The North Korea-linked nation-state actor generally known as Kimsuky is suspected of utilizing a beforehand undocumented Golang-based info stealer referred to as Troll Stealer.
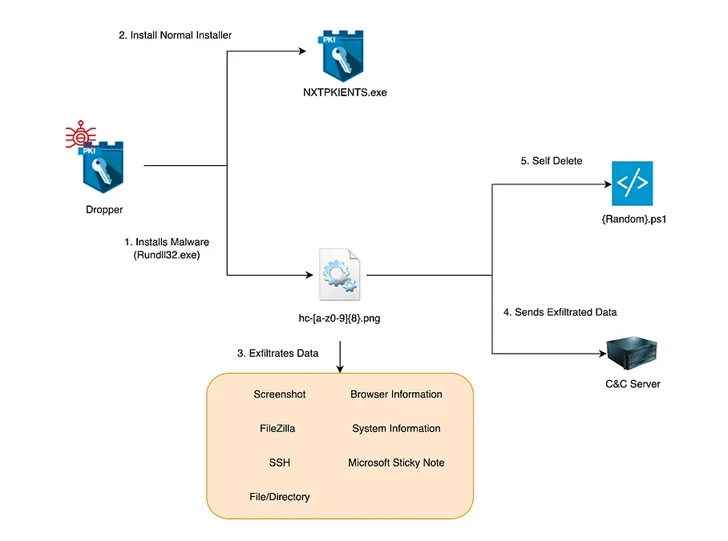
The malware steals “SSH, FileZilla, C drive information/directories, browsers, system info, [and] display captures” from contaminated techniques, South Korean cybersecurity firm S2W mentioned in a brand new technical report.
Troll Stealer’s hyperlinks to Kimsuky stem from its similarities to identified malware households, reminiscent of AppleSeed and AlphaSeed malware which were attributed to the group.
Kimsuky, additionally tracked below the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (beforehand Thallium), Nickel Kimball, and Velvet Chollima, is well-known for its propensity to steal delicate, confidential info in offensive cyber operations.
In late November 2023, the menace actors had been sanctioned by the U.S. Treasury Division’s Workplace of International Belongings Management (OFAC) for gathering intelligence to additional North Korea’s strategic goals.
The adversarial collective, in latest months, has been attributed to spear-phishing assaults focusing on South Korean entities to ship a wide range of backdoors, together with AppleSeed and AlphaSeed.
S2W’s newest evaluation reveals the usage of a dropper that masquerades as a safety program set up file from a South Korean firm named SGA Options to launch the stealer, which will get its identify from the trail “D:/~/repo/golang/src/root.go/s/troll/agent” that is embedded in it.
“The dropper runs as a reliable installer alongside the malware, and each the dropper and malware are signed with a legitimate, reliable D2Innovation Co.,LTD’ certificates, suggesting that the corporate’s certificates was truly stolen,” the corporate mentioned.
A stand-out characteristic of Troll Stealer is its skill to pilfer the GPKI certificates issued by the South Korean authorities from contaminated techniques, indicating that the malware could been put to make use of in assaults focusing on administrative and public organizations within the nation.
Given the absence of Kimsuky campaigns documenting the theft of GPKI folders, it has raised the likelihood that the brand new habits is both a shift in techniques or the work of one other menace actor intently related to the group that additionally has entry to the supply code of AppleSeed and AlphaSeed.
There are additionally indicators that the menace actor could also be concerned with a Go-based backdoor codenamed GoBear that is additionally signed with a reliable certificates related to D2Innovation Co., LTD and executes directions acquired from a command-and-control (C2) server.
“The strings contained within the names of the capabilities it calls have been discovered to overlap with the instructions utilized by BetaSeed, a C++-based backdoor malware utilized by the Kimsuky group,” S2W mentioned. “It’s noteworthy that GoBear provides SOCKS5 proxy performance, which was not beforehand supported by the Kimsuky group’s backdoor malware.”