Digital Safety
In at present’s digitally interconnected world, superior cyber capabilities have turn out to be an exceptionally potent and versatile software of tradecraft for nation-states and criminals alike
29 Jan 2024
•
,
4 min. learn

For hundreds of years, nations have engaged in espionage, spying on their neighbors, allies, and adversaries. Historically, this realm of “espionage” relied closely on human intelligence, however that began altering within the early Nineties with the arrival of applied sciences just like the telegraph, phone cellphone and subsequently radio alerts intelligence (SIGINT). Nevertheless, in at present’s digitally interconnected world, superior cyber capabilities have turn out to be an exceptionally potent and versatile software of tradecraft for nation-states and criminals alike, marking a big evolution in espionage for the twenty first century.
Six benefits of cyber operations
Cyber capabilities are extremely priceless for nation-states pursuing political, financial, and navy targets, providing vital benefits at a comparatively low value by way of sources and threat.
- Cyber operations could be stealthy, permitting for undetected entry to focus on methods for knowledge harvesting or covert actions, as seen in incidents like SolarWinds.
- They will also be loud and disruptive or harmful, as evidenced in conflicts in Ukraine and the Center East.
- Cyber means are manipulative, helpful for influencing situations, and more and more deployed throughout most continents.
- They’re profitable for monetary acquire, as demonstrated by actions attributed to North Korea, financing its navy program via ransomware campaigns.
- They are often outsourced by encouraging third-party operations as mercenaries or hacktivists keen to undertake these assaults in change for cash and even for political targets and beliefs.
- They usually have a excessive diploma of deniability, as it could possibly take time (together with overcoming obfuscation strategies) to hint the origin of an assault with absolute confidence.
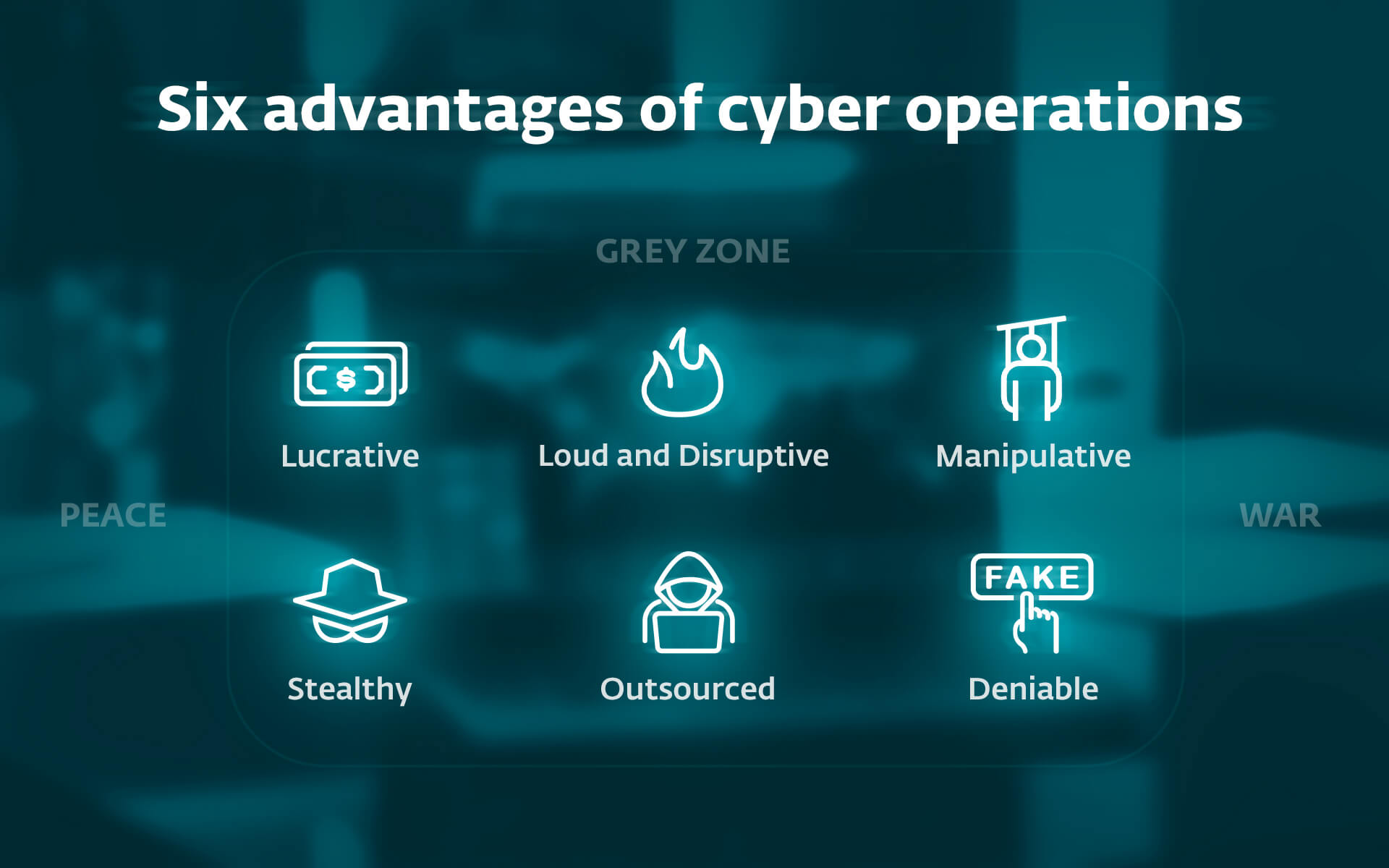
The cyber area can also be blessed with a wide range of techniques, instruments, and strategies, buoyed by a thriving darkish internet market and an infinite array of vulnerabilities to be exploited. Furthermore, the shortage of serious deterrence or punishment for cyber actions provides to its attractiveness for nation-states.
International cyber operations and evolving techniques of main nations
The growing attraction of cyber capabilities amongst nations is obvious, with many striving to maximise their cyber potential. Russia, China, Iran, and North Korea are often talked about for his or her malicious cyber actions. It’s mentioned all international locations spy, however some are seen as going past accepted norms.
China, specifically, has been using cyber’s distinctive capabilities extensively. Intelligence companies from the 5 Eyes nations frequently warn in regards to the widespread actions of China-aligned teams affecting each continent. Most just lately this alliance highlighted the size and class of China’s mental property theft and experience acquisition, which was described as unprecedented.
Russia, amidst its concentrate on Ukraine for disruption and destruction, additionally engages in cyberespionage globally with Europe notably in its crosshairs. Russia can also be alleged to have performed affect campaigns in Africa, focusing on governments with shut Western ties and looking for to undermine governments elsewhere which might be much less supportive of the Russian authorities.
North Korea-aligned teams stay targeted on buying defense-related applied sciences, producing income via ransomware, and conducting espionage, particularly in Asia. The Lazarus group might be probably the most notorious of North Korean aligned hackers, together with an alleged assault on a Spanish aerospace agency.
Iran-aligned teams are increasing their capabilities and attain, extending past their conventional concentrate on the Center East, notably focusing on Israel.
Past these well-known actors, an ever-increasing variety of states are growing their very own capabilities to conduct cyber operations past their borders or goal international entities, together with embassies, worldwide organizations, firms, and people, inside their very own international locations. As an example, the alleged Belarusian group MoustachedBouncer is believed to have the ability to entry a Belarusian telecommunication operator to conduct a “man within the center” assault on international entities inside Belarus.
However when in-house functionality is inadequate, or to reinforce deniability, some nations resort to the personal sector and cyber mercenaries. The variety of nations concerned in cyber operations might conservatively be over 50 and is rising globally. Actually, in keeping with CERT-EU, there have been 151 malicious actions of curiosity focusing on EU establishments, together with by Turkey-aligned and Vietnam-aligned teams. This world development underscores the rising significance and evolution of the menace panorama.
A window into a posh world
Actions in our on-line world are glimpses into the complexities of geopolitics, and infrequently assaults can solely be understood via the lens of political intent. The world’s three nice powers are locked in a contest for affect, prosperity, and energy. In most areas, there are stay conflicts, simmering tensions, political, safety, and financial challenges. On this local weather of instability, heightened competitors, typically disillusioned populations, and in a extra digitally related world, cyber is an especially handy software for states to deploy. It’s uncommon these days when bilateral disputes don’t contain some type of cyber dimension both from state actors, their proxies, or aligned/influenced hacktivists. While some contests in our on-line world between nations are predictable, bilateral spats may also erupt with out warning.
Securing settlement on binding worldwide norms of affordable state conduct in our on-line world appears unrealistic within the medium time period regardless of efforts by the UN. Confronted with this uncomfortable actuality, the necessity for better worldwide cooperation, coverage frameworks, and consciousness campaigns to handle and mitigate the dangers related to these malicious actions is changing into extra urgent than ever. Constructing resilience would require a holistic, society-wide strategy, because the cyber area is about to stay a pivotal battleground in an more and more restive world.

