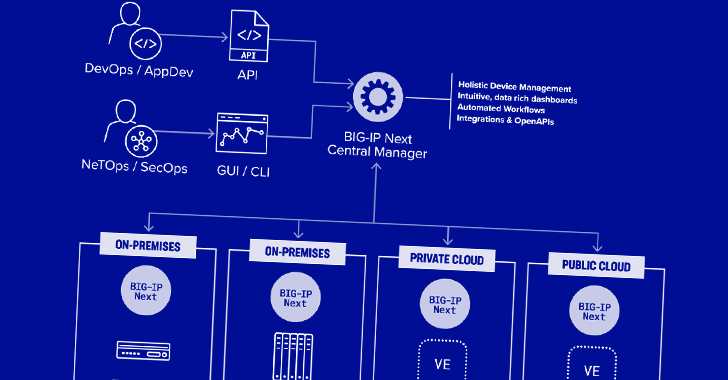
Two safety vulnerabilities have been found in F5 Subsequent Central Supervisor that may very well be exploited by a risk actor to grab management of the gadgets and create hidden rogue administrator accounts for persistence.
The remotely exploitable flaws “may give attackers full administrative management of the machine, and subsequently permit attackers to create accounts on any F5 belongings managed by the Subsequent Central Supervisor,” safety agency Eclypsium stated in a brand new report.
An outline of the 2 points is as follows –
- CVE-2024-21793 (CVSS rating: 7.5) – An OData injection vulnerability that might permit an unauthenticated attacker to execute malicious SQL statements via the BIG-IP NEXT Central Supervisor API
- CVE-2024-26026 (CVSS rating: 7.5) – An SQL injection vulnerability that might permit an unauthenticated attacker to execute malicious SQL statements via the BIG-IP Subsequent Central Supervisor API
Each the issues impression Subsequent Central Supervisor variations from 20.0.1 to twenty.1.0. The shortcomings have been addressed in model 20.2.0.
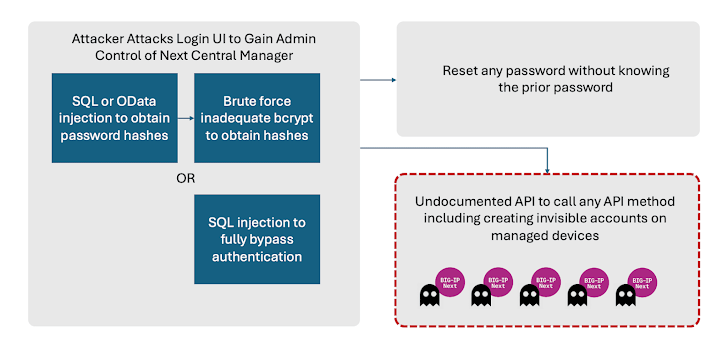
Profitable exploitation of the bugs may end up in full administrative management of the machine, enabling attackers to mix it with different flaws to create new accounts on any BIG-IP Subsequent asset managed by the Central Supervisor.
What’s extra, these malicious accounts would stay hid from the Central Supervisor itself. That is made potential by a server-side request forgery (SSRF) vulnerability that makes it potential to invoke an undocumented API and create the accounts.
“Which means even when the admin password is reset within the Central Supervisor, and the system is patched, attacker entry would possibly nonetheless stay,” the availability chain safety firm stated.
Additionally found by Eclypsium are two extra weaknesses that might merely brute-force assaults towards the admin passwords and allow an administrator to reset their passwords with out information of the prior one. An attacker may weaponize this subject to dam reliable entry to the machine from each account.
Whereas there aren’t any indications that the vulnerabilities have come underneath energetic exploitation within the wild, it is advisable that customers replace their situations to the most recent model to mitigate potential threats.
“Networking and software infrastructure have develop into a key goal of attackers lately,” Eclypsium stated. “Exploiting these extremely privileged techniques may give adversaries a really perfect strategy to acquire entry, unfold, and preserve persistence inside an atmosphere.”