Cybersecurity researchers have found a brand new Linux variant of a distant entry trojan (RAT) known as BIFROSE (aka Bifrost) that makes use of a misleading area mimicking VMware.
“This newest model of Bifrost goals to bypass safety measures and compromise focused programs,” Palo Alto Networks Unit 42 researchers Anmol Maurya and Siddharth Sharma mentioned.
BIFROSE is among the long-standing threats that has been lively since 2004. It has been supplied on the market in underground boards for as much as $10,000 prior to now, in keeping with a report from Pattern Micro in December 2015.
The malware has been put to make use of by a state-backed hacking group from China tracked as BlackTech (aka Circuit Panda, HUAPI, Manga Taurus, Palmerworm, PLEAD, Crimson Djinn, and Temp.Overboard), which has a historical past of putting organizations in Japan, Taiwan, and the U.S.
It is suspected that the menace actor bought the supply code or gained entry to it round 2010, and repurposed the malware to be used in its personal campaigns through customized backdoors like KIVARS and XBOW.
Linux variants of BIFROSE (aka ELF_BIFROSE) have been noticed since a minimum of 2020 with capabilities to launch distant shells, obtain/add information, and carry out file operations.
“Attackers sometimes distribute Bifrost by way of electronic mail attachments or malicious web sites,” the researchers mentioned. “As soon as put in on a sufferer’s laptop, Bifrost permits the attacker to assemble delicate info, just like the sufferer’s hostname and IP handle.”
What makes the most recent variant noteworthy is that it reaches out to a command-and-control (C2) server with the title “obtain.vmfare[.]com” in an try and masquerade as VMware. The misleading area is resolved by contacting a Taiwan-based public DNS resolver with the IP handle 168.95.1[.]1.
Unit 42 mentioned it detected a spike in Bifrost exercise since October 2023, figuring out at least 104 artifacts in its telemetry. It additional found an Arm model of the malware, suggesting the menace actors are doubtless trying to develop their assault floor.
“With new variants that make use of misleading area methods like typosquatting, a current spike in Bifrost exercise highlights the harmful nature of this malware,” the researchers mentioned.
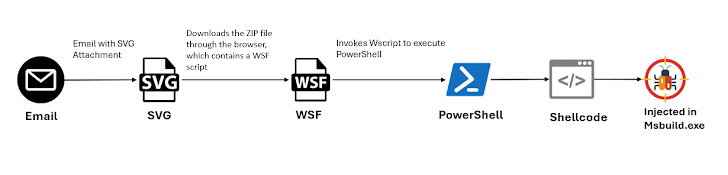
The event comes as McAfee Labs detailed a brand new GuLoader marketing campaign that propagates the malware by way of malicious SVG file attachments in electronic mail messages. The malware has additionally been noticed being distributed through VBS scripts as a part of a multi-stage payload supply.
“This current surge highlights its evolving techniques for broader attain and evasion,” Trustwave SpiderLabs mentioned in a submit on X earlier this week.
The Bifrost and GuLoader assaults coincide with the launch of a brand new model of the Warzone RAT, which not too long ago had two of its operators arrested and its infrastructure dismantled by the U.S. authorities.