On this article, we are going to stroll you thru the method of implementing effective grained entry management for the information governance framework throughout the Cloudera platform. This can enable a knowledge workplace to implement entry insurance policies over metadata administration property like tags or classifications, enterprise glossaries, and knowledge catalog entities, laying the muse for complete knowledge entry management.
In a very good knowledge governance technique, you will need to outline roles that enable the enterprise to restrict the extent of entry that customers can need to their strategic knowledge property. Historically we see three foremost roles in a knowledge governance workplace:
- Information steward: Defines the enterprise guidelines for knowledge use in keeping with company steerage and knowledge governance necessities.
- Information curator: Assigns and enforces knowledge classification in keeping with the principles outlined by the information stewards in order that knowledge property are searchable by the information client.
- Information client: Derives insights and worth from knowledge property and is eager to grasp the standard and consistency of tags and phrases utilized to the information.
Throughout the Cloudera platform, whether or not deployed on premises or utilizing any of the main public cloud suppliers, the Cloudera Shared Information Expertise (SDX) ensures consistency of all issues knowledge safety and governance. SDX is a elementary a part of any deployment and depends on two key open supply tasks to offer its knowledge administration performance: Apache Atlas supplies a scalable and extensible set of core governance providers, whereas Apache Ranger allows, displays, and manages complete safety for each knowledge and metadata.
On this article we are going to clarify how one can implement a effective grained entry management technique utilizing Apache Ranger by creating safety insurance policies over the metadata administration property saved in Apache Atlas.
Case Introduction
On this article we are going to take the instance of a knowledge governance workplace that desires to regulate entry to metadata objects within the firm’s central knowledge repository. This enables the group to adjust to authorities rules and inside safety insurance policies. For this job, the information governance group began by trying on the finance enterprise unit, defining roles and obligations for various kinds of customers within the group.
On this instance, there are three totally different customers that may enable us to indicate the totally different ranges of permissions that may be assigned to Apache Atlas objects via Apache Ranger insurance policies to implement a knowledge governance technique with the Cloudera platform:
- admin is our knowledge steward from the information governance workplace
- etl_user is our knowledge curator from the finance group
- joe_analyst is our knowledge client from the finance group
Word that it might be simply as straightforward to create extra roles and ranges of entry, if required. As you will note as we work via the instance, the framework offered by Apache Atlas and Apache Ranger is extraordinarily versatile and customizable.
First, a set of preliminary metadata objects are created by the information steward. These will enable the finance group to seek for related property as a part of their day-to-day actions:
- Classifications (or “tags”) like “PII”, “SENSITIVE”, “EXPIRES_ON”, “DATA QUALITY” and so on.
- Glossaries and phrases created for the three foremost enterprise items: “Finance,” “Insurance coverage,” and “Automotive.”
- A enterprise metadata assortment known as “Venture.”
NOTE: The creation of the enterprise metadata attributes shouldn’t be included within the weblog however the steps may be adopted right here.
Then, with the intention to management the entry to the information property associated to the finance enterprise unit, a set of insurance policies have to be applied with the next circumstances:
The finance knowledge curator <etl_user> ought to solely be allowed to:
- Create/learn classifications that begin with the phrase “finance.”
- Learn/replace entities which are categorised with any tag that begins with the phrase “finance,” and likewise any entities associated to the “worldwidebank” undertaking. The person also needs to be capable of add labels and enterprise metadata to these entities.
- Add/replace/take away classifications of the entities with the earlier specs.
- Create/learn/replace the glossaries and glossary phrases associated to “finance.”
The finance knowledge client <joe_analyst> ought to solely be allowed to:
- View and entry cClassifications associated to “finance” to look property.
- View and entry entities which are categorised with tags associated to “finance.”
- View and entry the “finance” glossary.
Within the following part, the method for implementing these insurance policies might be defined intimately.
Implementation of fine-grained entry controls (step-by-step)
As a way to meet the enterprise wants outlined above, we are going to show how entry insurance policies in Apache Ranger may be configured to safe and management metadata property in Apache Atlas. For this goal we used a public AMI picture to arrange a Cloudera Information Platform surroundings with all SDX elements. The method of establishing the surroundings is defined in this text.
1. Authorization for Classification Sorts
Classifications are a part of the core of Apache Atlas. They’re one of many mechanisms offered to assist organizations discover, manage, and share their understanding of the information property that drive enterprise processes. Crucially, classifications can “propagate” between entities in keeping with lineage relationships between knowledge property. See this web page for extra particulars on propagation.
1.1 Information Steward – admin person
To regulate entry to classifications, our admin person, within the function of information steward, should carry out the next steps:
- Entry the Ranger console.
- Acces Atlas repository to create and handle insurance policies.
- Create the suitable insurance policies for the information curator and the information client of the finance enterprise unit.
First, entry the Atlas Ranger insurance policies repository from the Ranger admin UI
Picture 1 – Ranger foremost web page
Within the Atlas coverage repository:
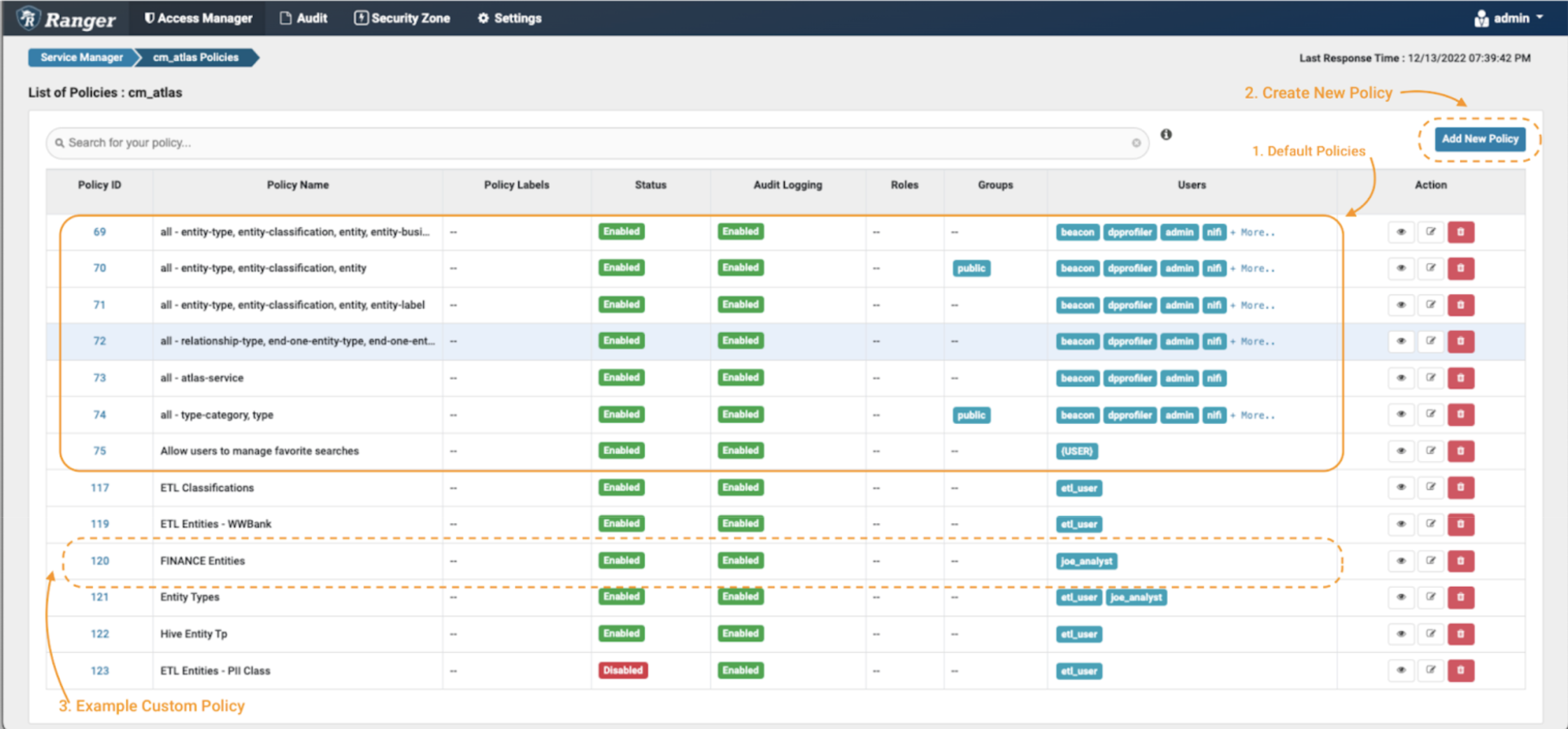
Picture 2 – Atlas insurance policies
The very first thing you will note are the default Atlas insurance policies (notice 1). Apache Ranger permits specification of entry insurance policies as each “enable” guidelines and “deny” guidelines. Nonetheless, it’s a really helpful good observe in all safety contexts to use the “precept of least privilege”: i.e., deny entry by default, and solely enable entry on a selective foundation. It is a way more safe strategy than permitting entry to everybody, and solely denying or excluding entry selectively. Subsequently, as a primary step, it’s best to confirm that the default insurance policies don’t grant blanket entry to the customers we’re searching for to limit on this instance situation.Then, you’ll be able to create the brand new insurance policies (eg. take away the general public entry of the default insurance policies by making a deny coverage; notice 2) and eventually you will note that the newly created insurance policies will seem on the backside of the part (notice 3).
After clicking the “Add New Coverage” button:
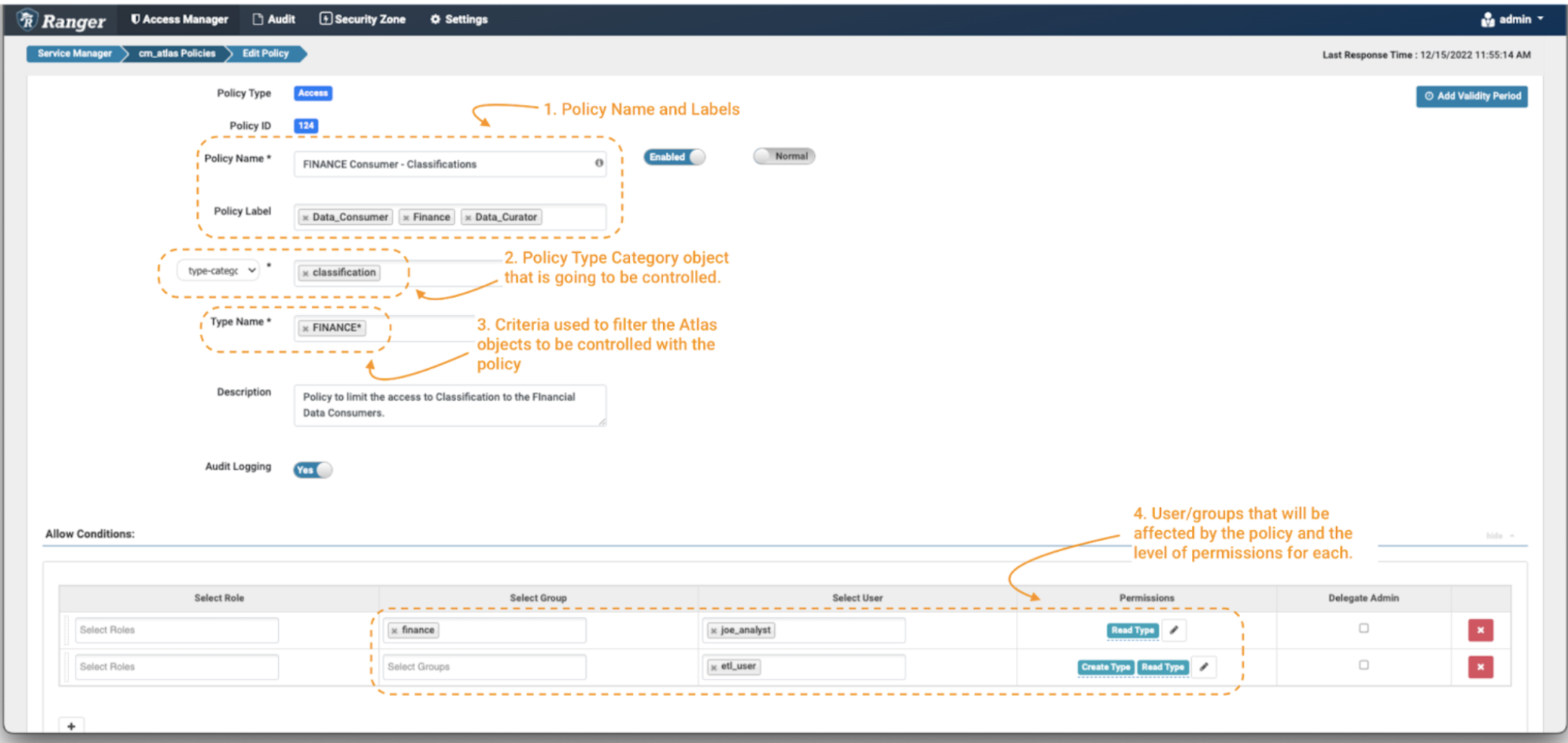
Picture 3 – Create coverage over finance classification
- First, outline a coverage identify and, if desired, some coverage labels (notice 1). These would not have a “practical” impact on the coverage, however are an necessary a part of protecting your safety insurance policies manageable as your surroundings grows over time. It’s regular to undertake a naming conference on your insurance policies, which can embrace short-hand descriptions of the person teams and/or property to which the coverage applies, and a sign of its intent. On this case we’ve got chosen the coverage identify “FINANCE Shopper – Classifications,” and used the labels “Finance.” “Information Governance,” and “Information Curator.”
- Subsequent, outline the kind of object on which you need to apply the coverage. On this case we are going to choose “type-category” and fill with “Classifications” (notice 2).
- Now, you should outline the standards used to filter the Apache Atlas objects to be affected by the coverage. You should utilize wildcard notations like “*”. To restrict the information client to solely seek for classifications beginning with the work finance, use FINANCE* (notice 3).
Lastly, you should outline the permissions that you just need to grant on the coverage and the teams and customers which are going to be managed by the coverage. On this case, apply the Learn Sort permission to group: finance and person: joe_analyst and Create Sort & Learn Sort permission to person: etl_user. (notice 4)
Now, as a result of they’ve the Create Sort permission for classifications matching FINANCE*, the information curator etl_user can create a brand new classification tag known as “FINANCE_WW” and apply this tag to different entities. This might be helpful if a tag-based entry coverage has been outlined elsewhere to offer entry to sure knowledge property.
1.2 Information Curator – etl_user person
We are able to now show how the classification coverage is being enforced over etl_user. This person is just allowed to see classifications that begin with the phrase finance, however he may create some extra ones for the totally different groups below that division.
etl_user can create a brand new classification tag known as FINANCE_WW below a guardian classification tag FINANCE_BU.
To create a classification in Atlas:
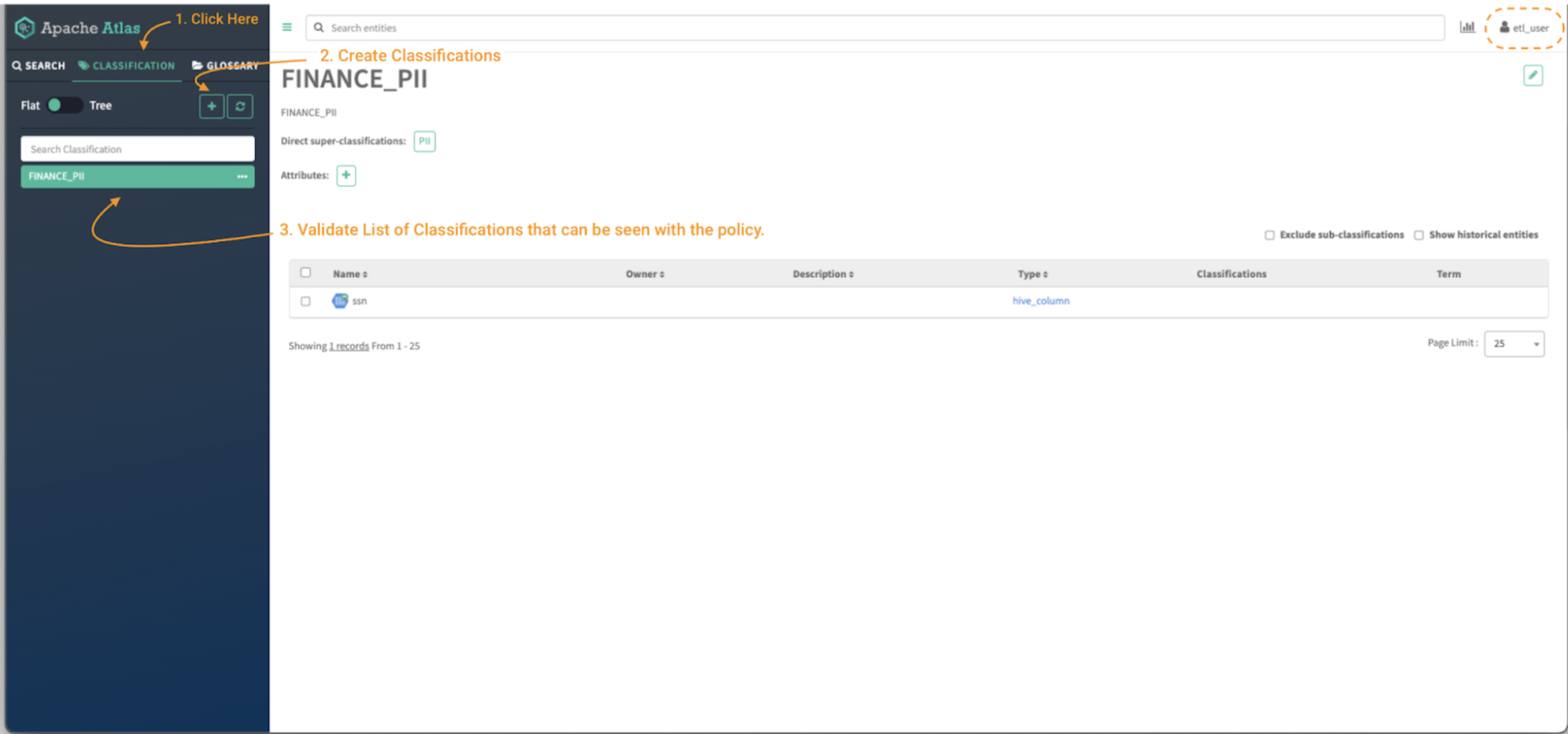
Picture 4 – Atlas classifications tab
- First, click on on the classification panel button (notice 1) to have the ability to see the present tags that the person has entry to. It is possible for you to to see the property which are tagged with the chosen classification. (notice 3)
Then, click on on the “+” button to create a brand new classification. (notice 2)
A brand new window open, requiring varied particulars to create the brand new classification
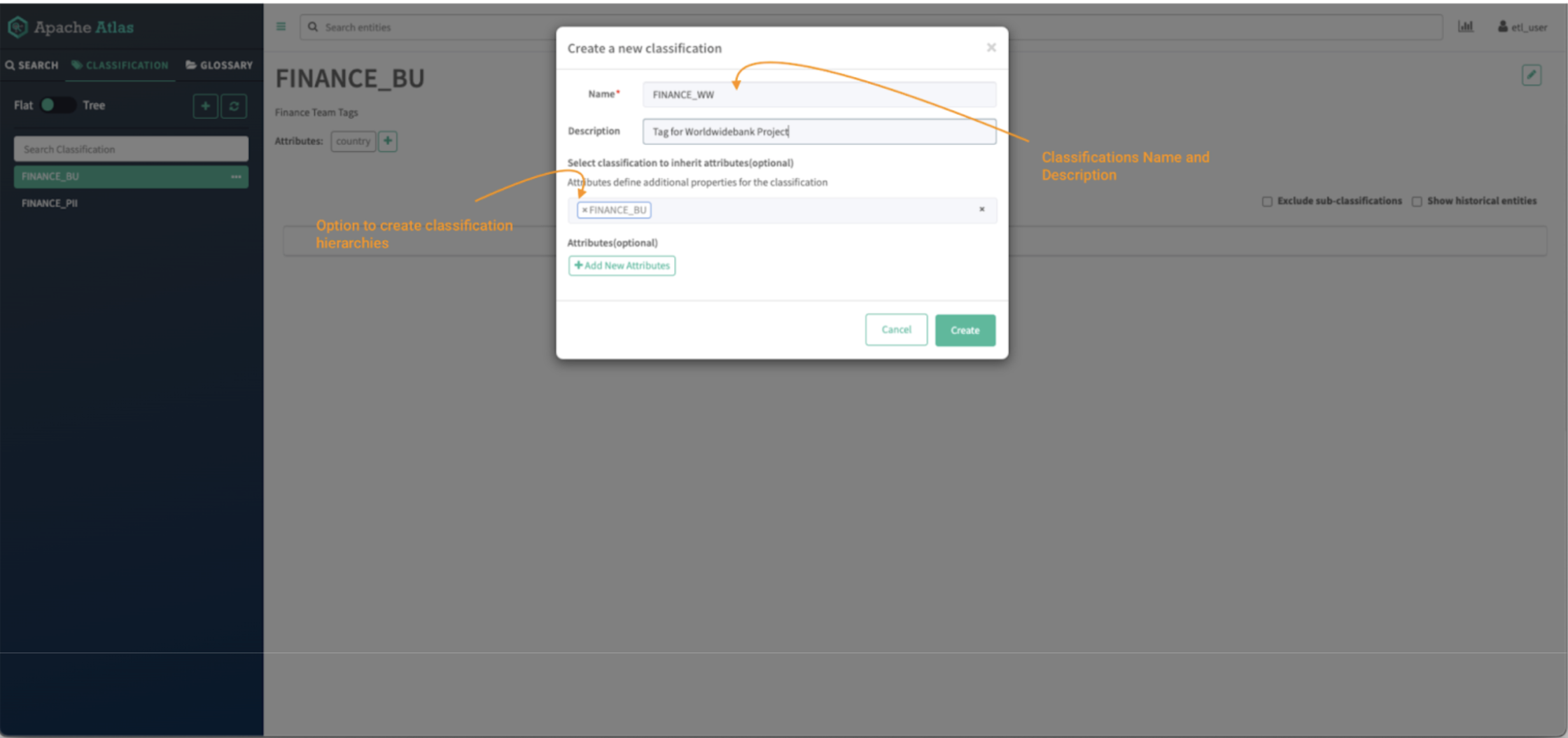
Picture 5 – Atlas classifications creation tab
- First, present the identify of the classification, on this case FINANCE_WW, and supply an outline, in order that colleagues will perceive the way it ought to be used..
- Classifications can have hierarchies and people inherit attributes from the guardian classification. To create a hierarchy, sort the identify of the guardian tag, on this case FINANCE_BU.
- Extra customized attributes may also be added to later be used on attribute-based entry management (ABAC) insurance policies. This falls exterior of the scope of this weblog submit however a tutorial on the topic may be discovered right here.
(Optionally available) For this instance, you’ll be able to create an attribute known as “nation,” which can merely assist to prepare property. For comfort you may make this attribute a “string” (a free textual content) sort, though in a dwell system you’d most likely need to outline an enumeration in order that customers’ inputs are restricted to a legitimate set of values.
After clicking the button “create” the newly created classification is proven within the panel:
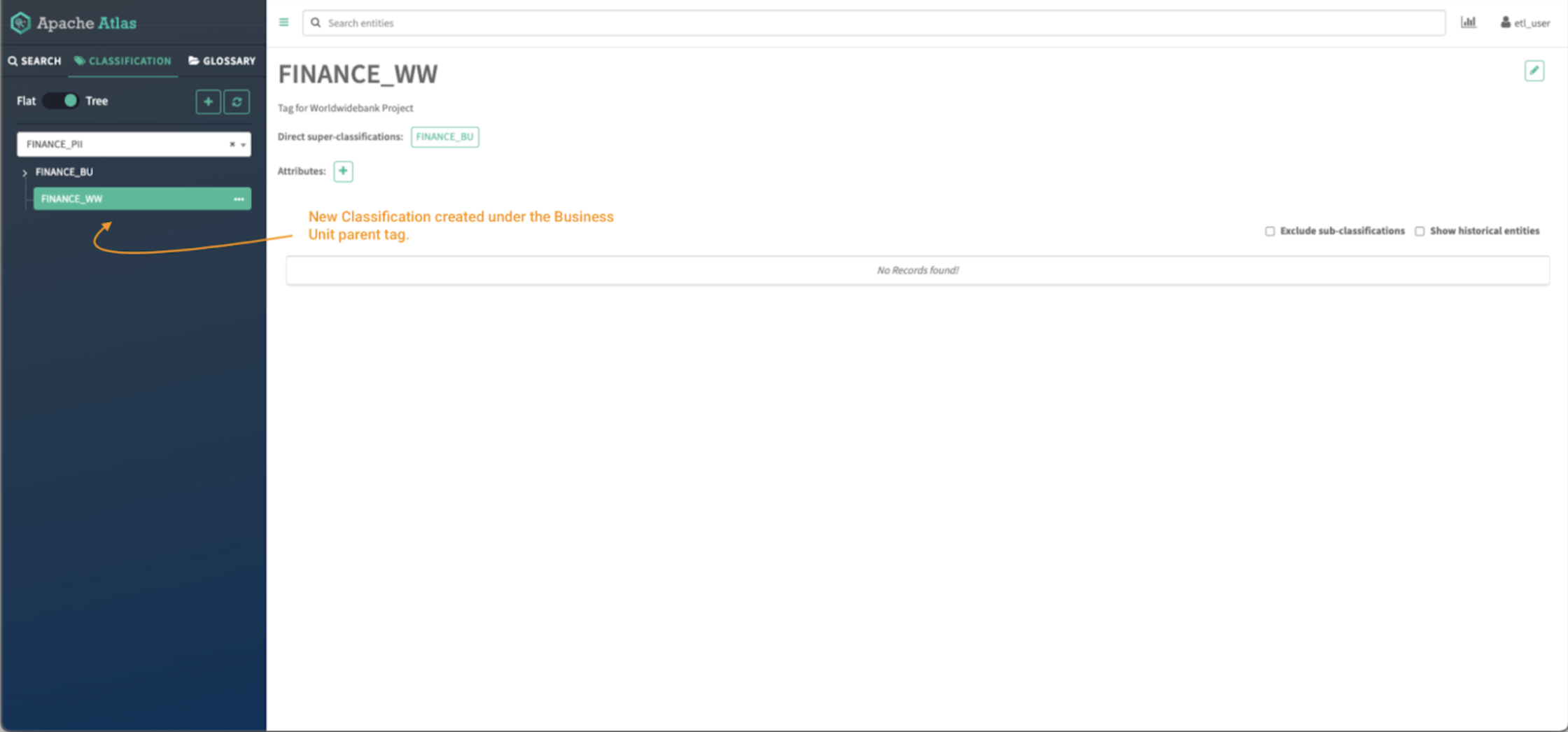
Picture 6 – Atlas classifications tree
Now you’ll be able to click on on the toggle button to see the tags in tree mode and it is possible for you to to see the guardian/baby relationship between each tags.
Click on on the classification to view all its particulars: guardian tags, attributes, and property at the moment tagged with the classification.
1.3 Information Shopper – joe_analyst person
The final step on the Classification authorization course of is to validate from the information client function that the controls are in place and the insurance policies are utilized appropriately.
After efficiently logging in with person joe_analyst:
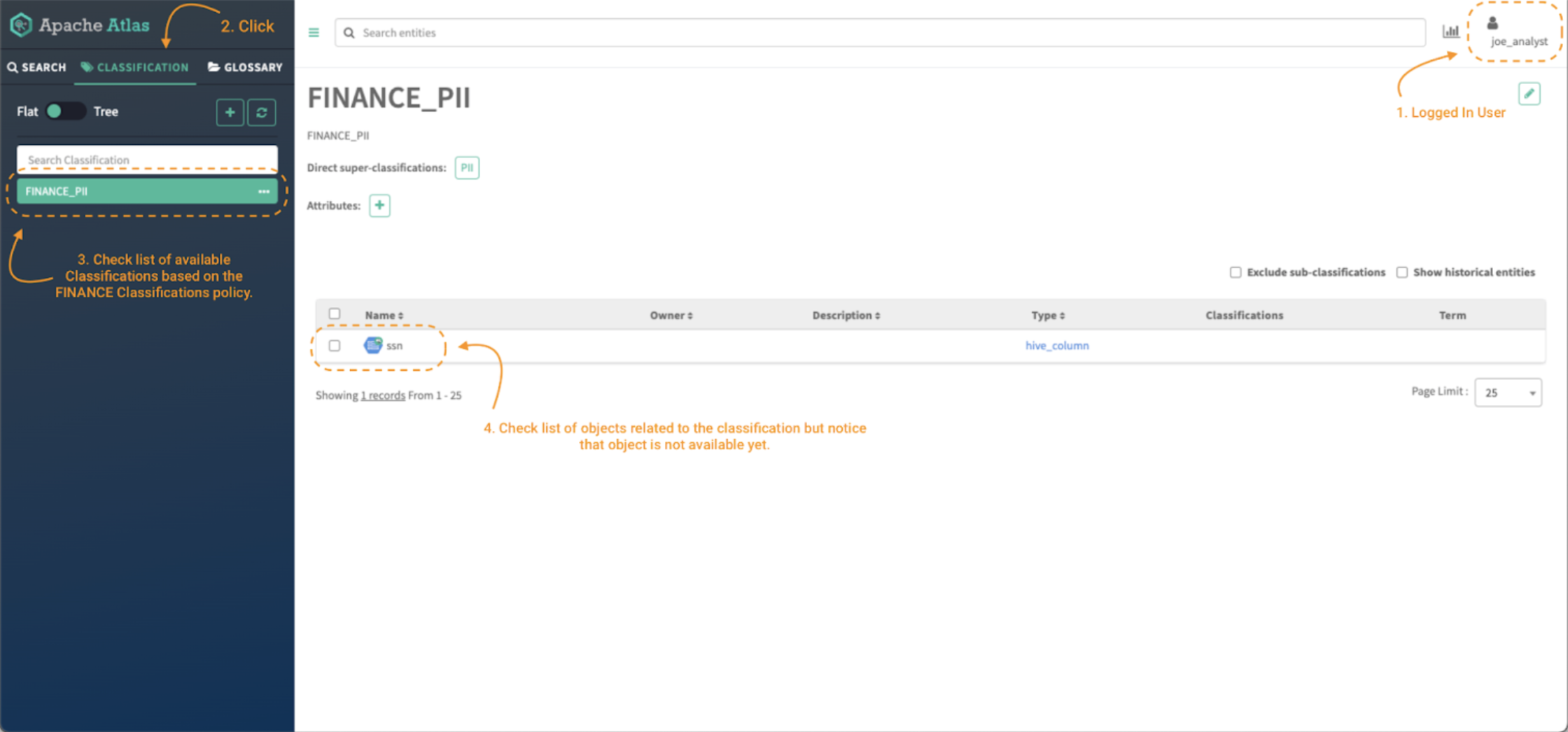
Picture 7 – Atlas classifications for finance knowledge client
To validate that the coverage is utilized and that solely classifications beginning with the phrase FINANCE may be accessed primarily based on the extent of permissions outlined within the coverage, click on on the Classifications tab (notice 2) and verify the checklist obtainable. (notice 3)
Now, to have the ability to entry the content material of the entities (notice 4), it’s required to present entry to the Atlas Entity Sort class and to the particular entities with the corresponding degree of permissions primarily based on our enterprise necessities. The subsequent part will cowl simply that.
2. Authorization for Entity Sorts, Labels and Enterprise Metadata
On this part, we are going to clarify how one can defend extra kinds of objects that exist in Atlas, that are necessary inside a knowledge governance technique; particularly, entities, labels, and enterprise metadata.
Entities in Apache Atlas are a selected occasion of a “sort” of factor: they’re the core metadata object that symbolize knowledge property in your platform. For instance, think about you will have a knowledge desk in your lakehouse, saved within the Iceberg desk format, known as “sales_q3.” This might be mirrored in Apache Atlas by an entity sort known as “ceberg desk,” and an entity named “sales_q3,” a specific occasion of that entity sort. There are numerous entity varieties configured by default within the Cloudera platform, and you may outline new ones as properly. Entry to entity varieties, and particular entities, may be managed via Ranger insurance policies.
Labels are phrases or phrases (strings of characters) that you would be able to affiliate with an entity and reuse for different entities. They’re a lightweight approach so as to add data to an entity so you could find it simply and share your data concerning the entity with others.
Enterprise metadata are units of associated key-value pairs, outlined prematurely by admin customers (for instance, knowledge stewards). They’re so named as a result of they’re usually used to seize enterprise particulars that may assist manage, search, and handle metadata entities. For instance, a steward from the advertising division can outline a set of attributes for a marketing campaign, and add these attributes to related metadata objects. In distinction, technical particulars about knowledge property are often captured extra straight as attributes on entity cases. These are created and up to date by processes that monitor knowledge units within the knowledge lakehouse or warehouse, and aren’t usually personalized in a given Cloudera surroundings.
With that context defined, we are going to transfer on to setting insurance policies to regulate who can add, replace, or take away varied metadata on entities. We are able to set fine-grained insurance policies individually for each labels and enterprise metadata, in addition to classifications. These insurance policies are outlined by the information steward, with the intention to management actions undertaken by knowledge curators and shoppers.
2.1 Information Steward – admin person
First, it’s necessary to guarantee that the customers have entry to the entity varieties within the system. This can enable them to filter their search when on the lookout for particular entities.
So as to take action, we have to create a coverage:
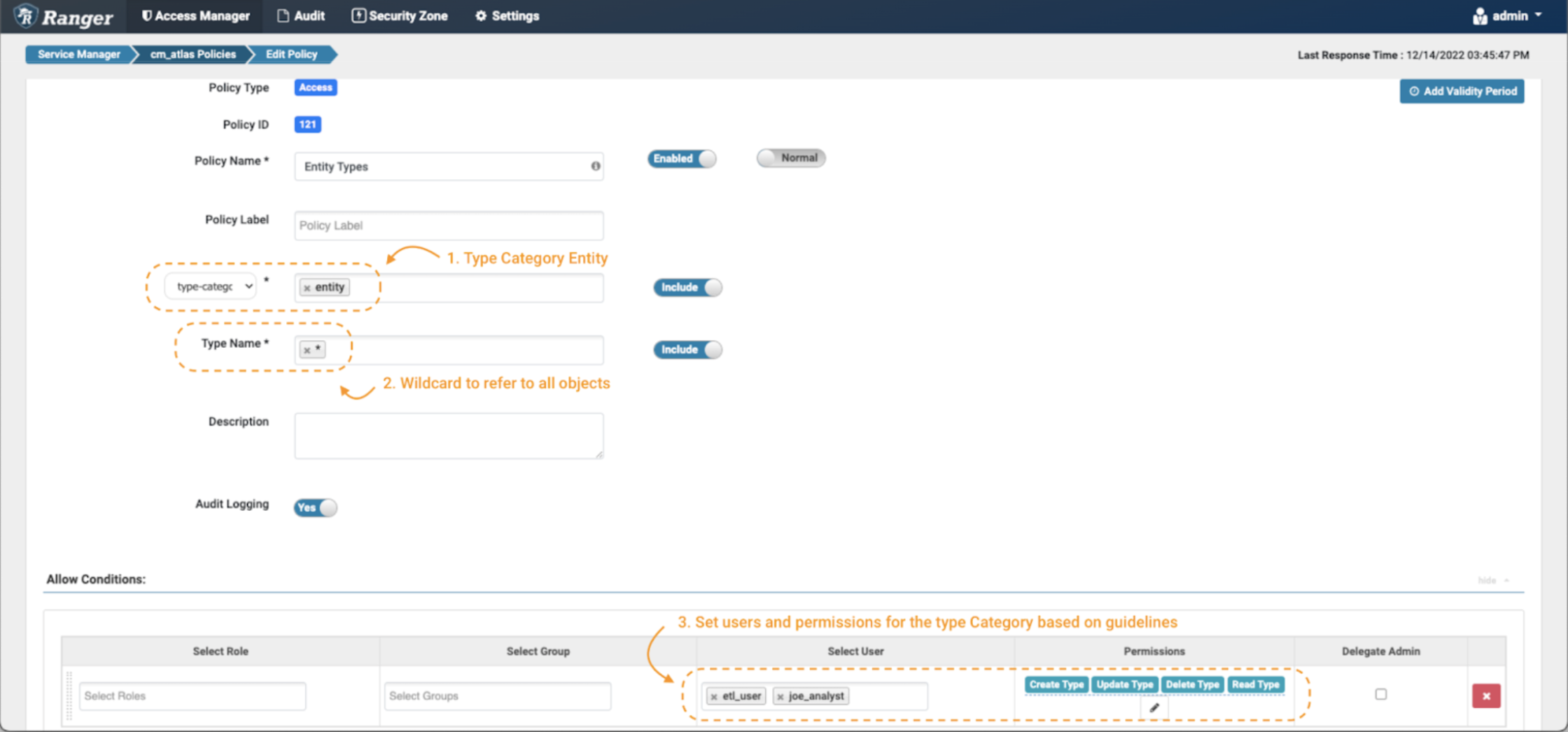
Picture 8 – Atlas entity sort insurance policies
Within the create coverage web page, outline the identify and labels as described earlier than. Then, choose the type-category “entity”(notice 1). Use the wildcard notation (*) (notice 2) to indicate all entity varieties, and grant all obtainable permissions to etl_user and joe_analyst.(notice 3)
This can allow these customers to see all of the entity varieties within the system.
The subsequent step is to permit knowledge client joe_analyst to solely have learn entry on the entities which have the finance classification tags. This can restrict the objects that he’ll be capable of see on the platform.
To do that, we have to comply with the identical course of to create insurance policies as proven within the earlier part, however with some modifications on the coverage particulars:
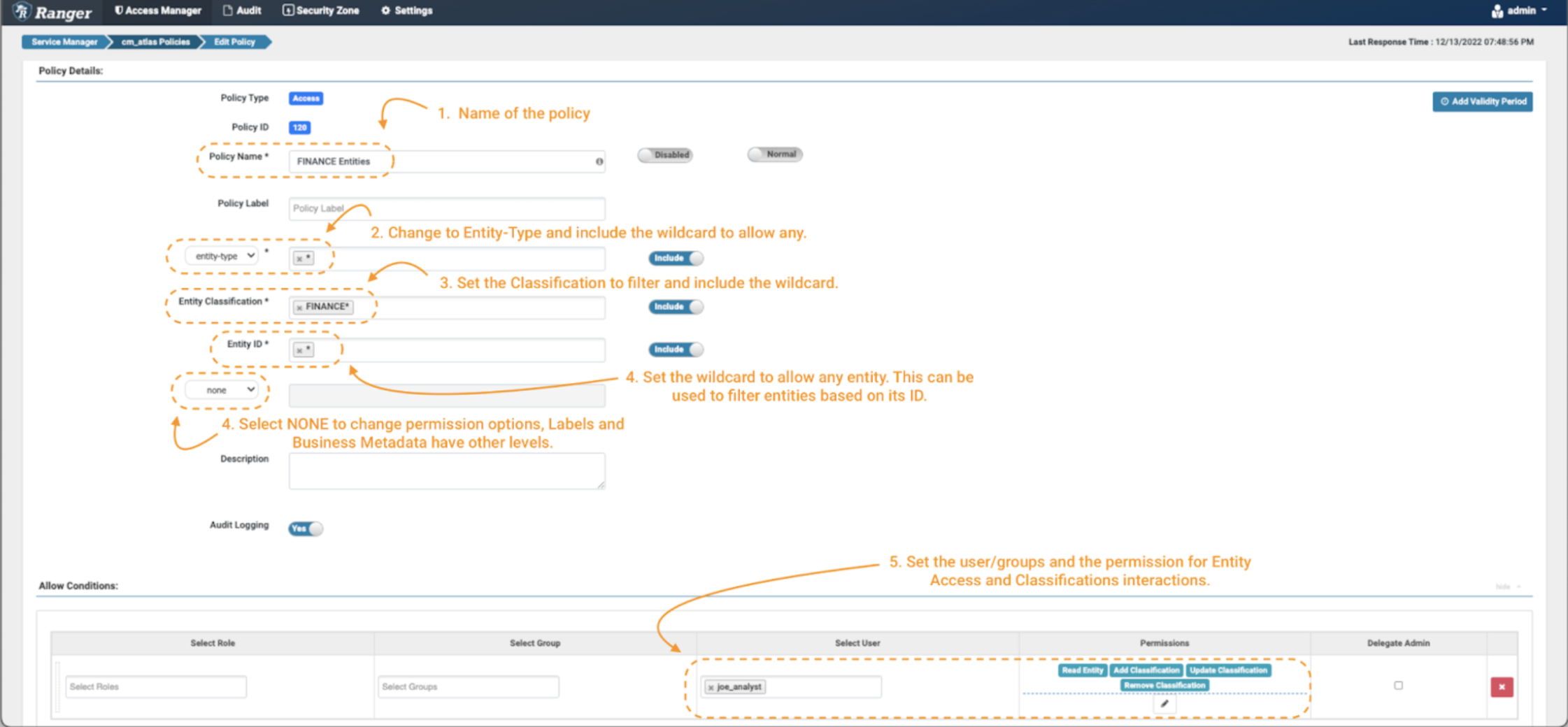
Picture 9 – Instance Atlas finance entity insurance policies
- As all the time, identify (and label) the coverage to allow straightforward administration later.
- The primary necessary change is that the coverage is utilized on an “entity-type” and never in a “type-category.” Choose “entity-type” within the drop-down menu (notice 2) and kind the wildcard to use it to all of the entity varieties.
- Some extra fields will seem within the kind. Within the entity classification discipline you’ll be able to specify tags that exist on the entities you need to management. In our case, we need to solely enable objects which are tagged with phrases that begin with “finance.” Use the expression FINANCE*. (notice 3)
- Subsequent, filter the entities to be managed via the entity ID discipline. On this train, we are going to use the wildcard (*) (notice 4) and for the extra fields we are going to choose “none.” This button will replace the checklist of permissions that may be enforced within the circumstances panel. (notice 4)
- As a knowledge client, we wish the joe_analyst person to have the ability to see the entities. To implement this, choose the Learn Entity permission. (notice 5)
- Add a brand new situation for the information curator etl_user however this time embrace permissions to change the tags appropriately, by including the Add Classification, Replace Classification & Take away Classification permissions to the particular person.
On this approach, entry to particular entities may be managed utilizing extra metadata objects like classification tags. Atlas supplies another metadata objects that can be utilized not solely to counterpoint the entities registered within the platform, but additionally to implement a governance technique over these objects, controlling who can entry and modify them. That is the case for the labels and the enterprise metadata.
If you wish to implement some management over who can add or take away labels:
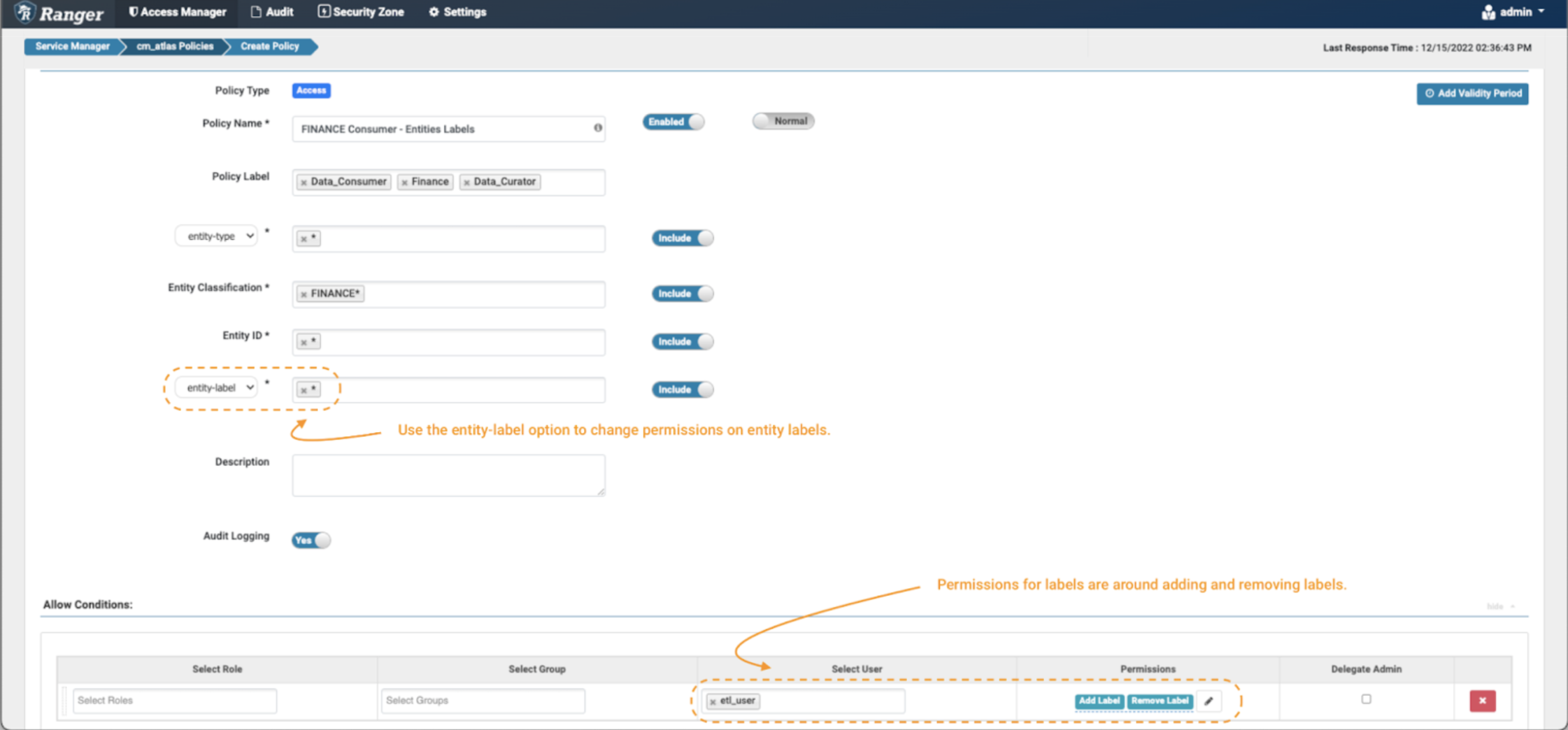
Picture 10 – Instance Atlas finance label coverage
- The one distinction between setting a coverage for labels versus the earlier examples is setting the extra fields filter to “entity-label” as proven within the picture and fill with the values of labels that need to be managed. On this case, we use the wildcard (*) to allow operations on any label on entities tagged with FINANCE* classifications.
- When the entity-label is chosen from the drop-down, the permissions checklist might be up to date. Choose Add Label & Take away Label permission to grant the information curator the choice so as to add and take away labels from entities.
The identical precept may be utilized to regulate the permissions over enterprise metadata:
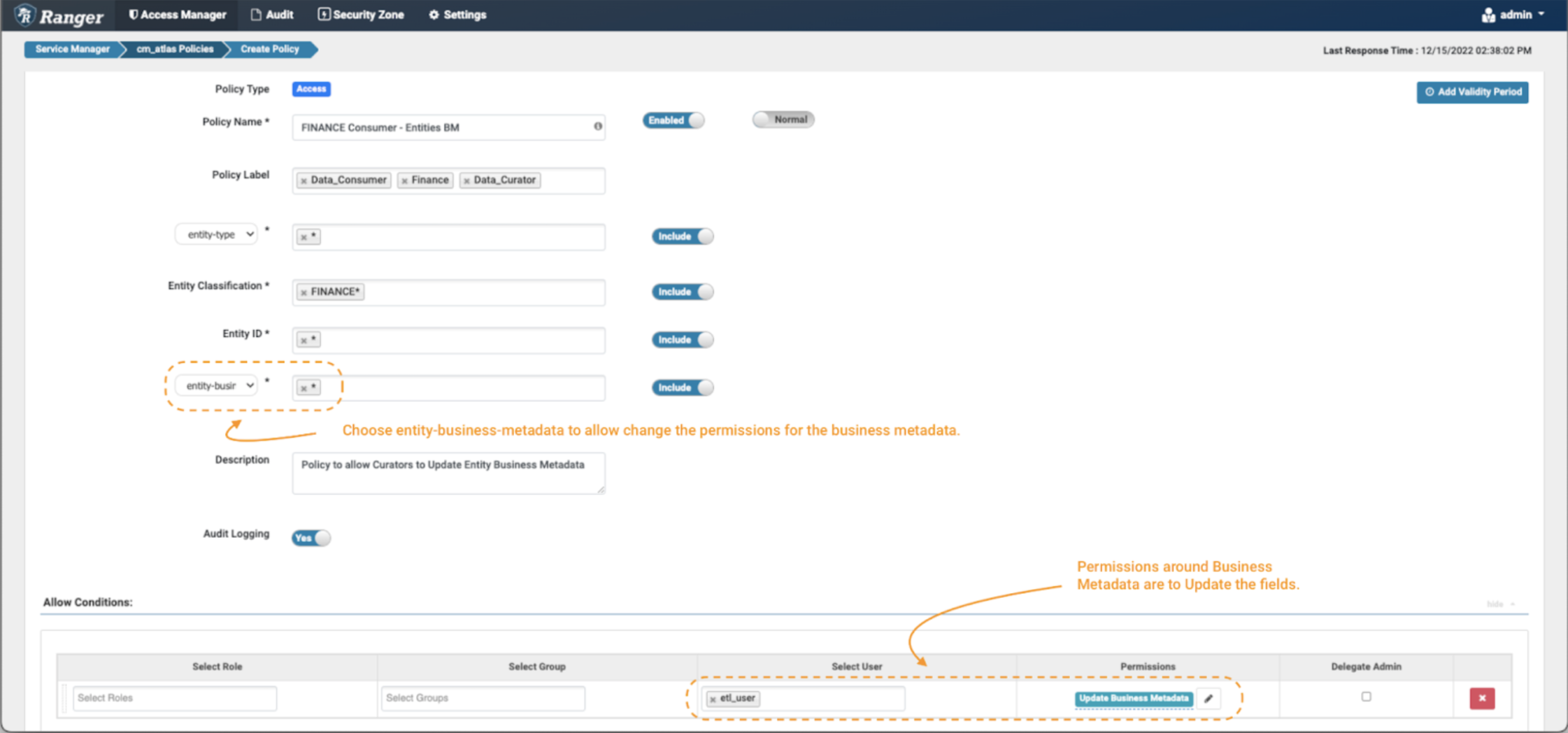
Picture 11 – Instance Atlas finance enterprise metadata coverage
- On this case, one should set the extra fields filter to “entity-business-metadata” as proven within the picture and fill with the values of enterprise metadata attributes that need to be protected. On this instance, we use the wildcard (*) to allow operations on all enterprise metadata attributes on entities tagged with FINANCE* classifications.
- Whenever you allow the entity-business-metadata drop-down, the permissions checklist might be up to date. Choose Replace Enterprise Metadata permission to grant the information curator the choice to change the enterprise metadata attributes of monetary entities.
As a part of the effective grained entry management offered by Apache Ranger over Apache Atlas objects, one can create insurance policies that use an entity ID to specify the precise objects to be managed. Within the examples above we’ve got usually used the wildcard (*) to discuss with “all entities;” beneath, we are going to present a extra focused use-case.
On this situation, we need to create a coverage pertaining to knowledge tables that are a part of a selected undertaking, named “World Huge Financial institution.” As a regular, the undertaking homeowners required that each one the tables are saved in a database known as “worldwidebank.”
To fulfill this requirement, we are able to use one of many entity varieties pre-configured in Cloudera’s distributions of Apache Atlas, particularly “hive_table”. For this entity sort, identifiers all the time start with the identify of the database to which the desk belongs. We are able to leverage that, utilizing Ranger expressions to filter all of the entities that belong to the “World Huge Financial institution” undertaking.
To create a coverage to guard the worldwidebank entities:
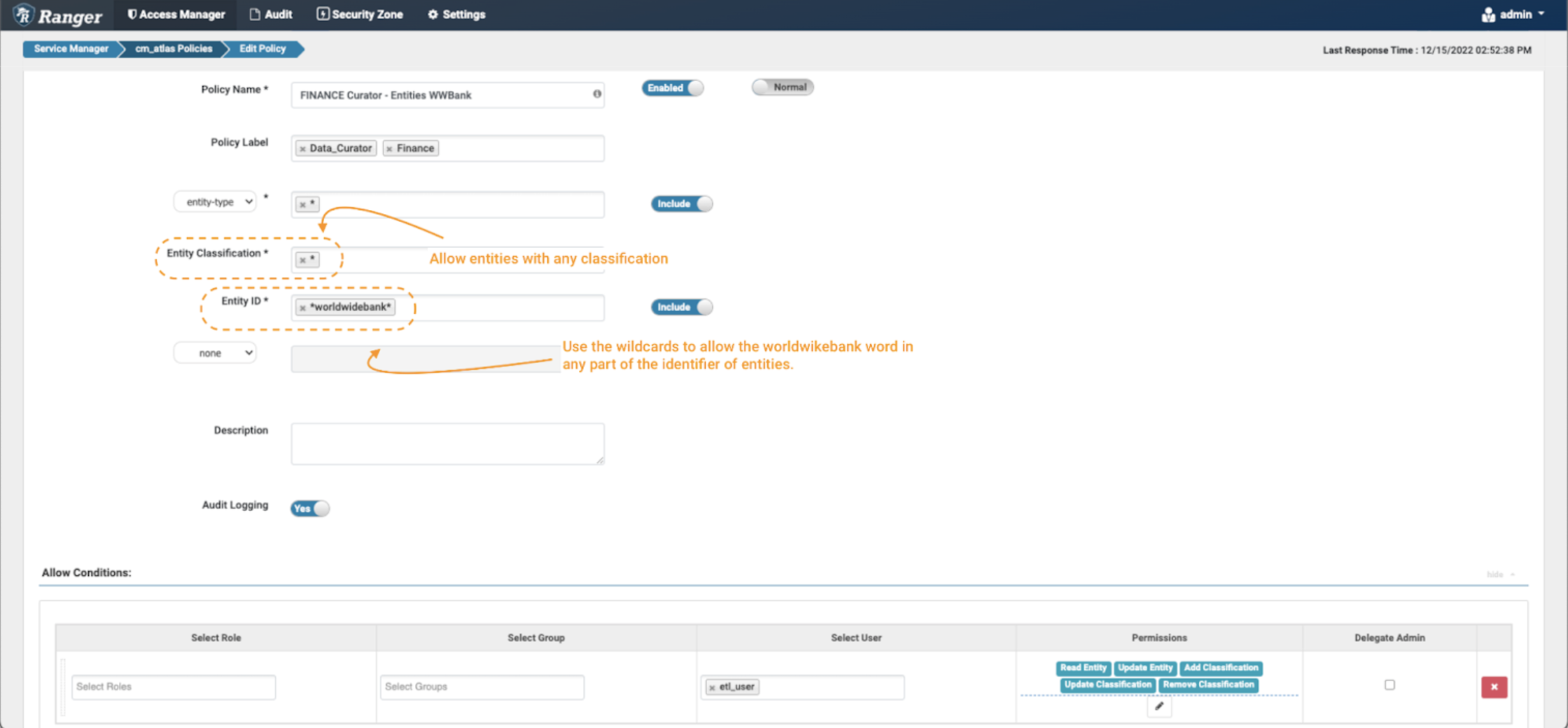
Picture 12 – Instance Atlas Worldwide Financial institution entity coverage
- Create a brand new coverage, however this time don’t specify any entity classification, use the wildcard “*” expression.
- Within the entity ID discipline use the expression: *worldwidebank*
- Within the Situations, choose the permissions Learn Entity, Replace Entity, Add Classification, Replace Classification & Take away Classification to the information curator etl_user to have the ability to see the small print of those entities and enrich/modify and tag them as wanted.
2.2 Information Curator – etl_user person
As a way to enable finance knowledge client joe_analyst to make use of and entry the worldwidebank undertaking entities, the information curator etl_user should tag the entities with the accepted classifications and add the required labels and enterprise metadata attributes.
Login to Atlas and comply with the method to tag the suitable entities:
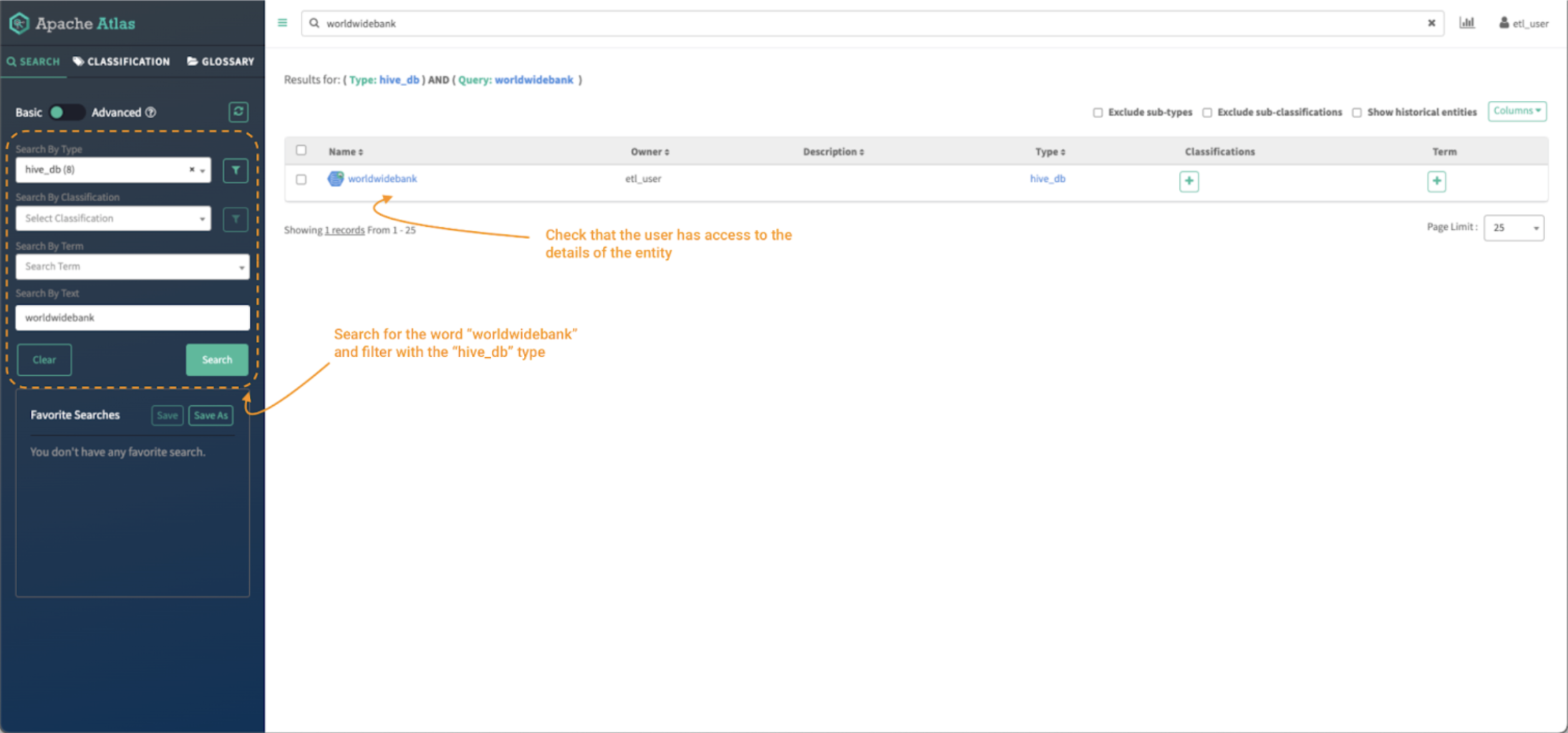
Picture 13 – Information curator entity search
- First, seek for the worldwidebank property utilizing the search bar. You too can use the “search by sort” filter on the left panel to restrict the search to the “hive_db” entity sort.
- As knowledge curator, it’s best to be capable of see the entity and be allowed to entry the small print of the worldwidebank database entity. It ought to have a clickable hyperlink to the entity object
- Click on on the entity object to see its particulars.
After clicking the entity identify, the entity particulars web page is proven:
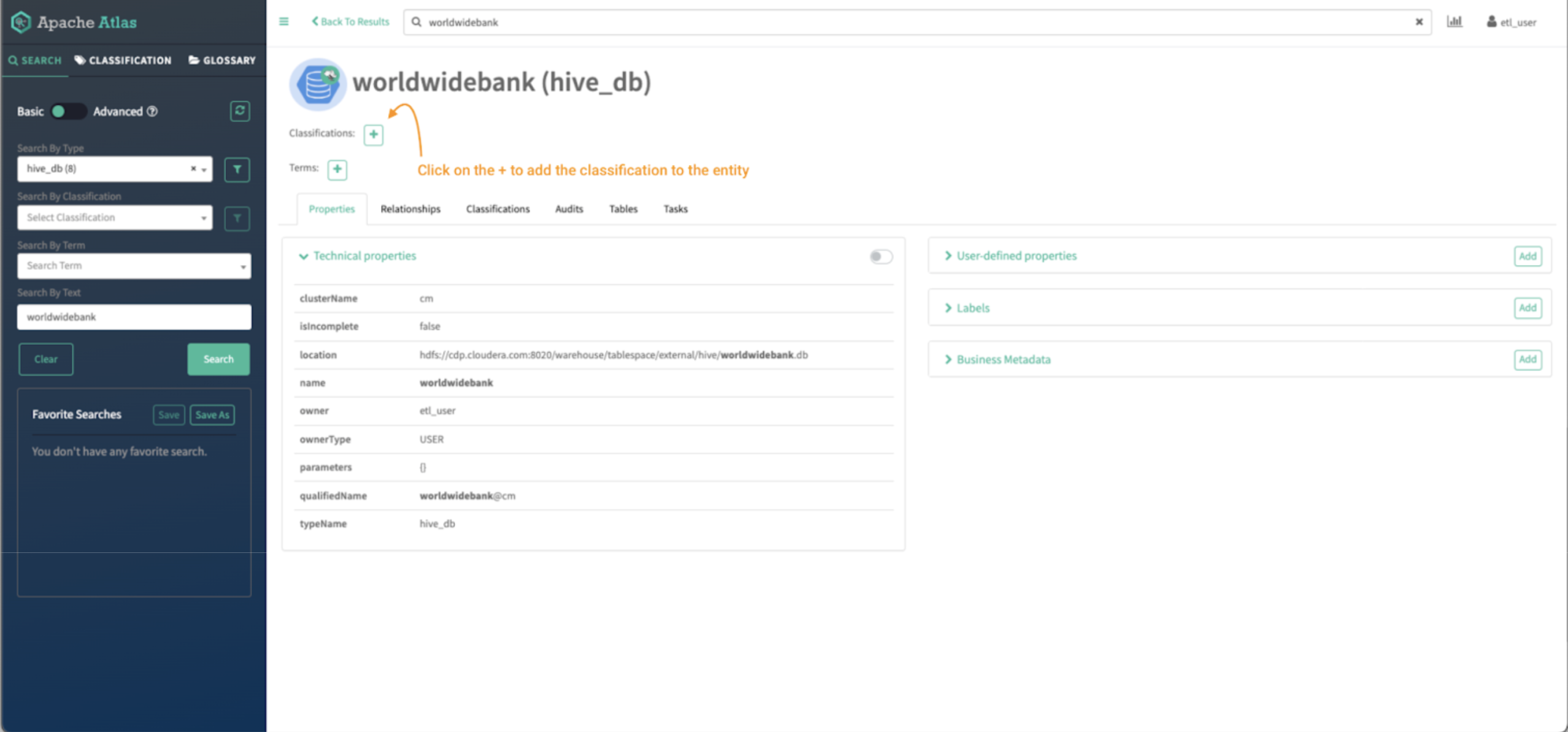
Picture 14 – Worldwide Financial institution database entity element
Within the high of the display, you’ll be able to see the classifications assigned to the entity. On this case there are not any tags assigned. We are going to assign one by clicking on the “+” signal.
Within the “Add Classification” display:
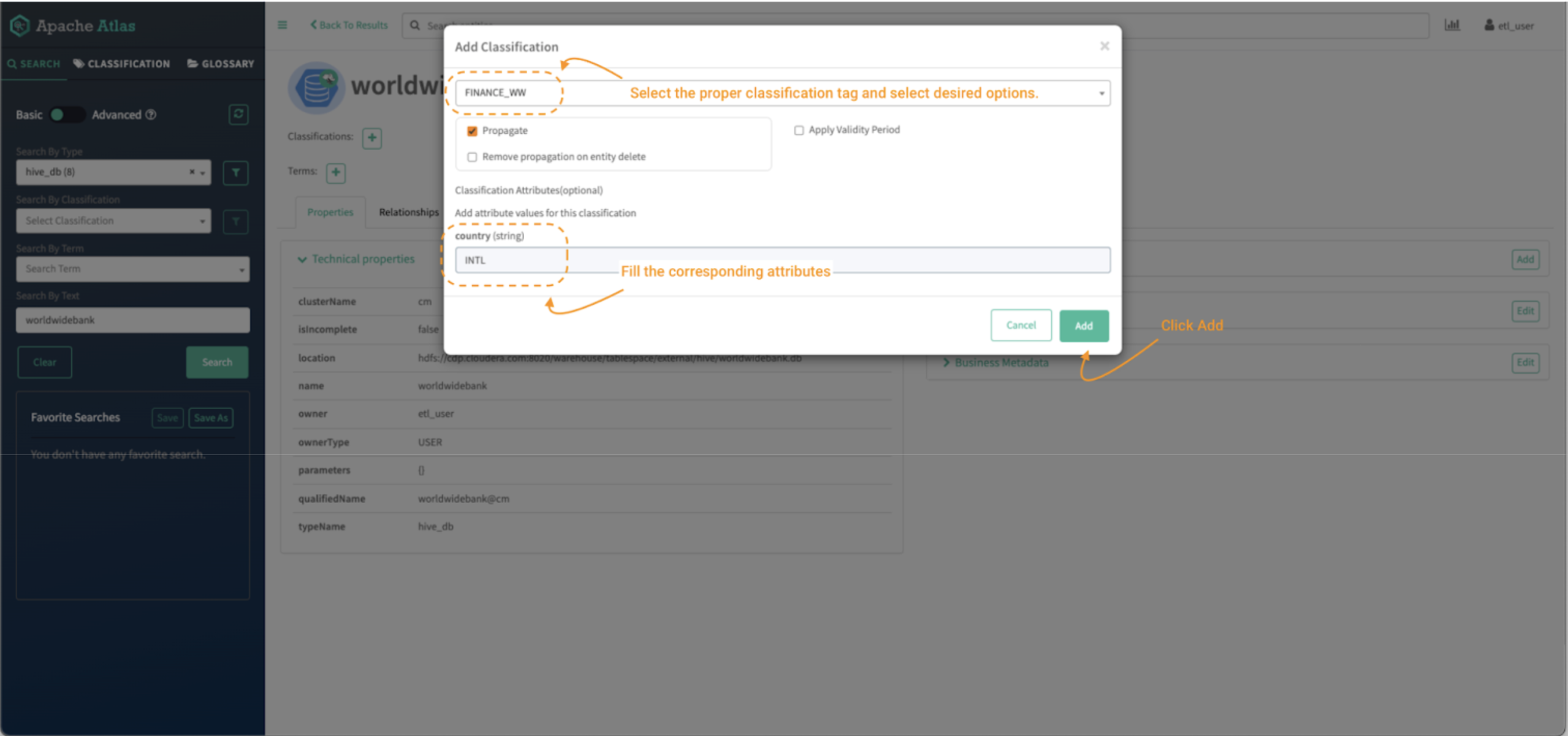
Picture 15 – Worldwide Financial institution database tag course of
- Seek for the FINANCE_WW tag and choose it.
- Then fill the suitable attributes if the classification tag has any. (Optionally available in Picture 5, within the 1.2 Information Curator – etl_user person part above.)
- Click on on “add.”
That can tag an entity with the chosen classification.
Now, enrich the worldwidebank hive_db entity with a brand new label and a brand new enterprise metadata attribute known as “Venture.”
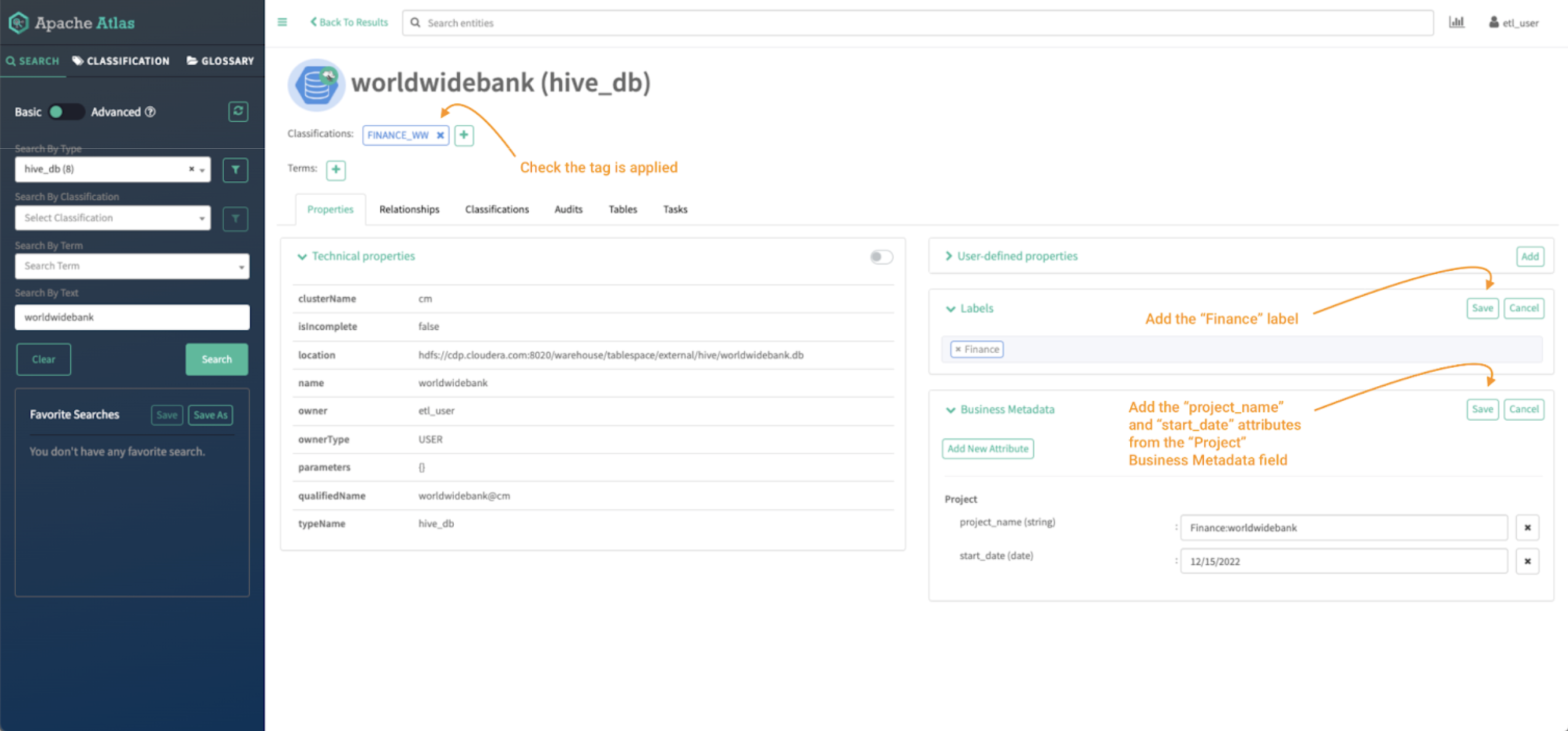
Picture 16 – Worldwide Financial institution database tag course of
So as to add a label, click on “Add” on the labels menu.
- Sort the label within the house and click on “save.”
So as to add a enterprise metadata attribute, click on “Add” on the enterprise metadata menu.
- Click on on “Add New Attribute” if it’s not assigned or “edit” if it already exists.
- Choose the attribute you need to add and fill the small print and hit “save.”
NOTE: The creation of the enterprise metadata attributes shouldn’t be included within the weblog however the steps may be adopted right here.
With the “worldwidebank” Hive object tagged with the “FINANCE_WW” classification, the information client ought to be capable of have entry to it and see the small print. Additionally, you will need to validate that the information client additionally has entry to all the opposite entities tagged with any classification that begins with “finance.”
2.3 Information Shopper – joe_analyst person
To validate that the insurance policies are utilized appropriately, login into Atlas:
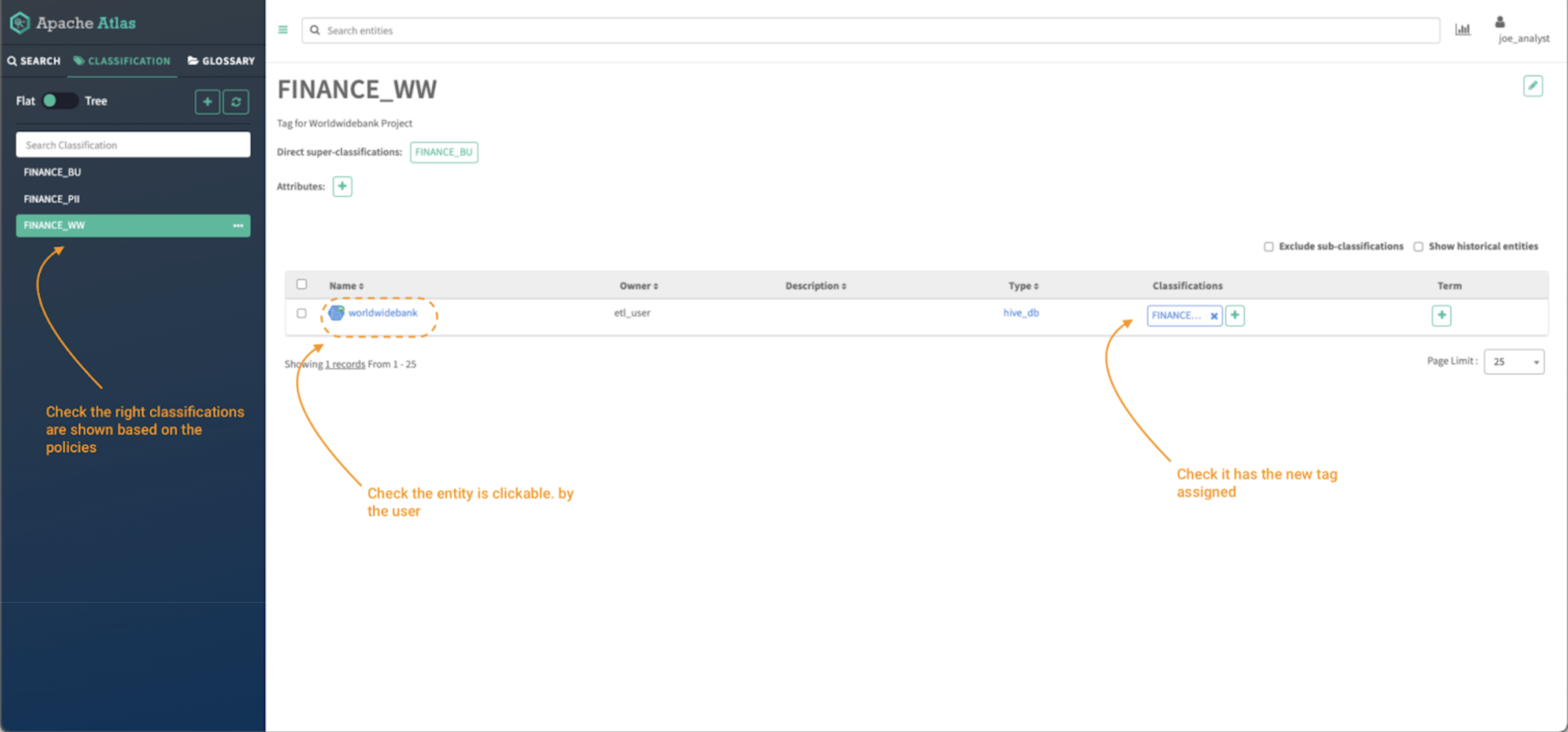
Picture 17 – Finance knowledge property
Click on on the classifications tab and validate:
- The checklist of tags which are seen primarily based on the insurance policies created within the earlier steps. All of the insurance policies should begin with the phrase “finance.”
Click on on the FINANCE_WW tag and validate the entry to the “worldwidebank” hive_db object.
After clicking on the “worldwidebank” object:
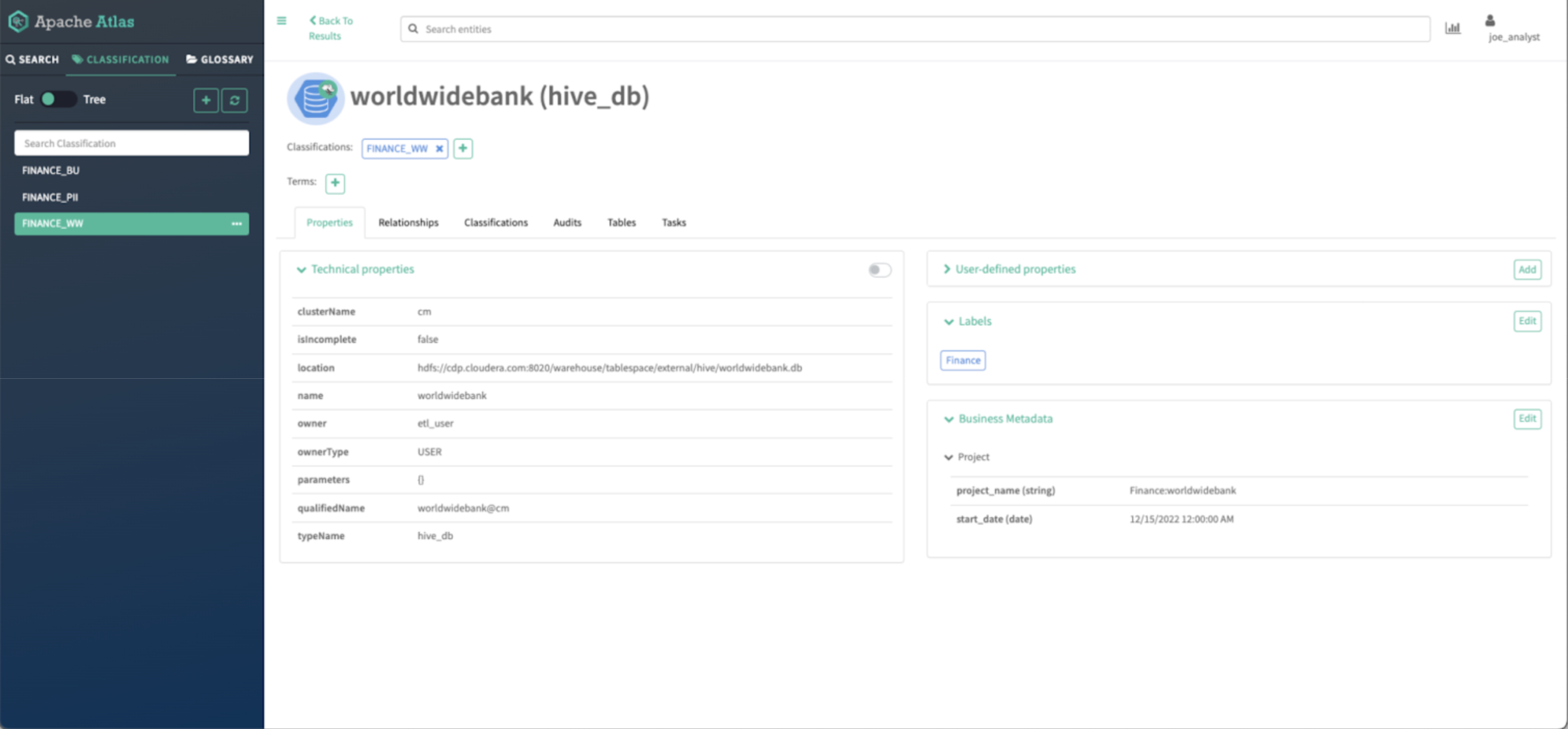
Picture 18 – WorldWideBank database asset particulars
You may see all the small print of the asset that the place enriched by the finance knowledge curator in earlier steps:
- You need to see all of the technical properties of the asset.
- You need to be capable of see the tags utilized to the asset
- You need to see the labels utilized to the asset.
- You need to see the enterprise metadata attributes assigned to the asset.
3. Authorization for Glossary and Glossary Phrases
On this part, we are going to clarify how a knowledge steward can create insurance policies to permit fine-grained entry controls over glossaries and glossary phrases. This enables knowledge stewards to regulate who can entry, enrich or modify glossary phrases to guard the content material from unauthorized entry or errors.
A glossary supplies applicable vocabularies for enterprise customers and it permits the phrases (phrases) to be associated to one another and categorized in order that they are often understood in several contexts. These phrases may be then utilized to entities like databases, tables, and columns. This helps summary the technical jargon related to the repositories and permits the person to find and work with knowledge within the vocabulary that’s extra acquainted to them.
Glossaries and phrases may also be tagged with classifications. The good thing about that is that, when glossary phrases are utilized to entities, any classifications on the phrases are handed on to the entities as properly. From a knowledge governance course of perspective, which means that enterprise customers can enrich entities utilizing their very own terminology, as captured in glossary phrases, and that may routinely apply classifications as properly, that are a extra “technical” mechanism, utilized in defining entry controls, as we’ve got seen.
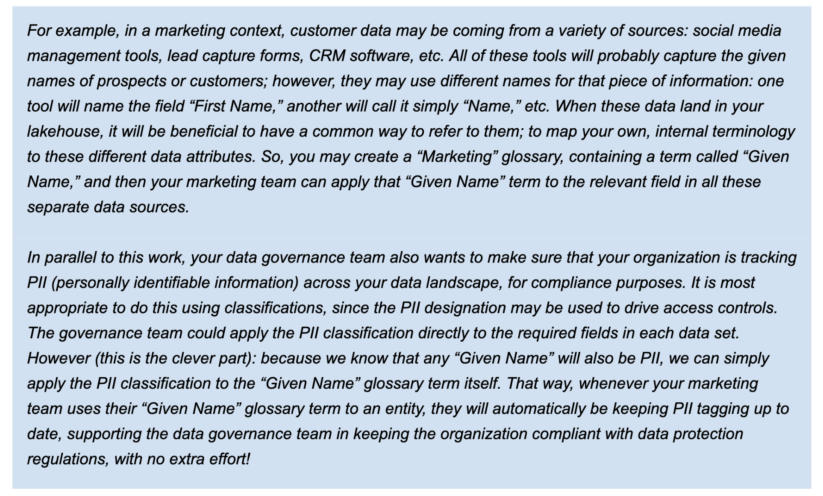
First, we are going to present how as a knowledge steward you’ll be able to create a coverage that grants learn entry to glossary objects with particular phrases within the identify and validate that the information client is allowed to entry the particular content material.
3.1 Information Steward – admin person
To create a coverage to regulate entry to glossaries and phrases, you’ll be able to:
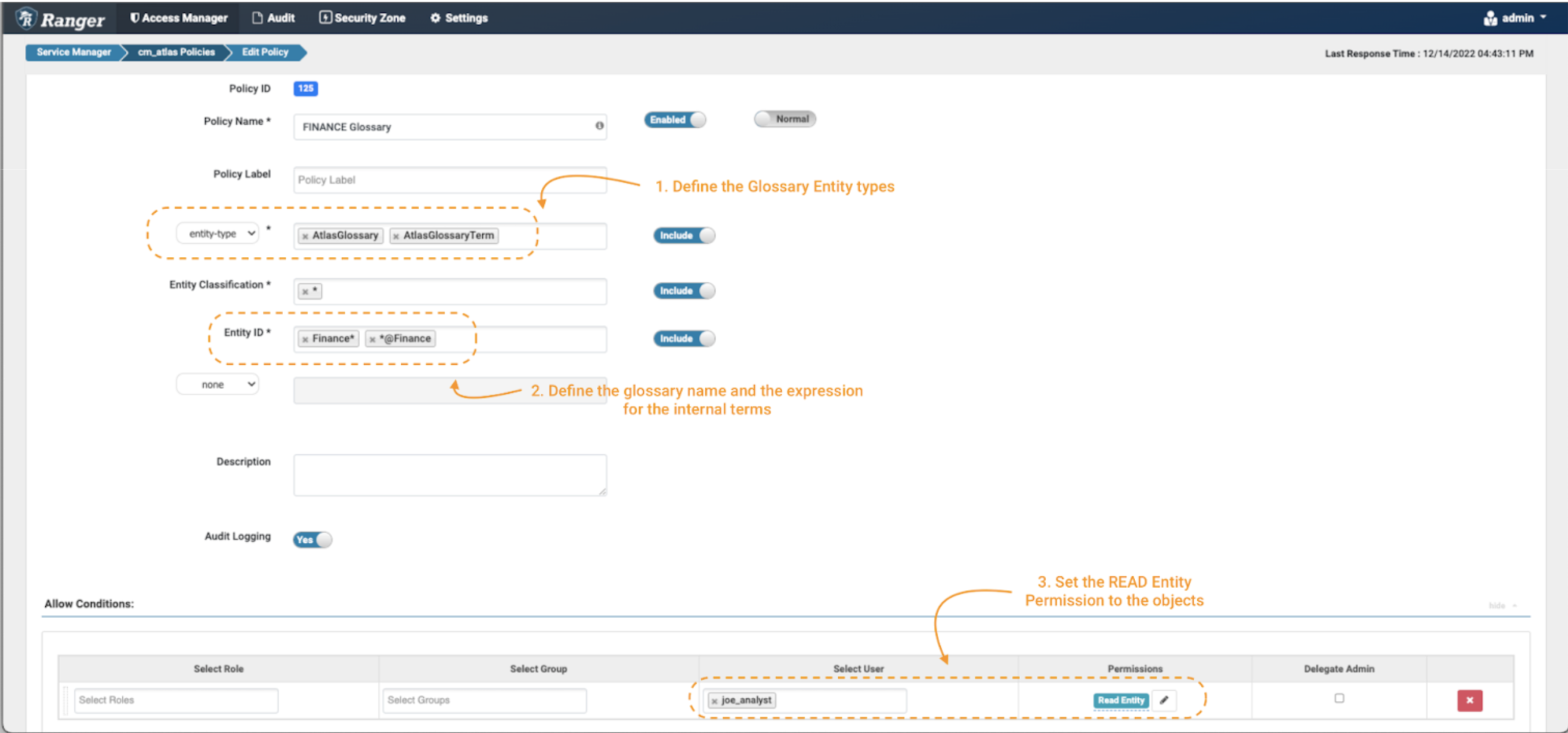
Picture 19 – Glossary management coverage
- Create a brand new coverage, however this time use the “entity-type” AtlasGlossary and AtlasGlossaryTerm. (notice 1)
- Within the entity classifications discipline, use the wildcard expression: *
- The entity ID is the place you’ll be able to outline which glossaries and phrases you need to defend. In Atlas, all of the phrases of a glossary embrace a reference to it with an “@” on the finish of its identify (ex. time period@glossary). To guard the “Finance” glossary itself, use Finance*; and to guard is phrases, use *@Finance (notice 2).
- Within the Situations, choose the permissions Learn Entity to the information client joe_analyst to have the ability to see the glossary and its phrases. (notice 3)
3.2 Information Shopper – joe_analyst person
To validate that solely “Finance” glossary objects may be accessed:
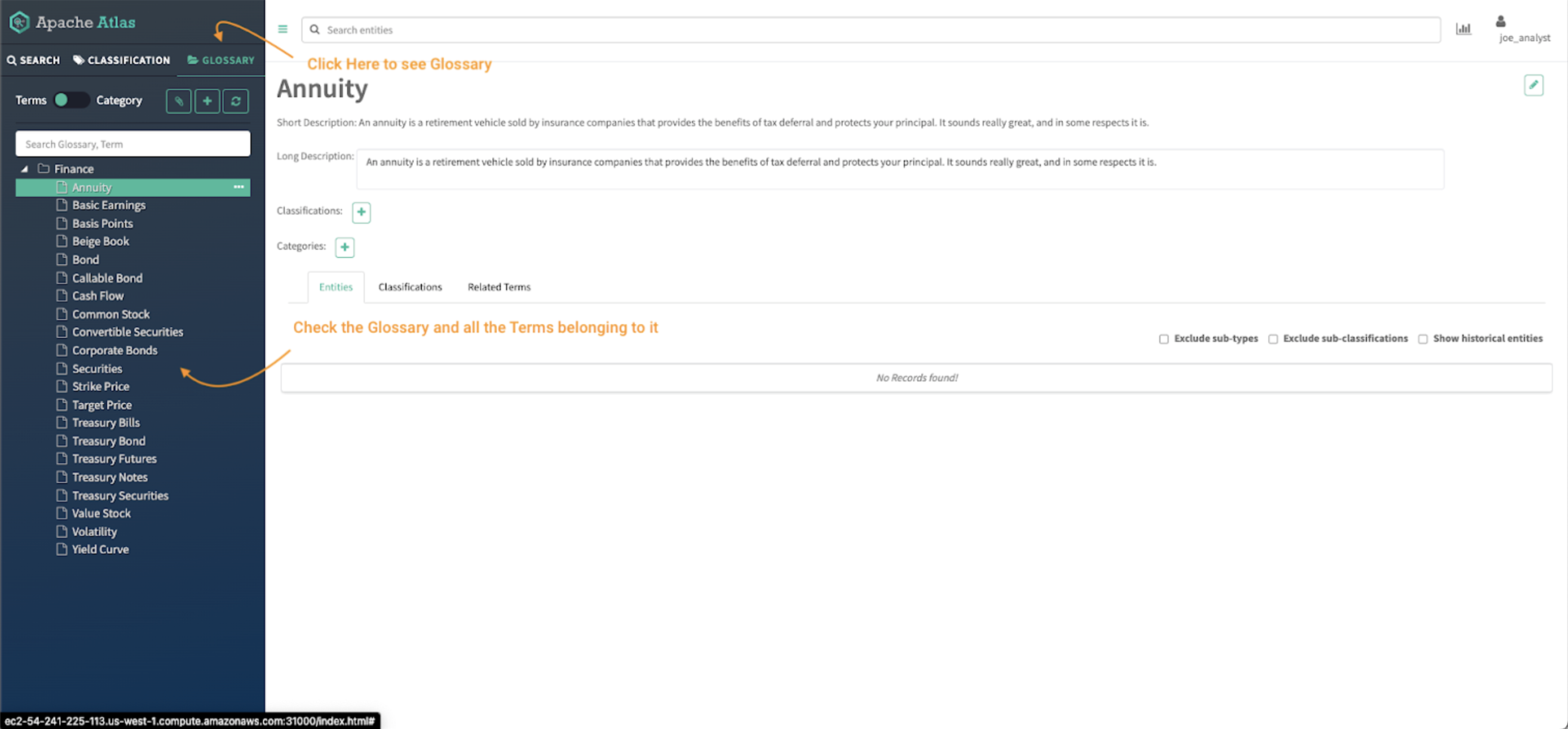
Picture 20 – Finance Atlas glossary
- Click on on the glossary tab within the Atlas panel.
- Examine the glossaries obtainable within the Atlas UI and the entry to the small print of the phrases of the glossary.
Conclusion
This text has proven how a company can implement a effective grained entry management technique over the information governance elements of the Cloudera platform, leveraging each Apache Atlas and Apache Ranger, the basic and integral elements of SDX. Though most organizations have a mature strategy to knowledge entry, management of metadata is usually much less properly outlined, if thought-about in any respect. The insights and mechanisms shared on this article can assist implement a extra full strategy to knowledge in addition to metadata governance. The strategy is crucial within the context of a compliance technique the place knowledge governance elements play a crucial function.
You may study extra about SDX right here; or, we might like to hear from you to debate your particular knowledge governance wants.

