Greater than 8,000 domains and 13,000 subdomains belonging to legit manufacturers and establishments have been hijacked as a part of a classy distribution structure for spam proliferation and click on monetization.
Guardio Labs is monitoring the coordinated malicious exercise, which has been ongoing since a minimum of September 2022, beneath the title SubdoMailing. The emails vary from “counterfeit bundle supply alerts to outright phishing for account credentials.”
The Israeli safety firm attributed the marketing campaign to a menace actor it calls ResurrecAds, which is understood to resuscitate useless domains of or affiliated with huge manufacturers with the tip purpose of manipulating the digital promoting ecosystem for nefarious features.
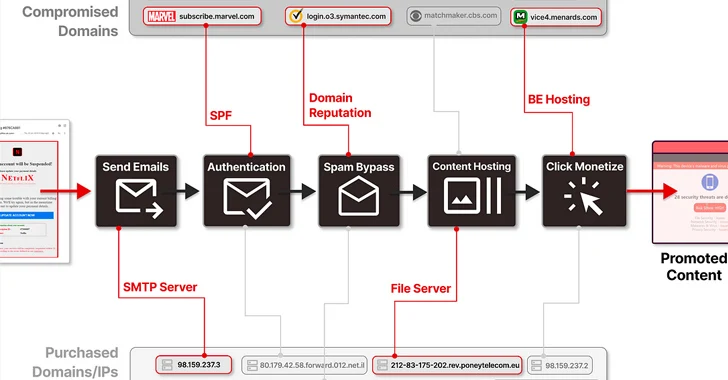
“‘ResurrecAds’ manages an intensive infrastructure encompassing a wide selection of hosts, SMTP servers, IP addresses, and even non-public residential ISP connections, alongside many extra owned domains,” safety researchers Nati Tal and Oleg Zaytsev mentioned in a report shared with The Hacker Information.
Particularly, the marketing campaign “leverages the belief related to these domains to flow into spam and malicious phishing emails by the hundreds of thousands every day, cunningly utilizing their credibility and stolen sources to slide previous safety measures.”
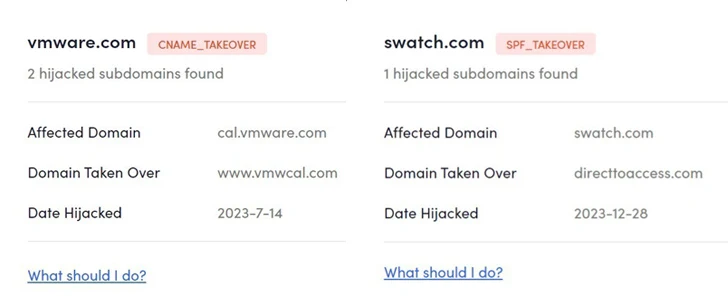
These subdomains belong to or are affiliated with huge manufacturers and organizations equivalent to ACLU, eBay, Lacoste, Marvel, McAfee, MSN, Pearson, PwC, Swatch, Symantec, The Economist, UNICEF, and VMware, amongst
The marketing campaign is notable for its capacity to bypass commonplace safety blocks, with all the physique conceived as a picture to evade text-based spam filters, clicking which initiates a collection of redirections by way of totally different domains.
“These redirects verify your machine kind and geographic location, resulting in content material tailor-made to maximise revenue,” the researchers defined.
“This may very well be something from an annoying advert or affiliate hyperlink to extra misleading techniques like quiz scams, phishing websites, or perhaps a malware obtain aimed toward swindling you out of your cash extra straight.”
One other essential facet of those emails is that also they are able to circumventing Sender Coverage Framework (SPF), an electronic mail authentication methodology that is designed to stop spoofing by making certain a mail server is permitted to ship electronic mail for a given area.
It is not simply SPF, because the emails additionally go DomainKeys Recognized Mail (DKIM) and Area-based Message Authentication, Reporting and Conformance (DMARC) checks that assist stop messages from being marked as spam.
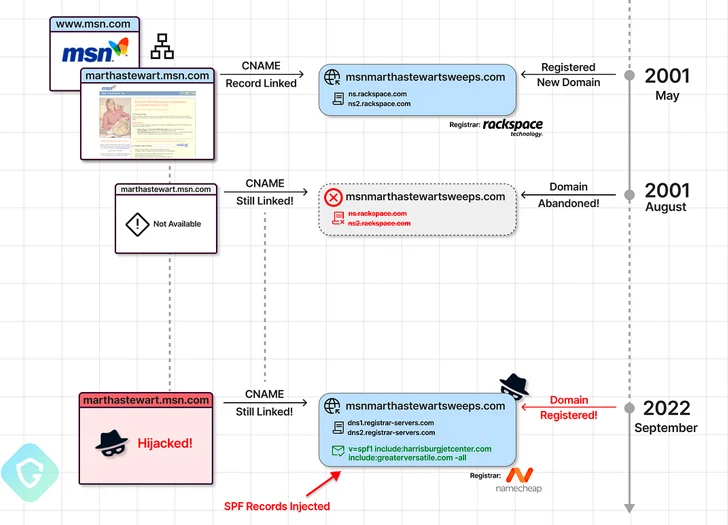
In a single instance of a misleading cloud storage warning electronic mail highlighted by Guardio, the message originated from an SMTP server in Kyiv, but was flagged as being despatched from Return_UlKvw@marthastewart.msn.com.
A more in-depth examination of the DNS document for marthastewart.msn.com revealed that the subdomain is linked to a different area (msnmarthastewartsweeps[.]com) by way of a CNAME document, an aliasing method that has been beforehand weaponized by promoting expertise firms to get round third-party cookie blocking.
“Which means that the subdomain inherits all the habits of msnmarthastewartsweeps[.]com , together with its SPF coverage,” the researchers mentioned. “On this case, the actor can ship emails to anybody they want as if msn[.]com and their authorized mailers despatched these emails!”
It is value mentioning right here that each the domains had been legit and briefly lively sooner or later in 2001, earlier than they had been left in an deserted state for 21 years. It wasn’t till September 2022 when msnmarthastewartsweeps[.]com was privately registered with Namecheap.
In different the hijacking scheme entails the menace actors systematically scanning for long-forgotten subdomains with dangling CNAME information of deserted domains after which registering them to take management of them.
CNAME-takeover can even have critical penalties when such reputed subdomains are seized to host bogus phishing touchdown pages designed to reap customers’ credentials. That mentioned, there is no such thing as a proof that any of the hijacked subdomains have been used for this objective.
Guardio mentioned it additionally discovered situations the place the DNS SPF document of a recognized area holds deserted domains related to defunct email- or marketing-related companies, thereby permitting attackers to seize possession of such domains, inject their very own IP addresses into the document, and finally ship emails on behalf of the principle area title.
In an effort to counter the menace and dismantle the infrastructure, Guardio has made out there a SubdoMailing Checker, a web site that permits area directors and web site house owners to search for indicators of compromise.
“This operation is meticulously designed to misuse these belongings for distributing varied malevolent ‘Ads,’ aiming to generate as many clicks as attainable for these ‘advert community’ shoppers,” the researchers mentioned.
“Armed with an enormous assortment of compromised respected domains, servers, and IP addresses, this advert community deftly navigates by way of the malicious electronic mail propagation course of, seamlessly switching and hopping amongst its belongings at will.”