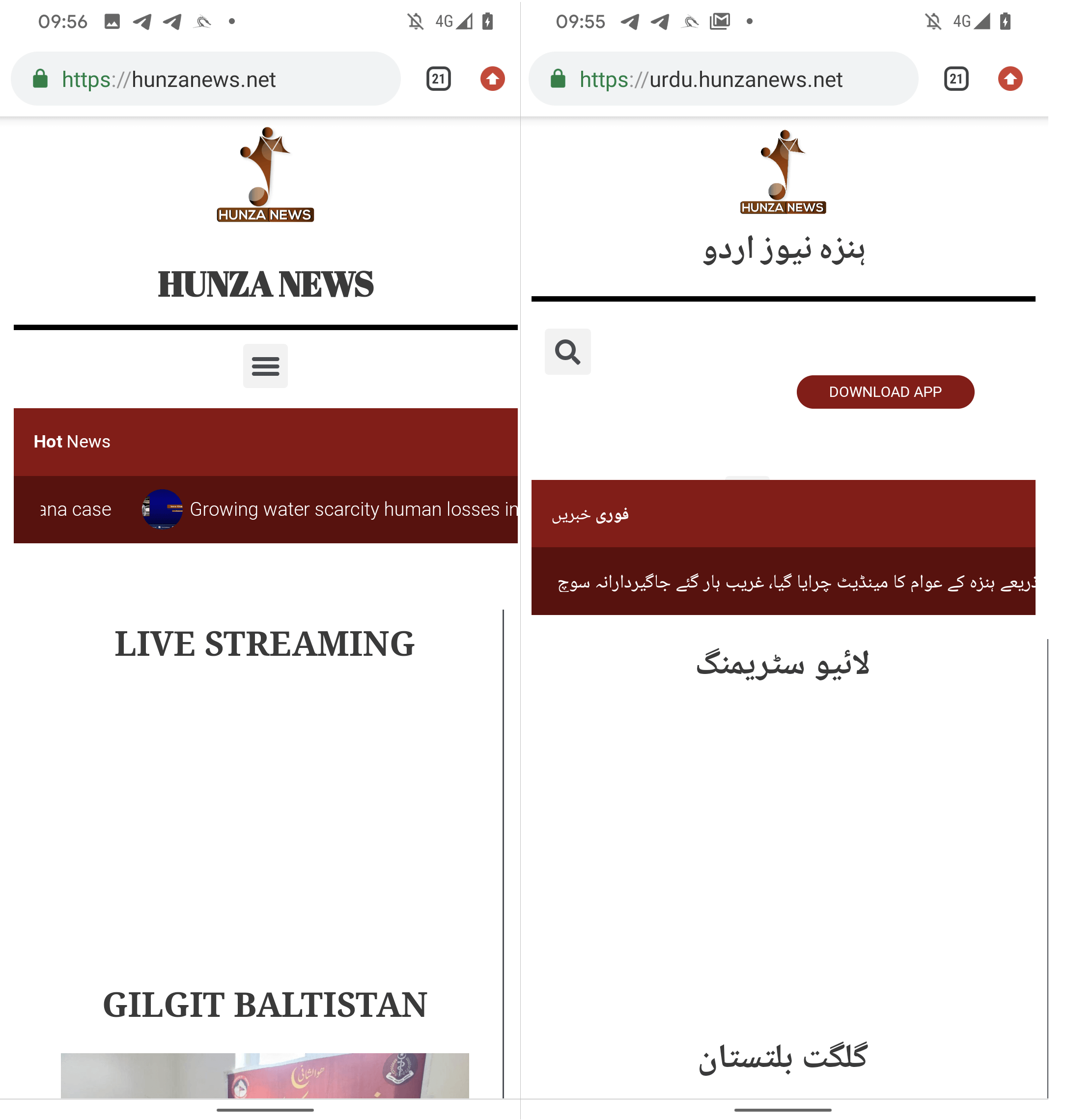
When analyzing a number of variations of the web site, we got here throughout one thing attention-grabbing: viewing the web site in a desktop browser in both language model of Hunza Information – English (hunzanews.internet) or Urdu (urdu.hunzanews.internet) – prominently shows the DOWNLOAD APP button on the high of the webpage. The downloaded app is a local Android utility which can’t be put in on a desktop machine and compromise it.
Nevertheless, on a cell system, this button is completely seen on the Urdu language variant (urdu.hunzanews.internet), as proven in Determine 6.
With a excessive diploma of confidence, we are able to affirm that the malicious app is particularly focused at Urdu-speaking customers who entry the web site by way of an Android system. The malicious app has been obtainable on the web site because the first quarter of 2023.
Clicking on the DOWNLOAD APP button triggers a obtain from https://hunzanews[.]internet/wp-content/uploads/apk/app-release.apk. As this malicious app has by no means been provided by the Google Play retailer and is downloaded from a third-party website to put in this app, the person is requested to allow the non-default, Android possibility to put in apps from unknown sources.
The malicious app, referred to as Hunza Information, is beforehand unknown spyware and adware that we named Kamran and that’s analyzed within the Kamran part under.
ESET Analysis reached out to Hunza Information relating to Kamran. Earlier than the publication of our blogpost we didn’t obtain any type of suggestions or response from the web site’s aspect.
Victimology
Based mostly on the findings from our analysis, we have been in a position to establish a minimum of 22 compromised smartphones, with 5 of them being situated in Pakistan.
Kamran
Kamran is beforehand undocumented Android spyware and adware characterised by its distinctive code composition, distinct from different, identified spyware and adware. ESET detects this spyware and adware as Android/Spy.Kamran.
We recognized just one model of a malicious app containing Kamran, which is the one obtainable to obtain from the Hunza Information web site. As defined within the Overview part, we’re unable to specify the precise date on which the app was positioned on the Hunza Information web site. Nevertheless, the related developer certificates (SHA-1 fingerprint: DCC1A353A178ABF4F441A5587E15644A388C9D9C), used to signal the Android app, was issued on January 10th, 2023. This date offers a ground for the earliest time that the malicious app was constructed.
In distinction, legit purposes from Hunza Information that have been previously obtainable on Google Play have been signed with a special developer certificates (SHA-1 fingerprint: BC2B7C4DF3B895BE4C7378D056792664FCEEC591). These clear and legit apps exhibit no code similarities with the recognized malicious app.
Upon launching, Kamran prompts the person to grant permissions for accessing varied knowledge saved on the sufferer’s system, corresponding to contacts, calendar occasions, name logs, location data, system recordsdata, SMS messages, and pictures. It additionally presents a person interface window, providing choices to go to Hunza Information social media accounts, and to pick out both the English or Urdu language for loading the contents of hunzanews.internet, as proven in Determine 7.
If the abovementioned permissions are granted, the Kamran spyware and adware robotically gathers delicate person knowledge, together with:
- SMS messages
- contacts record
- name logs
- calendar occasions
- system location
- record of put in apps
- acquired SMS messages
- system data
- pictures
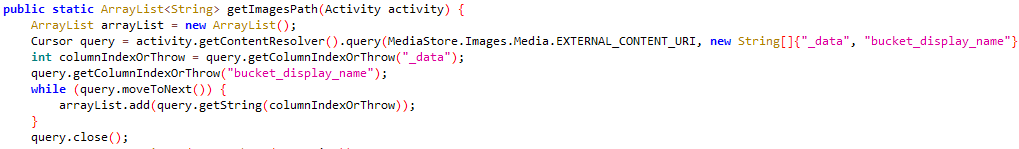
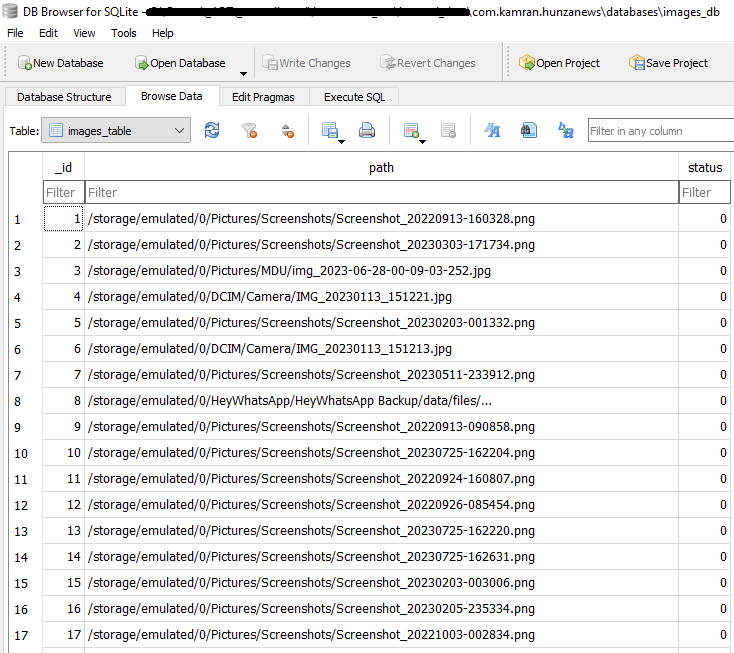
Apparently, Kamran identifies accessible picture recordsdata on the system (as depicted in Determine 8), obtains the file paths for these pictures, and shops this knowledge in an images_db database, as demonstrated in Determine 9. This database is saved within the malware’s inner storage.
All varieties of knowledge, together with the picture recordsdata, are uploaded to a hardcoded command and management (C&C) server. Apparently, the operators opted to make the most of Firebase, an online platform, as their C&C server: https://[REDACTED].firebaseio[.]com. The C&C server was reported to Google, because the platform is offered by this expertise firm.
You will need to observe that the malware lacks distant management capabilities. Because of this, person knowledge is exfiltrated by way of HTTPS to the Firebase C&C server solely when the person opens the app; knowledge exfiltration can not run within the background when the app is closed. Kamran has no mechanism monitoring what knowledge has been exfiltrated, so it repeatedly sends the identical knowledge, plus any new knowledge assembly its search standards, to its C&C.
Conclusion
Kamran is beforehand unknown Android spyware and adware focusing on Urdu-speaking folks within the Gilgit-Baltistan area. Our analysis signifies that the malicious app containing Kamran has been distributed since a minimum of 2023 by way of what most likely is a watering-hole assault on a neighborhood, on-line newspaper named Hunza Information.
Kamran demonstrates a novel codebase distinct from different Android spyware and adware, stopping its attribution to any identified superior persistent menace (APT) group.
This analysis additionally reveals that you will need to reiterate the importance of downloading apps completely from trusted and official sources.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis provides personal APT intelligence studies and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
Information
|
SHA-1 |
Package deal title |
Detection |
Description |
|
0F0259F288141EDBE4AB2B8032911C69E03817D2 |
com.kamran.hunzanews |
Android/Spy.Kamran.A |
Kamran spyware and adware. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
34.120.160[.]131 |
[REDACTED].firebaseio[.]com |
Google LLC |
2023-07-26 |
C&C server. |
|
191.101.13[.]235 |
hunzanews[.]internet |
Area.com, LLC |
2017-05-22 |
Distribution web site. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 13 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Discovery |
Software program Discovery |
Kamran spyware and adware can get hold of an inventory of put in purposes. |
|
|
File and Listing Discovery |
Kamran spyware and adware can record picture recordsdata on exterior storage. |
||
|
System Data Discovery |
Kamran spyware and adware can extract details about the system, together with system mannequin, OS model, and customary system data. |
||
|
Assortment |
Knowledge from Native System |
Kamran spyware and adware can exfiltrate picture recordsdata from a tool. |
|
|
Location Monitoring |
Kamran spyware and adware tracks system location. |
||
|
Protected Person Knowledge: Calendar Entries |
Kamran spyware and adware can extract calendar entries. |
||
|
Protected Person Knowledge: Name Logs |
Kamran spyware and adware can extract name logs. |
||
|
Protected Person Knowledge: Contact Checklist |
Kamran spyware and adware can extract the system’s contact record. |
||
|
Protected Person Knowledge: SMS Messages |
Kamran spyware and adware can extract SMS messages and intercept acquired SMS. |
||
|
Command and Management |
Software Layer Protocol: Internet Protocols |
Kamran spyware and adware makes use of HTTPS to speak with its C&C server. |
|
|
Internet Service: One-Manner Communication |
Kamran makes use of Google’s Firebase server as its C&C server. |
||
|
Exfiltration |
Exfiltration Over C2 Channel |
Kamran spyware and adware exfiltrates knowledge utilizing HTTPS. |

