The operate of the RDP Logins from Exterior IPs.sql question is pretty self-explanatory, primarily based on the title. On this submit, we’ll use it to search for profitable RDP connections which have taken place from exterior IP addresses – that’s, something that’s non-RFC 1918. For the sake of this demonstration, we’ll do the work of constructing and executing the question itself via our personal Sophos Central service, however the fundamentals maintain true irrespective of the investigation device. In its place, the “Executing the Exterior RDP Question” video linked beneath reveals the related steps, reasonably than describing them as we do right here.
Constructing and executing the question
Step one is to create the question, which in Sophos Central you’ll do in
Risk Evaluation Heart > Dwell Uncover > Designer Mode
by clicking the Create new question button, as proven in Determine 1.
Determine 1: Navigating to the query-creation button
Clicking the button results in a display with a SQL field, into which you’ll paste the next question (additionally accessible on our Github):
SELECT strftime('%Y-%m-%dTpercentH:%M:%SZ',datetime) AS date_time, eventid, CASE eventid WHEN 21 THEN eventid || ' - Session logon succeeded' WHEN 22 THEN eventid || ' - Shell begin notification acquired' WHEN 25 THEN eventid || ' - Session reconnection profitable' ELSE NULL END AS description, JSON_EXTRACT(knowledge, '$.UserData.Consumer') AS username, SUBSTR(JSON_EXTRACT(knowledge, '$.UserData.Consumer'), 1, INSTR(JSON_EXTRACT(knowledge, '$.UserData.Consumer'), '') - 1) AS area, JSON_EXTRACT(knowledge, '$.UserData.Tackle') AS source_IP, JSON_EXTRACT(knowledge, '$.UserData.SessionID') AS session_ID, CASE WHEN JSON_EXTRACT(knowledge, '$.UserData.Tackle') GLOB '*[a-zA-Z]*' THEN 'private_IP' WHEN INSTR(JSON_EXTRACT(knowledge, '$.UserData.Tackle'), '192.168.') = 1 THEN 'private_IP' WHEN INSTR(JSON_EXTRACT(knowledge, '$.UserData.Tackle'), '172.') = 1 AND CAST(SUBSTR(JSON_EXTRACT(knowledge, '$.UserData.Tackle'), 5, 2) AS INTEGER) BETWEEN 16 AND 31 THEN 'private_IP' WHEN INSTR(JSON_EXTRACT(knowledge, '$.UserData.Tackle'), '10.') = 1 THEN 'private_IP' WHEN INSTR(JSON_EXTRACT(knowledge, '$.UserData.Tackle'), '127.') = 1 THEN 'private_IP' WHEN JSON_EXTRACT(knowledge, '$.UserData.Tackle') = '0.0.0.0' THEN 'private_IP' WHEN JSON_EXTRACT(knowledge, '$.UserData.Tackle') LIKE '%::%' THEN 'unknown' WHEN JSON_EXTRACT(knowledge, '$.UserData.Tackle') = '' THEN 'private_IP' ELSE 'external_IP' END AS standing, 'TS LocalSession EVTX' AS data_source, 'Logins.01.4' AS question FROM sophos_windows_events WHERE supply="Microsoft-Home windows-TerminalServices-LocalSessionManager/Operational" AND eventid IN (21,22,25) AND (standing="external_IP" OR standing="unknown") UNION ALL SELECT strftime('%Y-%m-%dTpercentH:%M:%SZ',datetime) AS date_time, eventid, CASE eventid WHEN 1149 THEN eventid || ' - Consumer authentication succeeded' ELSE NULL END AS description, JSON_EXTRACT(knowledge, '$.UserData.Param1') AS username, JSON_EXTRACT(knowledge, '$.UserData.Param2') AS area, JSON_EXTRACT(knowledge, '$.UserData.Param3') AS source_IP, NULL AS Session_ID, CASE WHEN INSTR(JSON_EXTRACT(knowledge, '$.UserData.Param3'), '192.168.') = 1 THEN 'private_IP' WHEN INSTR(JSON_EXTRACT(knowledge, '$.UserData.Param3'), '172.') = 1 AND CAST(SUBSTR(JSON_EXTRACT(knowledge, '$.UserData.Param3'), 5, 2) AS INTEGER) BETWEEN 16 AND 31 THEN 'private_IP' WHEN INSTR(JSON_EXTRACT(knowledge, '$.UserData.Param3'), '10.') = 1 THEN 'private_IP' WHEN INSTR(JSON_EXTRACT(knowledge, '$.UserData.Param3'), '127.') = 1 THEN 'private_IP' WHEN JSON_EXTRACT(knowledge, '$.UserData.Param3') = '0.0.0.0' THEN 'private_IP' WHEN JSON_EXTRACT(knowledge, '$.UserData.Param3') LIKE '%::%' THEN 'unknown' WHEN JSON_EXTRACT(knowledge, '$.UserData.Param3') = '' THEN 'private_IP' ELSE 'external_IP' END AS standing, 'TS RemoteConnection EVTX' AS data_source, 'Logins.01.4' AS question FROM sophos_windows_events WHERE supply="Microsoft-Home windows-TerminalServices-RemoteConnectionManager/Operational" AND eventid = 1149 AND (standing="external_IP" OR standing="unknown")
As soon as that’s pasted in, you’ll choose the machines towards which this question ought to run. The question is Home windows-specific; working it towards macOS or Linux machines will return no outcomes, so deselecting these (beneath the Filters –> Working system choice) is an efficient first step. Past that, the wants of every enterprise are distinctive. Nevertheless, there’s a robust case to be made to run the question towards each Home windows machine in your community – even the endpoints, simply in case one’s incorrectly uncovered to the web. (Alas, our Incident Response investigators discover this much more usually than one would count on.)
Click on Replace Chosen Units to substantiate your picks, and choose Run Question at backside proper to execute. (The system will ask you to substantiate that you simply want to run this untested question; you do.) The question begins to execute; the velocity at which ends are returned depends upon what number of gadgets are queried and on their community connections. When it’s completed, the Standing column will provide you with a warning to question completion (or, if one thing’s gone improper, to question failure). Scroll up; there’s a bit known as Question outcomes that reveals the outcomes. If nothing’s there – congratulations! No RDP logins from exterior IP addresses had been discovered. If, nevertheless, there are outcomes proven…
Understanding the outcomes
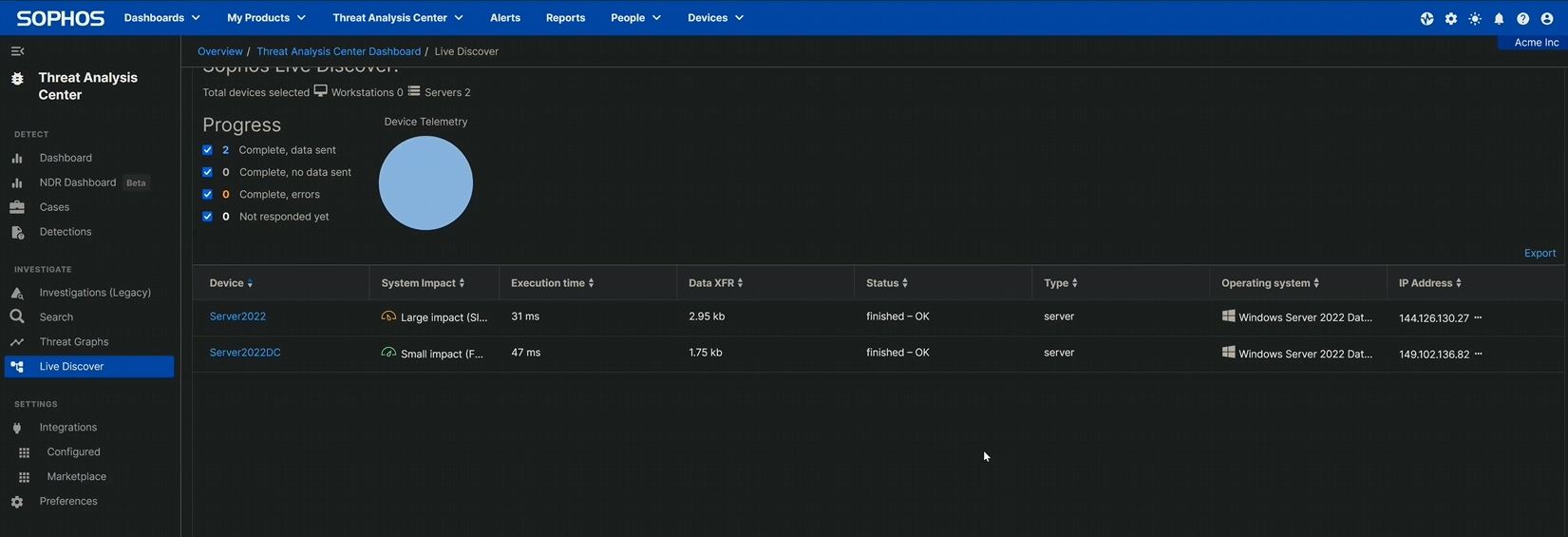
In case your question returns outcomes, the primary area to pay attention to in these outcomes is the endpoint title. Within the instance proven beneath (taken from the testbed we set as much as make our video), two machines reported again that they’ve exterior RDP connections.
Determine 2: Our testbed had two machines, and each of these machines have been touched by an exterior RDP angel
Increasing the outcomes reveals the date and time at which the connection occurred, the occasion ID returned by the question (with a short description of what that occasion ID means), the username of the account that logged in, and the supply IP tackle from which they related. The non-RFC 1918 addresses show that these connections didn’t come from the community’s personal tackle house.
It’s value noting that, as with all question of this sort, extra investigation is critical to be able to rule out false positives. Nevertheless, a “false” constructive – a peculiar exterior connection that actually was simply an administrator opening RDP on a server briefly – continues to be value understanding. As we famous earlier on this sequence of articles, attackers are breathtakingly fast to hop onto an open RDP connection. If the administrator was in a position to join, the percentages are glorious that an attacker had time to seek out the open port as nicely. An abundance of warning would recommend isolating the machine and inspecting it additional for potential compromise.
Distant Desktop Protocol: The Collection
Half 1: Distant Desktop Protocol: Introduction (submit, video)
Half 2: Distant Desktop Protocol: Uncovered RDP (is harmful) (submit, video)
Half 3: RDP: Queries for Investigation (submit, video)
Half 4: RDP Time Zone Bias (submit, video)
Half 5: Executing the Exterior RDP Question ([you are here], video)
Half 6: Executing the 4624_4625 Login Question (submit, video)
GitHub question repository: SophosRapidResponse/OSQuery
Transcript repository: sophoslabs/video-transcripts
YouTube playlist: Distant Desktop Protocol: The Collection