Poorly secured Microsoft SQL (MS SQL) servers are being focused within the U.S., European Union, and Latin American (LATAM) areas as a part of an ongoing financially motivated marketing campaign to realize preliminary entry.
“The analyzed menace marketing campaign seems to finish in one in every of two methods, both the promoting of ‘entry’ to the compromised host, or the last word supply of ransomware payloads,” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov mentioned in a technical report shared with The Hacker Information.
The marketing campaign, linked to actors of Turkish origin, has been codenamed RE#TURGENCE by the cybersecurity agency.
Preliminary entry to the servers entails conducting brute-force assaults, adopted by way of xp_cmdshell configuration possibility to run shell instructions on the compromised host. This exercise mirrors that of a previous marketing campaign dubbed DB#JAMMER that got here to gentle in September 2023.
This stage paves the way in which for the retrieval of a PowerShell script from a distant server that is answerable for fetching an obfuscated Cobalt Strike beacon payload.
The post-exploitation toolkit is then used to obtain the AnyDesk distant desktop utility from a mounted community share for accessing the machine and downloading further instruments similar to Mimikatz to reap credentials and Superior Port Scanner to hold out reconnaissance.
Lateral motion is completed by way of a respectable system administration utility known as PsExec, which might execute applications on distant Home windows hosts.
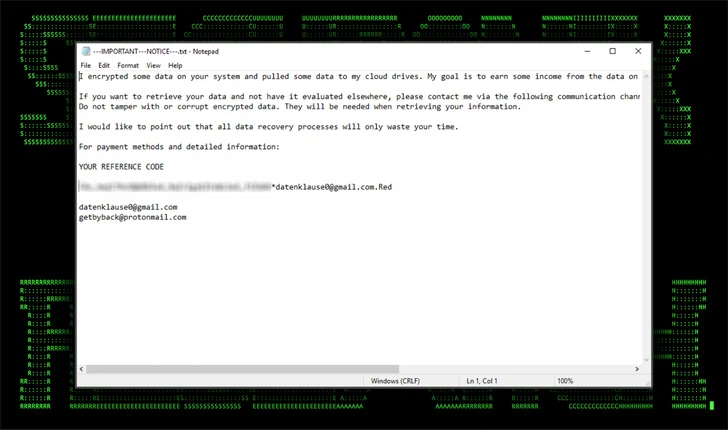
That assault chain, in the end, culminates with the deployment of Mimic ransomware, a variant of which was additionally used within the DB#JAMMER marketing campaign.
“The symptoms in addition to malicious TTPs used within the two campaigns are utterly completely different, so there’s a very excessive probability these are two disparate campaigns,” Kolesnikov advised The Hacker Information.
“Extra particularly, whereas the preliminary infiltration strategies are related, DB#JAMMER was barely extra subtle and used tunneling. RE#TURGENCE is extra focused and tends to make use of respectable instruments and distant monitoring and administration, similar to AnyDesk, in an try and mix in with regular exercise.”
Securonix mentioned it uncovered an operational safety (OPSEC) blunder made by the menace actors that allowed it to observe clipboard exercise owing to the truth that the clipboard sharing function of AnyDesk was enabled.
This made it potential to glean their Turkish origins and their on-line alias atseverse, which additionally corresponds to a profile on Steam and a Turkish hacking discussion board known as SpyHack.
“All the time chorus from exposing important servers on to the web,” the researchers cautioned. “With the case of RE#TURGENCE attackers had been instantly capable of brute pressure their method into the server from exterior the primary community.”