A brand new elaborate assault marketing campaign has been noticed using PowerShell and VBScript malware to contaminate Home windows techniques and harvest delicate data.
Cybersecurity firm Securonix, which dubbed the marketing campaign DEEP#GOSU, stated it is seemingly related to the North Korean state-sponsored group tracked as Kimsuky.
“The malware payloads used within the DEEP#GOSU characterize a classy, multi-stage menace designed to function stealthily on Home windows techniques particularly from a network-monitoring standpoint,” safety researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov stated in a technical evaluation shared with The Hacker Information.
“Its capabilities included keylogging, clipboard monitoring, dynamic payload execution, and information exfiltration, and persistence utilizing each RAT software program for full distant entry, scheduled duties in addition to self-executing PowerShell scripts utilizing jobs.”
A notable side of the an infection process is that it leverages professional providers resembling Dropbox or Google Docs for command-and-control (C2), thus permitting the menace actor to mix undetected into common community site visitors.
On prime of that, the usage of such cloud providers to stage the payloads permits for updating the performance of the malware or delivering extra modules.
The start line is claimed to be a malicious electronic mail attachment containing a ZIP archive with a rogue shortcut file (.LNK) that masquerades as a PDF file (“IMG_20240214_0001.pdf.lnk”).
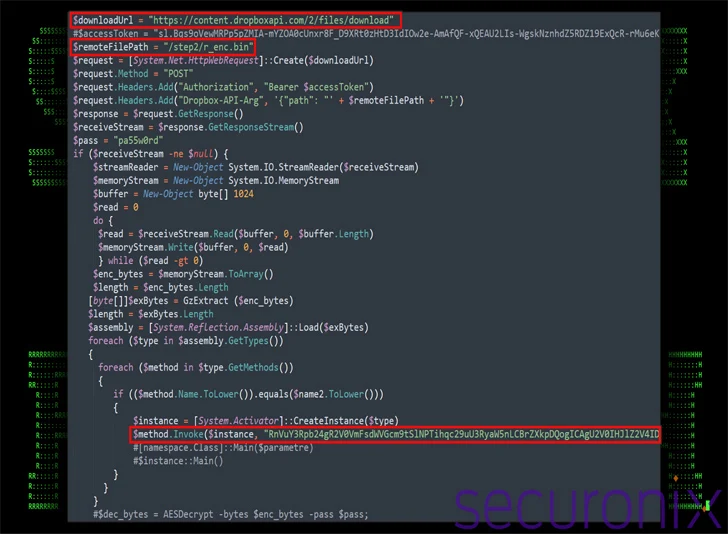
The .LNK file comes embedded with a PowerShell script in addition to a decoy PDF doc, with the previous additionally reaching out to an actor-controlled Dropbox infrastructure to retrieve and execute one other PowerShell script (“ps.bin”).
The second-stage PowerShell script, for its half, fetches a brand new file from Dropbox (“r_enc.bin”), a .NET meeting file in binary type that is really an open-source distant entry trojan often called TruRat (aka TutRat or C# RAT) with capabilities to document keystrokes, handle information, and facilitate distant management.
It is price noting that Kimsuky has employed TruRat in a minimum of two campaigns uncovered by the AhnLab Safety Intelligence Heart (ASEC) final yr.
Additionally retrieved by the PowerShell script from Dropbox is a VBScript (“info_sc.txt”), which, in flip, is designed to run arbitrary VBScript code retrieved from the cloud storage service, together with a PowerShell script (“w568232.ps12x”).
The VBScript can be designed to make use of Home windows Administration Instrumentation (WMI) to execute instructions on the system, and arrange scheduled duties on the system for persistence.
One other noteworthy side of the VBScript is the usage of Google Docs to dynamically retrieve configuration information for the Dropbox connection, permitting the menace actor to alter the account data with out having to change the script itself.
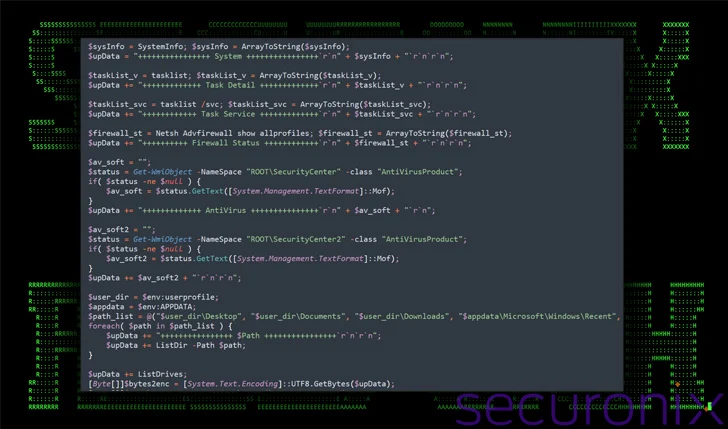
The PowerShell script downloaded in consequence is provided to assemble intensive details about the system and exfiltrate the main points by way of a POST request to Dropbox.
“The aim of this script seems to be designed to function a software for periodic communication with a command-and-control (C2) server by way of Dropbox,” the researchers stated. “Its foremost functions embody encrypting and exfiltrating or downloading information.”
In different phrases, it acts as a backdoor to manage the compromised hosts and constantly maintain a log of consumer exercise, together with keystrokes, clipboard content material, and the foreground window.
The event comes as safety researcher Ovi Liber detailed North Korea-linked ScarCruft’s embedding of malicious code inside Hangul Phrase Processor (HWP) lure paperwork current in phishing emails to distribute malware like RokRAT.
“The e-mail accommodates a HWP Doc which has an embedded OLE object within the type of a BAT script,” Liber stated. “As soon as the consumer clicks on the OLE object, the BAT script executes which in flip creates a PowerShell-based reflective DLL injection assault on the victims machine.”
It additionally follows Andariel’s exploitation of a professional distant desktop resolution known as MeshAgent to set up malware like AndarLoader and ModeLoader, a JavaScript malware meant for command execution.
“That is the primary confirmed use of a MeshAgent by the Andariel group,” ASEC stated. “The Andariel Group has been constantly abusing the asset administration options of home corporations to distribute malware within the technique of lateral motion, beginning with Innorix Agent prior to now.”
Andariel, additionally recognized by the names Nicket Hyatt or Silent Chollima, is a sub-cluster of the infamous Lazarus Group, actively orchestrating assaults for each cyber espionage and monetary achieve.
The prolific state-sponsored menace actor has since been noticed laundering a piece of the crypto property stolen from the hack of crypto change HTX and its cross-chain bridge (aka HECO Bridge) by means of Twister Money. The breach led to the theft of $112.5 million in cryptocurrency in November 2023.
“Following widespread crypto-laundering patterns, the stolen tokens had been instantly swapped for ETH, utilizing decentralized exchanges,” Elliptic stated. “The stolen funds then lay dormant till March 13, 2024, when the stolen crypto property started to be despatched by means of Twister Money.”
The blockchain analytics agency stated that Twister Money’s continuation of its operations regardless of sanctions have seemingly made it a beautiful proposition for the Lazarus Group to hide its transaction path following the shutdown of Sinbad in November 2023.
“The mixer operates by means of sensible contracts working on decentralized blockchains, so it can’t be seized and shut down in the identical manner that centralized mixers resembling Sinbad.io have been,” it famous.