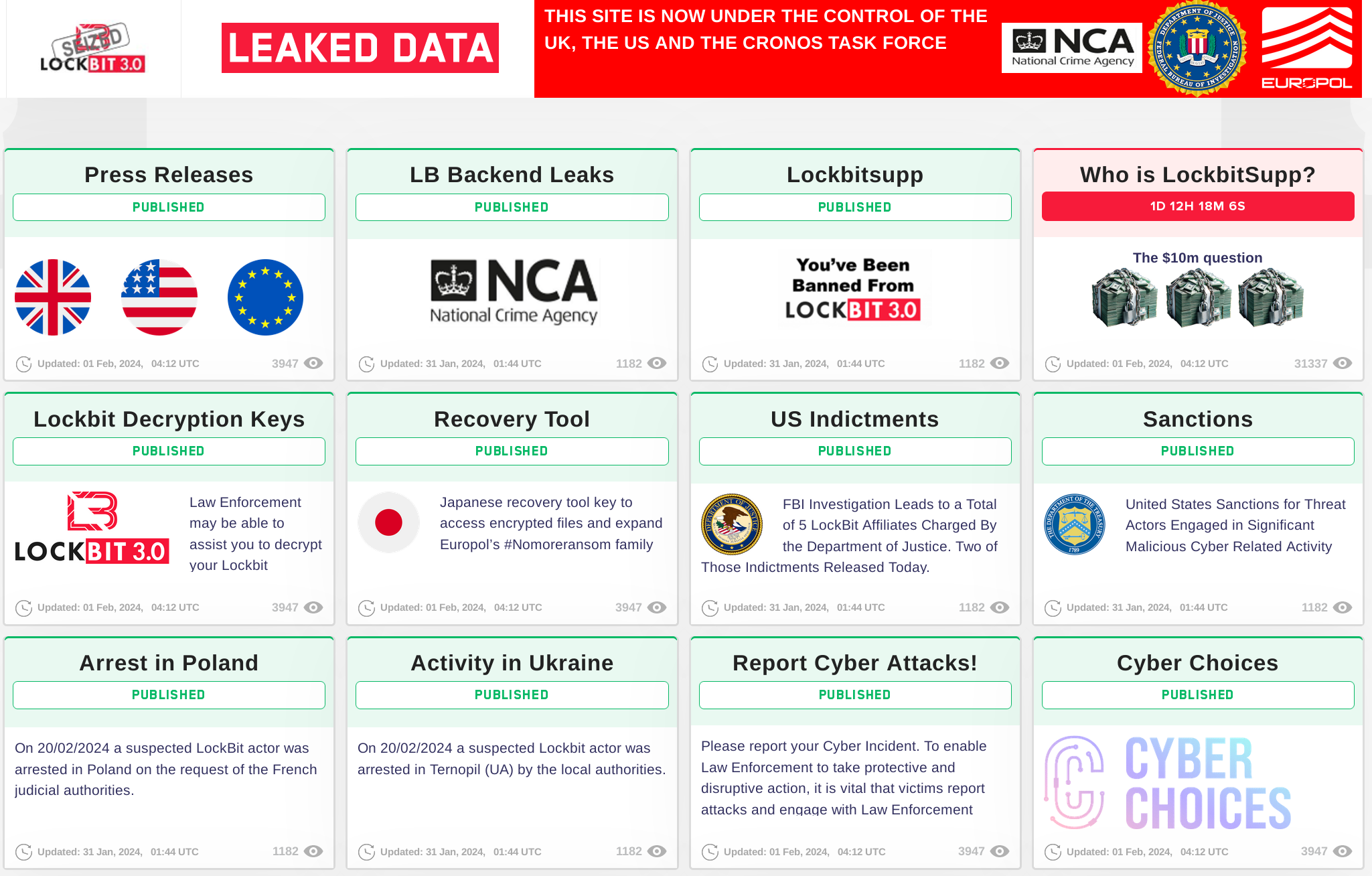
Late on February 19, 2024, the principle web site of LockBit, probably the most prolific ransomware group in current reminiscence, was seized by the UK’s Nationwide Crime Company (NCA). In cooperation with their worldwide regulation enforcement companions at america FBI, the French Gendarmerie Nationwide, Europol, and others, the NCA seized the bodily servers that operated the first web site and have arrested two males, one in Poland and the opposite in Ukraine. Moreover, the US on the identical day introduced sanctions of two Russian nationals for his or her position within the prison syndicate.
Such a coordinated, multinational regulation enforcement motion offers us new insights into how these organized crime teams function, and in addition exposes a number of the limits we have now obtainable to us to rein in this kind of exercise.
Let’s begin with the fundamentals: What precisely makes up a “ransomware syndicate?” More often than not they seem to take the type of an anarcho-syndicalist commune. Normally, that features a core group of software program builders to construct the web sites, malware, and cost websites; somebody to launder cash; and somebody with an honest grasp of English to barter cost with the victims. The precise assaults themselves are performed by so-called “associates.” These associates join to make use of the platform and model identify to extort victims and share the proceeds.
Identification is fluid within the prison underworld
Our first drawback lies in that construction: These “teams” are principally loosely affiliated and working beneath a model identify. Shutting down the model doesn’t essentially influence the core group members themselves. By the US issuing sanctions in opposition to a few of its members, the model “LockBit” is nearly as good as useless. No US-based entity can be keen to pay a ransom to LockBit, but when they reemerge tomorrow as CryptoMegaUnicornBit or comparable, it’s going to begin the cycle over again.
Depriving these people of revenue beneath a brand new identify may be very tough. The sanctions issued at present in opposition to Ivan Kondratyev and Artur Sungatov (the sanctioned Russian nationals) have ruined LockBit, however after they return as DatasLaYeR001 and Crypt0Keeper69 how will victims know that they’re sanctioned entities? The sanctions are merely pace bumps, not actual long-term options to the ransomware drawback.
The 5 indictments by the US Division of Justice (DOJ) are doubtless only the start. In previous instances of this type, the one indictments made public are for people who’re in nations the place the US is unlikely to acquire regulation enforcement cooperation; absent that, the US will select to the sanctioned entities checklist. Hopefully there are extra sealed indictments lurking, unknown for now to their topics; such indictments might, as an example, be used to ensnare different recognized individuals in the event that they make the error of touring internationally on a vacation. Individuals within the LockBit crime household who have been in regulation enforcement-friendly nations have been arrested — in Poland (for cash laundering) and in Ukraine (unspecified) — and can doubtless face costs in France.
Safety is tough
How did regulation enforcement handle to take down these thugs? All indicators are that it could have began with an unpatched safety vulnerability, CVE 2023-3824 — that’s, in case you imagine the criminals themselves. Being knowledgeable prison hacker doesn’t make you magically nice at securing your personal infrastructure, and observers had commented on LockBit’s battle to handle their IT infrastructure in mid-2023 – sarcastically, simply earlier than CVE-2023-3824 was publicly reported.
As soon as the online server working the leak web site was exploited, they have been presumably in a position to bodily seize the servers working the operation and start to unravel an increasing number of of the supporting infrastructure. Press have reported this was a multiyear operation. (As a reminder, LockBit is a comparatively long-lived model; the primary sighting dates again to 2019, and as of 19 February 2024 their very own file leak web page says the location had been up for 4 years and 169 days.)
This isn’t a brand new concept or method. We’ve got seen regulation enforcement “hack” prison infrastructure in earlier instances as effectively, generally utilizing zero-day vulnerabilities in browsers and instruments, different occasions catching the criminals making an error by forgetting to make use of a VPN or Tor Browser, resulting in their identification and apprehension. These operation safety (OpSec) errors are finally the undoing of even probably the most subtle criminals.
If we wish to proceed to extend the stress on these teams, we should ramp up regulation enforcement’s potential to conduct these operations. They’re important not solely to dismantling the infrastructure utilized in these assaults, however to undermining the boldness the co-conspirators place within the security of their participation. We’d like extra expert, competitively compensated cyber-cops and a better-informed judiciary to approve these operations.
Sadly, regardless of the success the NCA and their companions have had, they haven’t completely disabled the Lockbit community. A number of darkish websites utilized by the group are nonetheless obtainable, together with probably the most damaging one among all — the one internet hosting the purloined content material from victims to reveal them in retribution for his or her lack of cost. The hurt was already completed earlier than the takedown, however their compromise was not full.
Boasting, bluster, and perspective
Folks have been commenting on social media concerning the “epic trolling” of the NCA of their seizure and resurrection of the LockBit leak web site. Was this an act of bravado alone or is there a deeper motive on behalf of police and policymakers? I don’t have the reply, but I hope and suspect that is being completed with intent.
Determine 1: The takedown web page is informative, and it guarantees extra pleasure to return later within the week
Expertise means that many, however not all, of the prison puppeteers orchestrating these actions are in nations unable or unwilling to implement the rule of regulation in opposition to teams focusing on Western victims. Moreover, lots of their associates know very effectively they don’t seem to be as well-protected because the group leaders.
By making a scene and instilling worry, uncertainty, and doubt as as to whether their instruments, communications, and identities are being monitored or already compromised may dissuade the supporting actors from collaborating. There was a well-justified paranoia amongst prison gangs for some time that they’ve been compromised by researchers and regulation enforcement. They’re proper. We’re amongst them, watching them. The trolling and publicity the NCA have orchestrated drives house the purpose: We’re in you.
In criminals we belief?
Many victims have argued they paid the ransom to avoid wasting their prospects, staff, and shareholders from having their knowledge uncovered. The concept paying extortionists to delete stolen knowledge is a viable plan has been criticized by specialists because the daybreak of the crime itself. The NCA confirmed what we suspected; the criminals have stored copies of knowledge stolen from victims and will have supposed to additional exploit or monetize stated data. No honor amongst thieves.
What’s doubtless extra vital on this case isn’t our belief that the criminals are good for his or her phrase, relatively how can we unfold this mistrust amongst their very own operatives. Our personal skepticism mixed with the US sanctions needs to be sufficient to offer nearly any of us pause, however can we create an environment the place the criminals themselves are uncertain whom to belief?
I feel this might be our greatest deterrent. Not solely ought to the NCA, FBI, Europol, and others strut and expose after a takedown, however researchers and others ought to frequently expose chats, boards, and different entry they’ve gained on public boards to point out that what appears to be taking place at the hours of darkness is probably going on the radar of many.
Closing ideas
We’re not going to arrest or imprison our means out of this, definitely not when the world is shifting towards an more and more balkanized situation. I really feel like we’re rounding a nook with the maturity of our method; we’re working the levers to use stress the place it counts and at last using a multidisciplinary method on all fronts using the leverage at our disposal.
This occasion won’t finish ransomware and will not even finish the lively participation of many concerned within the LockBit cartel. What it does is advance our method to disrupting these teams, growing their price of doing enterprise and growing the mistrust among the many criminals themselves.
The criminals have been profitable by creating scripts and patterns for systemically exploit victims and we could also be approaching the turning level the place the defenders have a script of their very own. We should stand sturdy and help our regulation enforcement companions on this struggle and work to hit them the place it hurts most. They are saying teamwork makes the dream work and if they’ll’t kind cohesive groups, they may both fade off into the sundown or activate one another. Win – win.