Each Google Workspace administrator is aware of how shortly Google Drive turns into a messy sprawl of loosely shared confidential data. This is not anybody’s fault; it is inevitable as your productiveness suite is purposefully designed to allow real-time collaboration – each internally and externally.
For Safety & Threat Administration groups, the untenable threat of any Google Drive footprint lies within the poisonous combos of delicate information, extreme permissions, and improper sharing. Nevertheless, it may be difficult to distinguish between typical enterprise practices and potential dangers with out totally understanding the context and intent.
Materials Safety, an organization famend for its modern technique of defending delicate information inside worker mailboxes, has just lately launched Knowledge Safety for Google Drive to safeguard the sprawl of confidential data scattered all through Google Drive with a strong discovery and remediation toolkit.
How Materials Safety helps organizations safeguard Google Drive
Attempting to reply elementary questions on what’s in Google Drive and the place it is shared is painstakingly guide utilizing the Workspace admin dashboard, and dealing with the Drive API is expensive and complicated. Given the breadth of delicate content material, that is an space that warrants focus, but it surely’s difficult to get to the depth required.
Materials is backed by a strong information platform that syncs together with your Google Workspace tenant to construct out a structured mannequin of historic file contents, metadata, permissions, and sharing settings that’s stored up-to-date based mostly on ongoing exercise. This information platform allows in-depth inspection that would not be doable by interfacing with the Drive API alone. With this information platform as the muse, Materials:
- Scans file contents in opposition to a set of customized constructed ML-based detection guidelines to establish and classify delicate content material throughout a variety of PII, PCI, PHI, and different confidential information classes
- Calculates file and folder permission units and sharing settings to construct a unified entry mannequin that’s simpler to grasp and exhibit for compliance
- Permits automated entry revocation based mostly on exact search outcomes and exercise triggers to constantly cut back the danger profile
The precision of Materials permits you to successfully wrangle such a posh and huge information repository with out getting in the way in which of each day use – safety with out impacting productiveness. See it for your self.
Illuminate blind spots throughout your Google Drive footprint
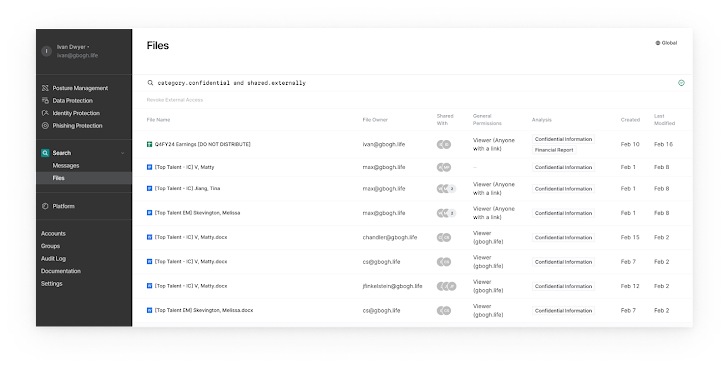
With a strong information platform as the muse, you achieve an expressive search interface that guides you thru your Google Drive footprint to establish poisonous combos worthy of investigation. You possibly can search in opposition to file metadata, possession, content material, location, and sharing to reply questions resembling:
- Present me each file that accommodates monetary information which are shared externally
- Present me each file viewable through a public hyperlink that accommodates PII
- Present me each file accessible by these customers who’re departing the corporate subsequent week
- Present me each file with confidential data that is shared with a gmail deal with
- Present me each file in a Shared Drive that accommodates well being information
As you illuminate extra of these harmful blind spots, you constantly achieve a extra full view of the surroundings with heightened safety posture – the kinds of issues that make it simpler to sleep at evening.
Block exfiltration paths with automated remediation
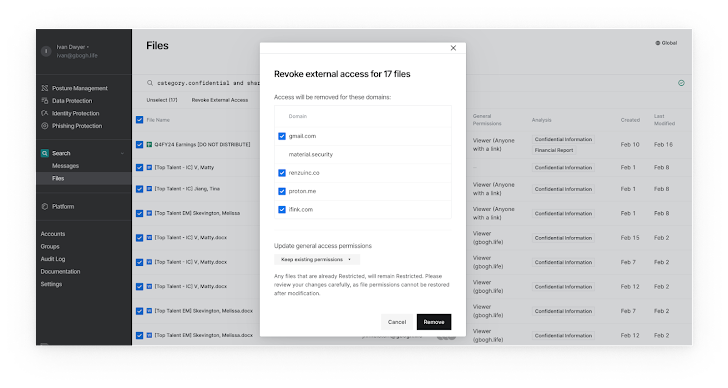
The first remediation mode to repair poisonous combos in Google Drive is to revoke entry. That sounds simple on the floor, however when you think about the situations of the entire house, it turns into a multi-dimensional puzzle. When is exterior sharing legitimate and when is it not? Are there customers that belong to teams that they should not? Which settings ought to change when a doc is modified so as to add confidential data?
Exact search and activity-based filtering allows remediation workflows for situations resembling:
- Robotically revoking public hyperlinks for any file that accommodates categorized data
- Sending customers a message to verify exterior sharing when information comprise any delicate information
- Chopping off entry to all information shared with particular exterior domains in a single bulk job
- Revoking all entry to a particular account that shows behaviors of a compromise
- Resetting any information accessible to the group that comprise private well being data to Restricted
Making use of automation typically can get in the way in which of day-to-day use, so it is essential to construct with precision – a greater understanding of the character of content material, which domains are trusted, and customary person behaviors provide help to comprise the floor space the proper manner.
Hold your productiveness suite productive with Materials Safety
At Materials, we focus our efforts on the productiveness suite as a result of we consider that it’s important infrastructure to any group. And as important infrastructure, in-depth safety defenses that may successfully cease assaults and cut back threat throughout the surroundings are paramount.
The brand new capabilities with Knowledge Safety for Google Drive remedy onerous information discovery, governance, and entry issues which have historically been difficult to do with out devoted tooling.
Wish to see it for your self? Schedule a private demo with our group at the moment.