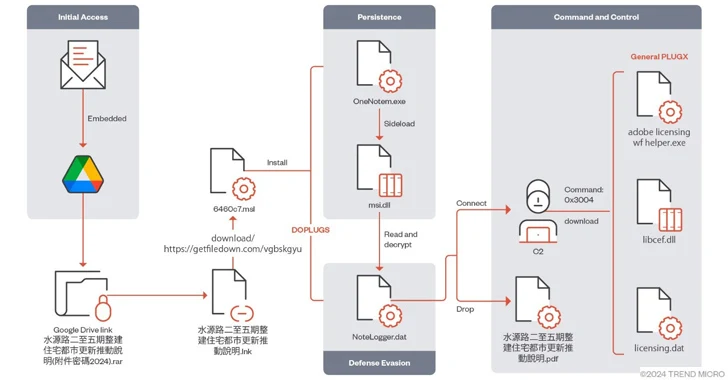
The China-linked menace actor referred to as Mustang Panda has focused numerous Asian international locations utilizing a variant of the PlugX (aka Korplug) backdoor dubbed DOPLUGS.
“The piece of personalized PlugX malware is dissimilar to the final kind of the PlugX malware that accommodates a accomplished backdoor command module, and that the previous is just used for downloading the latter,” Development Micro researchers Sunny Lu and Pierre Lee stated in a brand new technical write-up.
Targets of DOPLUGS have been primarily positioned in Taiwan, and Vietnam, and to a lesser extent in Hong Kong, India, Japan, Malaysia, Mongolia, and even China.
PlugX is a staple software of Mustang Panda, which can be tracked as BASIN, Bronze President, Camaro Dragon, Earth Preta, HoneyMyte, RedDelta, Crimson Lich, Stately Taurus, TA416, and TEMP.Hex. It is identified to be lively since a minimum of 2012, though it first got here to mild in 2017.
The menace actor’s tradecraft entails finishing up well-forged spear-phishing campaigns which can be designed to deploy customized malware. It additionally has a observe document of deploying its personal personalized PlugX variants corresponding to RedDelta, Thor, Hodur, and DOPLUGS (distributed by way of a marketing campaign named SmugX) since 2018.
Compromise chains leverage a set of distinct techniques, utilizing phishing messages as a conduit to ship a first-stage payload that, whereas displaying a decoy doc to the recipient, covertly unpacks a legit, signed executable that is susceptible to DLL side-loading to be able to side-load a dynamic-link library (DLL), which, in flip, decrypts and executes PlugX.
The PlugX malware subsequently retrieves Poison Ivy distant entry trojan (RAT) or Cobalt Strike Beacon to determine a reference to a Mustang Panda-controlled server.
In December 2023, Lab52 uncovered a Mustang Panda marketing campaign focusing on Taiwanese political, diplomatic, and governmental entities with DOPLUGS, however with a notable distinction.
“The malicious DLL is written within the Nim programming language,” Lab52 stated. “This new variant makes use of its personal implementation of the RC4 algorithm to decrypt PlugX, in contrast to earlier variations that use the Home windows Cryptsp.dll library.”
DOPLUGS, first documented by Secureworks in September 2022, is a downloader with 4 backdoor instructions, one in all which is orchestrated to obtain the final kind of the PlugX malware.
Development Micro stated it additionally recognized DOPLUGS samples built-in with a module referred to as KillSomeOne, a plugin that is answerable for malware distribution, info assortment, and doc theft by way of USB drives.
This variant comes fitted with an additional launcher part that executes the legit executable to carry out DLL-sideloading, along with supporting performance to run instructions and obtain the next-stage malware from an actor-controlled server.
It is price noting {that a} personalized PlugX variant, together with the KillSomeOne module designed for spreading by way of USB, was uncovered as early as January 2020 by Avira as a part of assaults directed in opposition to Hong Kong and Vietnam.
“This exhibits that Earth Preta has been refining its instruments for a while now, consistently including new functionalities and options,” the researchers stated. “The group stays extremely lively, notably in Europe and Asia.”