The U.S. authorities is warning in regards to the resurgence of BlackCat (aka ALPHV) ransomware assaults focusing on the healthcare sector as just lately as this month.
“Since mid-December 2023, of the almost 70 leaked victims, the healthcare sector has been essentially the most generally victimized,” the federal government mentioned in an up to date advisory.
“That is possible in response to the ALPHV/BlackCat administrator’s submit encouraging its associates to focus on hospitals after operational motion towards the group and its infrastructure in early December 2023.”
The alert comes courtesy of the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Safety Company (CISA), and the Division of Well being and Human Companies (HHS).
The BlackCat ransomware operation suffered a significant blow late final 12 months after a coordinated legislation enforcement operation led to the seizure of its darkish leak websites. However the takedown turned out to be a failure after the group managed to regain management of the websites and switched to a brand new TOR information leak portal that continues to stay energetic so far.
It has additionally ramped up towards crucial infrastructure organizations in current weeks, having claimed accountability for assaults on Prudential Monetary, LoanDepot, Trans-Northern Pipelines, and UnitedHealth Group subsidiary Optum.
The event has prompted the U.S. authorities to announce monetary rewards of as much as $15 million for info resulting in the identification of key members in addition to associates of the e-crime group.
BlackCat’s ransomware spree coincides with the return of LockBit after related disruption efforts led by the U.Ok. Nationwide Crime Company (NCA) final week.
In accordance with a report from SC Journal, risk actors breached Optum’s community by leveraging the just lately disclosed crucial safety flaws in ConnectWise’s ScreenConnect distant desktop and entry software program.
The failings, which permit for distant code execution on inclined programs, have additionally been weaponized by the Black Basta and Bl00dy ransomware gangs in addition to by different risk actors to ship Cobalt Strike Beacons, XWorm, and even different distant administration instruments like Atera, Syncro, and one other ScreenConnect shopper.
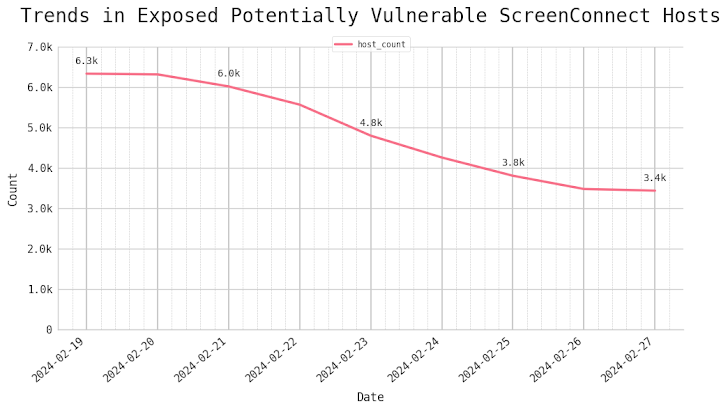
Assault floor administration agency Censys mentioned, as of February 27, 2024, it noticed a minimum of 3,400 uncovered probably weak ScreenConnect hosts on-line, with a majority of them situated within the U.S., Canada, the U.Ok., Australia, Germany, France, India, the Netherlands, Turkey, and Eire.
“It is clear that distant entry software program like ScreenConnect continues to be a chief goal for risk actors,” Censys safety researcher Himaja Motheram mentioned.
The findings come as ransomware teams like RansomHouse, Rhysida, and a Phobos variant referred to as Backmydata have continued to compromise numerous organizations within the U.S., U.Ok., Europe, and the Center East.
In an indication that these cybercrime teams are shifting to extra nuanced and complex ways, RansomHouse has developed a customized device dubbed MrAgent to deploy the file-encrypting malware at scale.
“MrAgent is a binary designed to run on [VMware ESXi] hypervisors, with the only goal of automating and monitoring the deployment of ransomware throughout giant environments with a excessive variety of hypervisor programs,” Trellix mentioned. Particulars of MrAgent first got here to mild in September 2023.
One other important tactic adopted by some ransomware teams is the sale of direct community entry as a brand new monetization technique through their very own blogs, on Telegram channels, or information leak web sites, KELA mentioned.
It additionally follows the general public launch of a Linux-specific, C-based ransomware risk referred to as Kryptina, which surfaced in December 2023 on underground boards and has since been made out there free of charge on BreachForums by its creator.
“The discharge of the RaaS supply code, full with in depth documentation, might have important implications for the unfold and influence of ransomware assaults towards Linux programs,” SentinelOne researcher Jim Walter mentioned.
“It’s more likely to improve the ransomware builder’s attractiveness and usefulness, drawing in but extra low-skilled individuals to the cybercrime ecosystem. There’s additionally important danger that it’ll result in the event of a number of spin-offs and a rise in assaults.”