A financially motivated risk actor known as Magnet Goblin is swiftly adopting one-day safety vulnerabilities into its arsenal so as to opportunistically breach edge gadgets and public-facing companies and deploy malware on compromised hosts.
“Menace actor group Magnet Goblin’s hallmark is its capability to swiftly leverage newly disclosed vulnerabilities, notably focusing on public-facing servers and edge gadgets,” Test Level mentioned.
“In some circumstances, the deployment of the exploits is inside 1 day after a [proof-of-concept] is revealed, considerably rising the risk degree posed by this actor.”
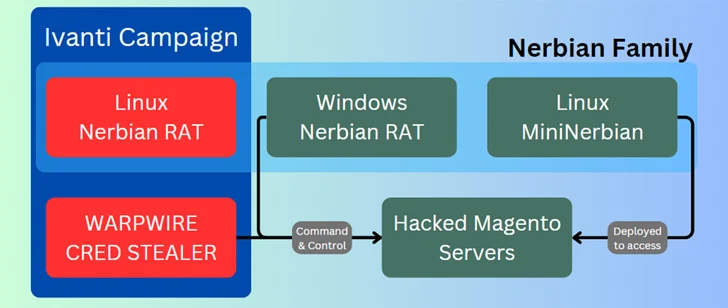
Assaults mounted by the adversary have leveraged unpatched Ivanti Join Safe VPN, Magento, Qlik Sense, and presumably Apache ActiveMQ servers as an preliminary an infection vector to realize unauthorized entry. The group is claimed to be energetic since at the least January 2022.
A profitable exploitation is adopted by the deployment of a cross-platform distant entry trojan (RAT) dubbed Nerbian RAT, which was first disclosed by Proofpoint in Could 2022, in addition to its simplified variant known as MiniNerbian. Using the Linux model of Nerbian RAT was beforehand highlighted by Darktrace.
Each the strains enable for execution of arbitrary instructions obtained from a command-and-control (C2) server and exfiltrating the outcomes backed to it.
A few of the different instruments utilized by Magnet Goblin embody the WARPWIRE JavaScript credential stealer, the Go-based tunneling software program referred to as Ligolo, and bonafide distant desktop choices equivalent to AnyDesk and ScreenConnect.
“Magnet Goblin, whose campaigns look like financially motivated, has been fast to undertake 1-day vulnerabilities to ship their customized Linux malware, Nerbian RAT and MiniNerbian,” the corporate mentioned.
“These instruments have operated beneath the radar as they principally reside on edge-devices. That is a part of an ongoing pattern for risk actors to focus on areas which till now have been left unprotected.”