Mexican customers have been focused with tax-themed phishing lures not less than since November 2023 to distribute a beforehand undocumented Home windows malware known as TimbreStealer.
Cisco Talos, which found the exercise, described the authors as expert and that the “risk actor has beforehand used comparable techniques, methods and procedures (TTPs) to distribute a banking trojan often known as Mispadu in September 2023.
Moreover using subtle obfuscation methods to sidestep detection and guarantee persistence, the phishing marketing campaign makes use of geofencing to single out customers in Mexico, returning an innocuous clean PDF file as an alternative of the malicious one if the payload websites are contacted from different areas.
Among the notable evasive maneuvers embrace leveraging customized loaders and direct system calls to bypass standard API monitoring, along with using Heaven’s Gate to execute 64-bit code inside a 32-bit course of, an method that was additionally just lately adopted by HijackLoader.
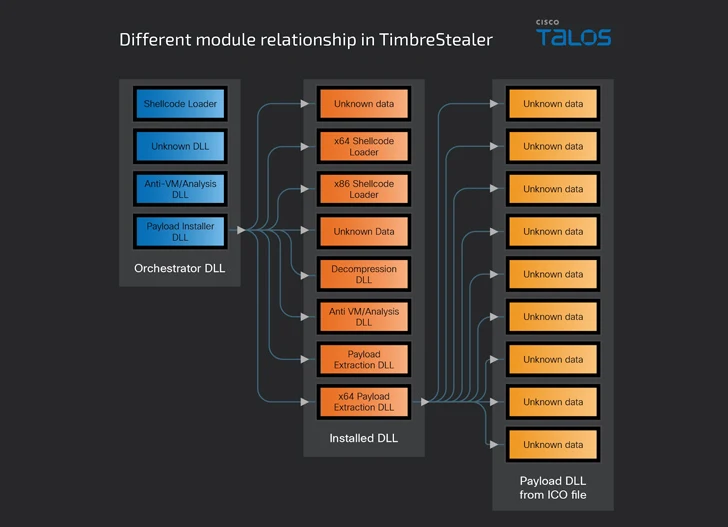
The malware comes with a number of embedded modules for orchestration, decryption, and safety of the principle binary, whereas additionally working a collection of checks to find out if it is working a sandbox setting, the system language is just not Russian, and the timezone is inside a Latin American area.
The orchestrator module additionally seems to be for information and registry keys to double-check that the machine hasn’t been beforehand contaminated, earlier than launching a payload installer element that shows a benign decoy file to the consumer, because it finally triggers the execution of TimbreStealer’s major payload.
The payload is designed to reap a variety of information, together with credential data from totally different folders, system metadata, and the URLs accessed, search for information matching particular extensions, and confirm the presence of distant desktop software program.
Cisco Talos stated it recognized overlaps with a Mispadu spam marketing campaign noticed in September 2023, though the goal industries of TimbreStealer are different and with a give attention to manufacturing and transportation sectors.
The disclosure comes amid the emergence of a brand new model of one other data stealer known as Atomic (aka AMOS), which is able to gathering information from Apple macOS methods equivalent to native consumer account passwords, credentials from Mozilla Firefox and Chromium-based browsers, crypto pockets data, and information of curiosity, utilizing an uncommon mixture of Python and Apple Script code.
“The brand new variant drops and makes use of a Python script to remain covert,” Bitdefender researcher Andrei Lapusneanu stated, noting the Apple Script block for accumulating delicate information from the sufferer’s pc reveals a “considerably excessive stage of similarity” with the RustDoor backdoor.
It additionally follows the emergence of recent stealer malware households equivalent to XSSLite, which was launched as a part of a malware growth competitors hosted by the XSS discussion board, at the same time as present strains like Agent Tesla and Pony (aka Fareit or Siplog) continued for use for data theft and subsequent sale on stealer logs marketplaces like Exodus.