
New analysis from cyber safety agency Rapid7 has proven the ransomware assaults that IT and safety professionals are up in opposition to in APAC are removed from uniform, and they’d be higher off tapping intelligence that sheds gentle on assault tendencies of their particular jurisdiction or sector.
Raj Samani, chief scientist at Rapid7, stated precise ransomware threats usually differ from assumptions primarily based on information protection. Assault floor analysis revealed vital current vulnerabilities like open ports and storage buckets and leaked credentials, he added.
How ransomware threats in Asia-Pacific differ by jurisdiction and sector
Rapid7’s analysis on Asia-Pacific ransomware exercise, carried out over the last half of 2023, discovered variations primarily based on firm location and trade, indicating that organisations taking a blanket method to ransomware protection might be lacking key data.
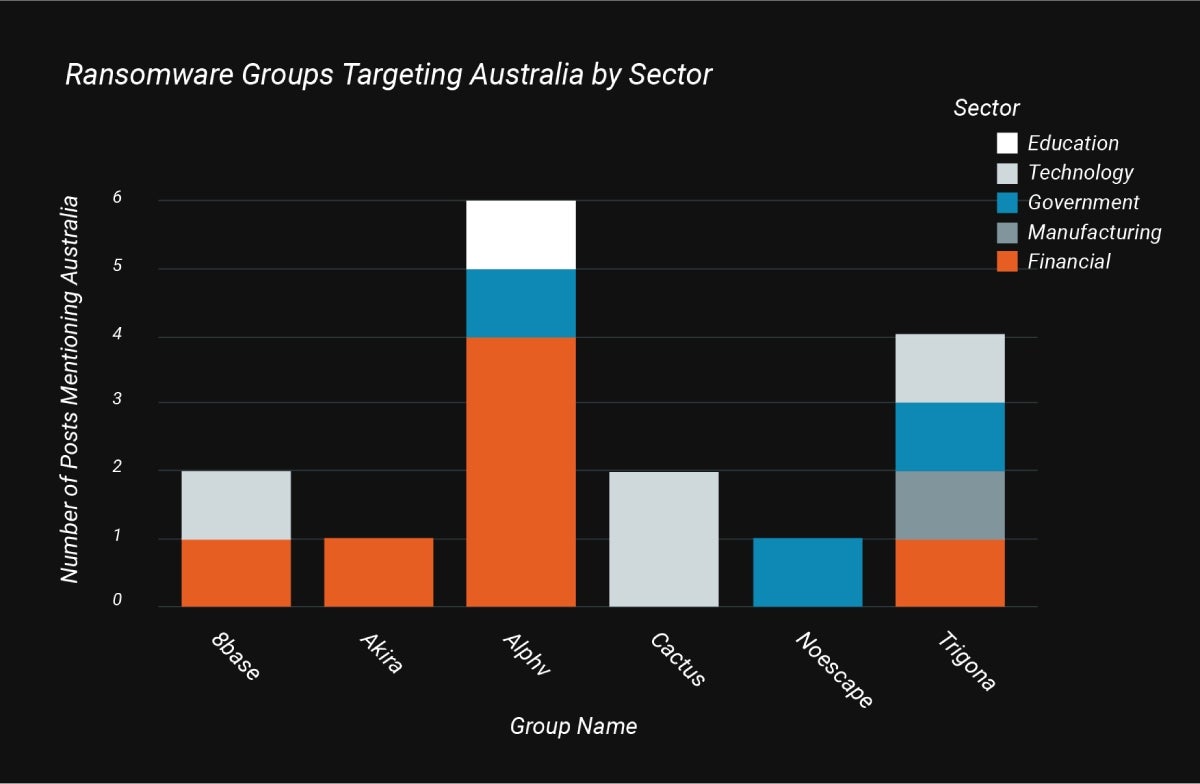
For instance, essentially the most prevalent ransomware group focusing on Australia was ALPHV, or BlackCat. The group was discovered to be primarily focusing on the monetary sector, with some exercise within the authorities and training sectors. The subsequent largest group was Trigona, adopted by 8Base (Determine A).
Determine A
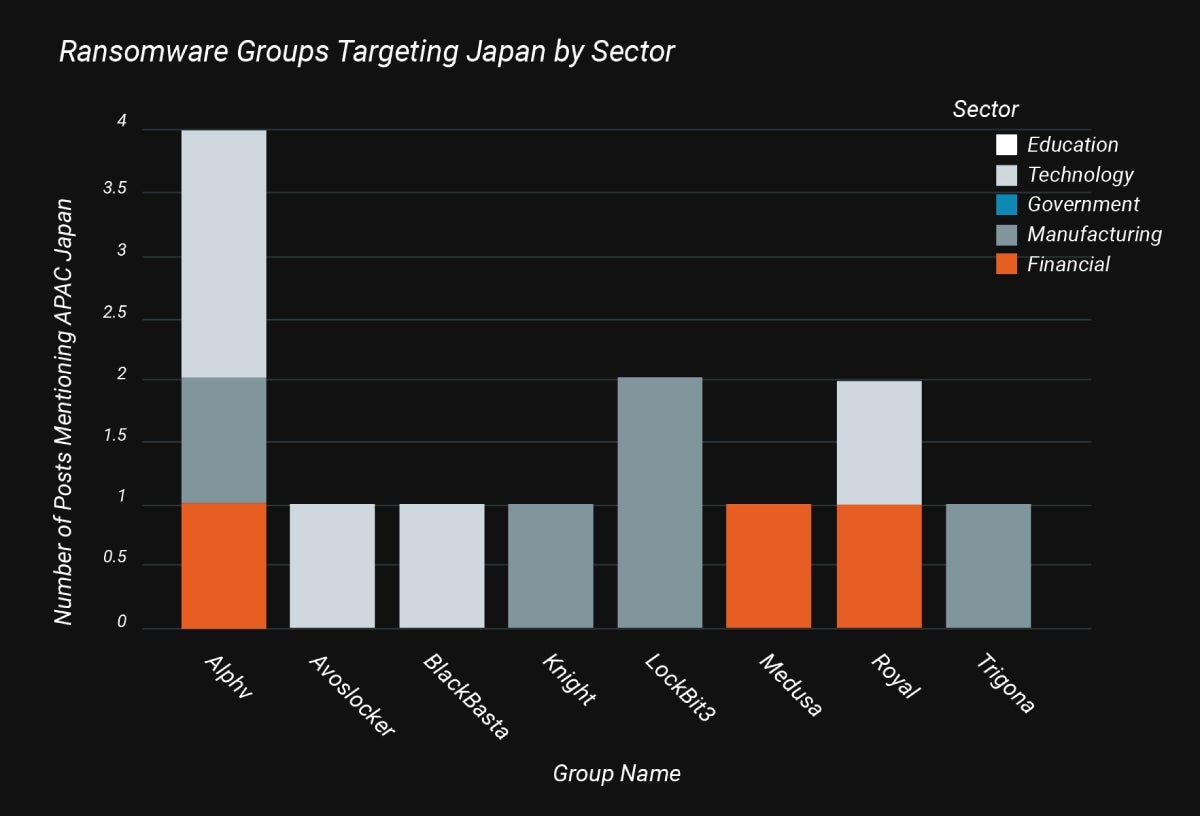
Japan was additionally attacked most by ALPHV, although the largest impression was felt by the tech sector, adopted by manufacturing (Determine B). The subsequent largest assault teams for Japan had been LockBit 3.0, once more focusing on manufacturing, and Royal, focusing on monetary and expertise industries.
Determine B
A side-by-side comparability of Australia with India reveals that, though many menace teams seem in each nations, there are variations within the prevalence of ransomware teams in numerous sectors; for instance, LockBit 3.0 is large in India’s monetary sector however not in Australia’s (Determine C).
Determine C

Extra deviation between sectors than anticipated by Rapid7 researchers
Rapid7 concluded the breadth of menace teams was moderately large for regionally-targeted ransomware campaigns, however the group that’s most prevalent diversified primarily based on the focused geography or sector. “We did count on extra overlap between menace actors between sectors,” Samani stated.
“What was fascinating was the delineation and deviation within the frequent menace teams within the Asia-Pacific,” Samani defined. “We are able to see from the information there are energetic ransomware teams particularly going after particular person sectors or particular nations throughout APAC.”
Samani added that, whereas a CISO in Indonesia, Malaysia or China is likely to be listening to quite a bit about LockBit or ALPHV, there could also be different ransomware menace teams to fret about. “There are a number of different menace teams which can be massively profitable going utterly below the radar nobody talks about.”
Assault floor leaving organisations open to entry brokers
A regarding discovering was how open organisations are to ransomware assaults. “We appeared on the assault floor of sectors inside markets like Australia, and requested if attackers had been going to do recon and break inside for a ransomware assault, is that this one thing that’s straightforward to do?”
Rapid7 discovered that, whereas “the home windows and doorways” weren’t being left open for attackers, they had been being left “unlocked.” Samani cited the variety of open ports and storage buckets, the entry to and availability of leaked credentials, in addition to unpatched techniques within the area.
“This stuff are usually not glamorous or thrilling. However by whether or not you will have open or check techniques on the web, or storage buckets are locked down, you’re beginning to make it tough for entry brokers, who’re expert at getting entry and promoting that on to menace teams.”
Rapid7’s evaluation used machine studying to analyse the exterior entry floor of a number of sectors inside the APAC area over the past half of 2023. It processed knowledge accessible “past openRDP and unpatched techniques,” together with leak websites and compromised datasets.
Increase ransomware defence with an intelligence-based method
Ransomware assaults are on the rise in Asia-Pacific. A latest report from Group-IB discovered that, primarily based on firms with data revealed on ransomware knowledge leak websites, regional assaults elevated by 39% to a complete of 463, with essentially the most (101) occurring in Australia.
SEE: Cyber Safety Traits to Watch in Australia in 2024
Rapid7 recommends organisations within the Asia-Pacific take a extra intelligence-based, nuanced method to coping with ransomware danger. Samani stated they shouldn’t be prioritising or “speculating primarily based on headlines involving organisations midway throughout the globe.”
“Everybody talks about the identical ransomware households. However nobody has sat right down to look and say, ‘Effectively, that doesn’t actually apply right here, what applies right here is that this group,’” Samani defined.
The agency argues that combining exterior assault floor administration and actionable intelligence to determine property with vulnerabilities being exploited within the wild ought to take the very best precedence, particularly when an attributed ransomware marketing campaign is focusing on the sector or geography of the organisation.
“Getting that visibility and intelligence is essential,” Samini stated. “That stage of intelligence means you already know who you’re up in opposition to, and find out how to shield your self.”
