The US Securities & Alternate Comission (SEC) has confirmed that hackers managed to grab management of a cellphone quantity related to its Twitter account, and used it to submit an unauthorised message.
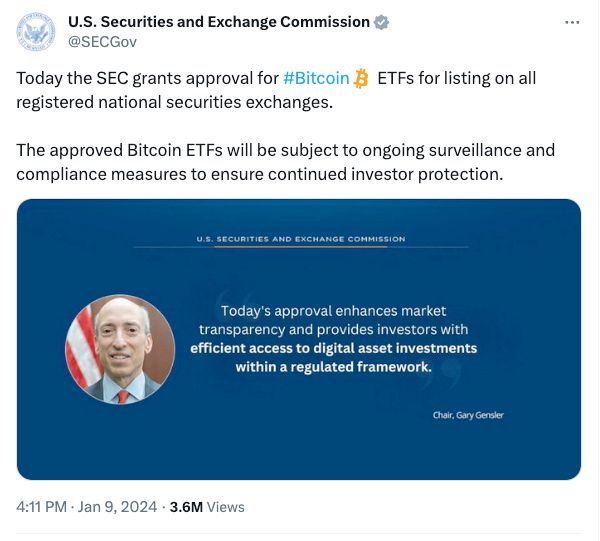
The unauthorised announcement to the SEC’s 660,000 Twitter followers earlier this month claimed {that a} much-anticipated approval of Bitcoin ETFs had been granted, and induced a short lived leap within the worth of the cryptocurrency.
When the reality emerged, the worth of Bitcoin fell again, which means that some buyers would have made losses – whereas others, presumably, profited from the pretend information.
The SEC introduced that it had genuinely Bitcoin ETFs the next day.
So, how did the hackers hijack the SEC’s Twitter account?
Here’s what the SEC says occurred:
Six months previous to the hack, the SEC disabled two-factor authentication (2FA) on its Twitter account.
At a later date, hackers managed to grab management of the mobile phone quantity related to the SEC’s Twitter account by way of a “SIM swap” assault. That is the place a scammer succeeds in tricking workers of a cellphone supplier into giving them management of another person’s cellphone quantity. Typically that is carried out by a fraudster reciting private details about their goal to the telecoms firm, tricking them into believing they’re somebody they’re not.
Sadly for the SEC, Twitter makes it doable to reset an account password simply by understanding and gaining access to its related cell phone quantity.
With the hacker now in charge of the account, they had been free to reset the account’s password, and submit the unauthorised message.
So, why did the SEC disable 2FA on its Twitter account within the first place? The SEC hasn’t stated, however Twitter warned in February 2023 that accounts risked being locked out of their accounts if they didn’t disable SMS textual content message 2FA.
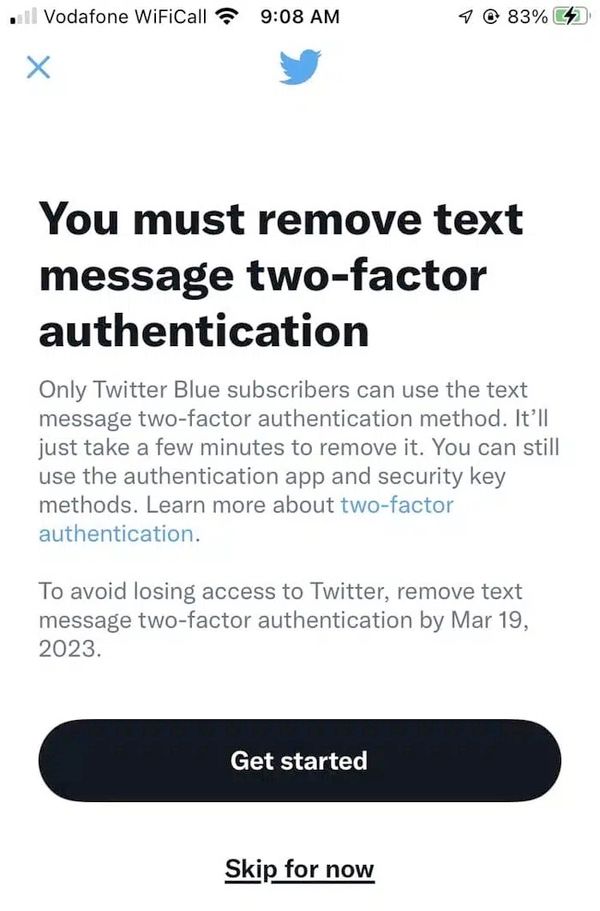
The explanation? Twitter needed its customers to pay up for a Twitter Blue subscription, and – in what I thought of a harmful transfer – Twitter offered SMS-based 2FA as a premium characteristic. (The fact is that for years SMS textual content messages has been thought of a much less safe method of implementing 2FA than options, and so providing it as a premium characteristic despatched a really poor message in my view).
Positive sufficient, in March 2023 Twitter eliminated SMS-based 2FA from all accounts apart from these which had paid for a Twitter Blue subscription. Anybody who nonetheless had SMS-based 2FA enabled, and was unwilling to succeed in into their pockets to pay Twitter was locked out of their accounts.
The SEC says that it used to have 2FA enabled on its account, however requested Twitter assist to disable it after it discovered it was unable to entry its account in July 2023. Sadly, the SEC didn’t re-enable the safety characteristic afterwards (though because the unauthorised tweet it has enabled 2FA – hopefully not in its SMS-based kind – on all its accounts).
All in all, it is a proper mess. And notably embarrassing for the SEC.
Not solely is the SEC within the behavior of rapping the knuckles of firms who haven’t taken acceptable steps to safe themselves in opposition to hackers, however its personal chairman was tweeting in regards to the significance of multi-factor authentication at a time when the SEC’s personal account was not protected by it.
