A forensic evaluation of a graph dataset containing transactions on the Bitcoin blockchain has revealed clusters related to illicit exercise and cash laundering, together with detecting legal proceeds despatched to a crypto alternate and beforehand unknown wallets belonging to a Russian darknet market.
The findings come from Elliptic in collaboration with researchers from the MIT-IBM Watson AI Lab.
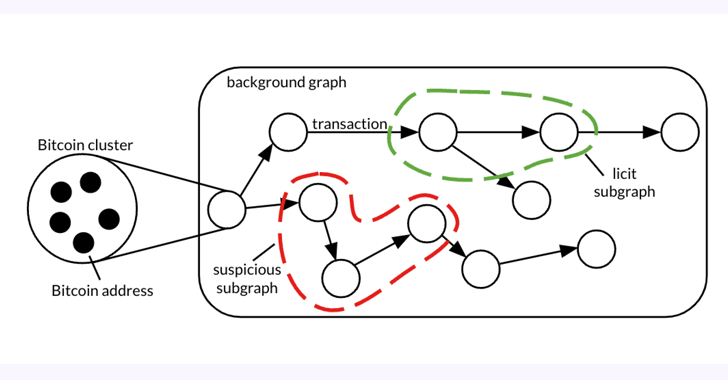
The 26 GB dataset, dubbed Elliptic2, is a “giant graph dataset containing 122K labeled subgraphs of Bitcoin clusters inside a background graph consisting of 49M node clusters and 196M edge transactions,” the co-authors stated in a paper shared with The Hacker Information.
Elliptic2 builds on the Elliptic Knowledge Set (aka Elliptic1), a transaction graph that was made public in July 2019 with the purpose of combating monetary crime utilizing graph convolutional neural networks (GCNs).
The thought, in a nutshell, is to uncover illicit exercise and cash laundering patterns by benefiting from blockchain’s pseudonymity and mixing it with information concerning the presence of licit (e.g., alternate, pockets supplier, miner, and many others.) and illicit companies (e.g., darknet market, malware, terrorist organizations, Ponzi scheme, and many others.) on the community.
“Utilizing machine studying on the subgraph stage – i.e., the teams of transactions that make up situations of cash laundering – will be efficient at predicting whether or not crypto transactions represent proceeds of crime,” Tom Robinson, chief scientist and co-founder of Elliptic, instructed The Hacker Information.
“That is completely different to traditional crypto AML options, which depend on tracing funds from recognized illicit wallets, or pattern-matching with recognized cash laundering practices.”
The examine, which experimented with three completely different subgraph classification strategies on Elliptic2, reminiscent of GNN-Seg, Sub2Vec, and GLASS, recognized subgraphs that represented crypto alternate accounts doubtlessly engaged in illegitimate exercise.
Moreover, it has made it attainable to hint again the supply of funds related to suspicious subgraphs to varied entities, together with a cryptocurrency mixer, a Panama-based Ponzi scheme, and an invite-only Russian darkish internet discussion board.
Robinson stated simply contemplating the “form” – the native constructions inside a posh community – of the cash laundering subgraphs proved to be an already efficient method to flag legal exercise.
Additional examination of the subgraphs predicted utilizing the skilled GLASS mannequin has additionally recognized recognized cryptocurrency laundering patterns, such because the presence of peeling chains and nested companies.
“A peeling chain is the place a small quantity of cryptocurrency is ‘peeled’ to a vacation spot handle, whereas the rest is distributed to a different handle beneath the person’s management,” Robinson defined. “This occurs repeatedly to type a peeling chain. The sample can have professional monetary privateness functions, but it surely may also be indicative of cash laundering, particularly the place the ‘peeled’ cryptocurrency is repeatedly despatched to an alternate service.”
“It is a recognized crypto laundering method and has an analogy in ‘smurfing’ inside conventional finance – so the truth that our machine studying mode independently recognized it’s encouraging.”
As for the following steps, the analysis is predicted to deal with rising the accuracy and precision of those methods, in addition to extending the work to additional blockchains, Robinson added.