A important severity vulnerability was found and patched within the Higher Search Exchange plugin for WordPress which has over 1 million energetic web site installs. Profitable assaults may result in arbitrary file deletions, delicate information retrieval and code execution.
Severity Degree Of Vulnerability
The severity of vulnerabilities are scored on some extent system with scores described as starting from low to important:
- Low 0.1-3.9
- Medium 4.0-6.9
- Excessive 7.0-8.9
- Important 9.0-10.0
The severity of the vulnerability found within the Higher Search Exchange plugin is rated as Important, which is the best degree, with a rating of 9.8 on the severity scale of 1-10.
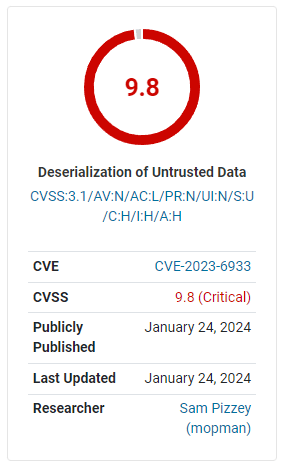 Illustration by Wordfence
Illustration by WordfenceHigher Search Exchange WordPress Plugin
The plugin is developed by WP Engine however it was initially created by the Scrumptious Brains improvement firm that was acquired by WP Engine. Higher Search Exchange is a poplar WordPress device that simplifies and automates the method of working a search and change job on a WordPress web site database, which is helpful in a website or server migration job. The plugin is available in a free and paid Professional model.
The plugin web site lists the next options of the free model:
- “Serialization help for all tables
- The flexibility to pick out particular tables
- The flexibility to run a “dry run” to see what number of fields shall be up to date
- No server necessities except for a working set up of WordPress
- WordPress Multisite help”
The paid Professional model has further options comparable to the power to trace what was modified, potential to backup and import the database whereas the plugin is working, and prolonged help.
The plugin’s recognition is as a result of ease of use, usefulness and a historical past of being a reliable plugin.
PHP Object Injection Vulnerability
A PHP Object Injection vulnerability, within the context of WordPress, happens when a user-supplied enter is unsafely unserialized. Unserialization is a course of the place string representations of objects are transformed again into PHP objects.
The non-profit Open Worldwide Software Safety Undertaking (OWASP) affords a basic description of the PHP Object Injection vulnerability:
“PHP Object Injection is an software degree vulnerability that might permit an attacker to carry out totally different sorts of malicious assaults, comparable to Code Injection, SQL Injection, Path Traversal and Software Denial of Service, relying on the context.
The vulnerability happens when user-supplied enter isn’t correctly sanitized earlier than being handed to the unserialize() PHP operate. Since PHP permits object serialization, attackers may move ad-hoc serialized strings to a weak unserialize() name, leading to an arbitrary PHP object(s) injection into the applying scope.
To be able to efficiently exploit a PHP Object Injection vulnerability two situations have to be met:
- The applying should have a category which implements a PHP magic methodology (comparable to __wakeup or __destruct) that can be utilized to hold out malicious assaults, or to start out a ‘POP chain’.
- All the lessons used through the assault have to be declared when the weak unserialize() is being referred to as, in any other case object autoloading have to be supported for such lessons.”
If an attacker can add (inject) an enter to incorporate a serialized object of their selecting, they’ll probably execute arbitrary code or compromise the web site’s safety. As talked about above, one of these vulnerability often arises as a consequence of insufficient sanitization of consumer inputs. Sanitization is a normal strategy of vetting enter information in order that solely anticipated kinds of enter are allowed and unsafe inputs are rejected and blocked.
Within the case of the Higher Search Exchange plugin, the vulnerability was uncovered in the best way it dealt with deserialization throughout search and change operations. A important safety function lacking on this situation was a POP chain – a sequence of linked lessons and capabilities that an attacker can use to set off malicious actions when an object is unserialized.
Whereas the Higher Search Exchange plugin didn’t comprise such a sequence, however the threat remained that if one other plugin or theme put in on the identical web site contained a POP chain that it may then permit an attacker to launch assaults.
Wordfence describes the vulnerability:
“The Higher Search Exchange plugin for WordPress is weak to PHP Object Injection in all variations as much as, and together with, 1.4.4 by way of deserialization of untrusted enter.
This makes it attainable for unauthenticated attackers to inject a PHP Object.No POP chain is current within the weak plugin. If a POP chain is current by way of an extra plugin or theme put in on the goal system, it may permit the attacker to delete arbitrary recordsdata, retrieve delicate information, or execute code.”
In response to this discovery, WP Engine promptly addressed the problem. The changelog entry for the replace to model 1.4.5, launched on January 18, 2024, highlights the measures taken:
“Safety: Unserializing an object throughout search and change operations now passes ‘allowed_classes’ => false to keep away from instantiating the thing and probably working malicious code saved within the database.”
This replace got here after Wordfence’s accountable disclosure of the vulnerability on December 18, 2023, which was adopted by WP Engine’s improvement and testing of the repair.
What To Do In Response
Customers of the Higher Search Exchange plugin are urged to replace to the newest model instantly to guard their web sites from undesirable actions.
