Most defenders are conversant in discover and search for suspicious RDP lateral motion, whether or not which means wanting based mostly on known-compromised customers or on an alert from antimalware or EDR protections related to a particular person. You’re beginning to pivot from the preliminary discover that one thing’s unsuitable; now what?
Analyzing the logs to examine account-activity timestamps is a typical method to spot odd conduct – for instance, James-from-the-head-office connecting to a website controller at 3 a.m., when he usually solely accesses the Sage servers, and people solely throughout enterprise hours. Nevertheless, there’s extra to learn about logins – not simply when the exercise occurred, however the time zone from which the exercise originated. This is named the bias, and it’s captured on trendy (Home windows 10 / Server 2016 and later) variations of Microsoft’s working system. Occasion ID 104 is out there within the Microsoft Home windows Distant Desktop Providers RDP Core TS Operational occasion log.
What does the defender see?
As one would possibly anticipate from the title, this occasion logs the time-zone bias from UTC of the machine making the connection. Because you in all probability already know the time zone(s) your customers would usually be logging in from, seeing deviations from that zone may also help you establish suspicious RDP connections, just because they’re not coming from the a part of the planet they need to be.
Taking James as our instance once more, let’s say James relies in London and that you simply’re investigating suspicious exercise within the early months of the yr. In January or February, the time-zone bias for James can be zero hours UTC, so if James is utilizing RDP to hook up with the community for no matter motive, the shopper time bias you need to see on his logins is [0]. If, abruptly, you begin seeing shopper time zone biases of [-8], or [6], or different values that differ from the norm for James, that might allow you to spot probably suspicious RDP connections, or at minimal extra questions price asking. (Is he touring? Was his machine stolen?)
Let’s take an instance the place a person’s credentials have been phished, the attacker’s logged into the VPN — since you don’t have MFA enabled, although you understand you need to — and so they begin accessing units utilizing RDP. You’d then begin to see the time zone of that attacker machine for these entry occasions.
There’s no single question that magically delivers each reply, and this one’s no exception. As an illustration, attackers usually host their machines hosted on numerous machines, situated in numerous time zones through which they might or might not be bodily situated. Nonetheless, they’re prone to differ from the conventional time zones for your customers.
One other potential weak point lies in false positives; in case your group operates in a means that makes it exhausting to discern what a “regular” time zone appears like, it could be more durable so that you can pinpoint the distinction between sign and noise. Lastly, false negatives are a risk; the occasion data the time zone on the attacker’s machine, so the attacker can undermine this information by altering the time zone on that machine. That stated, Occasion 104 is a useful occasion to maintain watch over – yet one more instrument in your protection toolkit.
Timezone bias and Dwell Uncover
Occasion 104 is after all accessible to anybody analyzing Microsoft techniques of the supported vintages (once more, Home windows 10 / Server 2016 and later). The data within the closing part of this publish is supplied for these readers utilizing Sophos’ Dwell Uncover to get the job performed. (Nevertheless, we’ll publish the question we’re about to debate on our Github, the place anybody can choose up a duplicate.) We additionally exhibit this question and its outcomes on our YouTube channel.
To execute an OS question and return timezone bias data in Dwell Uncover, use the next:
SELECT strftime('%Y-%m-%dTpercentH:%M:%SZ',datetime) AS Datetime, supply, eventid, JSON_EXTRACT(information, '$.EventData.TimezoneBiasHour') AS TimezoneBiasHour FROM sophos_windows_events WHERE supply="Microsoft-Home windows-RemoteDesktopServices-RdpCoreTS/Operational" AND eventid IN (104)
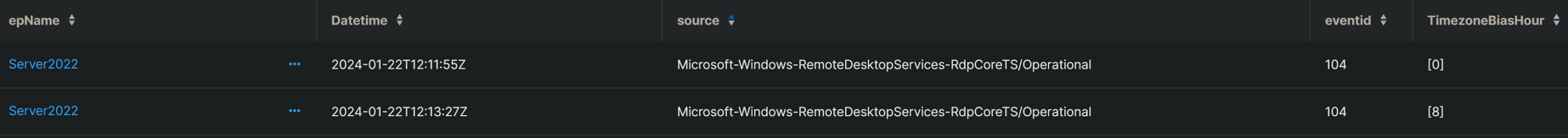
The output of the question appears just like the outcomes proven in Determine 1:
Determine 1: Both the person has found a method to teleport themself and their pc throughout eight time zones in 90 seconds, or one thing is unsuitable right here
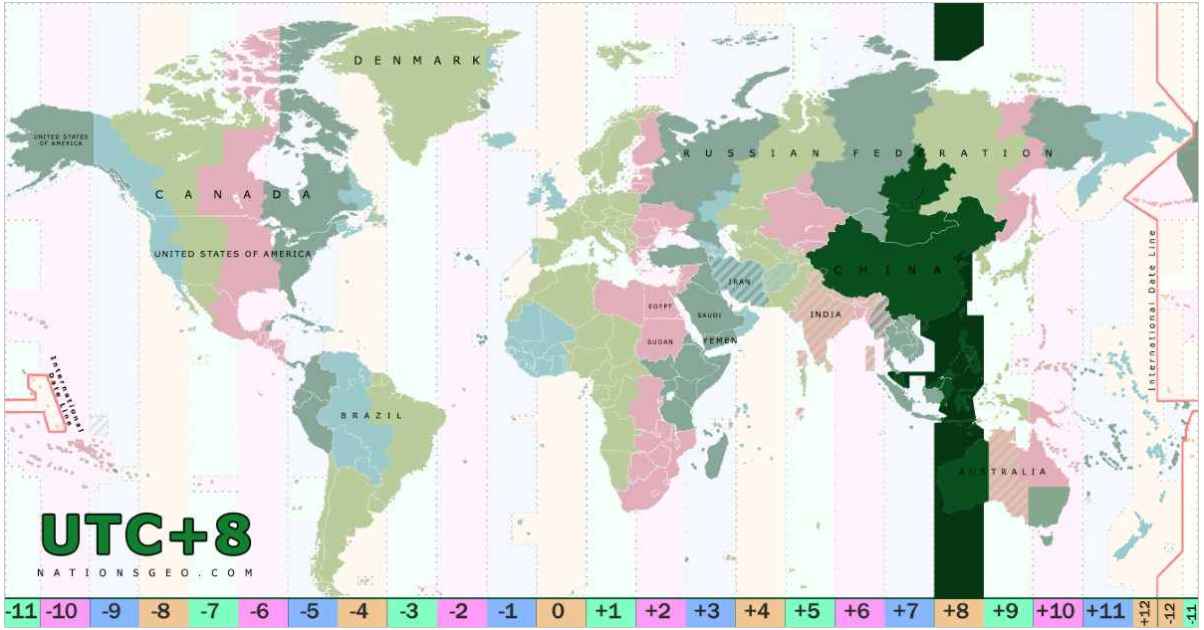
On the left within the picture above, we’ve the endpoint title – the identical for each entries on this two-event log. We see the date/time data in UTC, which exhibits that the 2 occasions occurred a few minute and a half aside. The supply is the place we discovered this occasion, which is proven as 104 within the subsequent column. And on the precise, we see the end result – the primary occasion originating in UTC 0, the second UTC +8, which is the realm indicated within the map in Determine 2.
Determine 2: UTC +8 is a captivating slice of the planet, nevertheless it’s positively not close to James in London. (Map picture courtesy nationsgeo.com)
We suggest executing this question throughout all units inside your atmosphere – go searching and establish if there are timezone bias entries within the RDP Core TS Operational occasion log that differ from what you’d usually anticipate.
Distant Desktop Protocol: The Collection
Half 1: Distant Desktop Protocol: Introduction (publish, video)
Half 2: Distant Desktop Protocol: Uncovered RDP (is harmful) (publish, video)
Half 3: RDP: Queries for Investigation (publish, video)
Half 4: RDP Time Zone Bias ([you are here], video)
Half 5: Executing the Exterior RDP Question (publish, video)
Half 6: Executing the 4624_4625 Login Question (publish, video)
GitHub question repository: SophosRapidResponse/OSQuery
Transcript repository: sophoslabs/video-transcripts
YouTube playlist: Distant Desktop Protocol: The Collection