Authored By Anuradha
McAfee Labs has not too long ago noticed a brand new wave of phishing assaults. On this wave, the attacker has been abusing server-parsed HTML (SHTML) recordsdata. The SHTML recordsdata are generally related to net servers redirecting customers to malicious, credential-stealing web sites or show phishing types domestically inside the browser to reap user-sensitive info.
SHTML Marketing campaign within the discipline:
Determine 1. reveals the geological distribution of McAfee purchasers who detect malicious SHTML recordsdata.
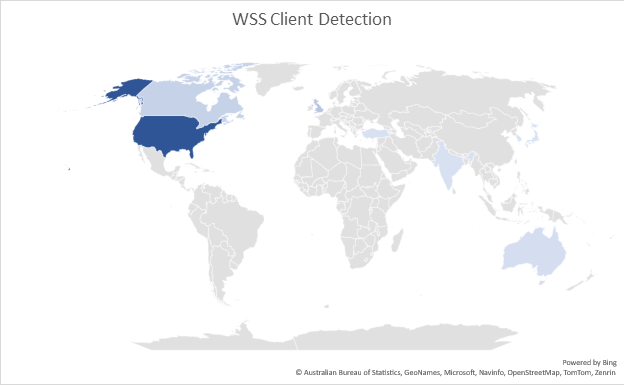
Determine 1. McAfee Shopper Detection of SHTML
Attackers victimize customers by distributing SHTML recordsdata as e-mail attachments. The emotions utilized in such phishing emails embrace a cost affirmation, bill, cargo and so forth., The e-mail comprises a small thread of messages to make the recipient extra curious to open the attachment.
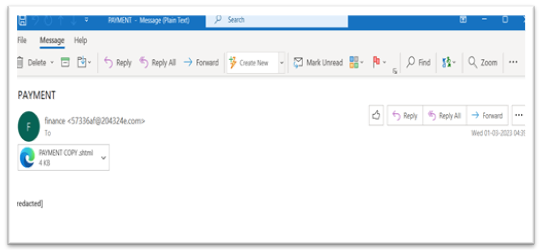
Determine 2. E-mail with SHTML attachment
Evaluation:
When the SHTML attachment is clicked, it opens a blurred pretend doc with a login web page within the browser as proven in Determine 3. To learn the doc, nevertheless, the consumer should enter his/her credentials. In some instances, the e-mail deal with is prefilled.
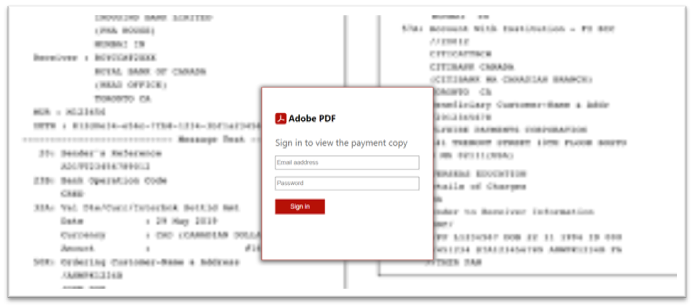
Determine 3. Pretend PDF doc
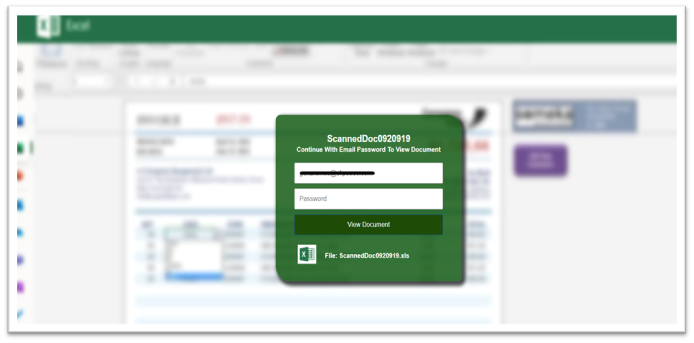
Determine 4. Pretend Excel doc

Determine 5. Pretend DHL Transport doc
Attackers generally use JavaScript within the SHTML attachments that can be used both to generate the malicious phishing type or to redirect or to cover malicious URLs and habits.
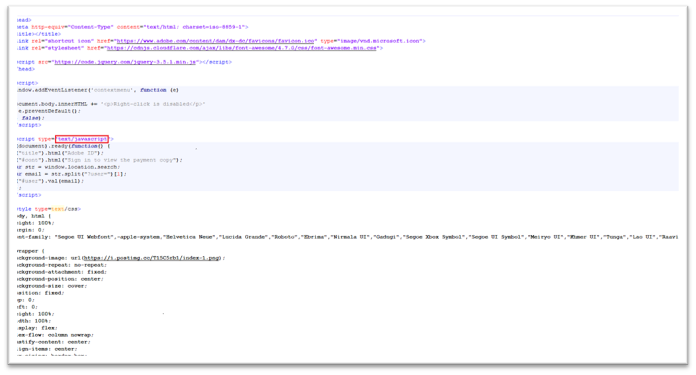
Determine 6. SHTML with JavaScript code
Under is the code snippet that reveals how the blurred background picture is loaded. The blurred photographs are taken from official web sites corresponding to:
https://isc.sans.edu
https://i.gyazo.com
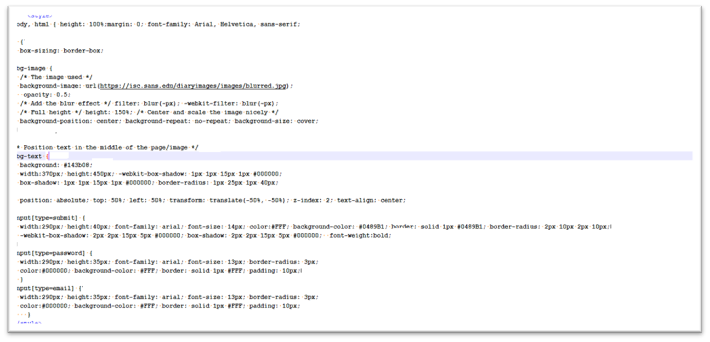
Determine 7. Code to load blurred picture
Abusing submission type service:
Phishing assaults abuse static type service suppliers to steal delicate consumer info, corresponding to Formspree and Formspark
Formspree.io is a back-end service that enables builders to simply add types on their web site with out writing server-side code, it additionally handles type processing and storage. It takes HTML type submissions and sends the outcomes to an e-mail deal with.
The attackers use the formpsree.io URL as an motion URL which defines the place the shape knowledge can be despatched. Under Determine 8. reveals the code snippet for motion URL that works together with POST methodology.
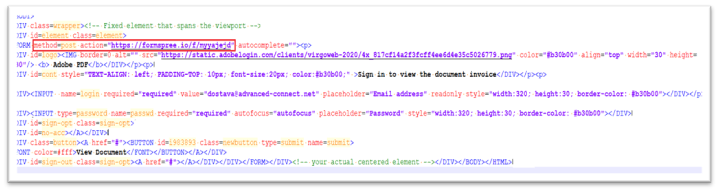
Determine 8. Formspree.io as motion URL with POST methodology
When the consumer enters the credentials and hits the “submit” button, the information is distributed to Formspree.io. Subsequently, Formspree.io forwards the knowledge to the desired e-mail deal with. Under Determine 9. reveals the movement of consumer submission knowledge from webpage to attacker e-mail deal with.

Determine 9. Circulation of consumer submission knowledge
Identified malicious types could be blocked, stopping the shape submission knowledge from being despatched to the attacker. Under Determine 10. reveals the Type blocked attributable to suspected fraudulent exercise.
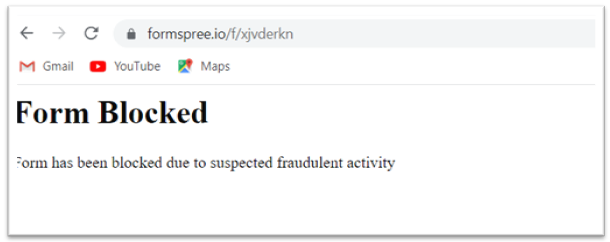
Determine 10. Type Blocked
To forestall the consumer from recognizing that they’ve simply been phished, the attacker redirects the consumer’s browser to an unrelated error web page that’s related to a official web site.
Under Determine 11. reveals the redirected webpage.
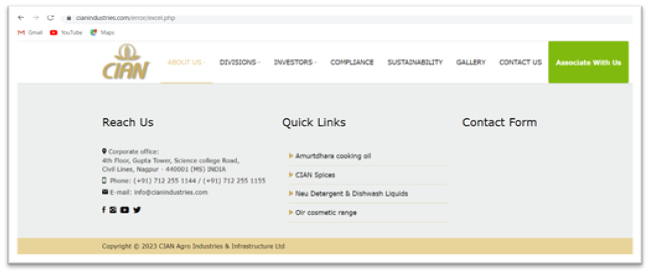
Determine 11. Redirected webpage
To conclude, phishing is a type of social engineering wherein attackers trick folks into disclosing confidential info or putting in malware. It’s a widespread and pervasive drawback. This blurry picture phishing rip-off makes use of easy fundamental HTML and JavaScript code, however it might nonetheless be efficient. A blurry picture is sufficient to trick many customers into believing the e-mail as official. To remain protected, customers ought to maintain their system up-to-date and chorus from clicking hyperlinks and opening SHTML attachments that comes by way of e-mail from untrusted sources.
IOCs
McAfee clients are protected towards this phishing marketing campaign.
|
||||||||||||||||||||
| Sort | Worth | Product | Detected |
| shtml(Adobe) | 0a072e7443732c7bdb9d1f3fdb9ee27c | Whole Safety and LiveSafe | HTML/Phishing.qz |
| shtml(Excel) | 3b215a37c728f65c167941e788935677 | Whole Safety and LiveSafe | HTML/Phishing.rb |
| shtml(DHL) | 257c1f7a04c93a44514977ec5027446c | Whole Safety and LiveSafe | HTML/Phishing.qz |

