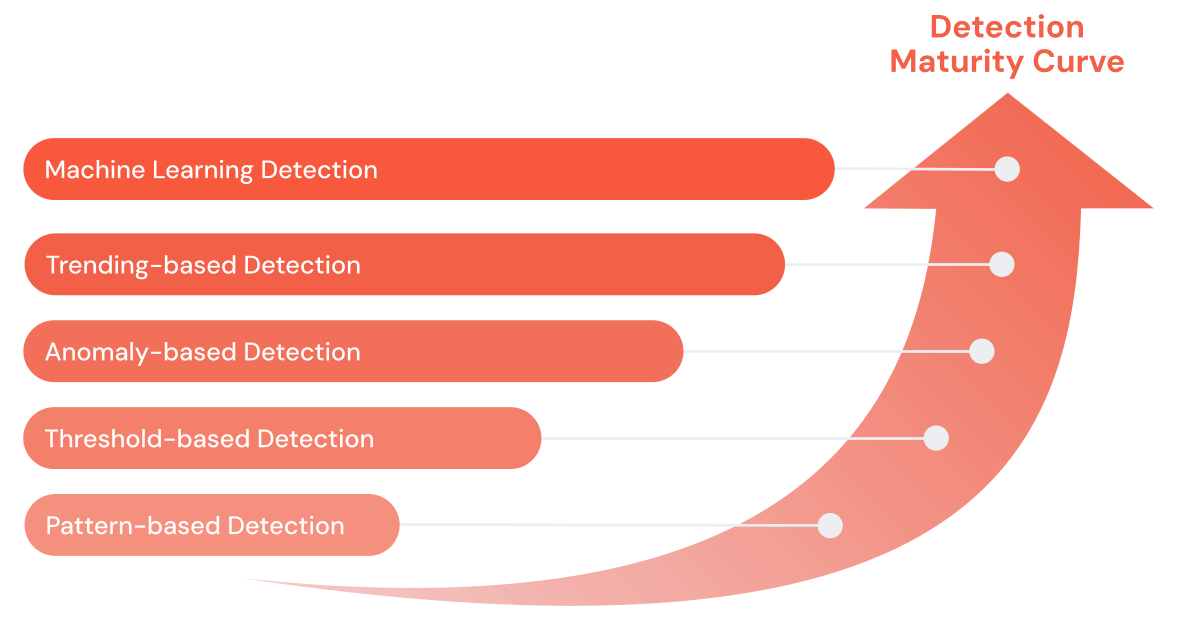
Cyber threats and the instruments to fight them have develop into extra refined. SIEM is over 20 years previous and has developed considerably in that point. Initially reliant on pattern-matching and threshold-based guidelines, SIEMs have superior their analytic talents to deal with extra refined cyber threats. This evolution, termed the ‘Detection Maturity Curve,’ illustrates the shift safety operations have taken from easy alert techniques to superior mechanisms able to predictive risk evaluation. Regardless of these developments, fashionable SIEMs face challenges scaling for giant information units and long-term trending or machine studying detection, underscoring a company’s capacity to detect and reply to more and more complicated risk actors.
That is the place Databricks helps cybersecurity groups. Databricks’ unified analytics, powered by Apache Spark™, MLflow, and Delta tables, cost-effectively scaling to satisfy enterprises’ fashionable huge information and machine studying wants.
This weblog publish will describe our journey of constructing evolving safety detection guidelines transitioning from primary sample matching to superior strategies. We’ll element every step and spotlight how Databricks Knowledge Intelligence Platform has been used to run these detections on over 100 terabytes of month-to-month occasion logs and 4 petabytes of historic information, beating the international world file for pace and price.
Introduction
Our essential goal is to demystify the detection patterns described within the detection maturity curve and discover their worth, advantages, and limitations. To assist, we’ve got created a GitHub repository with this weblog’s supply materials and a helper library that comprises repeatable PySpark code that can be utilized in your cyber analytics program. The examples on this information are based mostly on the pattern logs generated by the Git repository.
1. Sample-Based mostly Guidelines
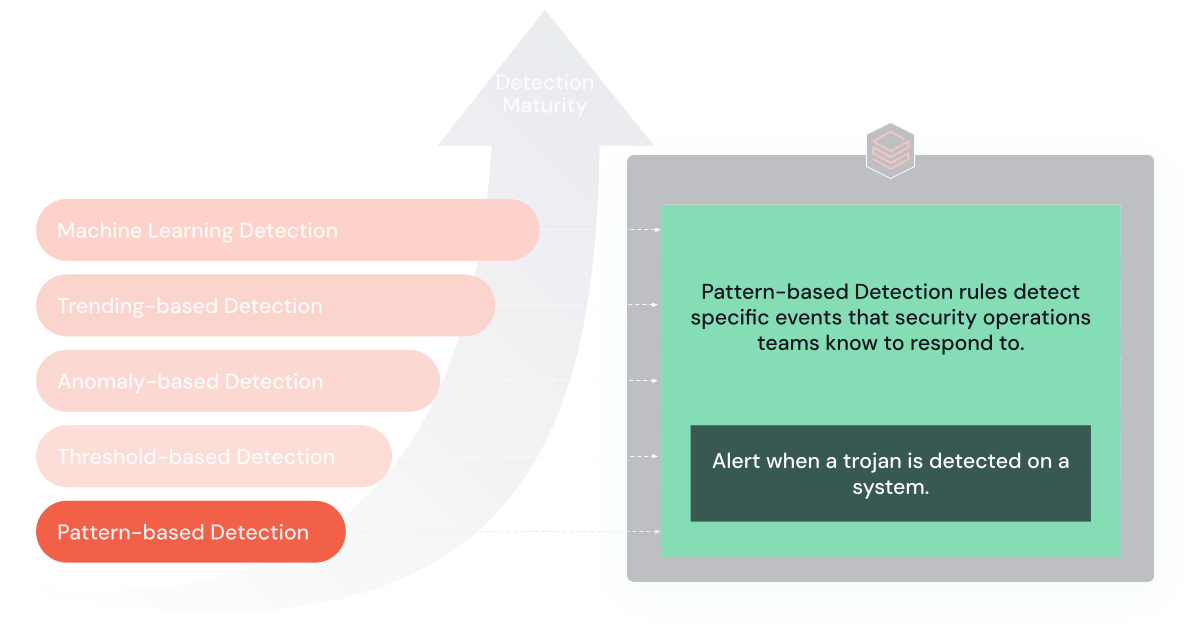
Sample-based guidelines are the only type of SIEM detection, which triggers alerts upon recognizing particular patterns or signatures in information.
Goal and Advantages: These guidelines are foundational for SIEM detection, providing simplicity and specificity. They’re extremely efficient in rapidly figuring out and responding to recognized threats.
Limitations: Their main downside is their restricted capability to adapt to new and unknown threats, making them much less efficient in opposition to refined cyber assaults.
When to Use: These guidelines are greatest fitted to organizations within the early levels of their cybersecurity program or these primarily going through well-documented threats.
As an example, the next SQL pattern-based rule may search for particular malware signatures:
SELECT *
FROM antivirus
WHERE virus_category = 'trojan'';2. Threshold-Based mostly Guidelines
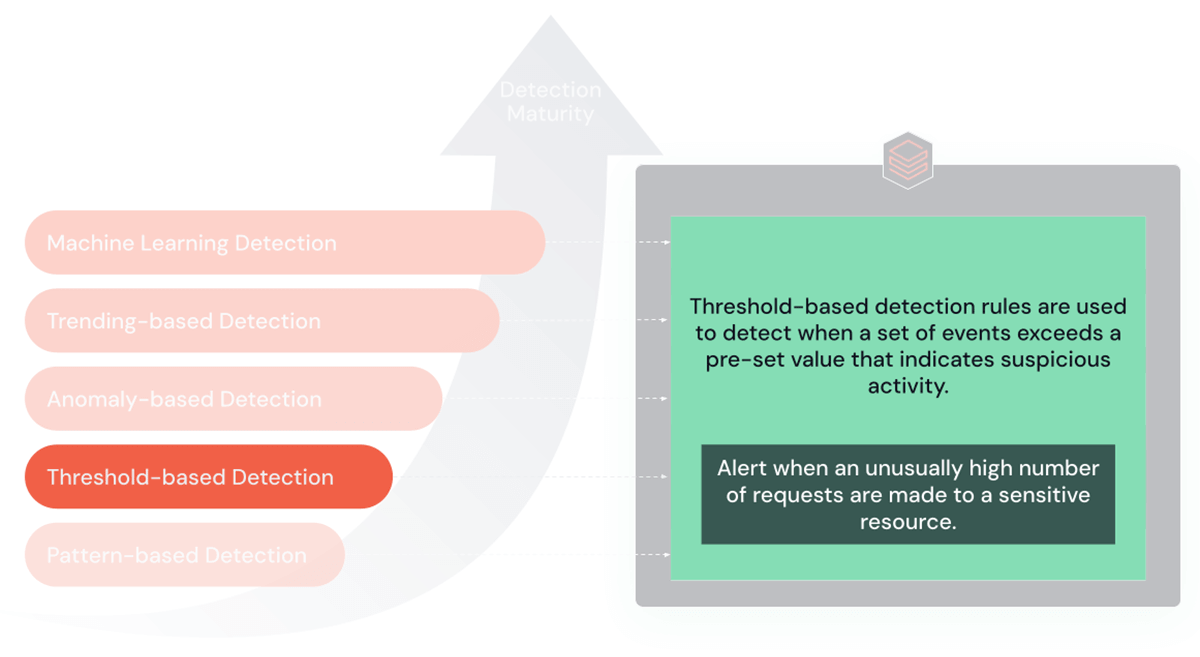
Threshold-based guidelines are designed to set off alerts when occasions surpass predefined limits or thresholds. They’re particularly efficient in situations like brute power or Denial of Service (DoS) assaults.
Goal and Advantages: The first power of those guidelines lies of their capacity to detect vital deviations from regular exercise, similar to unusually excessive community site visitors or an irregular variety of login makes an attempt. This makes them invaluable for figuring out large-scale, conspicuous assaults.
Limitations: Nevertheless, their effectiveness is lessened in opposition to sluggish, progressive assaults that do not instantly cross these set thresholds. Additionally they battle with static thresholds that, when set too low, trigger false positives or, when set too excessive, pricey false negatives.
When to Use: These guidelines are only in environments with established baseline exercise ranges, permitting for clear threshold settings. This contains situations like monitoring community site visitors or monitoring login makes an attempt.
As an example, the next SQL trending-based rule demonstrates determine statistically vital deviations in consumer login makes an attempt:
SELECT ip, COUNT(*) as makes an attempt
FROM delta.`/tmp/detection_maturity/tables/web_logs`
WHERE http_method='GET' AND timestamp > current_timestamp() - INTERVAL 'half-hour'
GROUP BY ip
HAVING makes an attempt > 100;This SQL question will set off an alert if there are greater than 100 connections from an IP in half-hour.
3. Statistical Anomaly Detection
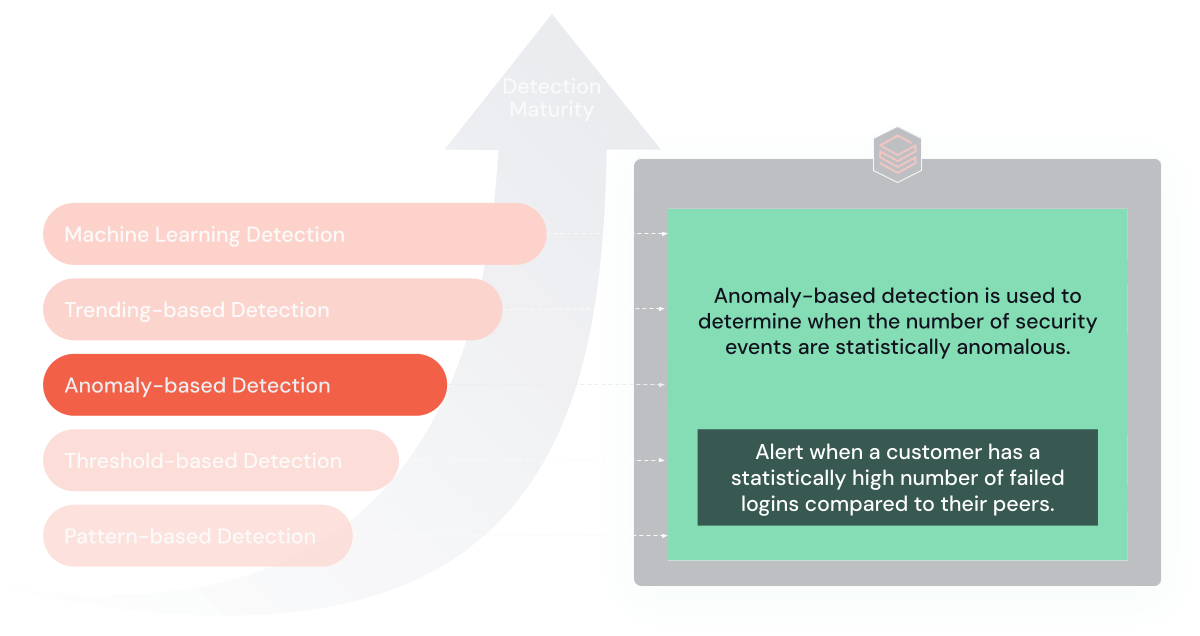
As your detection capabilities mature, you may incorporate strategies to detect statistical anomalies in your atmosphere. These guidelines construct a mannequin of “regular” habits based mostly on historic information after which set off an alert when there’s a vital deviation from the norm.
Goal and Advantages: These guidelines excel in recognizing deviations from ‘regular’ habits, providing a dynamic method to risk detection.
Limitations: Requires substantial historic information and may generate false positives if incorrectly calibrated. Monitoring many entities can require vital computation, inflicting efficiency points or lacking outcomes when hitting inner limits with conventional SIEMs.
When to Use: Splendid for mature cybersecurity environments with intensive historic information.
As an example, the next SQL anomaly-based rule detects when a consumer’s actions deviate statistically from the peer group’s:
WITH mean_stddev AS (
SELECT
login_id,
AVG(failed_logins) AS hourly_mean,
STDDEV(failed_logins) AS hourly_stddev
FROM
(
SELECT
login_id,
HOUR(_event_date) AS hour,
COUNT(*) AS failed_logins
FROM
delta.`/tmp/detection_maturity/tables/ciam`
WHERE
(consequence = 'DENIED' OR consequence = 'BLOCKED') AND
_event_date < current_timestamp() - INTERVAL 1 HOURS
GROUP BY
login_id, hour
)
GROUP BY
login_id
)
, last_hour_logins AS (
SELECT
login_id,
COUNT(*) AS failed_logins_last_hour
FROM
delta.`/tmp/detection_maturity/tables/ciam`
WHERE
(consequence = 'DENIED' OR consequence = 'BLOCKED') AND
_event_date > current_timestamp() - INTERVAL 1 HOURS
GROUP BY
login_id
)
SELECT
last_hour_logins.login_id,
last_hour_logins.failed_logins_last_hour,
mean_stddev.hourly_mean,
mean_stddev.hourly_stddev
FROM
last_hour_logins
JOIN mean_stddev
ON last_hour_logins.login_id = mean_stddev.login_id
WHERE
last_hour_logins.failed_logins_last_hour > mean_stddev.hourly_mean + 3 * mean_stddev.hourly_stddev;This question will set off an alert if a consumer’s failed logins are 3 times the usual deviation above their peer’s imply failed logins.
4. Trending-Based mostly Guidelines
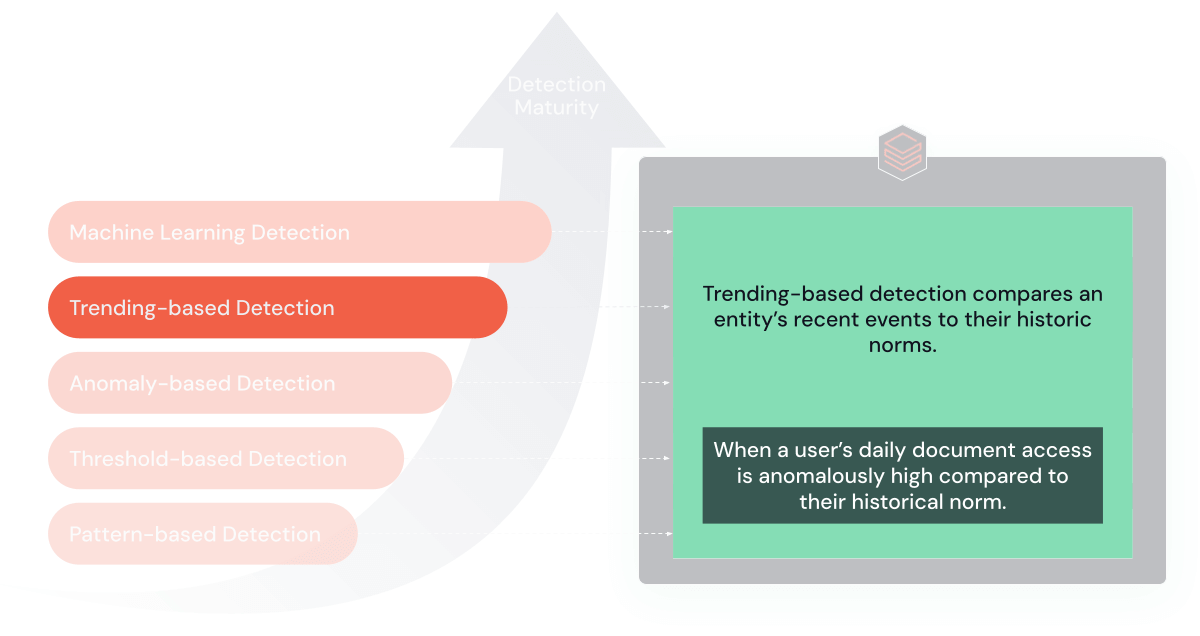
Trending-based guidelines are designed to determine anomalies or vital modifications in an entity’s habits over time. These guidelines evaluate present actions in opposition to a person’s historic norm to successfully scale back false positives.
Goal and Advantages: These guidelines are adept at uncovering refined, evolving threats. By analyzing information traits over time, they supply insights into modifications in habits which will point out a safety risk.
Limitations: One of many essential challenges with trending-based guidelines is that they are often resource-intensive and require ongoing evaluation of enormous volumes of information.
When to Use: They’re only when long-term information monitoring is sensible, the detection engine can scale, and threats might develop steadily. Conventional SIEMs usually are not usually used for development evaluation as a result of their complexity.
Let’s take into account monitoring anomalous login makes an attempt from the earlier sample. Whereas a consumer might deviate from their peer group, this deviation is perhaps typical for them. A trend-based rule may be deployed to alert when there’s a vital enhance in failed login makes an attempt for a selected hostname in comparison with their historic sample or, extra importantly, to not alert when it would not.
As an example, the next SQL trending-based rule detects when a consumer’s logins are statistically vital from their historic traits:
-- Calculate the typical variety of failed logins over the previous 90 days for every IP
WITH weekly_averages AS (
SELECT login_id, COUNT(*) / 7 AS avg_daily_failed_logins
FROM delta.`/tmp/detection_maturity/tables/ciam`
WHERE login_status = 'failure' AND login_time > current_timestamp() - INTERVAL '90
days'
GROUP BY login_id
),
-- Calculate the variety of failed logins previously 24 hours for every IP
daily_counts AS (
SELECT login_id, COUNT(*) AS daily_failed_logins
FROM delta.`/tmp/detection_maturity/tables/ciam`
WHERE login_status = 'failure' AND login_time > current_timestamp() - INTERVAL '1
day'
GROUP BY login_id
)
-- Alert on login_id with greater than twice the typical variety of failed logins
SELECT daily_counts.login_id
FROM daily_counts
JOIN weekly_averages ON daily_counts.login_id = weekly_averages.login_id
WHERE daily_counts.daily_failed_logins > 2 *
weekly_averages.avg_daily_failed_logins;On this instance, we calculate the typical day by day variety of failed login makes an attempt from every hostname over the previous week and the variety of failed makes an attempt from every host previously 24 hours. We then be part of these two outcome units on hostnames and filter for hosts the place the variety of failed makes an attempt previously 24 hours exceeds the typical day by day variety of makes an attempt over the previous 90 days.
5. Machine Studying-Based mostly Guidelines
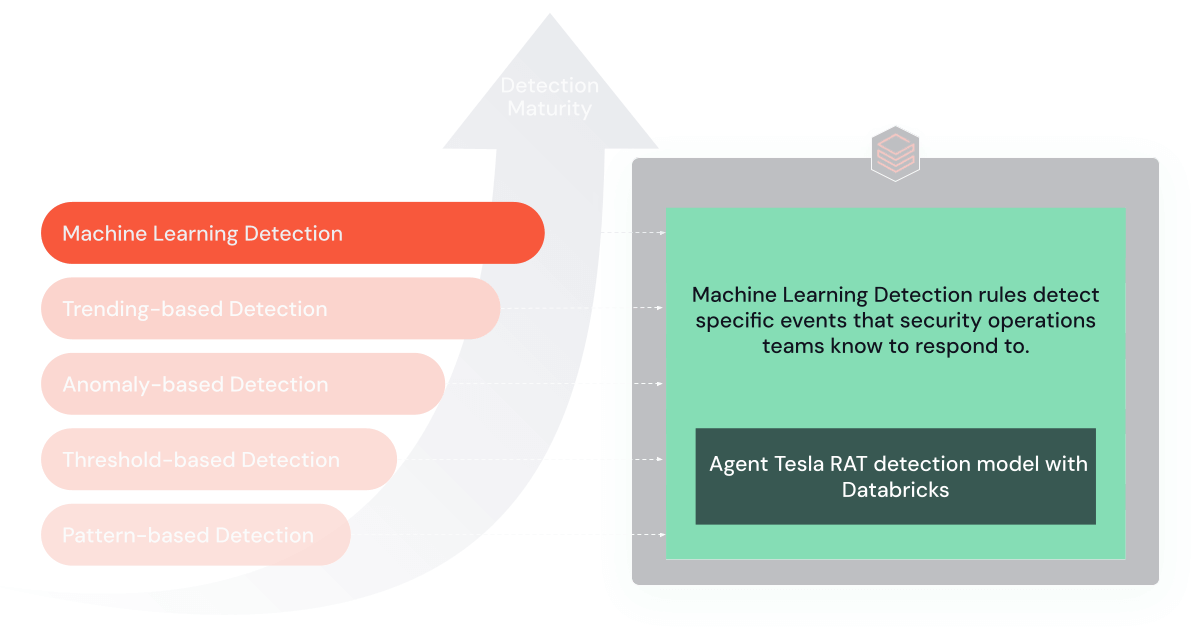
Probably the most superior detection guidelines regularly use machine studying algorithms to adapt to threats. These algorithms can be taught from historic information to foretell and detect future threats, usually catching assaults that extra deterministic guidelines may miss. Implementing and operationalizing machine studying fashions requires vital funding in information science and machine studying experience and platforms. The Databricks Knowledge Intelligence Platform facilitates complete administration of your complete machine studying lifecycle, encompassing preliminary mannequin improvement, deployment, and even the eventual sunsetting section.
Unsupervised studying fashions, educated utilizing algorithms similar to clustering (e.g., Ok-means, hierarchical clustering) and anomaly detection (e.g., Isolation Forests, One-Class SVM), are essential in figuring out novel, beforehand unknown cyber threats. These fashions work by studying the ‘regular’ habits patterns within the information after which flagging deviations from this norm as potential anomalies or assaults. Unsupervised studying is especially useful in cybersecurity as a result of it will probably assist detect new, rising threats for which labeled information doesn’t but exist.
Conversely, SOCs make use of supervised studying fashions to categorise and detect recognized kinds of assaults based mostly on labeled information. Examples of those fashions embrace logistic regression, choice timber, random forests, and help vector machines (SVM). These fashions are educated utilizing datasets the place the assault cases are recognized and labeled, enabling them to be taught the patterns related to various kinds of assaults and subsequently predict the labels of latest, unseen information.
For machine studying, I’ll reference the superb mission Detecting AgentTeslaRAT by DNS Analytics with Databricks (Github right here), which walks by coaching and serves the ML mannequin for cybersecurity use circumstances.
Bonus: Threat-based Alerting
Threat-based alerting is a strong technique that enhances detection patterns. Threat-based alerting quantifies “dangerous” actions (e.g., failed logins, off-hour actions) to entities (e.g., IP addresses, customers, and many others.). It usually contains useful metadata, similar to the danger class, kill-chain stage, and many others., permitting detection engineers to construct guidelines based mostly on a broader vary of occasions.
Constructing a risk-based detection course of requires the additional step of risk-scoring occasions. This may be completed by including a brand new risk-score column in a desk, however a danger desk that comes with danger occasions from a number of sources is often created.
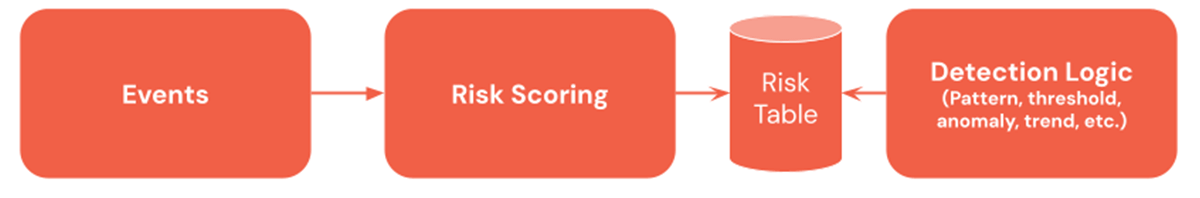
Organizations adopting risk-based detection methods can exploit the detection patterns talked about above. For instance, suppose a consumer has a high-risk rating. In that case, organizations can use the trending detection sample to confirm if that is distinctive for the consumer to keep away from alerting when admins often carry out late-night upgrades throughout a change window.
Repeatable Code
The GitHub repository comprises pocket book helper strategies with commonplace cyber capabilities for assortment, filtering, and detection. Databricks additionally has a mission to assist simplify this lifecycle. If you’re fascinated about studying extra, please contact your account supervisor.
Conclusion
Within the ever-evolving world of cyber threats, upgrading SIEM detection from primary sample matching to superior machine studying is crucial. This shift is a strategic necessity for successfully addressing complicated cyber threats. Whereas evolving detection strategies improve our capacity to uncover and reply to refined safety incidents, the problem lies in integrating these refined strategies with out overburdening our groups. In the end, the purpose is to develop a resilient, adaptable cybersecurity program able to going through each present threats and future challenges with effectivity and agility.
