After a lightweight begin to the 12 months, February delivered 72 patches and 21 advisories to Microsoft prospects. The CVEs addressed on this month’s Patch Tuesday launch included 43 for Home windows. Twelve different product teams or instruments are additionally affected. Of the CVEs addressed, 5 are thought of Crucial in severity by Microsoft; these have an effect on Home windows, Workplace, Trade, and Dynamics 365.
At patch time, two of the problems are recognized to be beneath exploit within the wild, and none has been publicly disclosed. (Nevertheless, one of many advisory objects most actually has; extra on that in a minute.) Eight of the addressed vulnerabilities in Home windows, Workplace, and Trade (together with a Crucial-severity elevation-of-privilege subject with an attention-getting 9.8 CVSS base rating) are by the corporate’s estimation extra prone to be exploited within the subsequent 30 days. Six of the problems addressed are coated by Sophos protections, and we embrace info on these in a desk under.
Along with these patches the discharge included info on six Chromium/Edge-related CVEs, together with an RCE that would result in sandbox escapes; one MITRE-issued CVE regarding a DNS subject that would result in denial of service; one Github-issued CVE addressing the current CVE-2024-21626 “Leaky Vessel” subject affecting Mariner, disclosed in a prolonged public publish by Snyk two weeks in the past and patched by varied different affected corporations since then; and 13 Adobe advisories, all associated to Acrobat Reader.
We don’t embrace advisories within the CVE counts and graphics under, however we offer info on all the things in an appendix on the finish of the article. We’re as common together with on the finish of this publish three different appendices itemizing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product household.
- Whole Microsoft CVEs: 72
- Whole Adobe advisories coated in replace: 13
- Whole Edge / Chromium points coated in replace: 6
- Whole Mariner advisories coated in replace: 1
- Whole MITRE advisories coated in replace: 1
- Publicly disclosed: 0
- Exploited: 2
- Severity
- Crucial: 5
- Necessary: 65
- Average: 2
- Impression
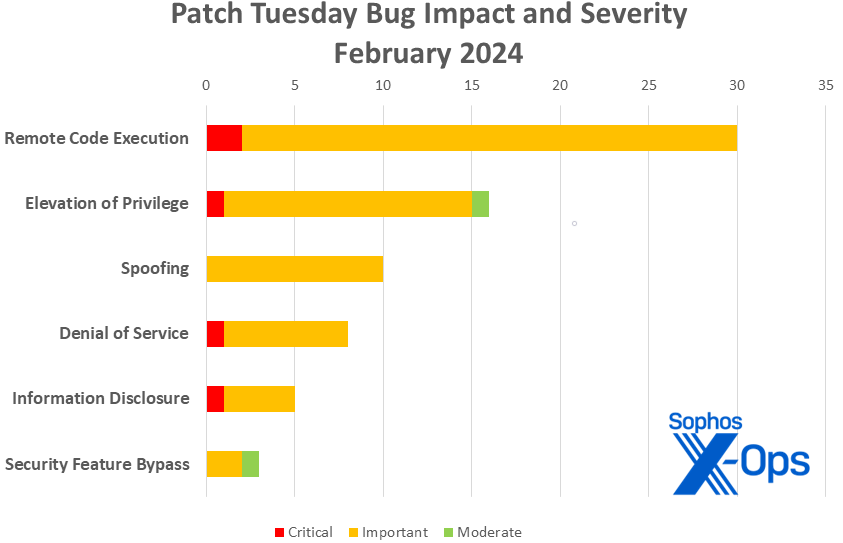
- Distant Code Execution: 30
- Elevation of Privilege: 16
- Spoofing: 10
- Denial of Service: 8
- Info Disclosure: 5
- Safety Characteristic Bypass: 3
Determine 1: After January’s massive month for info disclosure bugs, a wealth of OLE-related fixes put distant code execution again on prime for February
Merchandise
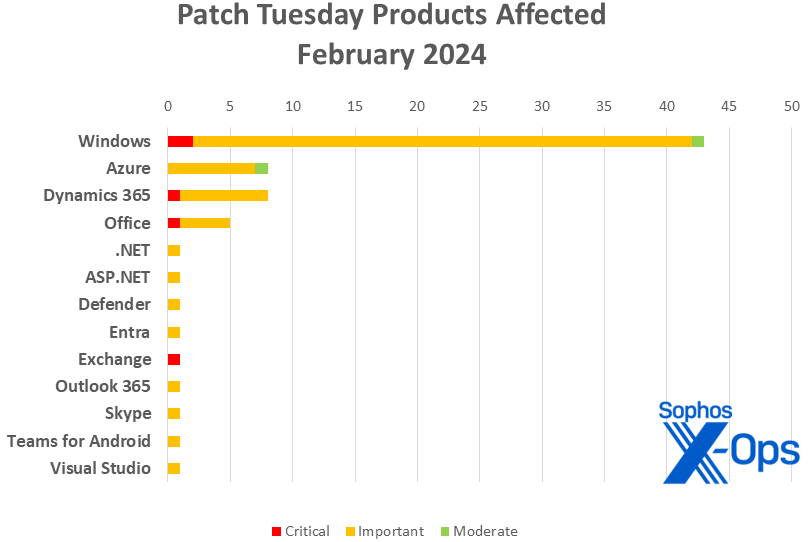
- Home windows: 43
- Azure: 8
- Dynamics 365: 8
- Workplace: 5
- .NET: 1
- ASP.NET: 1 (shared with Visible Studio)
- Defender: 1
- Entra [Azure AD]: 1
- Trade: 1
- Outlook 365: 1
- Skype: 1
- Groups for Android: 1
- Visible Studio: 1 (shared with ASP.NET)
Determine 2: It’s a Home windows-heavy month, thanks partly to a lot of fixes for Home windows Defender Software Management (WDAC)
Notable February updates
Along with the problems mentioned above, just a few particular objects are price noting.
CVE-2024-21350, CVE-2024-21352, CVE-2024-21358, CVE-2024-21359, CVE-2024-21360, CVE-2024-21361, CVE-2024-21365, CVE-2024-21366, CVE-2024-21367, CVE-2024-21368, CVE-2024-21369, CVE-2024-21370, CVE-2024-21375, CVE-2024-21391 (15 CVEs)
Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability
Fifteen CVEs that share not solely a reputation however a severity (Necessary), an affect (RCE), a lofty CVSS base rating (8.8), and a finder non-identification (Microsoft credit all 15 to “Nameless”). They’re accompanied by one further (however associated?) patch that shares all the things however the quantity and identify – CVE-2024-21353, Microsoft WDAC ODBC Driver Distant Code Execution Vulnerability.
CVE-2024-21404
Microsoft Entra Jira Single-Signal-On Plugin Elevation of Privilege Vulnerability
This extra-spicy EoP – Microsoft assigns it solely an Necessary severity ranking, however its base CVSS is a critical-level 9.8 – targets the Azure AD Jira SSO plugin. Considerably, it doesn’t even require the attacker to authenticate to trigger hassle; all it takes is a script to entry a focused Jira server, and the attacker will be capable to replace Entra ID SAML metadata and data for the plugin – permitting them to vary the authentication of the applying as they want. The repair is an replace to model 1.1.2; it’s obtainable from both the Microsoft Obtain Middle or from the Atlassian Market.
CVE-2024-21410
Microsoft Trade Server Elevation of Privilege Vulnerability
The opposite CVE with a 9.8 CVSS this month is a NTLM relay (pass-the-hash) vulnerability. It may permit the attacker to relay a consumer’s leaked Internet-NTLMv2 hash towards a weak Trade Server and authenticate because the consumer. It impacts a hodge-podge of variations: Trade Server 2016, cumulative replace 23; Trade Server 2019, cumulative replace 13; and Trade Server 2019, cumulative replace 14. Extra info is accessible on Microsoft’s Trade Group Weblog, however know that the corporate believes this one is extra prone to be exploited inside the subsequent 30 days.
CVE-2024-21378
Microsoft Outlook Distant Code Execution Vulnerability
Preview Pane is an assault vector for this important-severity, CVSS 8.0 RCE, and Microsoft believes that exploitation is extra doubtless within the subsequent 30 days. The race is on. (This implies two Outlook-related, Preview Pane-triggered vulns for February; the opposite, CVE-2024-21413, is nevertheless presently marked as Exploitation Unlikely by Microsoft.)
CVE-2024-21374
Microsoft Groups for Android Info Disclosure
The patch for this important-severity info disclosure subject is accessible through Google Play.
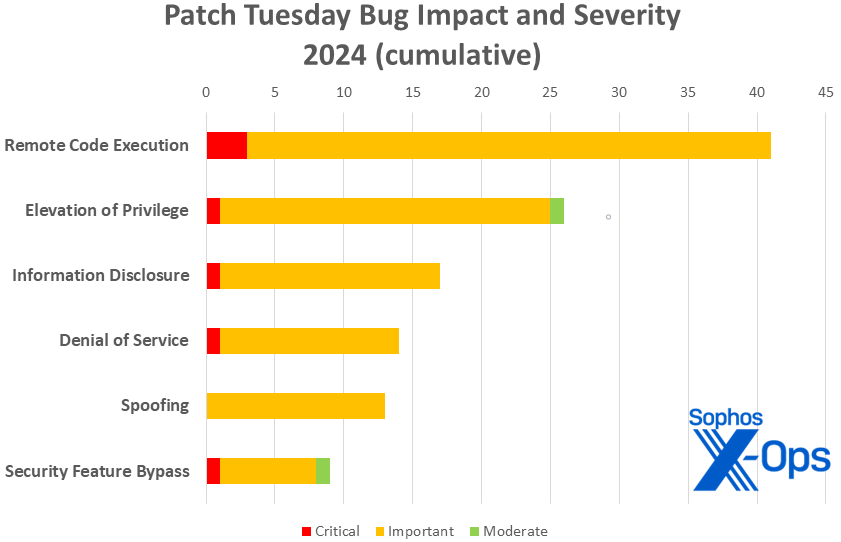
Determine 3: 2024’s off and trotting – although, with simply 120 patches thus far, totals are operating considerably behind different years. (The primary two months of 2023 introduced 173 patches; 2022, 154; 2021, 139; and 2020, 150.)
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-21338 | Exp/2421338-A | Exp/2421338-A |
| CVE-2024-21345 | Exp/2421345-A | Exp/2421345-A |
| CVE-2024-21346 | Exp/2421346-A | Exp/2421346-A |
| CVE-2024-21357 | Exp/2421357-A | Exp/2421357-A |
| CVE-2024-21371 | Exp/2421371-A | Exp/2421371-A |
| CVE-2024-21379 | N/A | sid:2309292 |
As you’ll be able to each month, when you don’t wish to wait on your system to tug down Microsoft’s updates itself, you’ll be able to obtain them manually from the Home windows Replace Catalog web site. Run the winver.exe software to find out which construct of Home windows 10 or 11 you’re operating, then obtain the Cumulative Replace package deal on your particular system’s structure and construct quantity.
Appendix A: Vulnerability Impression and Severity
This can be a listing of February patches sorted by affect, then sub-sorted by severity. Every listing is additional organized by CVE.
Distant Code Execution (30 CVEs)
| Crucial severity | |
| CVE-2024-21357 | Home windows Pragmatic Basic Multicast (PGM) Distant Code Execution Vulnerability |
| CVE-2024-21413 | Microsoft Workplace Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2024-20667 | Azure DevOps Server Distant Code Execution Vulnerability |
| CVE-2024-20673 | Microsoft Workplace Distant Code Execution Vulnerability |
| CVE-2024-21339 | Home windows USB Generic Mother or father Driver Distant Code Execution Vulnerability |
| CVE-2024-21341 | Home windows Kernel Distant Code Execution Vulnerability |
| CVE-2024-21347 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-21349 | Microsoft ActiveX Knowledge Objects Distant Code Execution Vulnerability |
| CVE-2024-21350 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21352 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21353 | Microsoft WDAC ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-21358 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21359 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21360 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21361 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21363 | Microsoft Message Queuing (MSMQ) Distant Code Execution Vulnerability |
| CVE-2024-21365 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21366 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21367 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21368 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21369 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21370 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21372 | Home windows OLE Distant Code Execution Vulnerability |
| CVE-2024-21375 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21376 | Microsoft Azure Kubernetes Service Confidential Container Distant Code Execution Vulnerability |
| CVE-2024-21378 | Microsoft Outlook Distant Code Execution Vulnerability |
| CVE-2024-21379 | Microsoft Phrase Distant Code Execution Vulnerability |
| CVE-2024-21384 | Microsoft Workplace OneNote Distant Code Execution Vulnerability |
| CVE-2024-21391 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21420 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
Elevation of Privilege (16 CVEs)
| Crucial severity | |
| CVE-2024-21410 | Microsoft Trade Server Elevation of Privilege Vulnerability |
| Necessary severity | |
| CVE-2024-21304 | Trusted Compute Base Elevation of Privilege Vulnerability |
| CVE-2024-21315 | Microsoft Defender for Endpoint Safety Elevation of Privilege Vulnerability |
| CVE-2024-21329 | Azure Related Machine Agent Elevation of Privilege Vulnerability |
| CVE-2024-21338 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21345 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21346 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-21354 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability |
| CVE-2024-21355 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability |
| CVE-2024-21371 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21397 | Microsoft Azure File Sync Elevation of Privilege Vulnerability |
| CVE-2024-21401 | Microsoft Entra Jira Single-Signal-On Plugin Elevation of Privilege Vulnerability |
| CVE-2024-21402 | Microsoft Outlook Elevation of Privilege Vulnerability |
| CVE-2024-21403 | Microsoft Azure Kubernetes Companies Confidential Container Elevation of Privilege Vulnerability |
| CVE-2024-21405 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability |
| Average severity | |
| CVE-2024-21364 | Microsoft Azure Website Restoration Elevation of Privilege Vulnerability |
Spoofing (10 CVEs)
| Necessary severity | |
| CVE-2024-20679 | Azure Stack Hub Spoofing Vulnerability |
| CVE-2024-21327 | Microsoft Dynamics 365 Buyer Engagement Cross-Website Scripting Vulnerability |
| CVE-2024-21328 | Dynamics 365 Gross sales Spoofing Vulnerability |
| CVE-2024-21381 | Microsoft Azure Energetic Listing B2C Spoofing Vulnerability |
| CVE-2024-21389 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2024-21393 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2024-21394 | Dynamics 365 Area Service Spoofing Vulnerability |
| CVE-2024-21395 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2024-21396 | Dynamics 365 Gross sales Spoofing Vulnerability |
| CVE-2024-21406 | Home windows Print Spooler Spoofing Vulnerability |
Denial of Service (8 CVEs)
| Crucial severity | |
| CVE-2024-20684 | Home windows Hyper-V Denial of Service Vulnerability |
| Necessary severity | |
| CVE-2024-21342 | Home windows DNS Consumer Denial of Service Vulnerability |
| CVE-2024-21343 | Home windows Community Deal with Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-21344 | Home windows Community Deal with Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-21348 | Web Connection Sharing (ICS) Denial of Service Vulnerability |
| CVE-2024-21356 | Home windows Light-weight Listing Entry Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-21386 | .NET Denial of Service Vulnerability |
| CVE-2024-21404 | .NET Denial of Service Vulnerability |
Info Disclosure (5 CVEs)
| Crucial severity | |
| CVE-2024-21380 | Microsoft Dynamics Enterprise Central/NAV Info Disclosure Vulnerability |
| Necessary severity | |
| CVE-2024-20695 | Skype for Enterprise Info Disclosure Vulnerability |
| CVE-2024-21340 | Home windows Kernel Info Disclosure Vulnerability |
| CVE-2024-21374 | Microsoft Groups for Android Info Disclosure Vulnerability |
| CVE-2024-21377 | Home windows DNS Info Disclosure Vulnerability |
Safety Characteristic Bypass (3 CVEs)
| Necessary severity | |
| CVE-2024-21362 | Home windows Kernel Safety Characteristic Bypass Vulnerability |
| CVE-2024-21412 | Web Shortcut Information Safety Characteristic Bypass Vulnerability |
| Average Severity | |
| CVE-2024-21351 | Home windows SmartScreen Safety Characteristic Bypass Vulnerability |
Appendix B: Exploitability
This can be a listing of the February CVEs judged by Microsoft to be both already beneath lively exploit within the wild or extra prone to be exploited within the wild inside the first 30 days post-release. Every listing is additional organized by CVE.
| Exploitation detected | |
| CVE-2024-21351 | Home windows SmartScreen Safety Characteristic Bypass Vulnerability |
| CVE-2024-21412 | Web Shortcut Information Safety Characteristic Bypass Vulnerability |
| Exploitation extra doubtless inside the subsequent 30 days | |
| CVE-2024-21338 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21345 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21346 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-21357 | Home windows Pragmatic Basic Multicast (PGM) Distant Code Execution Vulnerability |
| CVE-2024-21371 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21378 | Microsoft Outlook Distant Code Execution Vulnerability |
| CVE-2024-21379 | Microsoft Phrase Distant Code Execution Vulnerability |
| CVE-2024-21410 | Microsoft Trade Server Elevation of Privilege Vulnerability |
Appendix C: Merchandise Affected
This can be a listing of February’s patches sorted by product household, then sub-sorted by severity. Every listing is additional organized by CVE. Patches which are shared amongst a number of product households are listed a number of occasions, as soon as for every product household.
Home windows (43 CVEs)
| Crucial severity | |
| CVE-2024-20684 | Home windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-21357 | Home windows Pragmatic Basic Multicast (PGM) Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2024-21304 | Trusted Compute Base Elevation of Privilege Vulnerability |
| CVE-2024-21338 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21339 | Home windows USB Generic Mother or father Driver Distant Code Execution Vulnerability |
| CVE-2024-21340 | Home windows Kernel Info Disclosure Vulnerability |
| CVE-2024-21341 | Home windows Kernel Distant Code Execution Vulnerability |
| CVE-2024-21342 | Home windows DNS Consumer Denial of Service Vulnerability |
| CVE-2024-21343 | Home windows Community Deal with Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-21344 | Home windows Community Deal with Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-21345 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21346 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-21347 | Microsoft ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-21348 | Web Connection Sharing (ICS) Denial of Service Vulnerability |
| CVE-2024-21349 | Microsoft ActiveX Knowledge Objects Distant Code Execution Vulnerability |
| CVE-2024-21350 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21352 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21353 | Microsoft WDAC ODBC Driver Distant Code Execution Vulnerability |
| CVE-2024-21354 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability |
| CVE-2024-21355 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability |
| CVE-2024-21356 | Home windows Light-weight Listing Entry Protocol (LDAP) Denial of Service Vulnerability |
| CVE-2024-21358 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21359 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21360 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21361 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21362 | Home windows Kernel Safety Characteristic Bypass Vulnerability |
| CVE-2024-21363 | Microsoft Message Queuing (MSMQ) Distant Code Execution Vulnerability |
| CVE-2024-21365 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21366 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21367 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21368 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21369 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21370 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21371 | Home windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-21372 | Home windows OLE Distant Code Execution Vulnerability |
| CVE-2024-21375 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21377 | Home windows DNS Info Disclosure Vulnerability |
| CVE-2024-21391 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21405 | Microsoft Message Queuing (MSMQ) Elevation of Privilege Vulnerability |
| CVE-2024-21406 | Home windows Print Spooler Spoofing Vulnerability |
| CVE-2024-21412 | Web Shortcut Information Safety Characteristic Bypass Vulnerability |
| CVE-2024-21420 | Microsoft WDAC OLE DB supplier for SQL Server Distant Code Execution Vulnerability |
| CVE-2024-21351 | Home windows SmartScreen Safety Characteristic Bypass Vulnerability |
Azure (8 CVEs)
| Necessary severity | |
| CVE-2024-20667 | Azure DevOps Server Distant Code Execution Vulnerability |
| CVE-2024-20679 | Azure Stack Hub Spoofing Vulnerability |
| CVE-2024-21329 | Azure Related Machine Agent Elevation of Privilege Vulnerability |
| CVE-2024-21376 | Microsoft Azure Kubernetes Service Confidential Container Distant Code Execution Vulnerability |
| CVE-2024-21381 | Microsoft Azure Energetic Listing B2C Spoofing Vulnerability |
| CVE-2024-21397 | Microsoft Azure File Sync Elevation of Privilege Vulnerability |
| CVE-2024-21403 | Microsoft Azure Kubernetes Companies Confidential Container Elevation of Privilege Vulnerability |
| Average severity | |
| CVE-2024-21364 | Microsoft Azure Website Restoration Elevation of Privilege Vulnerability |
Dynamics 365 (8 CVEs)
| Crucial severity | |
| CVE-2024-21380 | Microsoft Dynamics Enterprise Central/NAV Info Disclosure Vulnerability |
| Necessary severity | |
| CVE-2024-21327 | Microsoft Dynamics 365 Buyer Engagement Cross-Website Scripting Vulnerability |
| CVE-2024-21328 | Dynamics 365 Gross sales Spoofing Vulnerability |
| CVE-2024-21389 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2024-21393 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2024-21394 | Dynamics 365 Area Service Spoofing Vulnerability |
| CVE-2024-21395 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2024-21396 | Dynamics 365 Gross sales Spoofing Vulnerability |
Workplace (5 CVEs)
| Crucial severity | |
| CVE-2024-21413 | Microsoft Workplace Distant Code Execution Vulnerability |
| Necessary severity | |
| CVE-2024-20673 | Microsoft Workplace Distant Code Execution Vulnerability |
| CVE-2024-21378 | Microsoft Outlook Distant Code Execution Vulnerability |
| CVE-2024-21379 | Microsoft Phrase Distant Code Execution Vulnerability |
| CVE-2024-21384 | Microsoft Workplace OneNote Distant Code Execution Vulnerability |
.NET (1 CVE, shared with Visible Studio)
| Necessary severity | |
| CVE-2024-21404 | .NET Denial of Service Vulnerability |
ASP.NET (1 CVE)
| Necessary severity | |
| CVE-2024-21386 | .NET Denial of Service Vulnerability |
Defender (1 CVE)
| Necessary severity | |
| CVE-2024-21315
|
Microsoft Defender for Endpoint Safety Elevation of Privilege Vulnerability |
Entra (1 CVE)
| Necessary severity | |
| CVE-2024-21401 | Microsoft Entra Jira Single-Signal-On Plugin Elevation of Privilege Vulnerability |
Trade (1 CVE)
| Crucial severity | |
| CVE-2024-21410 | Microsoft Trade Server Elevation of Privilege Vulnerability |
Outlook 365 (1 CVE)
| Necessary severity | |
| CVE-2024-21402 | Microsoft Outlook Elevation of Privilege Vulnerability |
Skype (1 CVE)
| Necessary severity | |
| CVE-2024-20695 | Skype for Enterprise Info Disclosure Vulnerability |
Groups for Android (1 CVE)
| Necessary severity | |
| CVE-2024-21374 | Microsoft Groups for Android Info Disclosure Vulnerability |
Visible Studio (1 CVE, shared with ASP.NET)
| Necessary severity | |
| CVE-2024-21386 | .NET Denial of Service Vulnerability |
Appendix D: Advisories and Different Merchandise
This can be a listing of advisories and data on different related CVEs within the February Microsoft launch, sorted by product.
Related to Edge / Chromium (6 CVEs)
| CVE-2024-1059 | Chromium: CVE-2024-1059 Use after free in WebRTC |
| CVE-2024-1060 | Chromium: CVE-2024-1060 Use after free in Canvas |
| CVE-2024-1077 | Chromium: CVE-2024-1077 Use after free in Community |
| CVE-2024-1283 | Chromium: CVE-2024-1283 Heap buffer overflow in Skia |
| CVE-2024-1284 | Chromium: CVE-2024-1284 Use after free in Mojo |
| CVE-2024-21399 | Microsoft Edge (Chromium-based) Distant Code Execution Vulnerability |
Related to Home windows (non-Microsoft launch) (one CVE)
| CVE-2023-50387 | MITRE: CVE-2023-50387 DNS RRSIGs and DNSKEYs validation will be abused to remotely devour DNS server sources |
Related to Adobe (13 CVEs)
| CVE-2024-20726 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20727 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20728 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20729 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20730 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20731 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20733 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20734 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20735 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20736 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20747 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20748 | Safety updates obtainable for Acrobat Reader |
| CVE-2024-20749 | Safety updates obtainable for Acrobat Reader |