With breaches making the headlines on an virtually weekly foundation, the cybersecurity challenges we face have gotten seen not solely to massive enterprises, who’ve constructed safety capabilities through the years, but additionally to small to medium companies and the broader public. Whereas that is creating larger consciousness amongst smaller companies of the necessity to enhance their safety posture, SMBs are sometimes left dealing with a spot available in the market, unable to search out safety tooling that’s each simple for them to make use of and which they will afford.
Once we contemplate the wants of SMBs, we have to focus each on the event of menace intelligence, which is critical to know and establish the threats being confronted, as properly because the instruments used to offer safety. NTTSH has constructed a pedigree of over 20 years’ expertise within the analysis and curation of menace intelligence in addition to the event of capabilities and merchandise which leverage its menace intelligence to guard clients. After a few years of deal with bigger enterprises, NTTSH is shifting to democratize cybersecurity and supply smaller companies with the safety they require.
World Menace Intelligence Heart
All of NTTSH’s efforts are underpinned by the capabilities of its World Menace Intelligence Heart (GTIC). The efforts of the GTIC transcend these of a pure analysis group by taking menace analysis and mixing it with NTTSH proprietary detective expertise to supply utilized menace intelligence.
The GTIC’s mission is to guard purchasers by offering superior menace analysis and safety intelligence, enabling NTTSH to stop, detect, and reply to cyber threats. To supply a very distinctive vantage level inside NTTSH’s services, GTIC leverages proprietary intelligence capabilities and NTT’s place because the operator of one of many world’s prime 5 tier 1 Web backbones, offering unequaled visibility of Web telemetry to achieve an understanding of and perception into the assorted menace actors, exploit instruments and malware – and the ways, methods, and procedures utilized by attackers. Along with curating its personal menace intelligence analysis, GTIC additionally maintains relationships with different key gamers on this house, together with the Cyber Menace Alliance, Microsoft, CISA, and the Nationwide Cyber Forensics and Coaching Alliance (NCFTA).
NTTSH’s annual World Menace Intelligence Report (GTIR) gives a window into the work carried out by GTIC, offering a synopsis of the important thing challenges within the safety panorama dealing with organizations of all sizes, along with actionable insights to assist organizations higher adapt to the evolving menace panorama. Within the Q3 replace of the 2023 GTIR, a particular focus was positioned on key business verticals, offering insights into the threats they face.
Menace focus by sector
The healthcare sector faces a singular set of challenges, not solely as a result of excessive worth of the data owned by healthcare suppliers but additionally because of steep progress within the adoption of expertise in healthcare in a context the place many suppliers, particularly smaller ones, lack consciousness of cybersecurity and in addition do not have the sources to deploy and preserve the sorts of controls loved by massive enterprises. Ransomware remains to be proving notably problematic. Healthcare ransomware breaches are proving to be notably concentrated throughout a number of geographies, with the USA, Australia, and the UK accounting for near 80% of those breaches.
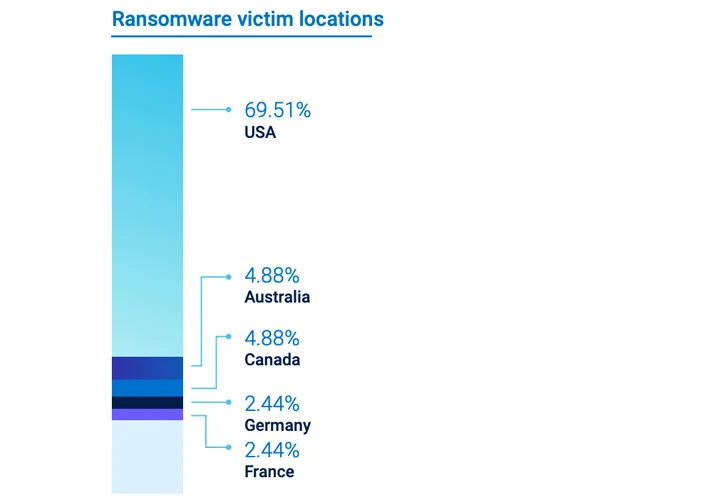 |
| Determine 1: Ransomware sufferer areas within the Healthcare sector. |
The same geographic pattern is seen within the telecommunications sector, the place the USA, UK, and Australia account for roughly 52% of ransomware assaults, whereas in schooling, the USA, UK, and Canada account for about 83%.
Throughout the entire focus sectors, Lockbit 3.0 stays probably the most prolific ransomware menace actor. Some ransomware actors are, nevertheless, specializing in particular sectors, such because the Bl00dy ransomware gang, which particularly targets schooling.
 |
| Determine 2: Prime ransomware actors within the telecommunications sector |
Safety Challenges of SaaS
A current space of focus for GTIC has been the best way during which the quickly accelerating adoption of SaaS is presenting its personal set of challenges. SaaS is quickly turning into an integral a part of the day-to-day operations of each small and huge companies, with annual progress anticipated to proceed at a charge of shut to twenty% by means of 2027. On this context, it is very important be aware that 99% of cloud safety breaches are anticipated to be the client’s fault, based on Gartner.
The shared accountability mannequin for cloud companies has been one thing that bigger enterprises have been conversant in for a while already. Smaller organizations are, nevertheless, nonetheless coming to grips with this mannequin. In respect of SaaS, because of this whereas the cloud supplier is accountable for the appliance, SMBs are nonetheless adapting to the truth that they keep accountability for his or her information and, crucially, handle their accounts and identities. Menace actors are, because of this, specializing in methods to compromise identities, particularly utilizing methods equivalent to credential stuffing and phishing.
Going through as much as the Challenges of Hybrid IT
Whereas SMBs have been beforehand in a position to depend on antivirus software program and firewalls to guard the expertise property on their premises, most have now moved into the world of hybrid IT as they more and more depend on cloud-delivered companies. Whereas the safety controls supplied by most cloud companies are good, SMBs face a wide range of challenges in utilizing the safety performance that’s out there to them.
Because the assault floor of even smaller firms expands, the variety of sources of safety alerting grows. That’s not the one problem: menace actors will typically not confine their actions to at least one a part of your expertise property. They could begin in a single space, for example, by compromising a number of endpoints (equivalent to laptops) after which use the data they collect (equivalent to credentials) to maneuver laterally, for example, to compromise a SaaS software. Whereas massive enterprises have spent the final 10 years or extra constructing devoted SecOps groups and complicated safety toolchains, SMBs lack the sources for this sort of funding.
Democratizing Safety Operations with XDR
What SMBs want is the flexibility to deliver alerting from all of their IT infrastructure and functions right into a single software, which may analyze all of a corporation’s telemetry, apply menace intelligence, after which present a easy interface that acts as a single pane of glass for managing alerting, performing investigations and responding to threats. That is the place XDR gives an answer that mixes the important thing elements of a standard SecOps toolchain in a single cloud-hosted software, which may be delivered affordably. That is the second key space the place NTTSH has turned its focus in direction of SMBs by focusing the event of its Samurai XDR product on the wants and budgets of SMBs whereas nonetheless delivering the performance that enormous enterprises have turn out to be accustomed to. Whereas GTIC’s analysis gives the intelligence wanted to know and detect the threats dealing with trendy organizations, Samurai XDR makes GTIC’s work accessible and actionable even for organizations that lack devoted SecOps sources. It’s essential to do not forget that whereas menace intelligence is important to have the ability to detect threats, each group wants instruments as a way to apply it.
A short journey by means of Samurai XDR
From the beginning, Samurai XDR is designed to be simple to make use of and, most significantly, to be accessible to all IT employees, not solely to safety analysts. The place to begin of all workflows in Samurai XDR is the alerts dashboard. That is the place the system presents safety alerts which have been prioritized primarily based on severity and confidence.
 |
| Determine 3: Samurai XDR Alerts Dashboard |
The alerts dashboard brings collectively alerts from the entire applied sciences utilized by the group right into a single prioritized view, with a deal with offering an intuitive interface that can be utilized by most IT employees, not solely by specialist safety analysts.
As soon as the person has determined that an alert warrants additional investigation, the Investigations view gives a equally easy and intuitive interface for managing the lifecycle of an investigation of a possible safety incident.
As soon as occasions and alerts are processed, they’re saved in Samurai XDR’s information lake. The information lake gives the flexibility for customers to question and analyze the entire occasions ingested into Samurai XDR, going again as much as one full yr. This makes it doable to interrogate a full yr’s historic information for functions equivalent to menace looking – permitting Samurai XDR customers to carry out detailed analyses of historic occasions for any indicators of threats that will have been dwelling for longer durations of time. Querying the occasions within the information lake is made doable by Samurai XDR’s Superior Question operate, which permits customers to go looking the information lake each graphically and utilizing Microsoft’s Kusto Question Language (KQL).
Integrations
Integrations present the mechanism to ingest telemetry (equivalent to logs) out of your IT infrastructure and functions into Samurai XDR. NTTSH has centered on bringing collectively the right combination of capabilities to ingest telemetry from each on-premises infrastructure and cloud companies, mirroring the sort of hybrid IT surroundings that has turn out to be typical for even most SMBs as we speak. Some examples of integrations at the moment out there embrace:
- Cloud: Azure Administration Airplane and Microsoft 365 (coming quickly), Google Workspace (coming quickly)
- Endpoint Detection and Response: Microsoft Defender for Endpoint, VMWare Carbon Black and Crowdstrike Falcon Perception
- Subsequent-Technology Firewalls: Cisco Safe Firewall (ASA and Firepower Menace Protection), Fortinet Fortigate, and Palo Alto Networks NGFW.
Over the approaching months, NTTSH will probably be busy including extra integrations, together with however not restricted to Meraki, Bitdefender, Sophos, Zoom, MalwareBytes, OneLogin, OKTA, Zscaler, AWS, and lots of extra!
Making it Simple
A key space of focus for NTTSH within the improvement of Samurai XDR has been that of constructing it simple to make use of and straightforward to afford. For instance, the configuration of integrations is supported by easy “level and click on” workflows. For infrastructure that gives logs through syslog, all that’s wanted is to level the log supply at Samurai XDR’s safe syslog collector, and Samurai XDR will do the work of detecting the sort of gadget that’s sending logs. Naturally, it is the identical for cloud integrations. Samurai XDR retains the steps to a minimal and guides the person by means of interactive steps and entry to knowledge-base articles.
Samurai XDR additionally follows a easy pricing mannequin – primarily based solely on the variety of endpoints that the client has, eradicating the necessity to attempt to estimate the information volumes of the telemetry that will probably be ingested into the platform. Normal pricing for 50 endpoints or extra is barely $3.33 per endpoint monthly, and for smaller clients, there’s a Starter Pack for as much as 25 endpoints, which is priced at $750 for a yr.
To make it simple to check out Samurai XDR, NTTSH is offering all new clients with a free 30-day trial, making it doable to expertise all of its performance with none commitments, giving even the smallest SMBs a risk-free path to constructing a complicated SecOps functionality.

