Greater than 50% of the 90,310 hosts have been discovered exposing a Tinyproxy service on the web that is susceptible to a crucial unpatched safety flaw within the HTTP/HTTPS proxy software.
The difficulty, tracked as CVE-2023-49606, carries a CVSS rating of 9.8 out of a most of 10, per Cisco Talos, which described it as a use-after-free bug impacting variations 1.10.0 and 1.11.1, which is the newest model.
“A specifically crafted HTTP header can set off reuse of beforehand freed reminiscence, which ends up in reminiscence corruption and will result in distant code execution,” Talos mentioned in an advisory final week. “An attacker must make an unauthenticated HTTP request to set off this vulnerability.”
In different phrases, an unauthenticated menace actor might ship a specifically crafted HTTP Connection header to set off reminiscence corruption that can lead to distant code execution.
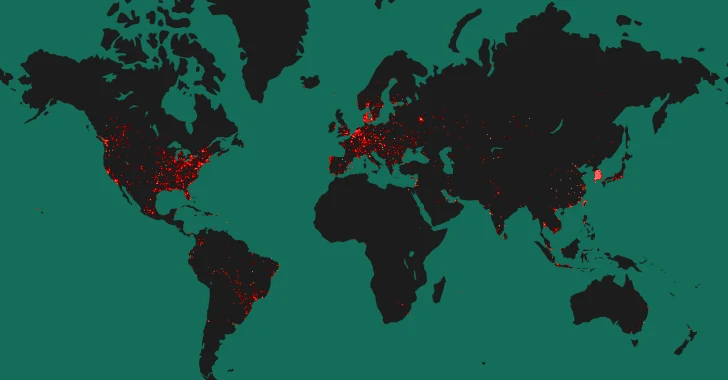
Based on knowledge shared by assault floor administration firm Censys, of the 90,310 hosts exposing a Tinyproxy service to the general public web as of Could 3, 2024, 52,000 (~57%) of them are working a susceptible model of Tinyproxy.
A majority of the publicly-accessible hosts are positioned within the U.S. (32,846), South Korea (18,358), China (7,808), France (5,208), and Germany (3,680).
Talos, which reported the difficulty to December 22, 2023, has additionally launched a proof-of-concept (PoC) for the flaw, describing how the difficulty with parsing HTTP Connection connections could possibly be weaponized to set off a crash and, in some instances, code execution.
The maintainers of Tinyproxy, in a set of commits revamped the weekend, referred to as out Talos for sending the report back to a possible “outdated e-mail tackle,” including they had been made conscious by a Debian Tinyproxy bundle maintainer on Could 5, 2024.
“No GitHub situation was filed, and no one talked about a vulnerability on the talked about IRC chat,” rofl0r mentioned in a commit. “If the difficulty had been reported on Github or IRC, the bug would have been mounted inside a day.”
Customers are suggested to replace to the newest model as and once they grow to be obtainable. It is also really useful that the Tinyproxy service shouldn’t be uncovered to the general public web.