
Ever surprise what malware can your Mac detect and take away with none third-party software program? Lately, safety researchers have correlated some weird macOS YARA guidelines utilized by the built-in XProtect suite with their public names. Right here’s what malware it seems for…
9to5Mac Safety Chew is completely delivered to you by Mosyle, the one Apple Unified Platform. Making Apple units work-ready and enterprise-safe is all we do. Our distinctive built-in method to administration and safety combines state-of-the-art Apple-specific safety options for absolutely automated Hardening & Compliance, Subsequent Era EDR, AI-powered Zero Belief, and unique Privilege Administration with probably the most highly effective and trendy Apple MDM available on the market. The result’s a completely automated Apple Unified Platform presently trusted by over 45,000 organizations to make tens of millions of Apple units work-ready with no effort and at an reasonably priced price. Request your EXTENDED TRIAL right now and perceive why Mosyle is every thing it’s worthwhile to work with Apple.

What’s XProtect?
XProtect was launched in 2009 as a part of macOS X 10.6 Snow Leopard. Initially, it was launched to detect and alert customers if malware was found in an putting in file. Nonetheless, over time, it has change into a collection of instruments as Apple continues to handle the rising downside of malware on its platform.
The XProtect suite makes use of YARA signature-based detection to establish and get rid of malware. YARA is a well-liked open-source software created by malware researchers, which works by figuring out malware based mostly on code similarities discovered in numerous malware households. Apple steadily provides to this pool with safety updates.
As of macOS 14 Sonoma, XProtect consists of three most important elements:
- XProtect detects malware utilizing YARA guidelines every time an app first launches, modifications, or updates its signatures.
- XProtectRemediator (XPR) can detect and take away malware by usually performing YARA scans during times of low exercise, which have minimal influence on the CPU.
- XProtectBehaviorService (XBS) was added with the newest model of macOS and displays system conduct in relation to important assets.
XProtectRemediator (XPR) presently consists of 23 scanning modules that execute virtually concurrently. Sadly, most have generic or inner naming schemes that don’t make a lot sense from the skin trying in.
“The remediator a part of XProtect has a collection of executables…every goal a selected malware household,” based on Alden, a malware researcher who just lately made vital developments by reverse engineering and figuring out 4 scanning modules, aka remediators.
“Some guidelines have significant names like XProtect_MACOS_PIRRIT_GEN, which is a sig for the Pirrit adware, whereas others are generic (XProtect_MACOS_2fc5997) or inner to Apple (XProtect_snowdrift).” Alden goes into extra element on their Github.
Whereas that is carried out for good cause, it may be difficult for these curious to know exactly what malware XPR is in search of.
How do I discover XProtect?
XProtect is enabled by default in each model of macOS. It additionally runs on the system degree, fully within the background, so no intervention is required. However right here’s the place it’s positioned:
- In Macintosh HD, go to Library > Apple > System > Library > CoreServices
- From right here, you could find remediators by right-clicking on XProtect
- Then click on Present Package deal Contents
- Develop Contents > Sources
- Open MacOS
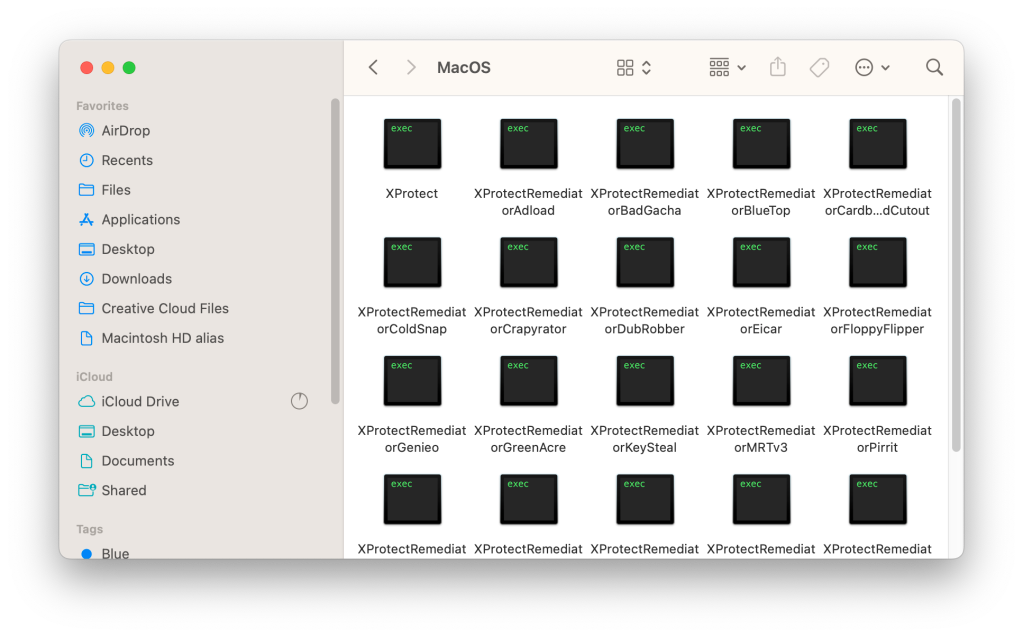
Utilizing Alden’s new and current findings, The Eclectic Gentle Firm shared a listing of the 14 out of 23 scanning modules within the present model of XPR and the way they correlate with their public malware names. Listed here are a number of:
- Adload is an previous adware and bundleware loader relationship again to 2016 that has a observe document of speedy change, enabling it to evade static detection. It usually achieves persistence by way of a bogus service put in in ~/Library/LaunchAgents/, and Phil Stokes provides fuller particulars right here.
- BadGacha stays unidentified, however steadily reviews false positives for helper apps in non-malicious apps.
- BlueTop is a bogus WindowServer app that was a part of a Trojan-Proxy marketing campaign investigated by Kaspersky in late 2023.
- ColdSnap is understood higher as SimpleTea, a cross-platform element that was a part of the 3CX supply-chain assault.
- Crapyrator has been recognized as BkDr.Activator, discovered in lots of torrents of cracked apps corresponding to MarsEdit, DaisyDisk, and SpamSieve. It makes use of subtle strategies, characteristically putting in Activator.app in the primary Purposes folder, prompts for a password and makes use of that to disable Gatekeeper checks, then kills Notification Centre to cowl its tracks. Additional particulars are given right here.
- DubRobber is understood extra usually as XCSSET, a flexible and troubling Trojan dropper that modifications steadily to flee detection.
- Eicar isn’t malware in any respect, however an ordinary non-malicious take a look at of detection strategies.
I extremely advocate taking a look at The Eclectic Gentle Firm’s full record. It’s eye-opening to see a number of the safety processes that Apple has integrated. That stated, customers shouldn’t rely completely on Apple’s XProtect suite, because it’s made to detect recognized threats. Extra superior or subtle assaults may simply circumvent detection. Proceed to make use of third-party antivirus software program.
About Safety Chew: Safety Chew is a weekly security-focused column on 9to5Mac. Each week, Arin Waichulis delivers insights on information privateness, uncovers vulnerabilities, and sheds gentle on rising threats inside Apple’s huge ecosystem of over 2 billion lively machines. Keep safe, keep secure.
FTC: We use earnings incomes auto affiliate hyperlinks. Extra.

