Menace hunters have recognized a brand new variant of Android malware referred to as MoqHao that robotically executes on contaminated units with out requiring any person interplay.
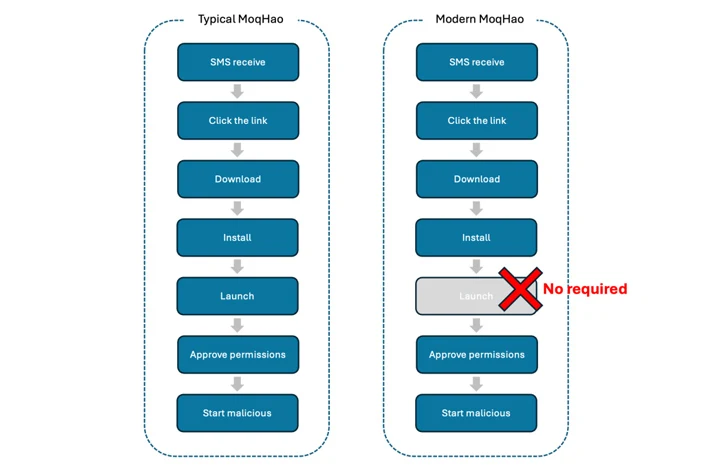
“Typical MoqHao requires customers to put in and launch the app to get their desired goal, however this new variant requires no execution,” McAfee Labs stated in a report printed this week. “Whereas the app is put in, their malicious exercise begins robotically.”
The marketing campaign’s targets embrace Android customers positioned in France, Germany, India, Japan, and South Korea.
MoqHao, additionally referred to as Wroba and XLoader (to not be confused with the Home windows and macOS malware of the identical identify), is an Android-based cellular risk that is related to a Chinese language financially motivated cluster dubbed Roaming Mantis (aka Shaoye).
Typical assault chains begin with bundle delivery-themed SMS messages bearing fraudulent hyperlinks that, when clicked from Android units, result in the deployment of the malware however redirect victims to credential harvesting pages impersonating Apple’s iCloud login web page when visited from an iPhone.
In July 2022, Sekoia detailed a marketing campaign that compromised not less than 70,000 Android units in France. As of early final yr, up to date variations of MoqHao have been discovered to infiltrate Wi-Fi routers and undertake Area Title System (DNS) hijacking, revealing the adversary’s dedication to innovating its arsenal.
The newest iteration of MoqHao continues to be distributed through smishing strategies, however what has modified is that the malicious payload is run robotically upon set up and prompts the sufferer to grant it dangerous permissions with out launching the app, a habits beforehand noticed with bogus apps containing the HiddenAds malware.
What’s additionally obtained a facelift is that the hyperlinks shared within the SMS messages themselves are hidden utilizing URL shorteners to extend the chance of the assault’s success. The content material for these messages is extracted from the bio (or description) area from fraudulent Pinterest profiles arrange for this goal.
MoqHao is supplied with a number of options that enable it to stealthily harvest delicate data like machine metadata, contacts, SMS messages, and images, name particular numbers with silent mode, and allow/disable Wi-Fi, amongst others.
McAfee stated it has reported the findings to Google, which is claimed to be “already engaged on the implementation of mitigations to forestall this kind of auto-execution in a future Android model.”
The event comes as Chinese language cybersecurity agency QiAnXin revealed {that a} beforehand unknown cybercrime syndicate named Bigpanzi has been linked to the compromise of Android-based good TVs and set-top packing containers (STBs) with a view to corral them right into a botnet for conducting distributed denial-of-service (DDoS) assaults.
The operation, lively since not less than 2015, is estimated to manage a botnet comprising 170,000 every day lively bots, most of that are positioned in Brazil. Nonetheless, 1.3 million distinct Brazilian IP addresses have been related to Bigpanzi since August 2023.
The infections are made attainable by tricking customers into putting in booby-trapped apps for streaming pirated films and TV exhibits by way of sketchy web sites. The marketing campaign was first disclosed by Russian antivirus vendor Physician Internet in September 2023.
“As soon as put in, these units rework into operational nodes inside their illicit streaming media platform, catering to providers like site visitors proxying, DDoS assaults, OTT content material provision, and pirate site visitors,” QiAnXin researchers stated.
“The potential for Bigpanzi-controlled TVs and STBs to broadcast violent, terroristic, or pornographic content material, or to make use of more and more convincing AI-generated movies for political propaganda, poses a big risk to social order and stability.”