Distant Desktop Protocol (RDP) was developed by Microsoft to permit customers, directors, and others to hook up with distant computer systems over a community connection utilizing a useful graphical consumer interface (GUI). The instruments required for this come as customary on Microsoft Home windows; to provoke and arrange an RDP connection, all of the instruments required to try this are current by default. Because of this RDP is used extensively all through networks by customers and directors to entry distant machines.
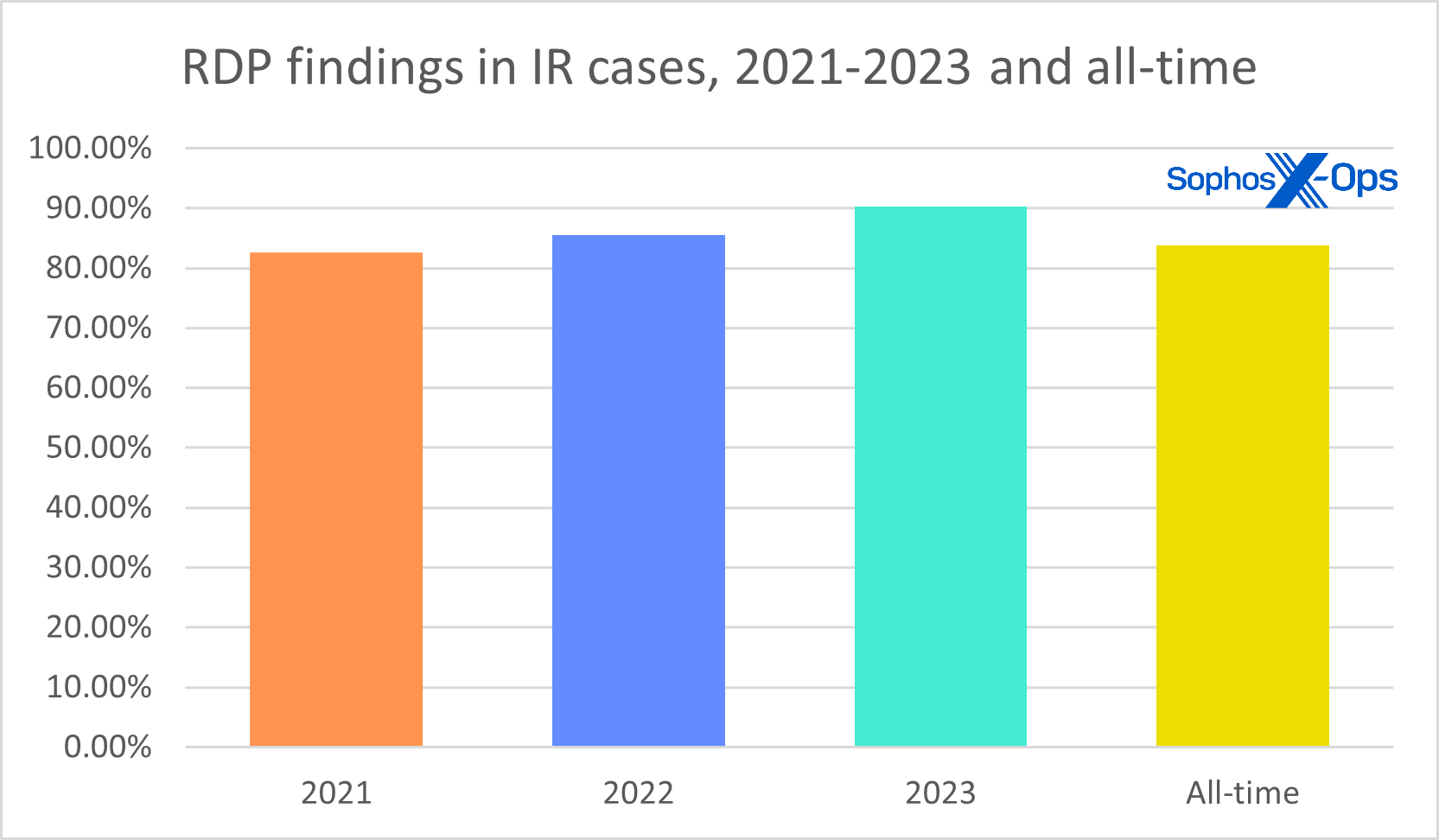
Sadly, it’s additionally generally abused by ransomware teams – so generally, actually, that in our common Energetic Adversary Studies our editors are pressured to deal with RDP in a different way in graphics so different findings are even seen. And RDP abuse is on the rise, as we see in Determine 1 — numbers from the previous few years of incident-response information as collected by the Energetic Adversary Report staff. Within the version of the report we’ll be releasing subsequent month, you’ll see that RDP has now cracked the 90 p.c mark – that’s, 9 out of ten IR circumstances embody RDP abuse.
Determine 1: A primary have a look at the total Energetic Adversary dataset from 2023 exhibits that RDP abuse is getting worse
Right now, to supply context and recommendation for directors and responders trying to cope with RDP, we’re publishing a complete bundle of sources – movies, companion articles with extra info, and a constellation of extra scripts and knowledge on our GitHub repository. We’re doing this each to share our Energetic Adversary staff’s analysis past the standard long-form stories we problem, and to supply what we hope is a helpful set of sources for dealing with one in all infosec’s extra annoying power illnesses.
From an attacker’s viewpoint, focusing on RDP is a pure selection. Most importantly, it’s a Microsoft-provided software (so, a living-off-the-land binary, or LOLBin) that blends in with typical consumer and administrative habits. Its utilization alone isn’t apt to attract consideration if nobody’s conserving an eye fixed out for it, and an attacker needn’t usher in extra instruments that could be detected by EDR or different anti-intrusion instruments. RDP additionally has a comparatively nice graphical consumer interface that lowers the ability barrier for attackers to browse information for exfiltration, and to put in and use varied functions.
Attackers additionally know that RDP is often misconfigured or misused inside an surroundings, each on servers and sometimes on endpoints themselves. The following article on this RDP assortment seems to be at simply how widespread such publicity is, and whether or not measures equivalent to switching off RDP’s ordinary 3389 port makes a distinction. (Spoiler: No.)
Rounding out the dismal RDP image, we see self-owns equivalent to lack of segregation, use of weak credentials, disabling (by directors) of potential protections equivalent to NLA (network-level authentication), and flagrant disregard for finest practices equivalent to least privilege. On the brighter aspect, there are helpful, sturdy queries that can provide nice perception into exactly how RDP is in use in your community… if you realize the place to look.
So, to supply context and recommendation for directors and responders trying to cope with RDP, we’re beginning with a complete bundle of sources – six movies, six companion articles with extra info, and a constellation of extra scripts and knowledge on our GitHub – with extra to be added over time as occasions dictate.
Distant Desktop Protocol: The Sequence
Half 1: Distant Desktop Protocol: Introduction ([you are here], video)
Half 2: Distant Desktop Protocol: Uncovered RDP (is harmful) (publish, video)
Half 3: RDP: Queries for Investigation (publish, video)
Half 4: RDP Time Zone Bias (publish, video)
Half 5: Executing the Exterior RDP Question (publish, video)
Half 6: Executing the 4624_4625 Login Question (publish, video)
GitHub question repository: SophosRapidResponse/OSQuery
Transcript repository: sophoslabs/video-transcripts
YouTube playlist: Distant Desktop Protocol: The Sequence