In 2020, america introduced costs in opposition to 4 males accused of constructing a bulletproof internet hosting empire that after dominated the Russian cybercrime trade and supported a number of organized cybercrime teams. All 4 pleaded responsible to conspiracy and racketeering costs. However there’s a fascinating and untold backstory behind the 2 Russian males concerned, who co-ran the world’s high spam discussion board and labored intently with Russia’s most harmful cybercriminals.
From January 2005 to April 2013, there have been two main directors of the cybercrime discussion board Spamdot (a.okay.a Spamit), an invite-only group for Russian-speaking individuals within the companies of sending spam and constructing botnets of contaminated computer systems to relay mentioned spam. The Spamdot admins glided by the nicknames Icamis (a.okay.a. Ika), and Salomon (a.okay.a. Sal).
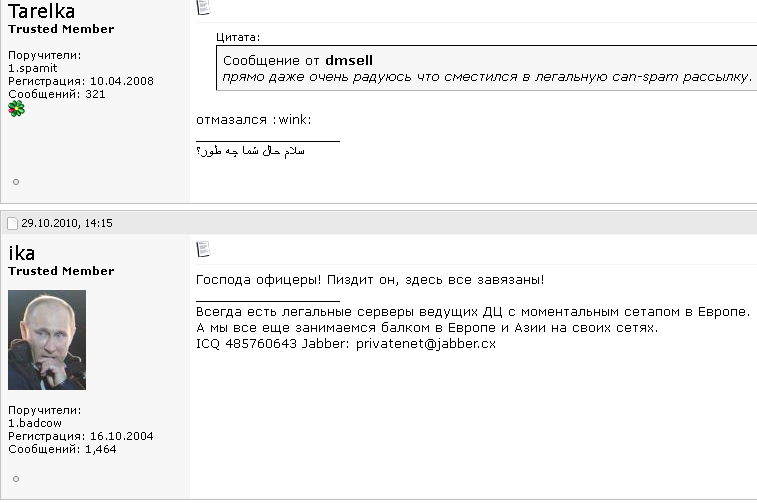
Spamdot discussion board administrator “Ika” a.okay.a. “Icamis” responds to a message from “Tarelka,” the botmaster behind the Rustock botnet. Dmsell mentioned: “I’m truly very glad that I switched to authorized spam mailing,” prompting Tarelka and Ika to scoff.
As detailed in my 2014 ebook, Spam Nation, Spamdot was residence to crooks controlling a number of the world’s nastiest botnets, international malware contagions that glided by unique names like Rustock, Cutwail, Mega-D, Festi, Waledac, and Grum.
Icamis and Sal had been in each day communications with these botmasters, through the Spamdot discussion board and personal messages. Collectively in management over hundreds of thousands of spam-spewing zombies, these botmasters additionally repeatedly harvested passwords and different information from contaminated machines.
As we’ll see in a second, Salomon is now behind bars, partially as a result of he helped to rob dozens of small companies in america utilizing a few of those self same harvested passwords. He’s at present housed in a federal jail in Michigan, serving the ultimate stretch of a 60-month sentence.
However the identification and whereabouts of Icamis have remained a thriller to this writer till just lately. For years, safety consultants — and certainly, many high cybercriminals within the Spamit associates program — have expressed the idea that Sal and Icamis had been probably the identical individual utilizing two completely different identities. And there have been many good causes to help this conclusion.
For instance, in 2010 Spamdot and its spam associates program Spamit had been hacked, and its consumer database exhibits Sal and Icamis usually accessed the discussion board from the identical Web deal with — normally from Cherepovets, an industrial city located roughly 230 miles north of Moscow. Additionally, it was frequent for Icamis to answer when Spamdot members communicated a request or grievance to Sal, and vice versa.
Picture: maps.google.com
Nonetheless, different clues instructed Icamis and Sal had been two separate people. For starters, they continuously modified the standing on their on the spot messenger shoppers at completely different occasions. Additionally, they every privately mentioned with others having attended completely different universities.
KrebsOnSecurity started researching Icamis’s real-life identification in 2012, however didn’t revisit any of that analysis till just lately. In December 2023, KrebsOnSecurity revealed new particulars in regards to the identification of “Rescator,” a Russian cybercriminal who’s considered intently linked to the 2013 information breach at Goal.
That story talked about Rescator’s real-life identification was uncovered by Icamis in April 2013, as a part of a prolonged farewell letter Ika wrote to Spamdot members whereby Ika mentioned he was closing the discussion board and quitting the cybercrime enterprise solely.
To nobody’s shock, Icamis didn’t give up the enterprise: He merely turned extra quiet and circumspect about his work, which more and more was centered on serving to crime teams siphon funds from U.S. financial institution accounts. However the Rescator story was a reminder that 10 years price of analysis on who Ika/Icamis is in actual life had been fully put aside. This publish is an try and treatment that omission.
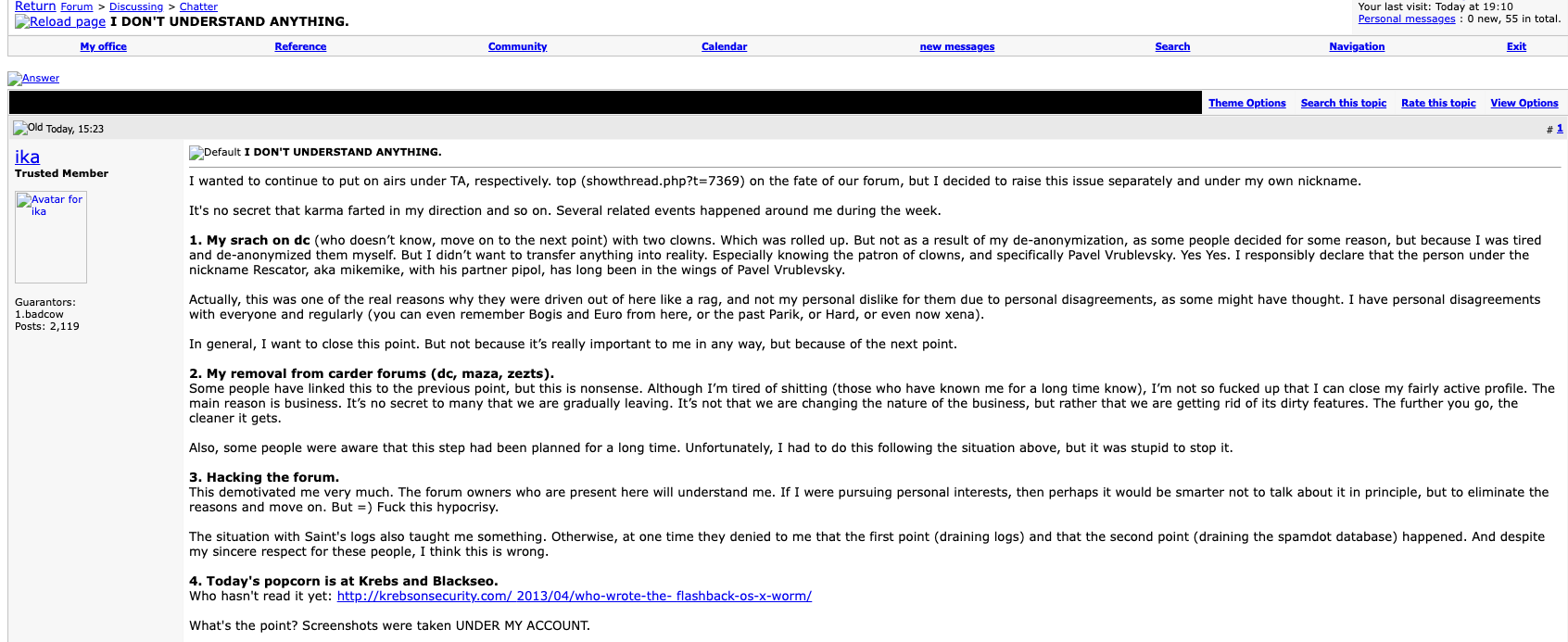
The farewell publish from Ika (aka Icamis), the administrator of each the BlackSEO discussion board and Pustota, the successor discussion board to Spamit/Spamdot.
GENTLEMEN SCAMMERS
Icamis and Sal supplied a complete package deal of products and providers that any aspiring or achieved spammer would want on a day-to-day foundation: Nearly limitless bulletproof area registration and internet hosting providers, in addition to providers that helped botmasters evade spam block lists generated by anti-spam teams like Spamhaus.org. Right here’s snippet of Icamis’s advert on Spamdot from Aug. 2008, whereby he addresses discussion board members with the salutation, “Hi there Gents Scammers.”
We’re glad to current you our providers!
Many are already conscious (and are our shoppers), however publicity is rarely superfluous. 🙂Domains.
– all main gtlds (com, internet, org, data, biz)
– many attention-grabbing and uninteresting cctlds
– choices for any matter
– processing of any portions
– ensures
– exceptionally low costs for domains for white and grey schemes (together with any web optimization and affiliate spam )
– management panel with balances and auto-registration
– all providers underneath the Ikamis model, confirmed over time;)Servers.
– long-term partnerships with a number of [data centers] in a number of elements of the world for any matter
– your individual information heart (now not in Russia ;)) for grey and white matters
– any configuration and any {hardware}
– your individual IP networks (PI, not PA) and full authorized help
– realtime backups to impartial websites
– ensures and full duty for the providers offered
– non-standard tools on request
– our personal admins to resolve any technical points (providers are free for shoppers)
– internet hosting (shared and vps) can also be attainableNon-standard and associated providers.
– ssl certificates signed by geotrust and thawte
– previous domains (any 12 months, any amount)
– lovely domains (key phrase, brief, and so forth.)
– domains with indicators (any, for web optimization, and so forth.)
– making unstable gtld domains steady
– interception and hijacking of customized domains (costly)
– full area posting through net.archive.org with restoration of native content material (preliminary purposes)
– any updates to our panels to fit your wants upon request (our personal coders)All orders for the “Domains” sections and “Servers” are carried out throughout the day (relying on our workload).
For non-standard and associated providers, a preliminary software is required 30 days prematurely (aside from ssl certificates – inside 24 hours).
Icamis and Sal continuously claimed that their service saved Spamhaus and different anti-spam teams a number of steps behind their operations. Nevertheless it’s clear that these anti-spam operations had an actual and painful impression on spam revenues, and Salomon was obsessive about putting again at anti-spam teams, significantly Spamhaus.
In 2007, Salomon collected greater than $3,000 from botmasters affiliated with competing spam affiliate packages that wished to see Spamhaus endure, and the cash was used to fund a week-long distributed denial-of-service (DDoS) assault in opposition to Spamhaus and its on-line infrastructure. However quite than divert their spam botnets from their regular exercise and thereby lower gross sales, the botmasters voted to create a brand new DDoS botnet by buying installations of DDoS malware on 1000’s of already-hacked PCs (at a price of $25 per 1,000 installs).
SALOMON
As an affiliate of Spamdot, Salomon used the e-mail deal with ad1@safe-mail.internet, and the password 19871987gr. The breach monitoring service Constella Intelligence discovered the password 19871987gr was utilized by the e-mail deal with grichishkin@gmail.com. A number of accounts are registered to that e mail deal with underneath the title Alexander Valerievich Grichishkin, from Cherepovets.
In 2020, Grichishkin was arrested outdoors of Russia on a warrant for offering bulletproof internet hosting providers to cybercriminal gangs. The U.S. authorities mentioned Grichishkin and three others arrange the infrastructure utilized by cybercriminals between 2009 to 2015 to distribute malware and assault monetary establishments and victims all through america.
These shoppers included crooks utilizing malware like Zeus, SpyEye, Citadel and the Blackhole exploit equipment to construct botnets and steal banking credentials.
“The Group and its members helped their shoppers to entry computer systems with out authorization, steal monetary info (together with banking credentials), and provoke unauthorized wire transfers from victims’ monetary accounts,” the federal government’s grievance acknowledged.
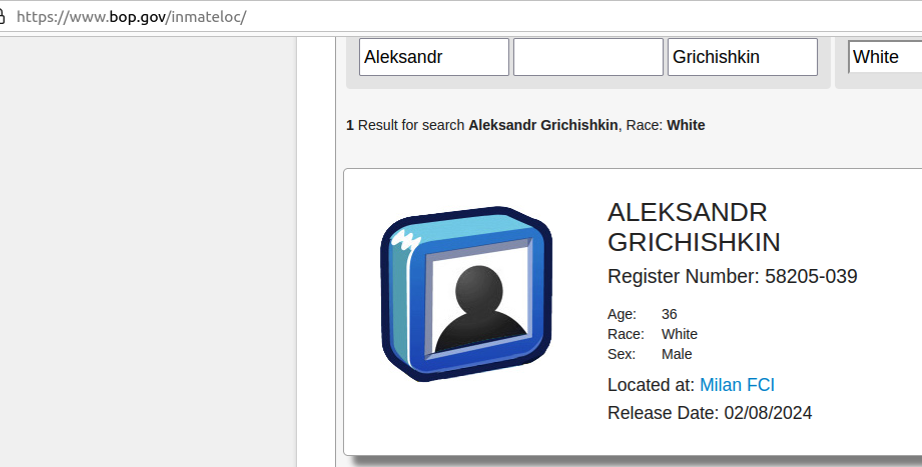
Grichishkin pleaded responsible to conspiracy costs and was sentenced to 4 years in jail. He’s 36 years previous, has a spouse and youngsters in Thailand, and is slated for launch on February 8, 2024.
ICAMIS, THE PHANTOM GRADUATE
The identification of Icamis got here into view when KrebsOnSecurity started specializing in clues which may join Icamis to Cherepovets (Ika’s obvious hometown primarily based on the Web addresses he frequently used to entry Spamdot).
Historic area possession data from DomainTools.com reveal that most of the e mail addresses and domains linked to Icamis invoke the title “Andrew Artz,” together with icamis[.]ws, icamis[.]ru, and icamis[.]biz. Icamis promoted his providers in 2003 — resembling bulk-domains[.]data — utilizing the e-mail deal with icamis@4host.data. From one in all his advertisements in 2005:
Domains For Tasks Marketed By Spam
I can register bulletproof domains for websites and initiatives marketed by spam(in fact they have to be authorized). I can’t present DNS for u, solely domains. The value might be:
65$ for area[if u will buy less than 5 domains]
50$ for area[more than 5 domains]
45$ for area[more than 10 domains]
These costs are for domains within the .internet & .com zones.
If u wish to order domains write me to: icamis@4host.data
In 2009, an “Andrew Artz” registered on the internet hosting service FirstVDS.com utilizing the e-mail deal with icamis@4host.data, with a notation saying the corporate title connected to the account was “WMPay.” Likewise, the bulletproof area service icamis[.]ws was registered to an Andrew Artz.
The area wmpay.ru is registered to the phonetically comparable title “Andrew Hertz,” at andrew@wmpay.ru. A search on “icamis.ru” in Google brings up a 2003 publish by him on a dialogue discussion board designed by and for college kids of Amtek, a secondary college in Cherepovets (Icamis was commenting from an Web deal with in Cherepovets).
The web site amtek-foreva-narod.ru continues to be on-line, and it hyperlinks to a number of yearbooks for Amtek graduates. It states that the yearbook for the Amtek class of 2004 is hosted at 41.wmpay[.]com.
The yearbook images for the Amtek class of 2004 are usually not listed within the Wayback Machine at archive.org, however the names and nicknames of 16 college students stay. Nevertheless, it seems that the entry for one scholar — the Wmpay[.]com website administrator — was eliminated sooner or later.
In 2004, the administrator of the Amtek dialogue discussion board — a 2003 graduate who used the deal with “Grand” — noticed that there have been three individuals named Andrey who graduated from Amtek in 2004, however one in all them was conspicuously absent from the yearbook at wmpay[.]ru: Andrey Skvortsov.
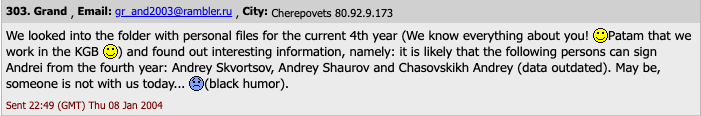
To deliver this full circle, Icamis was Andrey Skvortsov, the opposite Russian man charged alongside Grichiskin (the 2 others who pleaded responsible to conspiracy costs had been from Estonia and Lithuania). The entire defendants in that case pleaded responsible to conspiracy to have interaction in a Racketeer Influenced Corrupt Group (RICO).
[Author’s note: No doubt government prosecutors had their own reasons for omitting the nicknames of the defendants in their press releases, but that information sure would have saved me a lot of time and effort].
SKVORTSOV AND THE JABBERZEUS CREW
Skvortsov was sentenced to time served, and presumably deported. His present whereabouts are unknown and he was not reachable for remark through his identified contact addresses.
The federal government says Ika and Sal’s bulletproof internet hosting empire offered intensive help for a extremely damaging cybercrime group often called the JabberZeus Crew, which labored intently with the writer of the Zeus Trojan — Evgeniy Mikhailovich Bogachev — to develop a then-advanced pressure of the Zeus malware that was designed to defeat one-time codes for authentication. Bogachev is a high Russian cybercriminal with a standing $3 million bounty on his head from the FBI.
The JabberZeus Crew stole cash by continuously recruiting cash mules, individuals in america and in Europe who may very well be enticed or tricked into forwarding cash stolen from cybercrime victims. Curiously, Icamis’s varied e mail addresses are linked to web sites for an unlimited community of phony know-how corporations that claimed they wanted individuals with financial institution accounts to assist pay their abroad workers.
Icamis used the e-mail deal with tech@safe-mail.internet on Spamdot, and this e mail deal with is tied to the registration data for a number of phony know-how corporations that had been set as much as recruit cash mules.
One such website — sun-technology[.]internet — marketed itself as a Hong Kong-based electronics agency that was on the lookout for “sincere, accountable and motivated individuals in UK, USA, AU and NZ to be Gross sales Representatives in your specific area and obtain funds from our shoppers. Agent fee is 5 % of whole quantity acquired to the non-public checking account. It’s possible you’ll use your present checking account or open a brand new one for these functions.”
In January 2010, KrebsOnSecurity broke the information that the JabberZeus crew had simply used cash mules to steal $500,000 from tiny Duanesburg Central Faculty District in upstate New York. As a part of his sentence, Skvortsov was ordered to pay $497,200 in restitution to the Duanesburg Central Faculty District.
The JabberZeus Crew operated primarily out of the japanese Ukraine metropolis of Donetsk, which was all the time pro-Russia and is now occupied by Russian forces. However when Russia invaded Ukraine in February 2022, the alleged chief of the infamous cybercrime gang — Vyacheslav Igoravich Andreev (a.ka. Penchukov) — fled his necessary army service orders and was arrested in Geneva, Switzerland. He’s at present in federal custody awaiting trial, and is slated to be arraigned in U.S. federal court docket tomorrow (Jan. 9, 2024). A replica of the indictment in opposition to Andreev is right here (PDF).

Andreev, aka “Tank,” seen right here performing as a DJ in Ukraine in an undated photograph from social media.
