The 4624_4625 login occasions question offers defenders, particularly analysts, with a useful gizmo for each figuring out profitable RDP logins (Home windows Safety Log Occasion 4624) and failed makes an attempt (Home windows Safety Log Occasion 4625). These occasions could be generated by techniques, area controllers, and workstations.
These Home windows occasions are seen in Occasion Viewer, in fact, however on this submit (and within the companion video we’ve placed on our YouTube channel) we’ll reveal our evaluation utilizing Sophos Central. The SQL question we’ll use under is out there to all on our Github.
Constructing and executing the question
The SQL question we’ll be working with seems to be like this:
SELECT
strftime('%Y-%m-%dTpercentH:%M:%SZ',datetime) AS date_time,
eventid AS EventID,
CASE
WHEN eventid = 4624 THEN eventid || ' - Profitable Login'
WHEN eventid = 4625 THEN eventid || ' - Failed login'
END AS Description,
'Safety' AS Supply,
JSON_EXTRACT(information, '$.EventData.TargetUserName') AS Target_User,
JSON_EXTRACT(information, '$.EventData.WorkstationName') AS Source_Machine_Network,
JSON_EXTRACT(information, '$.EventData.IpAddress') AS Source_IP,
JSON_EXTRACT(information, '$.EventData.ProcessName') AS Process_Name,
JSON_EXTRACT(information, '$.EventData.LogonType') AS Logon_Type,
JSON_EXTRACT(information, '$.EventData.TargetUserSid') AS Target_User_SID,
JSON_EXTRACT(information, '$.EventData.Standing') AS Logon_Status_Code,
JSON_EXTRACT(information, '$.EventData.TargetDomainName') AS Target_Domain_Name,
JSON_EXTRACT(information, '$.EventData.AuthenticationPackageName') AS Authentication_package,
NULL AS SessionID,
NULL AS Session_ID,
'Safety EVTX' AS Data_Source,
'Logins.01.1' AS Question
FROM sophos_windows_events
WHERE supply="Safety"
AND (eventid = 4624 OR eventid = 4625)
AND JSON_EXTRACT(information, '$.EventData.TargetUserName') LIKE '$$username$$'
AND JSON_EXTRACT(information, '$.EventData.IpAddress') LIKE '$$source_ip$$'
AND JSON_EXTRACT(information, '$.EventData.WorkstationName') LIKE '$$workstation$$'
AND time > 0
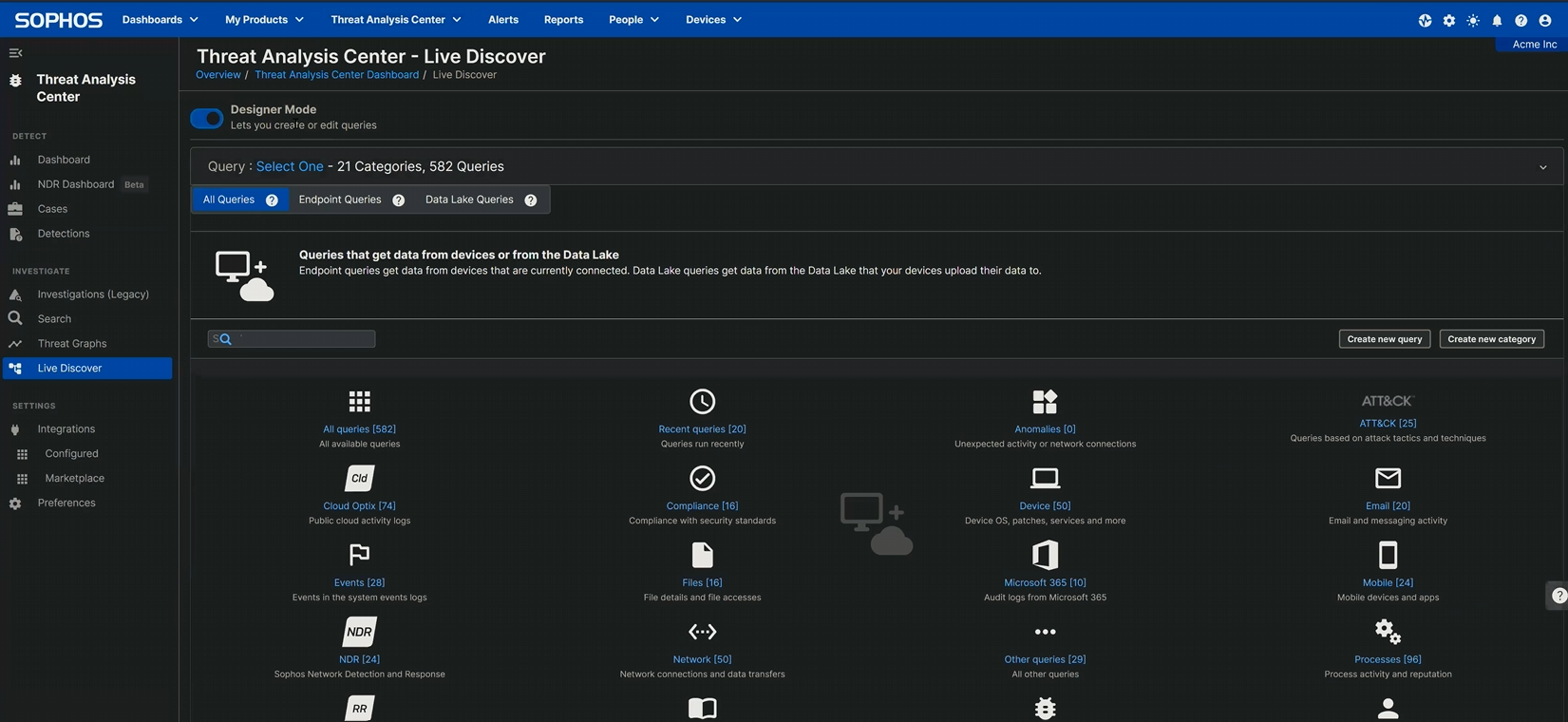
To execute this in Sophos Central, navigate to
Risk Evaluation Middle > Dwell Uncover > Designer Mode
and click on the Create new question button, as proven in Determine 1.
Determine 1: Creating a question on the Designer Mode display; the Create new question button is on the appropriate close to the center of the display
Clicking the button results in a display with a SQL field, into which you’ll paste the question.
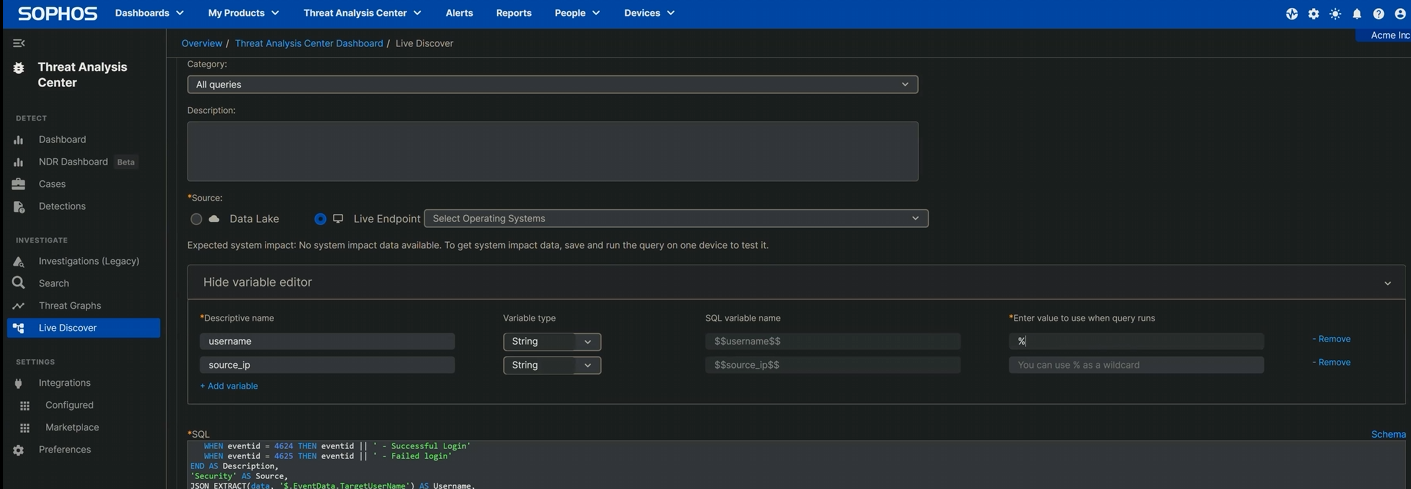
Word that this question has two variables – one for the focused username(s) (username) and one for the IP deal with of the entity trying entry (source_ip). Each of those are strings; to make sure the question returns the best potential variety of outcomes, these ought to embrace wildcards for these variables. (When our Incident Response investigators use this in the middle of their work, as a rule they run it in opposition to each Home windows gadget on the community; the primary time you run it and infrequently thereafter, think about doing the identical to get the broadest potential view of what’s taking place in your community.)
To do this, edit these two variables within the Variable Editor simply above the field into which the question is pasted. Click on Present Variable Editor, then click on + Add variable. Within the Descriptive title discipline, sort the primary variable title (username); the sort (String) and SQL variable title ($$username$$) will auto-populate. On the following line, do the identical for the second variable ($$source_ip$$). On the appropriate, add the proportion signal (%) that signifies a wildcard, as proven in Determine 2:
Determine 2: The variable modifying is almost full – another share signal and it’s prepared
Subsequent, scroll right down to the Filters space and choose the machines on which the question ought to run. (Since this can be a Home windows occasion, there’s no level operating it on any macOS or Linux machines in your property, so these ought to be filtered out.) Clicking the tickbox subsequent to “On-line standing” (on the prime of the column) selects all; click on “Replace chosen units checklist” to substantiate.
As soon as the variables and filters are set, click on Run Question, and click on it once more when the system asks if you wish to run this untested question. The execution begins; the time to completion will in fact depend upon the dimensions of your property, your connection velocity, and above all how massive the occasion log is. Nevertheless, it’ll finally conclude, returning a desk of outcomes. It’s in fact potential to overview these proper in Sophos Central, however it’s additionally potential (and maybe a bit extra nice) to export the entire thing to a CSV file for perusal in your most well-liked spreadsheet editor.
Understanding the outcomes
Nevertheless you favor to view the returned outcomes, just a few fields stand out:
| Question Outcomes: An summary | |
| epName | Endpoint title |
| date_time | The UTC-format time at which the occasion was recorded within the queried log; sorting on date_time can pinpoint bursts of exercise at sudden instances |
| EventID | Both the connection succeeded (4624) or it failed (4625) |
| Supply | The log by which these question outcomes had been discovered |
| Username | The username provided when the connection was tried; price checking for customers that shouldn’t be making RDP makes an attempt, in addition to for usernames that don’t suit your group’s “model” (eg., in case your org calls the system administration accounts “Administrator,” seeing “ADMINISTRATOR,” “admin,” or the like ought to get your consideration) |
| Source_Machine_Network | The true title of the host that linked (or tried to attach); a reputation you don’t acknowledge or that doesn’t match the group’s naming schema might be price investigating additional |
| Source_IP | The originating IP deal with; if it’s not coming from contained in the property (that’s, if it’s a non-RFC 1819 connection, a distant IP deal with), it bears scrutiny |
| Logon_Type | Microsoft assigns a dozen codes to several types of logins; on this state of affairs, investigators taking a look at RDP abuse might word sort 3 (community, together with post-NLA, logins), sort 7 (the workstation was unlocked; if the IP discipline related to this occasion is a distant deal with, that’s suspicious), or sort 10 (distant login utilizing Terminal Servies or, sure, RDP) |
Within the desk above, we’ve famous numerous potential grounds for additional investigation primarily based on the outcomes this question returns; right here’s another. Although this question can spot potential RDP publicity points, it could spot one thing else that wants your immediate consideration — as an example, SMB.
There may be, within the 12 months 2024 (a full seven years since EternalBlue and WannaCry dropped), no good purpose to go away a shared folder or drive hanging out on the web on this trend – and but one in 5 of the circumstances dealt with in 2022 and 2023 by the Incident Response crew had proof of SMB abuse. That statistic doesn’t maintain a candle to RDP’s cursed dominance in our IR findings, the place over 90 % of the circumstances embrace RDP-related findings, however it’s a great reminder that maintaining a tally of your group’s logs with recurrently run queries comparable to this may return some eye-opening outcomes certainly.
Distant Desktop Protocol: The Collection
Half 1: Distant Desktop Protocol: Introduction (submit, video)
Half 2: Distant Desktop Protocol: Uncovered RDP (is harmful) (submit, video)
Half 3: RDP: Queries for Investigation (submit, video)
Half 4: RDP Time Zone Bias (submit, video)
Half 5: Executing the Exterior RDP Question (submit, video)
Half 6: Executing the 4624_4625 Login Question ([you are here], video)
GitHub question repository: SophosRapidResponse/OSQuery
Transcript repository: sophoslabs/video-transcripts
YouTube playlist: Distant Desktop Protocol: The Collection