Authorities in Australia, the UK and america this week levied monetary sanctions towards a Russian man accused of stealing information on almost 10 million clients of the Australian medical health insurance big Medibank. 33-year-old Aleksandr Ermakov allegedly stole and leaked the Medibank information whereas working with one in all Russia’s most harmful ransomware teams, however little extra is shared concerning the accused. Right here’s a better take a look at the actions of Mr. Ermakov’s alleged hacker handles.

Aleksandr Ermakov, 33, of Russia. Picture: Australian Division of Overseas Affairs and Commerce.
The allegations towards Ermakov mark the primary time Australia has sanctioned a cybercriminal. The paperwork launched by the Australian authorities included a number of images of Mr. Ermakov, and it was clear they needed to ship a message that this was private.
It’s not arduous to see why. The attackers who broke into Medibank in October 2022 stole 9.7 million data on present and former Medibank clients. When the corporate refused to pay a $10 million ransom demand, the hackers selectively leaked extremely delicate well being data, together with these tied to abortions, HIV and alcohol abuse.
The U.S. authorities says Ermakov and the opposite actors behind the Medibank hack are believed to be linked to the Russia-backed cybercrime gang REvil.
“REvil was among the many most infamous cybercrime gangs on the earth till July 2021 once they disappeared. REvil is a ransomware-as-a-service (RaaS) operation and customarily motivated by monetary achieve,” a assertion from the U.S. Division of the Treasury reads. “REvil ransomware has been deployed on roughly 175,000 computer systems worldwide, with a minimum of $200 million paid in ransom.”
The sanctions say Ermakov glided by a number of aliases on Russian cybercrime boards, together with GustaveDore, JimJones, and Blade Runner. A search on the deal with GustaveDore on the cyber intelligence platform Intel 471 reveals this consumer created a ransomware associates program in November 2021 known as Sugar (a.okay.a. Encoded01), which centered on concentrating on single computer systems and end-users as an alternative of firms.
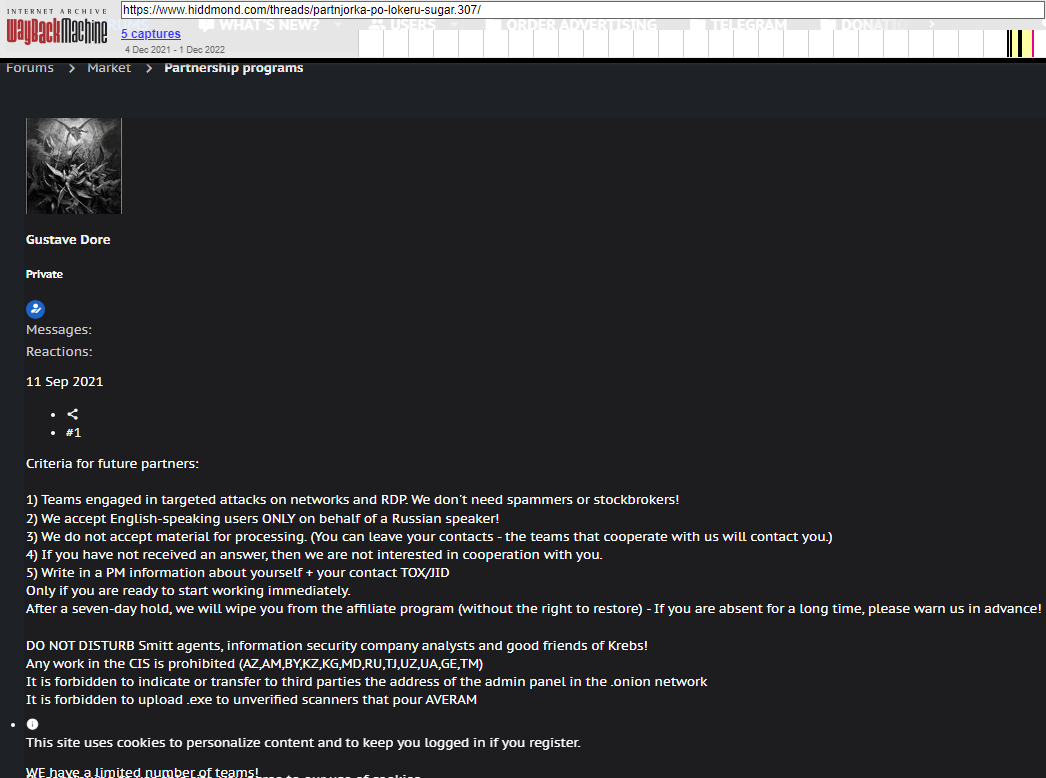
An advert for the ransomware-as-a-service program Sugar posted by GustaveDore warns readers towards sharing info with safety researchers, regulation enforcement, or “associates of Krebs.”
In November 2020, Intel 471 analysts concluded that GustaveDore’s alias JimJones “was utilizing and working a number of completely different ransomware strains, together with a personal undisclosed pressure and one developed by the REvil gang.”
In 2020, GustaveDore marketed on a number of Russian dialogue boards that he was a part of a Russian know-how agency known as Shtazi, which could possibly be employed for laptop programming, internet growth, and “status administration.” Shtazi’s web site stays in operation right now.
A Google-translated model of Shtazi dot ru. Picture: Archive.org.
The third consequence when one searches for shtazi[.]ru in Google is an Instagram publish from a consumer named Mikhail Borisovich Shefel, who promotes Shtazi’s providers as if it have been additionally his enterprise. If this identify sounds acquainted, it’s as a result of in December 2023 KrebsOnSecurity recognized Mr. Shefel as “Rescator,” the cybercriminal identification tied to tens of tens of millions of cost playing cards that have been stolen in 2013 and 2014 from large field retailers Goal and Residence Depot, amongst others.
How shut was the connection between GustaveDore and Mr. Shefel? The Treasury Division’s sanctions web page says Ermakov used the e-mail handle ae.ermak@yandex.ru. A seek for this e-mail at DomainTools.com reveals it was used to register only one area identify: millioner1[.]com. DomainTools additional finds {that a} telephone quantity tied to Mr. Shefel (79856696666) was used to register two domains: millioner[.]pw, and shtazi[.]internet.
The December 2023 story right here that outed Mr. Shefel as Rescator famous that Shefel just lately modified his final identify to “Lenin,” and had launched a service known as Lenin[.]biz that sells bodily USSR-era Ruble notes that bear the picture of Vladimir Lenin, the founding father of the Soviet Union. The Instagram account for Mr. Shefel contains photos of stacked USSR-era Ruble notes, in addition to a number of hyperlinks to Shtazi.

The Instagram account of Mikhail Borisovich Shefel, aka MikeMike aka Rescator.
In a report printed this week, Intel 471 stated investigators linked Ermakov to REvil as a result of the stolen Medibank information was printed on a weblog that had one time been managed by REvil associates who carried out assaults and paid an affiliate charge to the gang.
However by the point of the Medibank hack, the REvil group had largely scattered after a collection of high-profile assaults led to the group being disrupted by regulation enforcement. In November 2021, Europol introduced it arrested seven REvil associates who collectively made greater than $230 million value of ransom calls for since 2019. On the identical time, U.S. authorities unsealed two indictments towards a pair of accused REvil cybercriminals.
“The posting of Medibank’s information on that weblog, nevertheless, indicated a reference to that group, though the connection wasn’t clear on the time,” Intel 471 wrote. “This is sensible on reflection, as Ermakov’s group had additionally been a REvil affiliate.”
It’s straightforward to dismiss sanctions like these as ineffective, as a result of so long as Mr. Ermakov stays in Russia he has little to concern of arrest. Nevertheless, his alleged position as an obvious high member of REvil paints a goal on him as somebody who possible possesses massive sums of cryptocurrency, stated Patrick Grey, the Australian co-host and founding father of the safety information podcast Dangerous Enterprise.
“I’ve seen a couple of folks poo-poohing the sanctions…however the sanctions element is definitely much less vital than the doxing element,” Grey stated. “As a result of this man’s life simply bought much more sophisticated. He’s in all probability going to need to pay some bribes to remain out of hassle. Each single prison in Russia now is aware of he’s a susceptible 33 yr outdated with an absolute ton of bitcoin. So this isn’t a contented time for him.”
