The Android banking trojan generally known as Anatsa has expanded its focus to incorporate Slovakia, Slovenia, and Czechia as a part of a brand new marketing campaign noticed in November 2023.
“A few of the droppers within the marketing campaign efficiently exploited the accessibility service, regardless of Google Play’s enhanced detection and safety mechanisms,” ThreatFabric stated in a report shared with The Hacker Information.
“All droppers on this marketing campaign have demonstrated the aptitude to bypass the restricted settings for accessibility service in Android 13.” The marketing campaign, in whole, entails 5 droppers with greater than 100,000 whole installations.
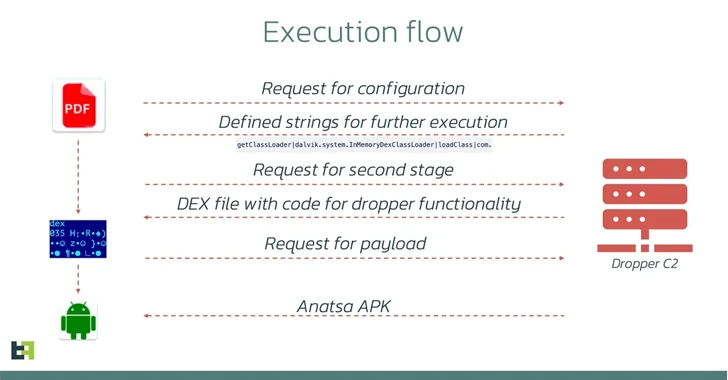
Additionally recognized by the title TeaBot and Toddler, Anatsa is understood to be distributed beneath the guise of seemingly innocuous apps on the Google Play Retailer. These apps, referred to as droppers, facilitate the set up of the malware by circumventing safety measures imposed by Google that search to grant delicate permissions.
In June 2023, the Dutch cellular safety agency disclosed an Anatsa marketing campaign that focused banking prospects within the U.S., the U.Okay., Germany, Austria, and Switzerland a minimum of since March 2023 utilizing dropper apps that had been collectively downloaded over 30,000 instances on the Play Retailer.
Anatsa comes fitted with capabilities to realize full management over contaminated gadgets and execute actions on a sufferer’s behalf. It will probably additionally steal credentials to provoke fraudulent transactions.
The most recent iteration noticed in November 2023 is not any completely different in that one of many droppers masqueraded as a cellphone cleaner app named “Cellphone Cleaner – File Explorer” (package deal title “com.volabs.androidcleaner”) and leveraged a method referred to as versioning to introduce its malicious conduct.
Whereas the app is not out there for obtain from the official storefront for Android, it might nonetheless be downloaded through different sketchy third-party sources.
In accordance with statistics out there on app intelligence platform AppBrain, the app is estimated to have been downloaded about 12,000 instances throughout the time it was out there on the Google Play Retailer between November 13 and November 27, when it was unpublished.
“Initially, the app appeared innocent, with no malicious code and its accessibility service not partaking in any dangerous actions,” ThreatFabric researchers stated.
“Nonetheless, per week after its launch, an replace launched malicious code. This replace altered the AccessibilityService performance, enabling it to execute malicious actions reminiscent of routinely clicking buttons as soon as it acquired a configuration from the [command-and-control] server.”
What makes the dropper notable is that its abuse of the accessibility service is tailor-made to Samsung gadgets, suggesting that it was designed to solely goal the company-made handsets in some unspecified time in the future, though different droppers used within the marketing campaign have been discovered to be producer agnostic.
The droppers are additionally able to circumventing Android 13’s restricted settings by mimicking the method utilized by marketplaces to put in new functions with out having their entry to the accessibility service functionalities disabled, as beforehand noticed within the case of dropper companies like SecuriDropper.
“These actors choose concentrated assaults on particular areas quite than a world unfold, periodically shifting their focus,” ThreatFabric stated. “This focused method allows them to focus on a restricted variety of monetary organizations, resulting in a excessive variety of fraud instances in a short while.”
The event comes as Fortinet FortiGuard Labs detailed one other marketing campaign that distributes the SpyNote distant entry trojan by imitating a official Singapore-based cryptocurrency pockets service generally known as imToken to interchange vacation spot pockets addresses and with actor-controlled ones and conduct illicit asset transfers.
“Like a lot Android malware right now, this malware abuses the accessibility API,” safety researcher Axelle Apvrille stated. “This SpyNote pattern makes use of the Accessibility API to focus on well-known crypto wallets.”