In 2021, the unique Russian cybercrime discussion board Mazafaka was hacked. The leaked consumer database exhibits one of many discussion board’s founders was an lawyer who suggested Russia’s high hackers on the authorized dangers of their work, and what to do in the event that they received caught. A assessment of this consumer’s hacker identities exhibits that in his time on the boards he served as an officer within the particular forces of the GRU, the overseas army intelligence company of the Russian Federation.
Launched in 2001 beneath the tagline “Community terrorism,” Mazafaka would evolve into one of the guarded Russian-language cybercrime communities. The discussion board’s member roster features a Who’s Who of high Russian cybercriminals, and it featured sub-forums for a variety of cybercrime specialities, together with malware, spam, coding and identification theft.
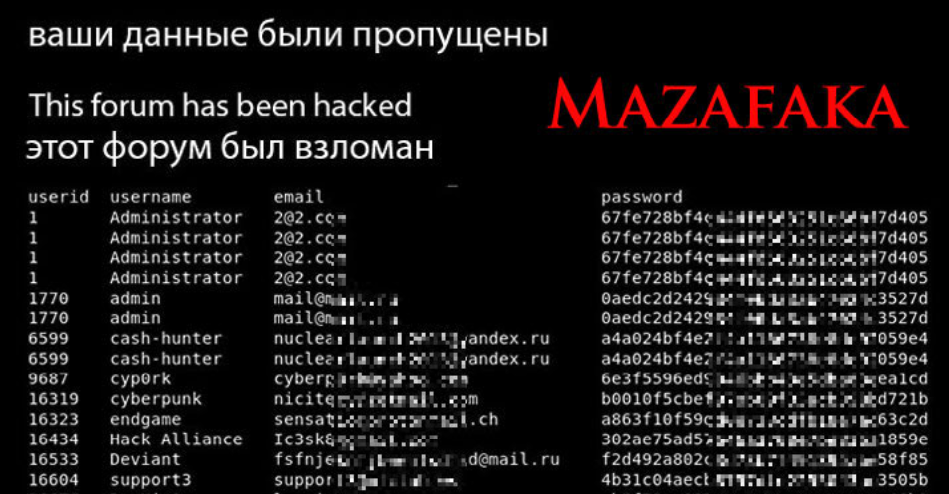
One illustration of the leaked Mazafaka database.
In nearly any database leak, the primary accounts listed are normally the directors and early core members. However the Mazafaka consumer data posted on-line was not a database file per se, and it was clearly edited, redacted and restructured by whoever launched it. Consequently, it may be troublesome to inform which members are the earliest customers.
The unique Mazafaka is thought to have been launched by a hacker utilizing the nickname “Stalker.” Nonetheless, the bottom numbered (non-admin) consumer ID within the Mazafaka database belongs to a different particular person who used the deal with “Djamix,” and the e-mail handle djamix@mazafaka[.]ru.
From the discussion board’s inception till round 2008, Djamix was certainly one of its most energetic and eloquent contributors. Djamix instructed discussion board members he was a lawyer, and practically all of his posts included authorized analyses of varied public instances involving hackers arrested and charged with cybercrimes in Russia and overseas.
“Hiding with purely technical parameters is not going to assist in a critical matter,” Djamix suggested Maza members in September 2007. “In an effort to ESCAPE the regulation, it is advisable to KNOW the regulation. That is crucial factor. Technical capabilities can’t overcome intelligence and crafty.”
Stalker himself credited Djamix with preserving Mazafaka on-line for therefore a few years. In a retrospective submit printed to Livejournal in 2014 titled, “Mazafaka, from conception to the current day,” Stalker stated Djamix had grow to be a core member of the neighborhood.
“This man is all over the place,” Stalker stated of Djamix. “There’s not a factor on [Mazafaka] that he doesn’t participate in. For me, he’s a stimulus-irritant and because of him, Maza remains to be alive. Our rallying drive!”
Djamix instructed different discussion board denizens he was a licensed lawyer who might be employed for distant or in-person consultations, and his posts on Mazafaka and different Russian boards present a number of hackers dealing with authorized jeopardy possible took him up on this provide.
“I’ve the suitable to characterize your pursuits in court docket,” Djamix stated on the Russian-language cybercrime discussion board Verified in Jan. 2011. “Remotely (within the type of fixed assist and consultations), or in individual – that is mentioned individually. In addition to the price of my companies.”
WHO IS DJAMIX?
A search on djamix@mazafaka[.]ru at DomainTools.com reveals this handle has been used to register at the very least 10 domains since 2008. These embody a number of web sites about life in and round Sochi, Russia, the positioning of the 2014 Winter Olympics, in addition to a close-by coastal city known as Adler. All of these websites say they had been registered to an Aleksei Safronov from Sochi who additionally lists Adler as a hometown.
The breach monitoring service Constella Intelligence finds that the cellphone quantity related to these domains — +7.9676442212 — is tied to a Fb account for an Aleksei Valerievich Safronov from Sochi. Mr. Safronov’s Fb profile, which was final up to date in October 2022, says his ICQ immediate messenger quantity is 53765. This is similar ICQ quantity assigned to Djamix within the Mazafaka consumer database.
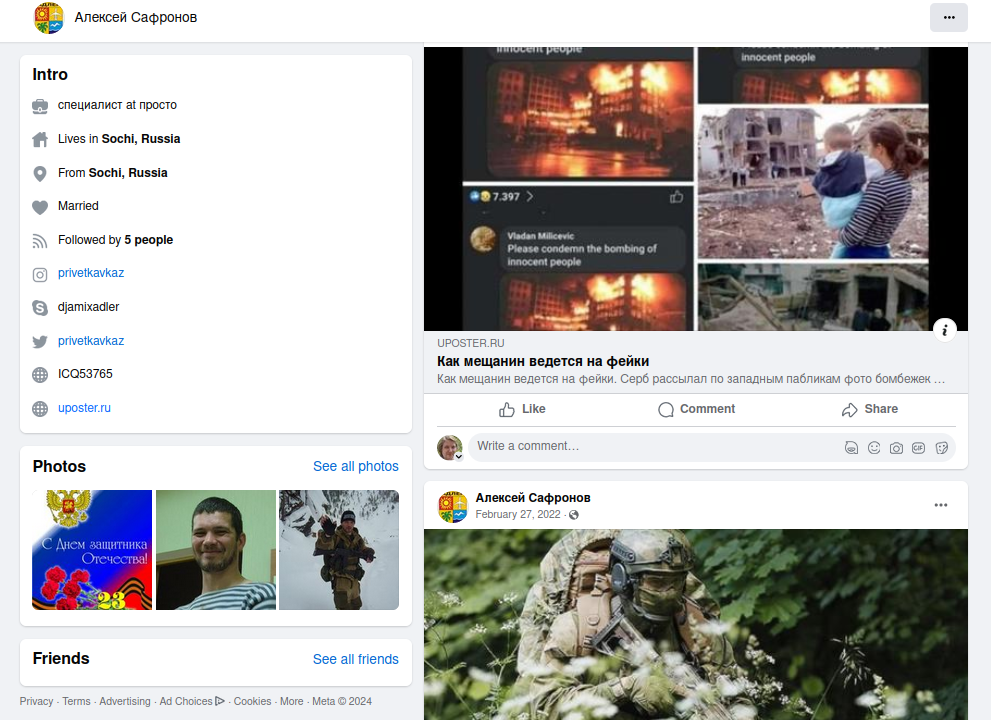
The Fb account for Aleksey Safronov.
A “Djamix” account on the discussion board privetsochi[.]ru (“Howdy Sochi”) says this consumer was born Oct. 2, 1970, and that his web site is uposter[.]ru. This Russian language information website’s tagline is, “We Create Communication,” and it focuses closely on information about Sochi, Adler, Russia and the battle in Ukraine, with a powerful pro-Kremlin bent.
Safronov’s Fb profile additionally provides his Skype username as “Djamixadler,” and it consists of dozens of photographs of him wearing army fatigues together with a regiment of troopers deploying in pretty distant areas of Russia. A few of these photographs date again to 2008.
In a number of of the pictures, we are able to see a patch on the arm of Safronov’s jacket that bears the brand of the Spetsnaz GRU, a particular forces unit of the Russian army. In keeping with a 2020 report from the Congressional Analysis Service, the GRU operates each as an intelligence company — gathering human, cyber, and alerts intelligence — and as a army group answerable for battlefield reconnaissance and the operation of Russia’s Spetsnaz army commando items.

Mr. Safronov posted this picture of himself on Fb in 2016. The insignia of the GRU might be seen on his sleeve.
“In recent times, stories have linked the GRU to a few of Russia’s most aggressive and public intelligence operations,” the CRS report explains. “Reportedly, the GRU performed a key function in Russia’s occupation of Ukraine’s Crimea area and invasion of jap Ukraine, the tried assassination of former Russian intelligence officer Sergei Skripal in the UK, interference within the 2016 U.S. presidential elections, disinformation and propaganda operations, and a number of the world’s most damaging cyberattacks.”
In keeping with the Russia-focused investigative information outlet Meduza, in 2014 the Russian Protection Ministry created its “information-operation troops” for motion in “cyber-confrontations with potential adversaries.”
“Later, sources within the Protection Ministry defined that these new troops had been meant to ‘disrupt the potential adversary’s data networks,’” Meduza reported in 2018. “Recruiters reportedly went in search of ‘hackers who’ve had issues with the regulation.’”
Mr. Safronov didn’t reply to a number of requests for remark. A 2018 treatise written by Aleksei Valerievich Safronov titled “One Hundred Years of GRU Navy Intelligence” explains the importance of the bat within the seal of the GRU.
“A method or one other, the bat is an emblem that unites all energetic and retired intelligence officers; it’s a image of unity and exclusivity,” Safronov wrote. “And, usually, it doesn’t matter who we’re speaking about – a secret GRU agent someplace within the military or a sniper in any of the particular forces brigades. All of them did and are doing one essential and accountable factor.”
It’s unclear what function Mr. Safronov performs or performed within the GRU, however it appears possible the army intelligence company would have exploited his appreciable technical expertise, information and connections on the Russian cybercrime boards.
Looking out on Safronov’s area uposter[.]ru in Constella Intelligence reveals that this area was utilized in 2022 to register an account at a well-liked Spanish-language dialogue discussion board devoted to serving to candidates put together for a profession within the Guardia Civil, certainly one of Spain’s two nationwide police forces. Pivoting on that Russian IP in Constella exhibits three different accounts had been created on the identical Spanish consumer discussion board across the identical date.
Mark Rasch, a former cybercrime prosecutor for the U.S. Division of Justice, stated there has at all times been an in depth relationship between the GRU and the Russian hacker neighborhood. Rasch famous that within the early 2000s, the GRU was soliciting hackers with the talents essential to hack US banks so as to procure funds to assist finance Russia’s battle in Chechnya.
“The man is closely hooked into the Russian cyber neighborhood, and that’s helpful for intelligence companies,” Rasch stated. “He might have been infiltrating the neighborhood to watch it for the GRU. Or he might simply be a man sporting a army uniform.”
