By now, virtually everybody throughout the tech panorama has heard of the Zero Belief (ZT) safety mannequin, which assumes that each system, software, or person trying to entry a community is to not be trusted (see NIST definitions beneath). However as fashions go, the thought is simpler than the execution.
To offer steering to federal companies, and in some ways paved the way for the non-public sector, the Cybersecurity and Infrastructure Safety Company (CISA) issued the preliminary Zero Belief Maturity Mannequin (ZTMM) in 2021 with the intent to present companies a conceptual roadmap to onboard to a shared zero-trust maturity mannequin by 2024. Subsequent to the ZTMM launch, CISA issued a request for remark, which has led to the revised model 2 of the ZTMM in April 2023, as “commenters requested extra steering and area to evolve alongside the maturity mannequin,” in accordance to CISA.
The revised ZTMM is organized by 5 classes or pillars: identification, units, networks, purposes and workloads, and knowledge, and 4 ranges of maturity: conventional, preliminary, superior, and optimum.
Specializing in the Information Pillar
In accordance with the Federal Information Technique, the federal authorities views itself because the “preeminent provider and complex and moral person of information.” With use circumstances from citizen providers to army intelligence, authorities knowledge is leveraged as a strategic asset throughout companies (civilian and DoD). Shifting to the “optimum” stage of maturity is vital to eliminating unauthorized entry by unhealthy actors, each overseas and home.
To succeed in optimum maturity, the ZTMM summarizes, “Company knowledge ought to be protected on units, in purposes, and on networks in accordance with federal necessities. Businesses ought to stock, categorize, and label knowledge; shield knowledge at relaxation and in transit; and deploy mechanisms to detect and cease knowledge exfiltration. Businesses ought to fastidiously craft and evaluation knowledge governance insurance policies to make sure all knowledge lifecycle safety features are appropriately enforced throughout the enterprise.”
How does Cloudera help the evolution to optimum?
Zero belief as a principal is vital to enhancing your safety posture, however zero belief with correct governance frees the information so you possibly can share it successfully throughout the group. It’s a win-win. The information is protected however it’s also accessible by the individuals who want it. That is the balancing act of safety.
Cloudera Shared Information Expertise (SDX) is a core element of Cloudera Information Platform’s structure. It operates independently from compute and storage layers, providing built-in safety and governance primarily based on metadata. With persistent context throughout analytics and cloud environments, SDX simplifies knowledge supply and entry with a unified multi-tenant mannequin. This reduces dangers and operational prices whereas enabling quicker deployment of safe and ruled knowledge lakes for broader knowledge entry.
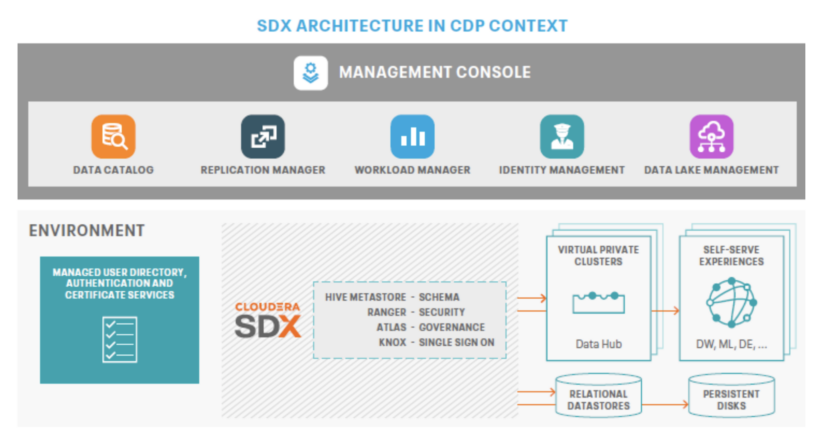
Cloudera adheres to the guiding ideas of a Zero Belief Structure as follows:
Confirm Explicitly
Cloudera gives multi-factor authentication all over the place, offering a normalized SSO token for representing the authenticated person. This token is usually used for WebSSO capabilities for end-user consumption of the REST APIs obtainable in Cloudera’s software program.
Use Least Privileged Entry
Cloudera leverages Ranger to restrict person entry utilizing each RBAC and ABAC insurance policies. With Ranger, directors can create default insurance policies that deny entry to all assets managed by Cloudera. Particular person customers and teams of customers can incrementally be granted entry on an as-needed foundation. Permissions are fine-grain and will be configured utilizing time-based home windows.
Information Safety
Cloudera leverages Navigator Key Trustee Server and Ranger Key Administration Service to create zones of assets which are encrypted utilizing distinctive and strong-cipher keys. Customers and teams of customers granted privileged entry to a useful resource should even be given entry to the suitable zone key to decrypt the underlying knowledge. This minimizes the blast radius of a breach via segmented knowledge entry.
Cloudera additionally leverages strong-ciphered TLS to encrypt all data-in-motion. This contains info alternate between Cloudera providers and all end-client connections.
Auditing
Cloudera offers full auditing of all useful resource entry and person behaviors via Ranger’s centralized auditing tooling. The person and useful resource audits will be forwarded to a SEIM answer for proactive monitoring and alerting.
Moreover, Cloudera satisfies sections six, seven, and eight of the Govt Order on Enhancing the Nation’s Cybersecurity with real-time assortment and scalable analytics of log knowledge. Lengthy-term retention of logs and sturdy machine studying capabilities offers companies a strong instrument for menace looking, investigation, and remediation.
Governance and knowledge cataloging
Cloudera prioritizes governance and cataloging via governance instruments Apache Atlas and Information Catalog. With Apache Atlas, Cloudera permits governance controls that successfully tackle enterprise-scale compliance necessities. Information Catalog helps the group perceive its knowledge by constructing metadata and simplifying the creation and upkeep of Ranger insurance policies. Understanding your knowledge is vital to defending the information.
Study extra about Cloudera’s method to safety and compliance at cloudera.com/trustcenter.

