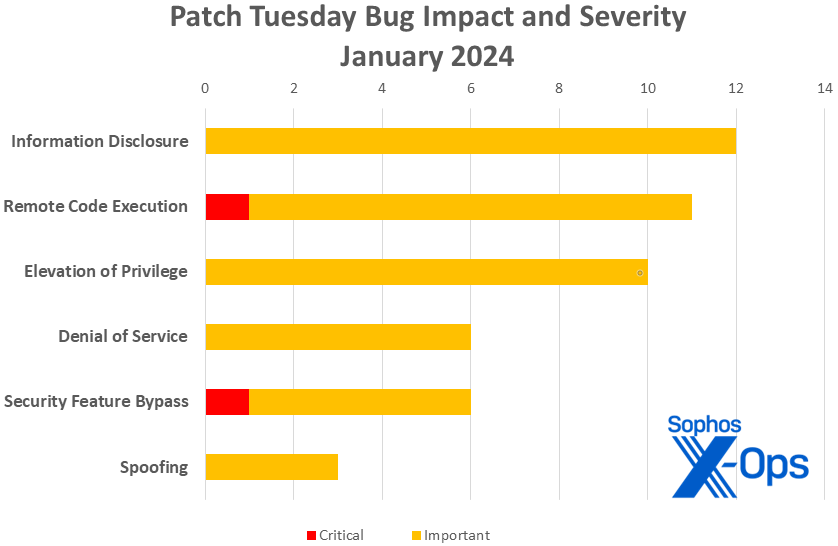
- Info Disclosure: 12
- Distant Code Execution: 11
- Elevation of Privilege: 10
- Denial of Service: 6
- Safety Characteristic Bypass: 6
- Spoofing: 3
Determine 1: You’re studying the labels appropriately: Info-disclosure points outnumber each EoP and RCE bugs in January. Safety characteristic bypass points – considered one of them Crucial-severity — additionally make a robust exhibiting
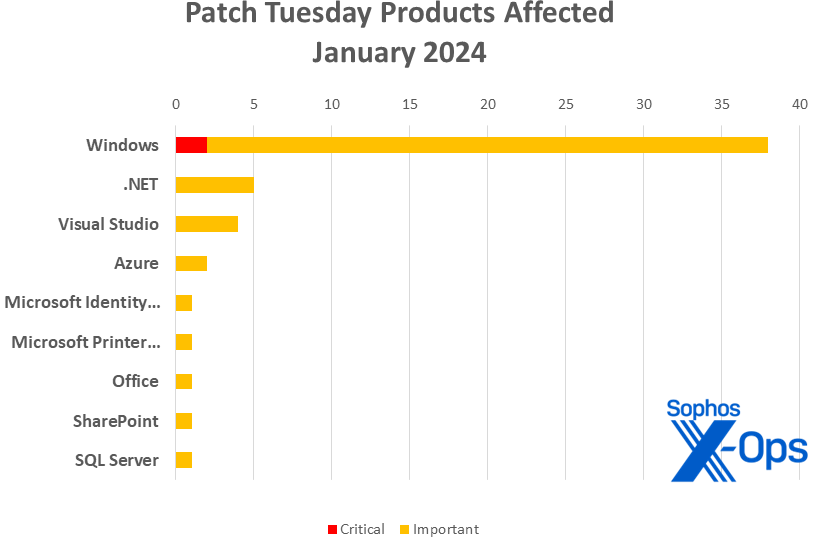
Merchandise
- Home windows: 38
- .NET: 5 (together with on shared with Visible Studio; one shared with Microsoft Id Mannequin / NuGet and Visible Studio; and one shared with Azure, SQL Server, and Visible Studio)
- Visible Studio: 4 (together with one shared with .NET; one shared with .NET and Microsoft Id Mannequin / NuGet; and one shared with .NET, Azure, and SQL Server)
- Azure: 2 (together with one shared with .NET, SQL Server, and Visible Studio)
- Microsoft Id Mannequin / NuGet: 1 (shared with .NET and Visible Studio)
- Microsoft Printer Metadata Troubleshooter Software: 1
- Workplace: 1
- SharePoint: 1
- SQL Server: 1 (shared with .NET, Azure, and Visible Studio)
Determine 2: Home windows is closely represented on this month’s patches, however a number of less-familiar instruments and functions are additionally within the combine (full names proven in tables beneath)
Notable January updates
Along with the problems mentioned above, a couple of particular objects are value noting.
CVE-2024-0057 — .NET, .NET Framework, and Visible Studio Framework Safety Characteristic Bypass Vulnerability
CVE-2024-20674 — Home windows Kerberos Safety Characteristic Bypass Vulnerability
Of this pair of safety characteristic bypass points, Microsoft deems solely the Kerberos difficulty to be Crucial-class. The CVSS scoring system begs to vary, because the information to that scoring system requires that scorers take into account possible worst-case eventualities when evaluating bugs in software program libraries. Their CVSS base scores are thus 9.1 and 9.0 respectively. In any case, admins are inspired to prioritize these two patches.
CVE-2024-20696 – Home windows Libarchive Distant Code Execution Vulnerability
CVE-2024-20697 – Home windows Libarchive Distant Code Execution Vulnerability
The data out there on these two identically named Vital-class RCEs is scant, however there’s a giant clue to their significance within the title: These two points have an effect on Libarchive, the engine for studying and writing in numerous compression and archive codecs.
CVE-2024-20666 – BitLocker Safety Characteristic Bypass Vulnerability
One other safety characteristic bypass, this time in a safety characteristic. This difficulty stands out for some pretty nuanced necessities round servicing the Protected OS; for many variations of Home windows 11 that is now a totally automated course of, and people counting on WSUS are routinely up to date, however these working in additional advanced environments are strongly inspired to test Microsoft’s printed steering for particular directions. In any case, the attacker requires bodily entry to the focused machine.
CVE-2024-21305 — Hypervisor-Protected Code Integrity (HVCI) Safety Characteristic Bypass Vulnerability
The CVE with the bottom CVSS base rating this month has one thing in widespread with the 2 highest-scoring CVEs: It’s one more safety characteristic bypass. This one, nevertheless, charges a mere 4.4 base rating and requires the attacker to have bodily entry to the focused machine and to have beforehand compromised admin credentials. It impacts an assortment of Home windows shopper and server variations and, for these nonetheless operating that {hardware}, 15 variations of the Floor.
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-20653 | Exp/2420653-A | Exp/2420653-A |
| CVE-2024-20698 | Exp/2420698-A | Exp/2420698-A |
| CVE-2024-21307 | Exp/2421307-A | Exp/2421307-A |
| CVE-2024-21310 | Exp/2421310-A | Exp/2421310-A |
As you may each month, for those who don’t need to wait in your system to tug down Microsoft’s updates itself, you may obtain them manually from the Home windows Replace Catalog web site. Run the winver.exe instrument to find out which construct of Home windows 10 or 11 you’re operating, then obtain the Cumulative Replace bundle in your particular system’s structure and construct quantity.
Appendix A: Vulnerability Affect and Severity
It is a record of January patches sorted by impression, then sub-sorted by severity. Every record is additional organized by CVE.
Info Disclosure (12 CVEs)
| Vital severity | |
| CVE-2024-0056 | Microsoft.Knowledge.SqlClient and System.Knowledge.SqlClient SQL Knowledge Supplier Info Disclosure Vulnerability |
| CVE-2024-20660 | Home windows Message Queuing Shopper Info Disclosure Vulnerability |
| CVE-2024-20662 | Home windows On-line Certificates Standing Protocol (OCSP) Info Disclosure Vulnerability |
| CVE-2024-20663 | Home windows Message Queuing Shopper (MSMQC) Info Disclosure |
| CVE-2024-20664 | Microsoft Message Queuing Shopper Info Disclosure Vulnerability |
| CVE-2024-20680 | Home windows Message Queuing Shopper (MSMQC) Info Disclosure |
| CVE-2024-20691 | Home windows Themes Info Disclosure Vulnerability |
| CVE-2024-20692 | Microsoft Native Safety Authority Subsystem Service Info Disclosure Vulnerability |
| CVE-2024-20694 | Home windows CoreMessaging Info Disclosure Vulnerability |
| CVE-2024-21311 | Home windows Cryptographic Providers Info Disclosure Vulnerability |
| CVE-2024-21313 | Home windows TCP/IP Info Disclosure Vulnerability |
| CVE-2024-21314 | Home windows Message Queuing Shopper (MSMQC) Info Disclosure |
Distant Code Execution (11 CVEs)
| Crucial severity | |
| CVE-2024-20700 | Home windows Hyper-V Distant Code Execution Vulnerability |
| Vital severity | |
| CVE-2024-20654 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-20655 | Microsoft On-line Certificates Standing Protocol (OCSP) Distant Code Execution Vulnerability |
| CVE-2024-20676 | Azure Storage Mover Distant Code Execution Vulnerability |
| CVE-2024-20677 | Microsoft Workplace Distant Code Execution Vulnerability |
| CVE-2024-20682 | Home windows Cryptographic Providers Distant Code Execution Vulnerability |
| CVE-2024-20696 | Home windows Libarchive Distant Code Execution Vulnerability |
| CVE-2024-20697 | Home windows Libarchive Distant Code Execution Vulnerability |
| CVE-2024-21307 | Distant Desktop Shopper Distant Code Execution Vulnerability |
| CVE-2024-21318 | Microsoft SharePoint Server Distant Code Execution Vulnerability |
| CVE-2024-21325 | Microsoft Printer Metadata Troubleshooter Software Distant Code Execution Vulnerability |
Elevation of Privilege (10 CVEs)
| Vital severity | |
| CVE-2024-20653 | Microsoft Widespread Log File System Elevation of Privilege Vulnerability |
| CVE-2024-20656 | Visible Studio Elevation of Privilege Vulnerability |
| CVE-2024-20657 | Home windows Group Coverage Elevation of Privilege Vulnerability |
| CVE-2024-20658 | Microsoft Digital Exhausting Disk Elevation of Privilege Vulnerability |
| CVE-2024-20681 | Home windows Subsystem for Linux Elevation of Privilege Vulnerability |
| CVE-2024-20683 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-20686 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-20698 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21309 | Home windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-21310 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
Denial of Service (6 CVEs)
| Vital severity | |
| CVE-2024-20661 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2024-20672 | .NET Core and Visible Studio Denial of Service Vulnerability |
| CVE-2024-20687 | Microsoft AllJoyn API Denial of Service Vulnerability |
| CVE-2024-20699 | Home windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-21312 | .NET Framework Denial of Service Vulnerability |
| CVE-2024-21319 | Microsoft Id Denial of Service Vulnerability |
Safety Characteristic Bypass (6 CVEs)
| Crucial severity | |
| CVE-2024-20674 | Home windows Kerberos Safety Characteristic Bypass Vulnerability |
| Vital Severity | |
| CVE-2024-0057 | .NET, .NET Framework, and Visible Studio Framework Safety Characteristic Bypass Vulnerability |
| CVE-2024-20652 | Home windows HTML Platforms Safety Characteristic Bypass Vulnerability |
| CVE-2024-20666 | BitLocker Safety Characteristic Bypass Vulnerability |
| CVE-2024-21305 | Hypervisor-Protected Code Integrity (HVCI) Safety Characteristic Bypass Vulnerability |
| CVE-2024-21316 | Home windows Server Key Distribution Service Safety Characteristic Bypass |
Spoofing (3 CVEs)
| Vital severity | |
| CVE-2024-20690 | Home windows Close by Sharing Spoofing Vulnerability |
| CVE-2024-21306 | Microsoft Bluetooth Driver Spoofing Vulnerability |
| CVE-2024-21320 | Home windows Themes Spoofing Vulnerability |
Appendix B: Exploitability
It is a record of the January CVEs judged by Microsoft to be extra more likely to be exploited within the wild throughout the first 30 days post-release. Every record is additional organized by CVE. No CVEs addressed within the January patch assortment are recognized to be underneath lively exploit within the wild but.
| Exploitation extra doubtless inside 30 days | |
| CVE-2024-20652 | Home windows HTML Platforms Safety Characteristic Bypass Vulnerability |
| CVE-2024-20653 | Microsoft Widespread Log File System Elevation of Privilege Vulnerability |
| CVE-2024-20674 | Home windows Kerberos Safety Characteristic Bypass Vulnerability |
| CVE-2024-20683 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-20686 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-20698 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21307 | Distant Desktop Shopper Distant Code Execution Vulnerability |
| CVE-2024-21310 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-21318 | Microsoft SharePoint Server Distant Code Execution Vulnerability |
Appendix C: Merchandise Affected
It is a record of December’s patches sorted by product household, then sub-sorted by severity. Every record is additional organized by CVE. Patches which can be shared amongst a number of product households are listed a number of occasions, as soon as for every product household.
Home windows (38 CVEs)
| Crucial severity | |
| CVE-2024-20674 | Home windows Kerberos Safety Characteristic Bypass Vulnerability |
| CVE-2024-20700 | Home windows Hyper-V Distant Code Execution Vulnerability |
| Vital severity | |
| CVE-2024-20652 | Home windows HTML Platforms Safety Characteristic Bypass Vulnerability |
| CVE-2024-20653 | Microsoft Widespread Log File System Elevation of Privilege Vulnerability |
| CVE-2024-20654 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-20655 | Microsoft On-line Certificates Standing Protocol (OCSP) Distant Code Execution Vulnerability |
| CVE-2024-20657 | Home windows Group Coverage Elevation of Privilege Vulnerability |
| CVE-2024-20658 | Microsoft Digital Exhausting Disk Elevation of Privilege Vulnerability |
| CVE-2024-20660 | Home windows Message Queuing Shopper Info Disclosure Vulnerability |
| CVE-2024-20661 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2024-20662 | Home windows On-line Certificates Standing Protocol (OCSP) Info Disclosure Vulnerability |
| CVE-2024-20663 | Home windows Message Queuing Shopper (MSMQC) Info Disclosure |
| CVE-2024-20664 | Microsoft Message Queuing Shopper Info Disclosure Vulnerability |
| CVE-2024-20666 | BitLocker Safety Characteristic Bypass Vulnerability |
| CVE-2024-20680 | Home windows Message Queuing Shopper (MSMQC) Info Disclosure |
| CVE-2024-20681 | Home windows Subsystem for Linux Elevation of Privilege Vulnerability |
| CVE-2024-20682 | Home windows Cryptographic Providers Distant Code Execution Vulnerability |
| CVE-2024-20683 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-20686 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-20687 | Microsoft AllJoyn API Denial of Service Vulnerability |
| CVE-2024-20690 | Home windows Close by Sharing Spoofing Vulnerability |
| CVE-2024-20691 | Home windows Themes Info Disclosure Vulnerability |
| CVE-2024-20692 | Microsoft Native Safety Authority Subsystem Service Info Disclosure Vulnerability |
| CVE-2024-20694 | Home windows CoreMessaging Info Disclosure Vulnerability |
| CVE-2024-20696 | Home windows Libarchive Distant Code Execution Vulnerability |
| CVE-2024-20697 | Home windows Libarchive Distant Code Execution Vulnerability |
| CVE-2024-20698 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-20699 | Home windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-21305 | Hypervisor-Protected Code Integrity (HVCI) Safety Characteristic Bypass Vulnerability |
| CVE-2024-21306 | Microsoft Bluetooth Driver Spoofing Vulnerability |
| CVE-2024-21307 | Distant Desktop Shopper Distant Code Execution Vulnerability |
| CVE-2024-21309 | Home windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-21310 | Home windows Cloud Recordsdata Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-21311 | Home windows Cryptographic Providers Info Disclosure Vulnerability |
| CVE-2024-21313 | Home windows TCP/IP Info Disclosure Vulnerability |
| CVE-2024-21314 | Home windows Message Queuing Shopper (MSMQC) Info Disclosure |
| CVE-2024-21316 | Home windows Server Key Distribution Service Safety Characteristic Bypass |
| CVE-2024-21320 | Home windows Themes Spoofing Vulnerability |
.NET (5 CVEs)
| Vital severity | |
| CVE-2024-0056 | Microsoft.Knowledge.SqlClient and System.Knowledge.SqlClient SQL Knowledge Supplier Info Disclosure Vulnerability |
| CVE-2024-0057 | .NET, .NET Framework, and Visible Studio Framework Safety Characteristic Bypass Vulnerability |
| CVE-2024-20672 | .NET Core and Visible Studio Denial of Service Vulnerability |
| CVE-2024-21312 | .NET Framework Denial of Service Vulnerability |
| CVE-2024-21319 | Microsoft Id Denial of Service Vulnerability |
Visible Studio (4 CVEs)
| Vital severity | |
| CVE-2024-0056 | Microsoft.Knowledge.SqlClient and System.Knowledge.SqlClient SQL Knowledge Supplier Info Disclosure Vulnerability |
| CVE-2024-0057 | .NET, .NET Framework, and Visible Studio Framework Safety Characteristic Bypass Vulnerability |
| CVE-2024-20656 | Visible Studio Elevation of Privilege Vulnerability |
| CVE-2024-21319 | Microsoft Id Denial of Service Vulnerability |
Azure (2 CVEs)
| Vital severity | |
| CVE-2024-0056 | Microsoft.Knowledge.SqlClient and System.Knowledge.SqlClient SQL Knowledge Supplier Info Disclosure Vulnerability |
| CVE-2024-20676 | Azure Storage Mover Distant Code Execution Vulnerability |
Microsoft Id Mannequin (1 CVE)
| Vital severity | |
| CVE-2024-21319 | Microsoft Id Denial of Service Vulnerability |
Microsoft Printer Metadata Troubleshooter Software (1 CVE)
| Vital severity | |
| CVE-2024-21325 | Microsoft Printer Metadata Troubleshooter Software Distant Code Execution Vulnerability |
Workplace (1 CVE)
| Vital severity | |
| CVE-2024-20677 | Microsoft Workplace Distant Code Execution Vulnerability |
SharePoint (1 CVE)
| Vital severity | |
| CVE-2024-21318 | Microsoft SharePoint Server Distant Code Execution Vulnerability |
SQL Server (1 CVE)
| Vital severity | |
| CVE-2024-0056
|
Microsoft.Knowledge.SqlClient and System.Knowledge.SqlClient SQL Knowledge Supplier Info Disclosure Vulnerability |
Appendix D: Advisories and Different Merchandise
It is a record of advisories and data on different related CVEs within the December Microsoft launch, sorted by product.
Related to Edge / Chromium (4 CVEs)
| CVE-2024-0222 | Chromium: CVE-2024-0222 Use after free in ANGLE |
| CVE-2024-0223 | Chromium: CVE-2024-0223 Heap buffer overflow in ANGLE |
| CVE-2024-0224 | Chromium: CVE-2024-0224 Use after free in WebAudio |
| CVE-2024-0225 | Chromium: CVE-2024-0225 Use after free in WebGPU |
Related to Home windows (third-party product) (one CVE)
| CVE-2022-35737 | MITRE: CVE-2022-35737 SQLite permits an array-bounds overflow |