Highlights from CrowdStrike’s 2024 report:
|
CrowdStrike’s new 2024 World Risk report uncovered the newest tendencies in cyberattacks, and we’re highlighting the primary subjects of curiosity for enterprises.
The cyberattacks ecosystem retains rising, with CrowdStrike observing 34 new risk actors in 2023. Attackers more and more goal cloud environments, principally for monetary motives. But in some circumstances, it permits attackers to achieve on-premise servers.
Provide chain assaults are sometimes used, as these assaults enable a risk actor to hit a number of targets simply. Organizations working within the tech sector are additionally uniquely in danger from these assaults, as practically each trusted-relationship compromise originated from intrusions into organizations offering business software program. Finish of Life merchandise and unmanaged gadgets within the community periphery are additionally focused.
1. Id-based and social engineering assaults nonetheless take heart stage.
Whereas phishing continues to be a legitimate methodology to acquire credentials from workers of focused organizations, different authentication information can be used to conduct assaults. Irrespective of the motivation for a cybersecurity assault, identity-based and social engineering assaults are nonetheless taking heart stage.
For instance, the FANCY BEAR risk actor carried out phishing campaigns in 2023 and developed a customized toolkit to gather credentials from Yahoo! Mail and ukr.internet webmail customers. The toolkit made use of the Browser-in-the-Browser method and added multifactor authentication interception capabilities to gather one-time passwords used within the authentication.
SCATTERED SPIDER used SMS phishing (smishing) and voice phishing (vishing) to get credentials. And the risk actor leveraged earlier intrusions at telecom organizations to run SIM swap operations on focused workers; as soon as the SIM swap is lively, the risk actor may obtain SMS messages with OTP codes instantly. Moreover, the risk actor usually used residential proxies to bypass detections based mostly on the bodily location of their goal.
API keys and secrets and techniques are additionally focused by attackers — proudly owning these permits a cybercriminal to take care of indefinite entry so long as the API keys or secrets and techniques should not modified. Cookie session and token theft had been additionally utilized in 2023 by risk actors.
As well as, attackers steal or forge Kerberos tickets to realize entry to encrypted credentials that may be cracked offline. An enormous 583% enhance in Kerberoasting assaults has been noticed by CrowdStrike.
2. Cloud-environment intrusions elevated by 75%.
CrowdStrike famous that cloud-environment intrusions have elevated globally by 75% from 2022 to 2023 (Determine A).
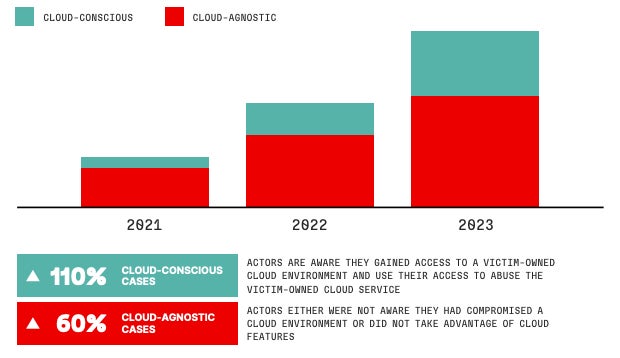
In CrowdStrike’s evaluation, the workforce separates cloud-conscious circumstances (i.e., circumstances by which the attacker is conscious of the cloud setting and makes use of it) and cloud-agnostic circumstances (i.e., an attacker doesn’t discover the cloud setting or doesn’t use it).
Cloud-conscious circumstances have elevated by 110%, whereas cloud-agnostic circumstances have elevated by 60% from 2022 to 2023.
Cybercriminals with monetary motivation are probably the most lively in focusing on cloud environments; they’re answerable for 84% of all cloud-conscious intrusions, whereas focused intrusions solely characterize 16%.
Attackers would possibly leverage cloud-environment intrusions to focus on company networks. For example, the SCATTERED SPIDER risk actor usually makes use of the sufferer’s Microsoft 365 environments to seek for VPN directions earlier than utilizing the VPN to entry and transfer laterally inside the interior community of the focused group.
3. Third-party relationships exploitation make it simpler for attackers to hit lots of of targets
Focused intrusion actors persistently tried to take advantage of trusted relationships to realize entry to organizations throughout a number of verticals and areas in 2023, based on CrowdStrike’s report.
These assaults have an fascinating return on funding for attackers: compromising a third-party that gives IT companies or a third-party that’s a part of a software program provide chain can result in lots of or hundreds of follow-on targets. These assaults can even extra successfully assist attackers focusing on a hardened group.
For instance, JACKPOT PANDA used a trojanized installer for CloudChat, a China-based widespread chat software usually utilized by playing communities, which in the long run contaminated customers with a malware named XShade.
In one other case, an unidentified risk actor compromised an India-based data safety software program vendor to distribute malware by way of the reliable software program replace course of.
In accordance with CrowdStrike, trusted-relationship compromises will proceed to draw focused intrusion actors within the fast future. Organizations working within the expertise sector are at increased threat as a result of they supply their companies to plenty of organizations worldwide.
4. CrowdStrike added 34 new risk actors in 2023.
Over the course of 2023, CrowdStrike added 34 new risk actors — which additionally they name adversaries — to its record of 232 actors. Along with these identified adversaries, CrowdStrike tracks greater than 130 lively and malicious exercise clusters.
Devoted Knowledge Leak websites confirmed a 76% enhance over 2022 within the variety of victims being uncovered, which brings the full sufferer rely to 4,615 for 2023. Newly emerged Huge Recreation Looking gamers are one of many components that elevated the variety of victims, along with the expansion of current adversary operations and high-volume campaigns reminiscent of a number of Sleek Spider risk actor operations. This risk actor exploited three zero-day vulnerabilities to gather information from lots of of victims worldwide.
5. Attackers are compromising networks at a quicker price.
Gaining an preliminary foothold on a focused community is mostly solely the primary part of an assault; as soon as they’re in, the attackers want to interrupt out of the primary compromised gadget and transfer laterally to different elements of the community to achieve their objectives.
The typical breakout time for interactive eCrime intrusion exercise dropped from 84 minutes to 62 minutes between 2022 and 2023, with the quickest breakout time being 2 minutes and seven seconds.
In an instance supplied by CrowdStrike, an attacker dropped reliable tooling 31 seconds after the login intrusion began to run a reconnaissance operation on the community and procure system data. Then, the attacker dropped extra information, with extra instruments being added inside 3 minutes, together with ransomware (Determine B).
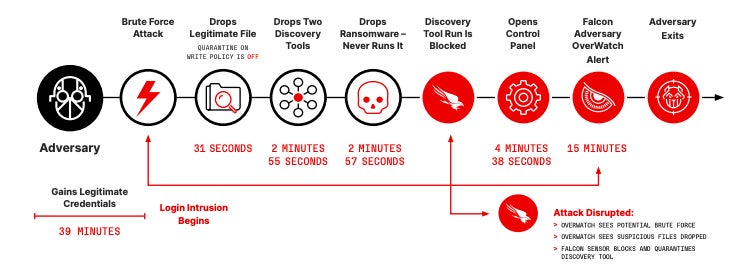
In accordance with the report, attackers additionally achieve time by utilizing much less malware and more practical means, reminiscent of utilizing stolen credentials and exploiting trusted relationships vulnerabilities. Malware-free actions now characterize 75% of all detections in 2023, as in comparison with 71% in 2022 and fewer than 62% earlier than 2021. The success of id assaults and the acquisition of legitimate credentials from preliminary entry brokers clarify this development of utilizing much less malware.
6. Attackers are focusing on periphery networks.
Because of the elevated use of endpoint detection and response sensors, risk actors have tailored their exploitation techniques for preliminary entry and lateral actions by focusing on the community periphery (Determine C).
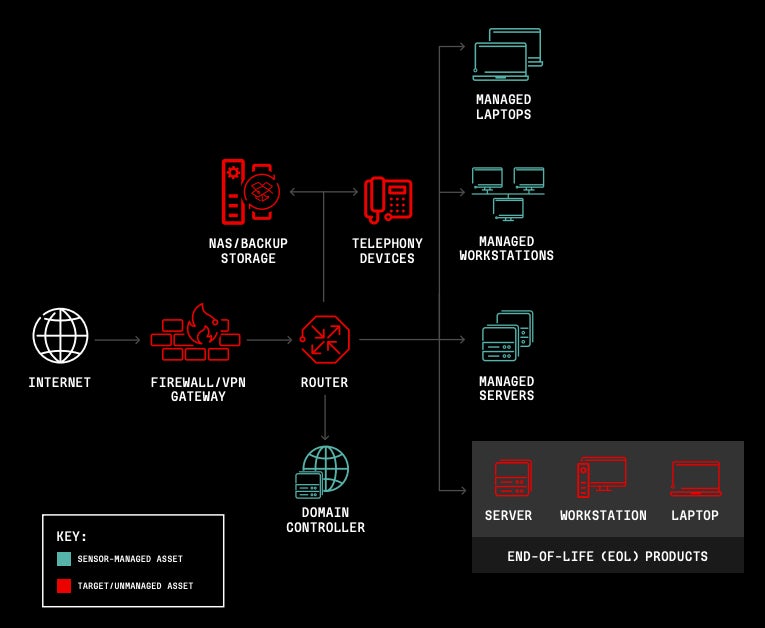
Some gadgets should not essentially monitored by safety options inside a company community. Specifically, edge gateway gadgets are sometimes based mostly on out of date structure and due to this fact weak to a number of vulnerabilities that could be exploited by attackers.
Vulnerabilities in firewalls and VPN platforms have, for instance, hit Cisco, Citrix and F5 in 2023. Routers, cellphones or NAS/backup storage may also be hit.
CrowdStrike highlighted one other development noticed in 2023: The attacker’s deal with Finish of Life product exploitation. These merchandise, which aren’t patched anymore and infrequently don’t enable trendy safety options deployment, are focused by attackers who actively develop exploits to abuse these merchandise.
SEE: Botnet Assault Focused Routers: A Wake-Up Name for Securing Distant Workers’ {Hardware}
Suggestions for mitigating these cybersecurity dangers
In accordance with CrowdStrike, it’s important to implement phishing-resistant MFA and prolong it to legacy and protocols, along with educating groups on social engineering.
Person consciousness applications needs to be initiated to know and battle phishing and social engineering strategies.
Expertise that may detect and correlate threats throughout id, endpoint and cloud environments have to be applied.
Cloud Native Utility Safety Platforms that embody pre-runtime safety, runtime safety and agentless expertise needs to be favored to remoted cloud safety instruments that don’t present a unified platform for monitoring and detecting potential threats and vulnerabilities.
Since attackers have a tendency to make use of much less malware and use legitimate credentials and bonafide instruments, it’s troublesome for defenders to distinguish between regular consumer and attacker exercise; an understanding of the relationships between id, cloud, endpoint and information safety telemetry is obligatory for that job. A consolidated safety platform offering full visibility in a single place have to be applied.
As well as, defenders ought to prioritize patching uncovered merchandise and eliminating EOL merchandise.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.
