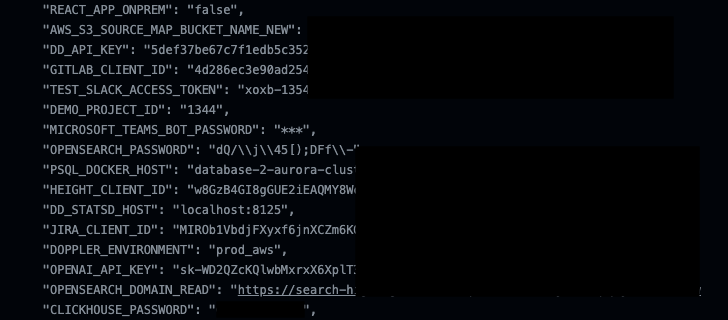
New cybersecurity analysis has discovered that command-line interface (CLI) instruments from Amazon Internet Providers (AWS) and Google Cloud can expose delicate credentials in construct logs, posing important dangers to organizations.
The vulnerability has been codenamed LeakyCLI by cloud safety agency Orca.
“Some instructions on Azure CLI, AWS CLI, and Google Cloud CLI can expose delicate info within the type of setting variables, which might be collected by adversaries when printed by instruments akin to GitHub Actions,” safety researcher Roi Nisimi stated in a report shared with The Hacker Information.
Microsoft has since addressed the problem as a part of safety updates launched in November 2023, assigned it the CVE identifier CVE-2023-36052 (CVSS rating: 8.6).
The thought, in a nutshell, has to do with how the CLI instructions akin to might be used to point out (pre-)outlined setting variables and output to Steady Integration and Steady Deployment (CI/CD) logs. An inventory of such instructions spanning AWS and Google Cloud is beneath 0
- aws lambda get-function-configuration
- aws lambda get-function
- aws lambda update-function-configuration
- aws lambda update-function-code
- aws lambda publish-version
- gcloud features deploy <func> –set-env-vars
- gcloud features deploy <func> –update-env-vars
- gcloud features deploy <func> –remove-env-vars
Orca stated it discovered a number of tasks on GitHub that inadvertently leaked entry tokens and different delicate information through Github Actions, CircleCI, TravisCI, and Cloud Construct logs.
Not like Microsoft, nevertheless, each Amazon and Google contemplate this to be anticipated conduct, requiring that organizations take steps to keep away from storing secrets and techniques in setting variables and as a substitute use a devoted secrets and techniques retailer service like AWS Secrets and techniques Supervisor or Google Cloud Secret Supervisor.
Google additionally recommends using the “–no-user-output-enabled” choice to suppress the printing of command output to plain output and normal error within the terminal.
“If dangerous actors get their palms on these setting variables, this might doubtlessly result in view delicate info together with credentials, akin to passwords, person names, and keys, which might enable them to entry any sources that the repository house owners can,” Nisimi stated.
“CLI instructions are by default assumed to be working in a safe setting, however coupled with CI/CD pipelines, they might pose a safety menace.”