ESET merchandise and analysis have been defending Ukrainian IT infrastructure for years. For the reason that begin of the struggle in February 2022, we now have prevented and investigated a major variety of assaults launched by Russia-aligned teams. We have now additionally revealed a number of the most attention-grabbing findings on WeLiveSecurity:
Regardless that our principal focus stays on analyzing threats involving malware, we now have discovered ourselves investigating an data operation or psychological operation (PSYOP) making an attempt to boost doubts within the minds of Ukrainians and Ukrainian audio system overseas.
Operation Texonto
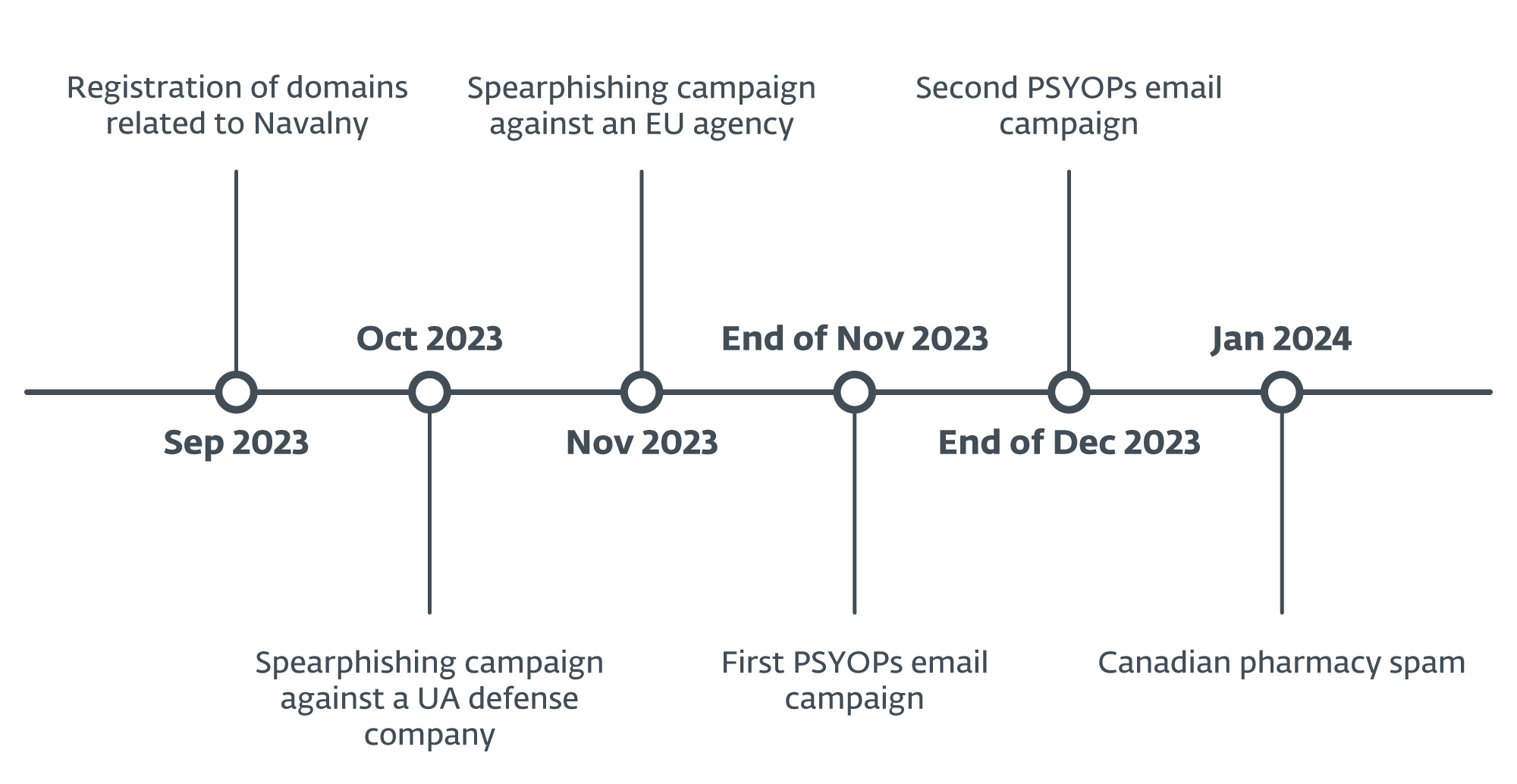
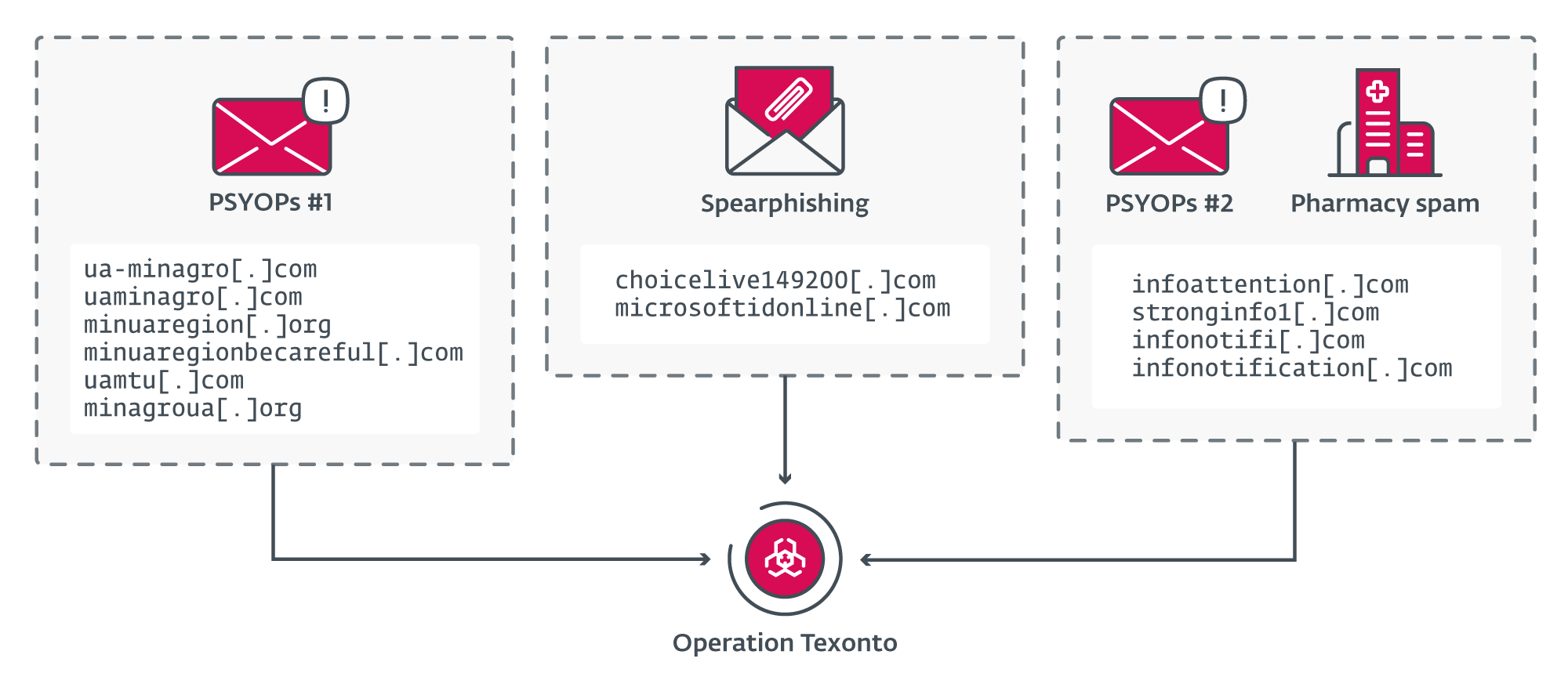
Operation Texonto is a disinformation/PSYOP marketing campaign utilizing spam mails as the primary distribution technique. Surprisingly, it doesn’t appear that the perpetrators used frequent channels comparable to Telegram or pretend web sites to convey their messages. We have now detected two completely different waves, the primary one in November 2023 and the second on the finish of December 2023. The contents of the emails had been about heating interruptions, drug shortages, and meals shortages, that are typical themes of Russian propaganda.
Along with the disinformation marketing campaign, we now have detected a spearphishing marketing campaign that focused a Ukrainian protection firm in October 2023 and an EU company in November 2023. The objective of each was to steal credentials for Microsoft Workplace 365 accounts. Due to similarities within the community infrastructure utilized in these PSYOPs and phishing operations, we’re linking them with excessive confidence.
Curiously, just a few extra pivots additionally revealed domains which might be a part of Operation Texonto and associated to inner Russian subjects comparable to Alexei Navalny, the well-known Russian opposition chief who was in jail and died on February 16th, 2024. Which means Operation Texonto most likely contains spearphishing or data operations concentrating on Russian dissidents and supporters of the late opposition chief. These domains embrace:
- navalny-votes[.]web
- navalny-votesmart[.]web
- navalny-voting[.]web
Even perhaps stranger is that an electronic mail server, operated by the attackers and used to ship PSYOP emails, was reused two weeks later to ship typical Canadian pharmacy spam. This class of unlawful enterprise has been highly regarded inside the Russian cybercrime group for a very long time, as this blogpost from 2011 explains.
Determine 1 summarizes the primary occasions of Operation Texonto.
The unusual brew of espionage, data operations, and pretend pharma can solely remind us of Callisto, a widely known Russia-aligned cyberespionage group who was the topic of an indictment by the US DOJ in December, 2023. Callisto targets authorities officers, individuals in suppose tanks, and military-related organizations by way of spearphishing web sites designed to imitate frequent cloud suppliers. The group has additionally run disinformation operations comparable to a doc leak simply forward of the 2019 UK normal election. Lastly, pivoting on its outdated community infrastructure results in pretend pharma domains comparable to musclepharm[.]prime or ukrpharma[.]ovh.
Whereas there are a number of high-level factors of similarity between Operation Texonto and Callisto operations, we haven’t discovered any technical overlap and we presently don’t attribute Operation Texonto to a selected menace actor. Nonetheless, given the TTPs, concentrating on, and the unfold of messages, we attribute the operation with excessive confidence to a gaggle that’s Russian aligned.
Phishing marketing campaign: October–November 2023
Staff working at a serious Ukrainian protection firm obtained a phishing electronic mail in October 2023, purportedly coming from their IT division. The emails had been despatched from it.[redacted_company_name]@gmail.com, an electronic mail deal with most definitely created particularly for this marketing campaign, and the e-mail topic was Запрошено утверждение:Планова інвентаризація (machine translation from Ukrainian: Approval requested: Deliberate stock).
The content material of the e-mail is the next:
У період з 02 жовтня по 13 жовтня співробітники відділу інформаційних технологій проводять планову інвентаризацію та видалення поштових скриньок, що не використовуються. Якщо Ви плануєте використовувати свою поштову адресу ([redacted_address]@[redacted_company_name].com) у майбутньому, будь ласка, перейдіть на веб-версію поштової скриньки за цим посиланням та увійдіть до системи, використовуючи свої облікові дані.
Жодних додаткових дій не потрібно, Ваша поштова скринька отримає статус “підтверджений” і не буде видалена під час планової інвентаризації ресурсів. Якщо ця поштова адреса не використовується Вами (або її використання не планується в майбутньому), то в цьому випадку Вам не потрібно виконувати жодних дій – поштову скриньку буде видалено автоматично 13 жовтня 2023 року.
З повагою,
Відділ інформаційних технологій.
A machine translation of the e-mail is:
Within the interval from October 2 to October 13, staff of the data expertise division will conduct a deliberate stock and elimination of unused mailboxes. In case you plan to make use of your electronic mail deal with ([redacted_address]@[redacted_company_name].com) sooner or later, please go to the online model of the mailbox at this hyperlink and log in utilizing your credentials.
No further actions are required, your mailbox will obtain the standing “confirmed” and won’t be eliminated throughout a scheduled useful resource stock. If this electronic mail deal with will not be utilized by you (or its use will not be deliberate sooner or later), then on this case you do not want to take any motion – the mailbox shall be deleted robotically on October 13, 2023.
Finest regards,
Division of data applied sciences.
The objective of the e-mail is to entice targets into clicking on за цим посиланням (machine translation: at this hyperlink), which ends up in https://login.microsoftidonline[.]com/frequent/oauth2/authorize?client_id=[redacted];redirect_uri=httpspercent3apercent2fpercent2foutlook.office365.compercent2fowapercent2f&useful resource=[redacted]&response_mode=form_post&response_type=code+id_token&scope=openid&msafed=1&msaredir=1&client-request-id=[redacted]&protectedtoken=true&claims=%7bpercent22id_tokenpercent22percent3apercent7bpercent22xms_ccpercent22percent3apercent7bpercent22valuespercent22percent3apercent5bpercent22CP1percent22percent5dpercent7dpercent7dpercent7d&domain_hint=[redacted]&nonce=[redacted]&state=[redacted] (partially redacted). This URL factors to the malicious area login.microsoftidon-line[.]com. Word that this area could be very near the official one, login.microsoftonline.com.
We haven’t been in a position to retrieve the phishing web page, however it was most definitely a pretend Microsoft login web page supposed to steal the targets’ credentials.
For one more area belonging to Operation Texonto, choicelive149200[.]com, there have been two VirusTotal submissions (one and two) for the URL https://choicelive149200[.]com/owa/auth/logon.aspx?replaceCurrent=1&url=https://hbd.eupolcopps.eu/owa/. Sadly, the positioning was not reachable on the time of research, however it was doubtless a credential-phishing web page for the Outlook on the net/OWA webmail of eupolcopps.eu, the EU Coordinating Workplace for Palestinian Police Help. Word that we now have not seen the e-mail pattern, simply the URL submitted to VirusTotal.
First PSYOP wave: November 2023
On November 20th, we detected the primary wave of disinformation emails with a PDF attachment despatched to at the very least just a few hundred recipients in Ukraine. Folks working on the Ukrainian authorities, power firms, and even people, obtained the emails. We have no idea how the listing of electronic mail addresses was constructed.
Opposite to the beforehand described phishing marketing campaign, the objective of those emails was to sow doubt within the thoughts of Ukrainians; as an illustration, one electronic mail says that “There could also be heating interruptions this winter”. It doesn’t appear there was any malicious hyperlink or malware on this particular wave, solely disinformation.
Determine 2 exhibits an electronic mail instance. Its topic is Рекомендації моз україни на тлі дефіциту ліків (machine translation from Ukrainian: Suggestions of the Ministry of Well being of Ukraine on the time of a scarcity of medicines) and the e-mail was despatched from mozua@ua-minagro[.]com. Word that this deal with might be seen within the envelope-from and return-path fields.
ua-minagro[.]com is a site operated by the attackers and was used completely for sending disinformation emails on this marketing campaign. The area is masquerading because the Ministry of Agrarian Coverage and Meals of Ukraine whose authentic area is minagro.gov.ua.
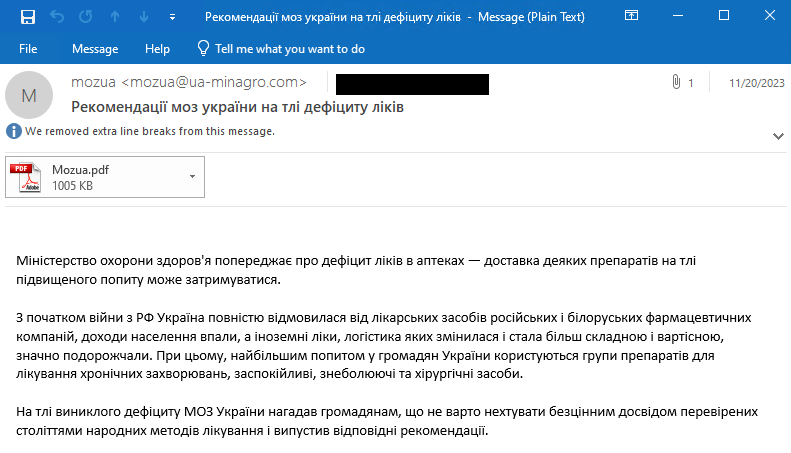
Connected to the e-mail is a PDF doc, as proven in Determine 3. Whereas it isn’t malicious per se, it additionally comprises disinformation messages.

The doc is misusing the brand of the Ministry of Well being of Ukraine and explains that as a result of struggle, there’s a drug scarcity in Ukraine. It additionally says that the Ukrainian authorities is refusing to import medicine from Russia and Belarus. On the second web page, they clarify the best way to substitute some medicine with crops.
What’s attention-grabbing to notice is that the e-mail was despatched from a site masquerading because the Ministry of Agrarian Coverage and Meals of Ukraine, whereas the content material is about drug shortages and the PDF is misusing the brand of the Ministry of Well being of Ukraine. It’s probably a mistake from the attackers or, at the very least, exhibits they didn’t care about all particulars.
Along with ua-minagro[.]com, 5 further domains had been used to ship emails on this wave:
- uaminagro[.]com
- minuaregion[.]org
- minuaregionbecareful[.]com
- uamtu[.]com
- minagroua[.]org
minuaregion[.]org and minuaregionbecareful[.]com are masquerading because the Ministry of Reintegration of the Quickly Occupied Territories of Ukraine whose authentic web site is https://minre.gov.ua/en/.
uamtu[.]com is masquerading because the Ministry of Growth of Communities, Territories and Infrastructure of Ukraine, whose authentic web site is https://mtu.gov.ua.
We have now recognized three extra completely different electronic mail message templates, every with a unique mail physique and PDF attachment. A abstract is offered in Desk 1.
Desk 1. Disinformation emails
|
E mail physique |
Machine translation of the e-mail physique |
|
Російськими військовими системно обстрілюються об’єкти енергетичної інфраструктури. У разі виникнення екстреної ситуації подача опалення та електрики в будинки може бути повністю припинена. Щоб вижити в такій ситуації, рекомендуємо вам наступне: |
The Russian army is systematically shelling the power amenities infrastructure. Heating provide in case of an emergency and electrical energy to properties could also be utterly lower off. To outlive in such a scenario, we suggest the next: |
|
Цієї зими можуть спостерігатися перебої з опаленням. Рівень температури в будинках може бути нижче допустимих значень на кілька градусів. У деяких випадках можливо навіть відключення опалення, об’єкти енергетичної безпеки знаходяться під постійною загрозою. У зв’язку з цим, радимо взяти до уваги наступні рекомендації. |
There could also be heating interruptions this winter. Temperature degree in homes might be a number of levels under the permissible values. In some circumstances, it’s even attainable to show off the heating, amenities power safety are beneath fixed menace. On this regard, we advise you to keep in mind the next suggestions. |
|
Міністерство охорони здоров’я попереджає про дефіцит ліків в аптеках — доставка деяких препаратів на тлі підвищеного попиту може затримуватися. З початком війни з РФ Україна повністю відмовилася від лікарських засобів російських і білоруських фармацевтичних компаній, доходи населення впали, а іноземні ліки, логістика яких змінилася і стала більш складною і вартісною, значно подорожчали. При цьому, найбільшим попитом у громадян України користуються групи препаратів для лікування хронічних захворювань, заспокійливі, знеболюючі та хірургічні засоби. На тлі виниклого дефіциту МОЗ України нагадав громадянам, що не варто нехтувати безцінним досвідом перевірених століттями народних методів лікування і випустив відповідні рекомендації. |
The Ministry of Well being warns of a scarcity of medicines in pharmacies — supply of some medicine in opposition to the background of elevated demand could also be delayed. With the start of the struggle with the Russian Federation, Ukraine utterly refused Russian and Belarusian pharmaceutical medicine firms, incomes of the inhabitants fell, and international medicines, the logistics of which modified and have become extra advanced and costly, considerably turned costlier. On the similar time, the best demand is from residents. Ukraine makes use of teams of medicine for the therapy of continual illnesses, sedatives, ache relievers and surgical means. In opposition to the background of the scarcity, the Ministry of Well being of Ukraine reminded residents that you shouldn’t neglect the invaluable expertise of the examined centuries of folks strategies of therapy and launched the suitable ones really useful. |
|
Агресія Росії призвела до значних втрат в аграрному секторі України. Землі забруднені мінами, пошкоджені снарядами, окопами і рухом військової техніки. У великій кількості пошкоджено та знищено сільськогосподарську техніку, знищено зерносховища. До стабілізації обстановки Міністерство аграрної політики та продовольства рекомендує вам урізноманітнити раціон стравами з доступних дикорослих трав. Вживання свіжих, соковитих листя трав у вигляді салатів є найбільш простим, корисним і доступним. Пам’ятайте, що збирати рослини слід далеко від міст і селищ, а також від жвавих трас. Пропонуємо вам кілька корисних і простих у приготуванні рецептів. |
Russia’s aggression led to vital losses within the agricultural sector of Ukraine. The lands are polluted by mines, broken by shells, trenches, and the motion of army gear. A considerable amount of agricultural equipment was broken and destroyed, and granaries had been destroyed. Till the scenario stabilizes, the Ministry of Agrarian Coverage and Meals recommends diversifying your eating regimen with dishes constructed from accessible wild herbs. Consuming contemporary, juicy leaves of herbs within the type of salads is the most straightforward, helpful, and inexpensive. Do not forget that you need to gather crops removed from cities and cities, in addition to from busy roads. We give you a number of helpful and easy-to-prepare recipes. |
The associated PDF attachments are allegedly from the Ukrainian Ministry of Areas (see Determine 4) and the Ministry of Agriculture (see Determine 5).


Within the final doc, allegedly from the Ministry of Agriculture, they counsel to eat “pigeon risotto” and so they even present a photograph of a residing pigeon and a cooked pigeon.… This exhibits these paperwork had been purposely created to be able to rile the readers.
Total, the messages align with frequent Russian propaganda themes. They’re making an attempt to make Ukrainian individuals imagine they received’t have medicine, meals, and heating due to the Russia-Ukraine struggle.
Second PSYOP wave: December 2023
A couple of month after the primary wave, we detected a second PSYOP electronic mail marketing campaign concentrating on not solely Ukrainians, but additionally individuals in different European international locations. The targets are considerably random, starting from the Ukrainian authorities to an Italian shoe producer. As a result of all of the emails are written in Ukrainian, it’s doubtless that the international targets are Ukrainian audio system. In accordance with ESET telemetry, just a few hundred individuals obtained emails on this second wave.
We discovered two completely different electronic mail templates on this wave. The primary one was despatched on December 25th and is proven in Determine 6. As for the primary wave, the e-mail messages had been despatched from an electronic mail server operated by the attackers, infoattention[.]com on this case.
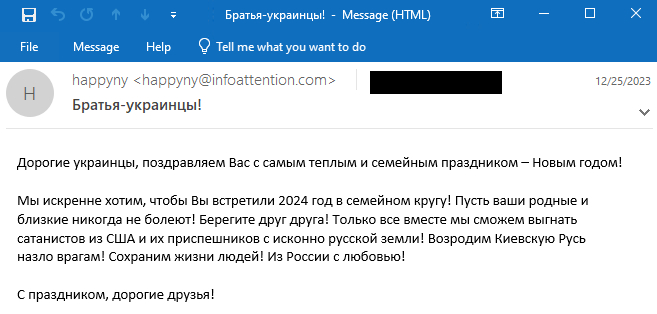
A machine translation of the e-mail physique is the next:
Expensive Ukrainians, we congratulate you on the warmest and most household vacation – the New 12 months!
We sincerely need you to have fun 2024 with your loved ones! Could your loved ones and pals by no means get sick! Handle one another! Solely collectively we can drive out the Satanists from the USA and their minions from the unique Russian soil! Let’s revive Kievan Rus despite our enemies! Let’s save individuals’s lives! From Russia with love!
Completely satisfied vacation, pricey pals!
The second electronic mail template, proven in Determine 7, was despatched on December 26th, 2023 from a unique electronic mail server: stronginfo1[.]com. Throughout this wave, two further electronic mail addresses had been used:
- happyny@infonotifi[.]com
- happyny@infonotification[.]com
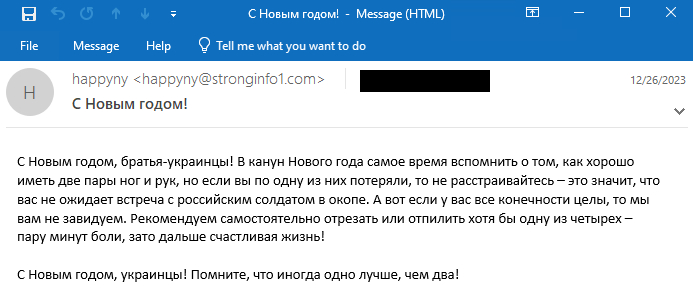
A machine translation of the e-mail physique is the next:
Completely satisfied New 12 months, Ukrainian brothers! On New 12 months’s Eve, it is time to bear in mind how good it’s to have two pairs of legs and arms, however when you’ve got misplaced one in every of them, then do not be upset – which means you will not meet a Russian soldier in a trench. And right here if all of your limbs are intact, then we don’t envy you. We suggest slicing or sawing off at the very least one of many 4 your self – a few minutes of ache, however then a contented life!
Completely satisfied New 12 months, Ukrainians! Do not forget that typically one is healthier than two!
Whereas the primary PSYOP electronic mail marketing campaign in November 2023 was quite well-prepared, with specifically created PDF paperwork that had been considerably convincing, this second marketing campaign is quite extra primary and darker in its messaging. The second electronic mail template is especially disturbing, with the attackers suggesting individuals amputate a leg or arm to keep away from army deployment. Total, it has all of the traits of PSYOPs throughout struggle time.
Canadian pharmacy spam: January 2024
In a fairly stunning twist of occasions, one of many domains used to ship PSYOP emails in December 2023, infonotification[.]com, began getting used to ship Canadian pharmacy spam on January 7th, 2024.
An instance is offered in Determine 8 and the hyperlink redirects to the pretend Canadian pharmacy web site onlinepharmacycenter[.]com. The spam marketing campaign was reasonably giant (within the lots of of messages at the very least) and other people in lots of international locations obtained such emails.
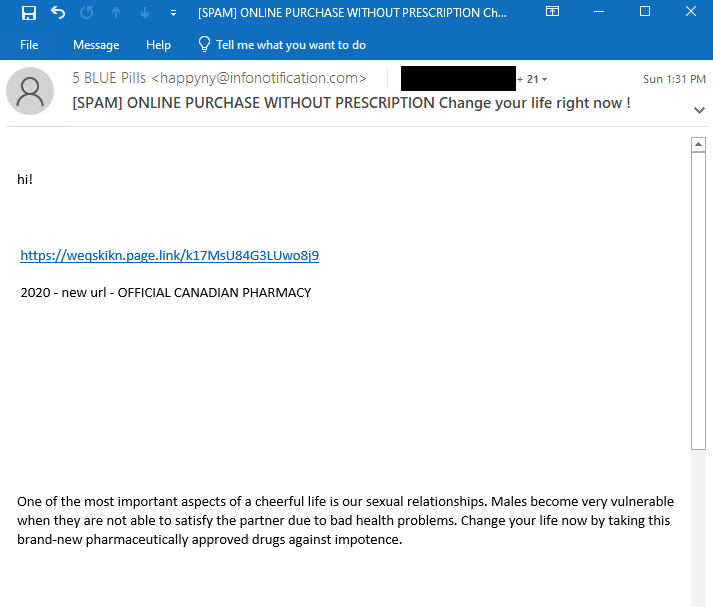
The emails had been despatched from happyny@infonotification[.]com and this was verified within the electronic mail headers:
Return-Path: <happyny@infonotification[.]com>
Delivered-To: [redacted]
[redacted]
Acquired: from infonotification[.]com ([185.12.14[.]13])
by [redacted] with esmtps (TLS1.3:TLS_AES_256_GCM_SHA384:256)
[redacted]
Solar, 07 Jan 2024 12:39:10 +0000
Faux Canadian pharmacy spam is a enterprise traditionally operated by Russian cybercriminals. It was extensively lined up to now by bloggers comparable to Brian Krebs, particularly in his Spam Nation ebook.
Hyperlinks between these spam campaigns
Whereas we don’t know why the operators of the PSYOP campaigns determined to reuse one in every of their servers to ship pretend pharmacy spam, it’s doubtless that they realized that their infrastructure was detected. Therefore, they might have determined to attempt to monetize the already burnt infrastructure, both for their very own revenue or to fund future espionage operations or PSYOPs. Determine 9 summarizes the hyperlinks between the completely different domains and campaigns.
Conclusion
For the reason that begin of the struggle in Ukraine, Russia-aligned teams comparable to Sandworm have been busy disrupting Ukrainian IT infrastructure utilizing wipers. In current months, we now have noticed an uptick in cyberespionage operations, particularly by the notorious Gamaredon group.
Operation Texonto exhibits yet one more use of applied sciences to attempt to affect the struggle. We discovered just a few typical pretend Microsoft login pages however most significantly, there have been two waves of PSYOPs by way of emails most likely to attempt to affect and demoralize Ukrainian residents with disinformation messages about war-related subjects.
A complete listing of Indicators of Compromise (IoCs) and samples might be present in our GitHub repository.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.
ESET Analysis provides non-public APT intelligence stories and information feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
Recordsdata
|
SHA-1 |
Filename |
ESET detection identify |
Description |
|
3C201B2E40357996B383 |
Minagroua111.pdf |
PDF/Fraud.CDY |
PDF utilized in an data operation in opposition to Ukraine. |
|
15BF71A771256846D44E |
Mozua.pdf |
PDF/Fraud.CDU |
PDF utilized in an data operation in opposition to Ukraine. |
|
960341B2C296C425821E |
Minregion.pdf |
PDF/Fraud.CDT |
PDF utilized in an data operation in opposition to Ukraine. |
|
BB14153040608A4F559F |
Minregion.pdf |
PDF/Fraud.CDX |
PDF utilized in an data operation in opposition to Ukraine. |
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
N/A |
navalny-votes[.]web |
N/A |
2023-09-09 |
Area associated to Alexei Navalny. |
|
N/A |
navalny-votesmart[.]web |
N/A |
2023-09-09 |
Area associated to Alexei Navalny. |
|
N/A |
navalny-voting[.]web |
N/A |
2023-09-09 |
Area associated to Alexei Navalny. |
|
45.9.148[.]165 |
infoattention[.]com |
Good IT Providers Group Inc. |
2023-12-25 |
Server used to ship emails in Operation Texonto. |
|
45.9.148[.]207 |
minuaregionbecareful[.]com |
Good IT Providers Group Inc. |
2023-11-23 |
Server used to ship emails in Operation Texonto. |
|
45.9.150[.]58 |
stronginfo1[.]com |
Good IT Providers Group Inc. |
2023-12-25 |
Server used to ship emails in Operation Texonto. |
|
45.129.199[.]200 |
minuaregion[.]org |
Hostinger |
2023-11-21 |
Server used to ship emails in Operation Texonto. |
|
45.129.199[.]222 |
uamtu[.]com |
Hostinger |
2023-11-20 |
Server used to ship emails in Operation Texonto. |
|
46.249.58[.]177 |
infonotifi[.]com |
serverius-mnt |
2023-12-28 |
Server used to ship emails in Operation Texonto. |
|
89.116.52[.]79 |
uaminagro[.]com |
IPXO LIMITED |
2023-11-17 |
Server used to ship emails in Operation Texonto. |
|
154.49.137[.]16 |
choicelive149200[.]com |
Hostinger |
2023-10-26 |
Phishing server. |
|
185.12.14[.]13 |
infonotification[.]com |
Serverius |
2023-12-28 |
Server used to ship emails in Operation Texonto. |
|
193.43.134[.]113 |
login.microsoftidonline[.]com |
Hostinger |
2023-10-03 |
Workplace 365 phishing server. |
|
195.54.160[.]59 |
minagroua[.]org |
BlueVPS |
2023-11-21 |
Server used to ship emails in Operation Texonto. |
E mail addresses
- minregion@uaminagro[.]com
- minregion@minuaregion[.]org
- minregion@minuaregionbecareful[.]com
- minregion@uamtu[.]com
- mozua@ua-minagro[.]com
- mozua@minagroua[.]org
- minagroua@vps-3075.lethost[.]community
- happyny@infoattention[.]com
- happyny@stronginfo1[.]com
- happyny@infonotifi[.]com
- happyny@infonotification[.]com
MITRE ATT&CK methods
This desk was constructed utilizing model 14 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Identify |
Description |
|
Useful resource Growth |
Purchase Infrastructure: Domains |
Operators purchased domains at Namecheap. |
|
|
Purchase Infrastructure: Server |
Operators rented servers at Good IT, Hostinger, Serverius, and BlueVPS. |
||
|
Preliminary Entry |
Phishing |
Operators despatched emails with disinformation content material. |
|
|
Phishing: Spearphishing Hyperlink |
Operators despatched emails with a hyperlink to a pretend Microsoft login web page. |
||
|
Protection Evasion |
Masquerading |
Operators used domains much like official Ukrainian authorities domains. |

