The 2023/2024 Axur Menace Panorama Report offers a complete evaluation of the newest cyber threats. The data combines information from the platform’s surveillance of the Floor, Deep, and Darkish Internet with insights derived from the in-depth analysis and investigations performed by the Menace Intelligence crew.
Uncover the complete scope of digital threats within the Axur Report 2023/2024.
Overview
In 2023, the cybersecurity panorama witnessed a exceptional rise in cyberattacks.
One notable shift was the cyber danger integration with enterprise danger, an idea gaining traction in boardrooms worldwide. Because the magnitude of losses because of cyberattacks grew to become evident, organizations began reevaluating their methods.
Geopolitical elements performed a major function in shaping info safety. The conflicts between nations like Russia and Ukraine had ripple results, influencing the ways of cybercriminals. It was a yr the place exterior elements intertwined with digital threats.
Ransomware assaults, as soon as primarily centered on encryption, took a brand new flip. Menace actors prioritized information publicity, focusing on organizations with hefty fines for information breaches. The stakes have been larger than ever.
Synthetic intelligence emerged as a potent weapon in cyberattacks. From deepfake movies that includes celebrities to automated social engineering, AI’s function in cybercrime has grown considerably.
One instance is the pretend movies selling cryptocurrency scams utilizing celebrities resembling billionaire Elon Musk and Ethereum creator Vitalik Buterin. The movies use pictures of those executives at occasions, however the authentic strains are changed by an AI-synthesized voice. The photographs are solely altered to make sure lip sync, which is one other perform of this sort of AI.
Hacktivist teams additionally made their mark, aligning with numerous sides throughout world conflicts. Their symbolic assaults posed dangers to people and organizations, highlighting the necessity for vigilance in an interconnected world.
Let’s delve into the platform’s information, right here synthesized into 7 key findings.
Key findings:
1. A Threefold Improve in Leaked Playing cards
The report signifies a troubling escalation in cyber threats. In 2023, a staggering 13.5 million credit score and debit card particulars have been leaked, tripling the quantity from the earlier yr. America tops the listing, accounting for practically half of all detected card leaks. This surge displays the intensified actions on Deep & Darkish Internet channels, the place such information are steadily traded.
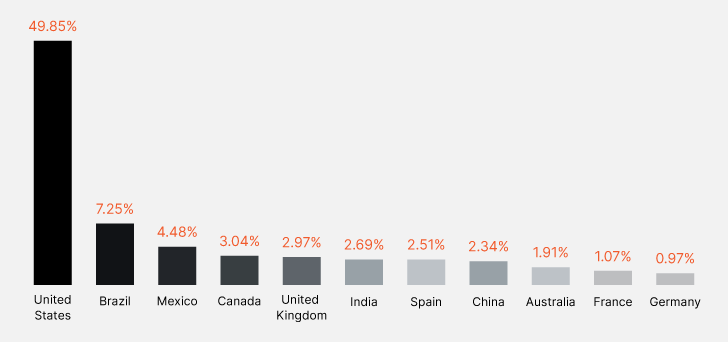 |
| High 10 International locations with the Most Uncovered Playing cards |
2. Highlight on Credential Leaks and Data Stealers
Credential leaks, though secure at 4.2 billion, have witnessed a shift with a surge in pastes and main leaks as sources. Notably, 15% of those uncovered credentials might be thought-about company, highlighting the urgency of strong company cybersecurity measures.
Distinctively, credential stealer malware poses a major menace by acquiring 98% of credentials in plain textual content, bypassing encryption hurdles. These stolen passwords are meticulously cataloged in log recordsdata, offering cybercriminals with insights into acquisition strategies. Moreover, credential stealers seize authorization tokens and cookies, doubtlessly compromising multi-factor authentication.
 |
| Supply of Credentials Leakage in 2023 |
3. Model Misuse and Digital Fraud Panorama
Unconventional use of brand name impersonation, resembling in social media profiles, apps, and paid ads, led to 200,680 detections in 2023, a slight improve from the earlier yr.
 |
| Kinds of Model Misuse in 2023 |
Discover the Menace Panorama Report for cutting-edge insights and options.
4. New Frauds: Evolving Ways
The report has recognized a sequence of novel ways that demand our consideration. Notably, menace actors now possess the potential to ascertain full e-commerce shops inside a matter of minutes, leveraging standard platforms.
Moreover, the rise of “apphishing” scams has taken heart stage, showcasing the rising sophistication of up to date cyber fraud. In these scams, malicious apps masquerade as official browsers, loading cloned pages below the management of cybercriminals. This rising development highlights the necessity for heightened vigilance and revolutionary countermeasures to fight these evolving threats successfully.
5. Behind the Disruption Metrics: Takedown and Uptime
Final yr, Axur executed 330,612 takedowns (the elimination of a web site or web page from the web) with a exceptional success charge, notably in countering threats resembling phishing (96.85%) and faux accounts (97.63%). The spotlight of this course of is the automated notification workflows that considerably cut back the time between incident identification and supplier notifications.
As an example, Axur initiates notifications for phishing instances inside 5 minutes, offering environment friendly dealing with for entities resembling Shopify, Cloudflare, Namecheap, Hostinger, and GoDaddy, usually throughout the similar day. When addressing model impersonation, accounts might be faraway from platforms like Fb and Instagram (sometimes inside a median time of 41 minutes and 56 minutes, respectively) following notifications.
 |
| Takedown Response Time by Group and Platform |
6. Deep & Darkish Internet Insights: Monitoring the Underworld
The evaluation of 133 million messages and posts on the Deep & Darkish Internet supplied insights into the ways and procedures of malicious brokers, enjoying an important function in stopping cyber threats. This monitoring extends to messaging apps resembling Telegram, WhatsApp, and Discord, in addition to deep net boards and illicit marketplaces the place cybercriminals commerce leaked information, compromised pc entry, and illicit providers.
There are greater than 529,965 incidents on monitored Deep & Darkish Internet sources, specializing in retail/e-commerce, monetary establishments, and expertise providers sectors.
 |
| Most Focused Sectors on the Deep & Darkish Internet in 2023 |
Notably, 374,592 incidents resulted from textual content detections, whereas 155,373 incidents have been attributed to audio, video, or picture detections. Multimedia content material evaluation is more and more important because it unveils hidden threats and enhances general menace visibility.
7. Synthetic Intelligence: A New Frontier in Cybercrime
Synthetic Intelligence (AI) instruments, helpful for software program and content material creation, are actually getting used for malicious functions. These instruments allow scammers to craft extra convincing narratives and interactions, enhancing the sophistication of fraud. Then again, Axur is pioneering using generative AI in cyber protection, launching Polaris.
Polaris: AI-powered platform to automate menace administration
Because the core of this AI-driven platform, a specialised Massive Language Mannequin sifts by means of huge information swimming pools, delivering tailor-made, actionable insights immediately aligned with the group’s distinctive assault floor. This revolutionary method not solely streamlines the menace intelligence course of but additionally ensures that safety groups deal with strategic responses, enhancing productiveness and decision-making.
Polaris signifies a departure from the overwhelming, fragmented nature of conventional menace administration by providing a cohesive and centered perspective that facilitates swift, knowledgeable actions in opposition to potential threats, dramatically decreasing evaluation time and enhancing organizational response functionality.
Your Automated Menace Intel Analyst: Start Your 15-Day Polaris Trial Now
Conclusion
The Axur Report elucidates the intricate and evolving cyber menace panorama, notably highlighting the vulnerabilities and challenges confronted in the US. The info offered underscores an pressing want for organizations to adapt and fortify their cybersecurity frameworks in response to the rising sophistication of cyber threats.
To navigate the complexities of the present cybersecurity panorama, organizations should deal with two pivotal methods:
1. Complete Monitoring and Swift Response:
The essence of strong cybersecurity lies within the prolonged monitoring of digital belongings and the effectivity of response mechanisms. Organizations should guarantee deep surveillance of their digital ecosystem, together with monitoring credential sources, monitoring the proliferation of pretend profiles and apps, and vigilant oversight of Deep & Darkish Internet actions.
This thorough monitoring have to be coupled with a fast and decisive response to attenuate the publicity window of potential fraud and digital dangers. By figuring out and addressing threats promptly, organizations can considerably mitigate the impacts of cyber incidents.
2. Harnessing AI for Menace Intelligence and Automation:
Leveraging synthetic intelligence is changing into not simply helpful however important. As guide work is not viable, AI-driven applied sciences supply unparalleled benefits in scaling and automating the detection and neutralization of cyber threats. By adopting AI-powered superior safety options, organizations can improve their menace monitoring and evaluation capabilities.
This not solely ensures a fast and knowledgeable response to cyber incidents but additionally strengthens the group’s general protection framework. Embracing a multi-layered safety method that mixes proactive prevention with reactive methods and AI’s analytical prowess ensures a extra resilient protection in opposition to the more and more subtle panorama of cyber threats.
Be taught Extra About Axur
Axur is a cutting-edge Exterior Menace Intelligence platform famend for its end-to-end automation, top-tier takedown capabilities, and scalable intelligence. Empowering info safety groups, Axur ensures safer digital experiences by detecting, inspecting, and containing threats throughout the exterior perimeter.





