Conventional perimeter-based safety has turn out to be expensive and ineffective. Consequently, communications safety between folks, programs, and networks is extra vital than blocking entry with firewalls. On high of that, most cybersecurity dangers are attributable to just some superusers – sometimes one out of 200 customers. There’s an organization aiming to repair the hole between conventional PAM and IdM options and safe your one out of 200 customers – SSH Communications Safety.
Your Privileged Entry Administration (PAM) and Identification Administration (IdM) ought to work hand in hand to safe your customers’ entry and identities – common customers and privileged customers alike. However conventional options wrestle to attain that.
Let us take a look at what organizations want to grasp about PAM and IdM and how one can bridge and future-proof your PAM and IdM.
PIM, PAM, IAM – you want all three of them
Privileged Identification Administration (PIM), Privileged Entry Administration (PAM), and Identification and Entry Administration (IAM) – all three are carefully related, and also you want all three of them to successfully handle and safe your digital identities, customers and entry.
Let’s rapidly assessment what PIM, PAM, and IAM concentrate on:
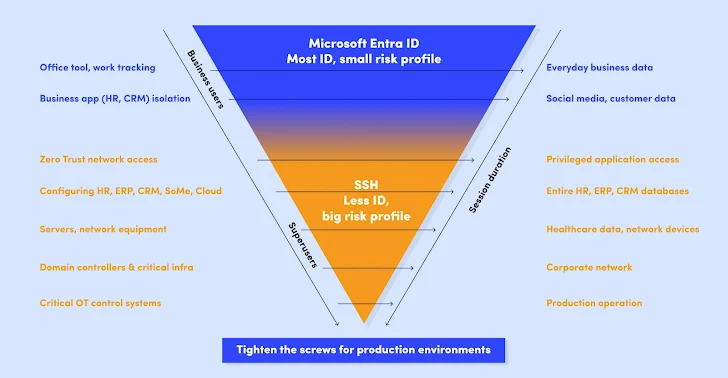
Not all digital identities are created equal – superusers want tremendous safety
Take into consideration this: Your typical consumer most likely wants entry to common workplace instruments, like your CRM or M365. They do not want entry to any of your vital property.
The id verification course of ought to correspond to this. A daily consumer must be verified with robust authentication strategies, e.g. Microsoft Entra ID, however there’s often no have to transcend that.
These typical customers type nearly all of your customers, as much as 99,5% of them.
However, you might have your privileged high-impact customers – there’s solely a small variety of them (sometimes round one in 200 customers), however the energy and dangers they carry are enormous as a result of they will entry your vital knowledge, databases, infrastructures, and networks.
Equally, applicable id verification procedures ought to apply. Within the case of your high-impact customers, you want entry controls that transcend robust identity-based authentication.
Enter the Zero Belief – Borderless, Passwordless, Keyless and Biometric Future
Conventional options aren’t sufficient to bridge your PAM and IdM. They only cannot deal with the safety that you want to shield your vital property. Nor can they provide efficient and future-proof safety controls for entry and identities of your typical customers in addition to high-impact customers.
The way forward for cybersecurity is borderless, passwordless, keyless, biometric, and Zero Belief.
Which means that you want a future-proof cybersecurity mannequin with no implicitly trusted customers, connections, functions, servers, or gadgets. On high of that, you want a further layer of safety with passwordless, keyless, and biometric authentication.
Study the significance of implementing the passwordless and keyless method into your cybersecurity from the whitepaper supplied by SSH Communications Safety.