The China-linked menace actor often called Evasive Panda orchestrated each watering gap and provide chain assaults concentrating on Tibetan customers at the least since September 2023.
The top of the assaults is to ship malicious downloaders for Home windows and macOS that deploy a identified backdoor referred to as MgBot and a beforehand undocumented Home windows implant often called Nightdoor.
The findings come from ESET, which stated the attackers compromised at the least three web sites to hold out watering-hole assaults in addition to a supply-chain compromise of a Tibetan software program firm. The operation was found in January 2024.
Evasive Panda, energetic since 2012 and often known as Bronze Highland and Daggerfly, was beforehand disclosed by the Slovak cybersecurity agency in April 2023 as having focused a global non-governmental group (NGO) in Mainland China with MgBot.
One other report from Broadcom-owned Symantec across the similar time implicated the adversary to a cyber espionage marketing campaign aimed toward infiltrating telecom providers suppliers in Africa at the least since November 2022.
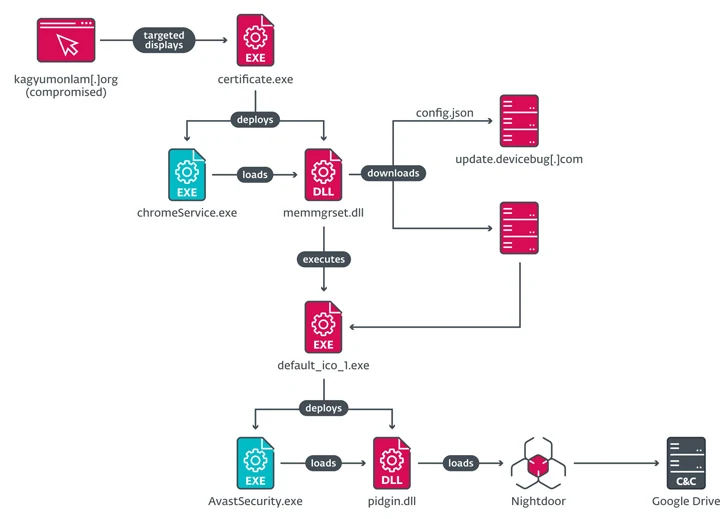
The newest set of cyber assaults entails the strategic internet compromise of the Kagyu Worldwide Monlam Belief’s web site (“www.kagyumonlam[.]org”).
“The attackers positioned a script within the web site that verifies the IP handle of the potential sufferer and whether it is inside one of many focused ranges of addresses, exhibits a pretend error web page to entice the person to obtain a ‘repair’ named certificates,” ESET researchers stated.
“This file is a malicious downloader that deploys the subsequent stage within the compromise chain.” The IP handle checks present that the assault is particularly designed to focus on customers in India, Taiwan, Hong Kong, Australia, and the U.S.
It is suspected that Evasive Panda capitalized on the annual Kagyu Monlam Pageant that befell in India in late January and February 2024 to focus on the Tibetan group in a number of nations and territories.
The executable – named “certificates.exe” on Home windows and “certificates.pkg” for macOS – serves as a launchpad for loading the Nightdoor implant, which, subsequently, abuses the Google Drive API for command-and-control (C2).
As well as, the marketing campaign is notable for infiltrating an Indian software program firm’s web site (“monlamit[.]com”) and provide chain in an effort to distribute trojanized Home windows and macOS installers of the Tibetan language translation software program. The compromise occurred in September 2023.
“The attackers additionally abused the identical web site and a Tibetan information web site referred to as Tibetpost – tibetpost[.]web – to host the payloads obtained by the malicious downloads, together with two full-featured backdoors for Home windows and an unknown variety of payloads for macOS,” the researchers famous.
The trojanized Home windows installer, for its half, triggers a complicated multi-stage assault sequence to both drop MgBot or Nightdoor, indicators of which have been detected as early as 2020.
The backdoor comes outfitted with options to collect system info, checklist of put in apps, and operating processes; spawn a reverse shell, carry out file operations, and uninstall itself from the contaminated system.
“The attackers fielded a number of downloaders, droppers, and backdoors, together with MgBot – which is used solely by Evasive Panda – and Nightdoor: the most recent main addition to the group’s toolkit and which has been used to focus on a number of networks in East Asia,” ESET stated.